WPS or Wi-Fi Protected Setup , is a protocol designed specifically for home Wi-Fi networks. Thanks to the WPS we can connect to Wi-Fi wireless networks without entering the complex WPA or WPA2 password that we have configured on our router, however, having WPS enabled poses a risk to the security of the wireless network itself, so Its use is not recommended. Today we will show you in detail how WPS or Wi-Fi Protected Setup works.
What is WPS and how does it work?
The vast majority of home devices that connect to the Internet and the local network do so via Wi-Fi. Smartphones, tablets, smart speakers, lighting, laptops, desktops, home automation devices, IP cloud cameras with Wi-Fi and much more, connect to our router via Wi-Fi , all these connections can be made in a traditional way, Entering the complex WPA / WPA2 password that is still the most secure today , or via WPS (Wi-Fi Protected Setup).
To make the concept clear, the WPS system is an authentication method created to facilitate access to secure networks in a simple way . This method of connection has been introduced since 2007 with the appearance of the Wi-Fi 4 or Wi-Fi N standard, although the Wi-Fi Alliance has currently terminated this method because it is considered unsafe. However, we will have a time of transition, where the manufacturers of routers and domestic APs will continue to incorporate it to give compatibility with older equipment, since it is very possible that they are not compatible with WPA3. Being a standard that was invented 12 years ago, currently all equipment with the Wi-Fi standard 4 onwards incorporates it, even the routers of the operators have this feature, in order to facilitate users fast and fast connection. easy.
Through WPS, any user can connect to a wireless network without having to know the password of that network. The WPS allows two connection methods, through the router’s WPS button itself, or by entering a PIN code of at least 8 digits, and a maximum of 8 digits.
WPS through the physical button on the routers
If we select the WPS button connection option, just press this WPS button on our router for a couple of seconds, and search the network with our devices to connect. The device will find the network, and it will automatically connect without having to enter any PIN code. Logically, when pressing the WPS button we will have a time of between one and two minutes to connect without entering any authentication, later this «access» will be closed for security. Currently most manufacturers have opted for this option to connect different devices to the wireless network, since it is more secure than the PIN entry method.

WPS by entering a PIN code
As for the method of entering PIN code . At any time, and without physically pressing the WPS button, we can connect to the Wi-Fi wireless network, and enter the WPS PIN code that we have configured on our router. This will allow us to remember a PIN code of at least 8 digits, and a maximum of 8 digits, and not the complex WPA / WPA2 password we have on our wireless router.
This WPS method with PIN code entry has undergone changes since it appeared. The first thing that we have to take into account, is that to crack the 8 digits of the WPS, we will not need to test 100,000,000 combinations, those corresponding to an 8-digit length of 0-9, but the combinations are much smaller since this 8-digit PIN, internally it is divided into two sub-pins of 4 digits each, and, in addition, according to the standard the last digit of the second PIN is checksum. Due to this architecture, the combinations that we will have to try to crack a WPS PIN goes from 100,000,000 combinations to only 11,000 combinations.
Manufacturers try to mitigate WPS vulnerabilities
The manufacturers, when different vulnerabilities were discovered in this WPS protocol, what they decided was to incorporate into their firmwares methods to avoid brute force attacks, since with 11,000 combinations it is very feasible to be able to discover the PIN in about 24 hours, although it will depend on several factors (chipset of the Wi-Fi card with which you audit the Wi-Fi network, Wi-Fi router, and also distance to that router). This currently means that if we enter the PIN code incorrectly a number of times (in some routers they are 3 times, in other 5 times, etc.) the access via PIN is automatically blocked until we restart the router, to protect against these attacks. In some cases, some operator routers always have the same PIN code set, so cracking in seconds is completely trivial. In other cases, the WPS PIN of the routers are based on the serial number of the router itself, and the PIN is not generated randomly, so cracking the PIN is greatly facilitated.
