
VLANs (Virtual LAN) , or also known as virtual local area networks, is a networking technology that allows us to create independent logical networks within the same physical network. The objective of using VLANs in a home or professional environment is to properly segment the network and use each subnet in a different way, in addition, by segmenting by subnets using VLANs, traffic between the different VLANs can be allowed or denied thanks to a device. L3 as a router or an L3 multilayer switch. Today in this article we are going to explain in detail what VLANs are, what they are for and what types exist.
What are VLANs?
VLANs or also known as ” Virtual LAN ” allow us to create logically independent networks within the same physical network, making use of manageable switches that support VLANs to adequately segment the network. It is also very important that the routers we use support VLANs, otherwise we will not be able to manage all of them or allow or deny communication between them. Currently most professional routers and even firewall / router oriented operating systems like pfSense or OPNsense support VLAN because it is a standard today. The use of VLANs provides us with the following:
- Security : VLANs allow us to create logically independent networks , therefore, we can isolate them so that they only have an Internet connection, and deny traffic from one VLAN to another. By default, VLANs are not allowed to exchange traffic with another VLAN, it is totally necessary to go up to the network level (L3) with a router or a multilayer switch, in order to activate inter-vlan routing, that is, the routing between VLANs to allow communication between them whenever we need it.
- Segmentation : VLANs allow us to segment all the computers into different subnets , each subnet will be assigned a different VLAN. For example, we can create an internal management subnet for all routers, switches and access points, we can create a main subnet for administrators, another subnet for IoT devices and a different subnet for guests. That is, we can segment the main network into a subnet so that each subnet makes use of communications as they wish. Thanks to segmentation, we can group a large number of computers within the same broadcast domain, even if they are physically far away.
- Flexibility : thanks to the VLANs we can place the different teams in one subnet or another, easily and quickly, and have communication policies where we will allow or deny traffic to other VLANs or to the Internet. For example, if we create a guest VLAN, we could prohibit them from using video streaming services.
- Network optimization . By having smaller subnets, in environments where we have hundreds or thousands of connected computers, we will contain the broadcast in smaller domains, therefore, the network performance will be optimal, without having to transmit the broadcast messages to all the connected computers. which would cause the performance of the network to drop dramatically and could even collapse. By using VLAN, we will have several broadcast domains on the same switch.
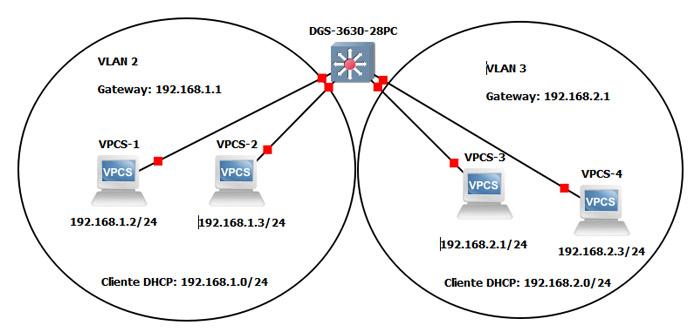
VLANs allow us to logically associate the different users , based on labels, switch ports, their MAC address and even depending on the authentication they have performed in the system. VLANs can exist in a single manageable switch, to later assign each port access to a specific VLAN, but they can also exist in several switches that are interconnected, therefore, VLANs can be extended by different switches through the trunk links. This allows us to have the VLANs on different switches and assign a specific VLAN on any of these switches or on several simultaneously.
When we create and configure VLANs in a router, they cannot communicate with each other, the only way that VLANs can communicate is by ascending to the network level (L3), we can do this in different ways:
- Use a router / firewall with support for the VLANs standard . The switch will pass a trunk with all the VLANs and the router / firewall will register the different VLANs in its firmware or operating system, and will allow inter-vlan routing. It is possible that, by default, this routing is activated, but by rules in the firewall communication between the VLANs is denied, until we allow access.
- Use a L3 managed switch . The L3 managed switches allow us to create IPv4 and IPv6 interfaces, so we can create an interface for each VLAN that we have configured in the switch and activate inter-vlan routing. This is a very good option to intercommunicate the VLANs without the need for the router to take care of everything, generally these L3 switches are at the core of the network.
To allow communication or non-communication of the VLANs, you must use ACLs (Access Control Lists) , or configure the corresponding firewall to allow or deny traffic. For example, communication could be allowed from a VLAN 2 to a VLAN 3, but not the other way around, therefore, by correctly configuring the firewall and the connection states, the communication could be adjusted to the requirements of the company.
What are VLANs for?
When we configure a local area network, either in a home environment where we want to segment the different devices to connect, or in a professional environment, we make use of VLANs to have different subnets. Let’s imagine that we are the network administrators of a school, we can create different VLANs for different uses and make a much easier administration of the network, in addition, we will be able to “contain” broadcast messages in smaller broadcast domains, that is, We will have small subnets to provide addressing to the dozens of computers we have, and not just a subnet where there are hundreds of connected devices. In this scenario of a school, we could perfectly have the following VLANs:
- Management VLAN: we can create a management VLAN to access the router, firewall, all the switches distributed throughout the school and also the WiFi access points that we have, the monitoring systems will also be in this VLAN to continuously monitor the different network equipment.