Other manufacturers have directly disabled the WPS option by entering a PIN, and it is only allowed through the physical button, since we will have to press it on our router to connect. This is the best way to use WPS without being so vulnerable. It is really rare for any of your neighbors to have the necessary knowledge to steal your PIN, but as a recommendation, you should always deactivate the WPS, especially if it uses a PIN to connect clients and does not have measures to mitigate attacks by force gross
Tools to crack the WPS PIN
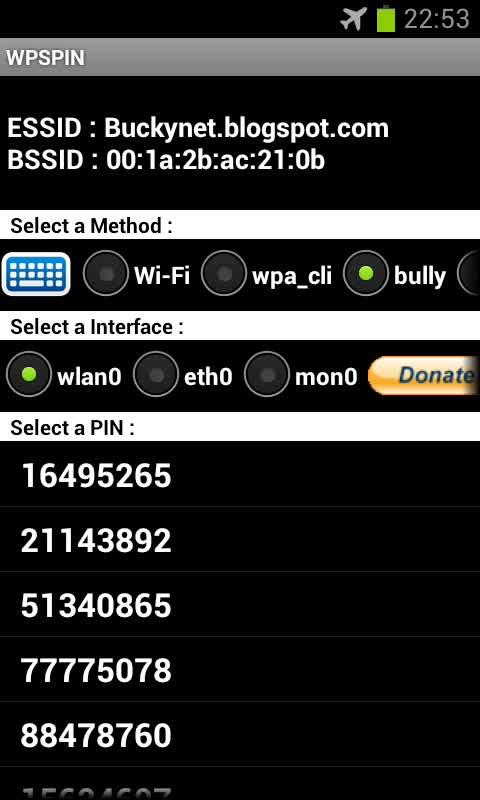
To understand how you can get our WPS PIN, let’s take the Dumpper tool as an example, since this tool has greatly simplified the fact of hacking Wi-Fi networks and any user can get to violate the security of an active WPS network without having great previous knowledge. The creator of this “tool to detect failures in the security of our networks” ensures that any user with a minimum of interest and some luck can violate the security of a Wi-Fi network in less than ten minutes just by clicking a couple of times in the interface of your tool. Dumpper is a software with which we can crack the WPS PINs of the nearby routers, see the amount of Wi-Fi networks in each channel, ping any network, perform dictionary attacks and many other utilities.
Once the tool is started and updated, we will choose the network interface, and click on Scan in the WPS tab. We will see all the networks within reach of our wireless network card with the WPS option activated, and information about each of them. We can see a circle with 4 possible colors, each one will belong to the probability of hitting with the PIN they offer. In addition, we can see the MAC address of the access point in question, the channel on which the network is currently located, its signal quality and the PIN suggested by the tool. If we select one of the networks we can see more information about the interface. In this way, we can obtain up to the router model that generates the network that we have chosen, which can be useful if we want to find the default password in the tool dictionary to access the configuration. Finally, we will only have to press on WpsWin and wait , if the Dumpper manages to enter, a «.txt» file will be generated automatically with the WPS PIN, we will only have to use it to connect to the network.
Other tools
If you are familiar with Linux environments, we recommend you try the WifiSlax distribution as it includes all the tools necessary to crack the WPS. We have tools like Bully and Reaver to perform wireless audits efficiently, and we even have other automated tools such as Bullycioso, and even tools that have dictionaries with the default PINs of different routers, ideal for cracking the WPS PIN in seconds.

Other use tools to hack a Wi-Fi network, this time from an Android device, is WPSapp , this tool is practically a mirror of Dumpper but for Android devices. Once installed it works in the same way as Dumpper, scans networks with active WPS and uses a huge library of default keys to give us the most likely pins of success, once we get the PIN is done, we have access. Another tool is, for example, WPSPIN that will allow us to use dictionary and brute force attacks.
Security recommendations regarding WPS (Wi-Fi Protected Setup)
The solution to all this of the WPS vulnerabilities is much simpler than you are thinking, a recommendation that they will have already made more than once, deactivating the WPS from the router firmware , is very simple and we will avoid possible problems intrusions We are going to give you simple steps to deactivate the WPS function of your equipment for the current operators with a common step, in all the routers we will enter the interface through the IP address 192.168.1.1, regardless of the company that provides us with service.
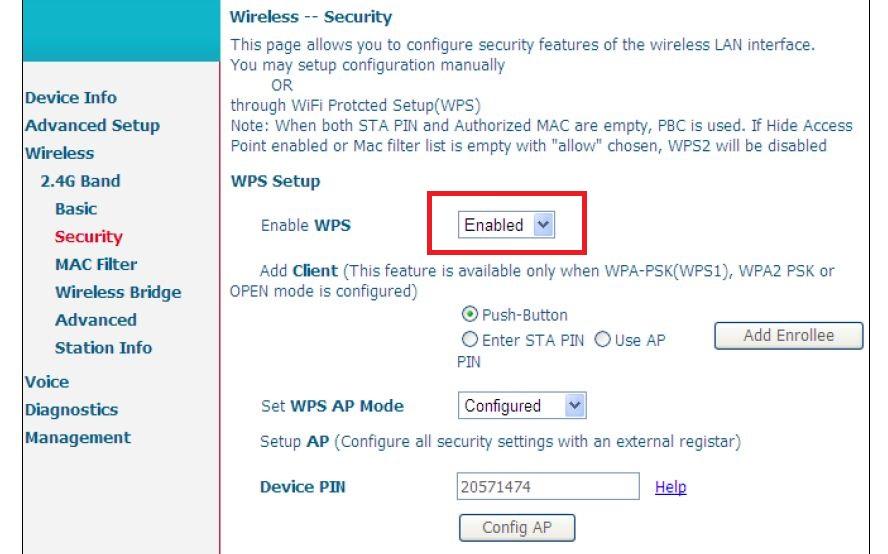
For the Movistar HGU, you only have to access the Wi-Fi configuration and in the security section change the drop-down to «deactivated» and save the settings. Through its “configure AP” button we can install a new code automatically generated by the router’s own dictionary of keys.
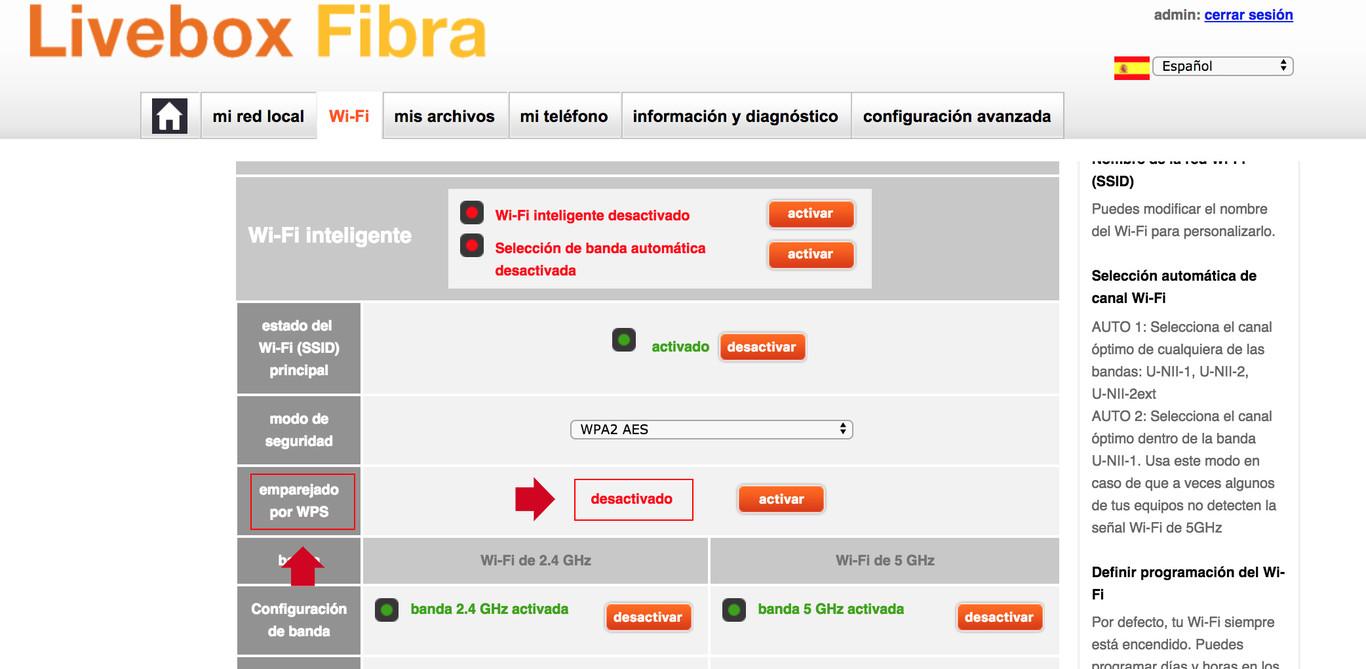
For the Livebox Fibra and the Livebox Plus (they share firmware and the process is identical) of Orange and Jazztel, you must click on the Wi-Fi top tab and lowering a bit we will reach the option of “paired by WPS”, we deactivate it and click on save.
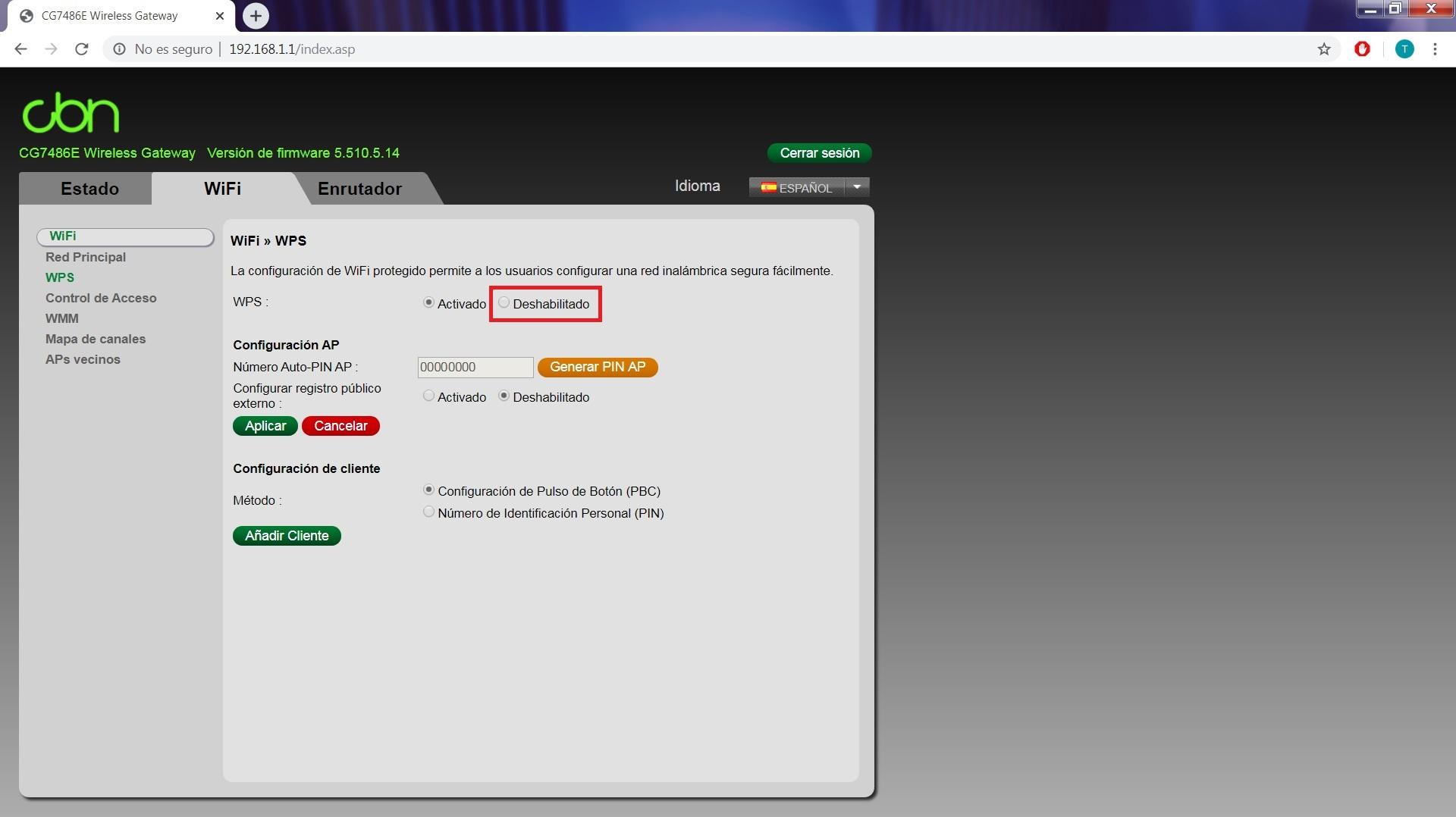
For Vodafone Compat CG7486E , Wi-Fi top tab, WPS section and click on off and apply to save changes. With its «Generate AP PIN» button we can generate a new PIN code which will be assigned from the router’s key dictionary. However, it is advisable to always disable it.
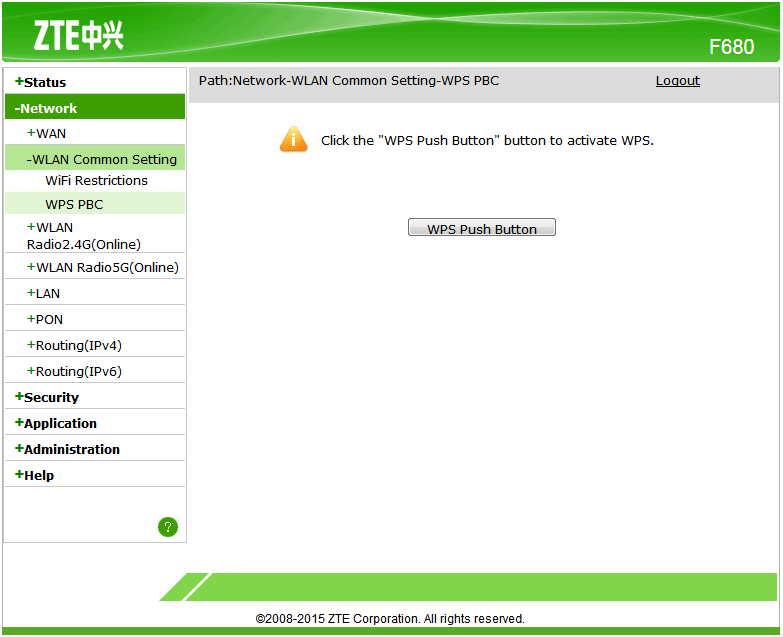
And for the ZTE F680 of MásMovil group, they had the idea of not being able to enter WPS PIN, their authentication by WPS can only be done through the physical button of the router or from the interface in the WPS PBC tab. So, in this case, we do not run a risk unless we press that button ourselves.
From RedesZone we hope that this article has helped you, and now that you know everything about the WPS, you can defend yourself from anyone who wants to access your network in breach of your security, you will know how to make a smarter use of this connection method and in case of To receive an attack, you will be more prepared to solve the problems that it may cause.
WPS will no longer be used in the next generation of wireless equipment in favor of Wi-Fi Easy Connect , in fact, the latest operating systems are already beginning to stop supporting this protocol for the safety of its users. This Wi-Fi Easy Connect provides a simplified method for connecting to wireless networks, making use of QR codes to easily scan with our mobile device, in addition, a Wi-Fi Easy Connect compatible device will not need any graphical user interface, ideal for IoT devices. Finally, this method uses public key cryptography to ensure authentication, and is compatible with WPA2 and WPA3.