- School administration VLAN: in this VLAN will be all the PCs of the principal, school secretary, teachers and other staff.
- Student VLAN: all the students’ computers will be in this VLAN, whether they are wired computers in the classrooms or via WiFi with a specific SSID associated with a VLAN.
- Guest VLAN: this VLAN could connect the different smartphones and tablets of the students themselves, the parents when they visit, etc.
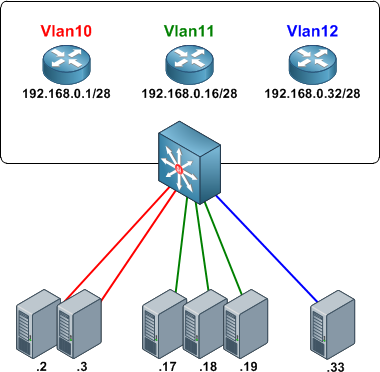
As you can see, a VLAN will allow us to segment the local network into several smaller subnets, specifically focused on a specific task, in addition, we can provide security because the VLANs between them will not be able to communicate (or yes, depending on the ACL configuration that we want). Thanks to the VLANs the general performance of the network will improve, because we will be containing the broadcast in smaller broadcast domains.
Once we have seen what VLANs are and what they are for, we will see what types exist.
Types of VLANs
Currently there are several types of VLANs that we can use in the different equipment, that is, in the switches and WiFi access points. The different VLANs that exist are those based on the 802.1Q standard VLAN Tagging based on tags, port-based VLANs, MAC-based VLANs, application-based VLANs, although the latter is not usually used regularly.
802.1Q VLAN Tagging
It is the most widely used type of VLAN, it makes use of the 802.1Q standard to tag or untag VLANs. This standard consists of introducing an 802.1Q header into the Ethernet frame that we all know, in order to differentiate the different VLANs that we have configured. This standard does not encapsulate the original Ethernet frame, but adds 4 bytes to the original Ethernet header, in addition, the change of “EtherType” is changed to the value 0x8100 to indicate that the frame format has been changed.
When we are using the 802.1Q standard and we create the different VLANs on a switch, we can configure the different ports as “tagged” or “untagged”, that is, tagged or untagged.
- VLAN tagged : the “tag” of the VLAN ID that we have configured is incorporated into the Ethernet frames. This type of VLANs are understood by all switches, by professional WiFi access points and by routers. One or more VLANs on a given port can be configured in tagged mode. Trunks (from a router to a switch, from switch to switch and from switch to AP) are usually always configured as “tagged” to “send” all VLANs to them.
- VLAN untagged : in the Ethernet frames the tag that we have configured is removed, this type of VLANs are understood by all devices, but they are mainly used for end equipment such as computers, laptops, printers, IP cameras and another type of device . In a specific port, we can only configure one VLAN as “untagged”, we cannot put two VLANs as “untagged” because the end device would not “understand” anything.
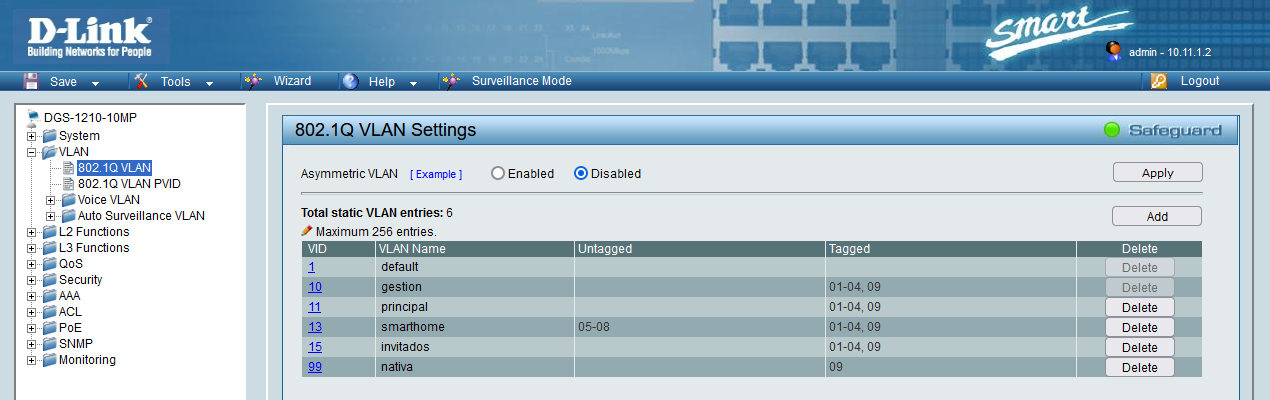
In the following image you can see that we have different VLANs created, and we will have an «untagged» column with the switch ports that are unlabeled. We also have a column with “tagged” where the tagged VLANs are. In this example, ports 1-4 and 9 are configured with professional APs and with another switch, therefore, we will be passing the tagged VLANs.
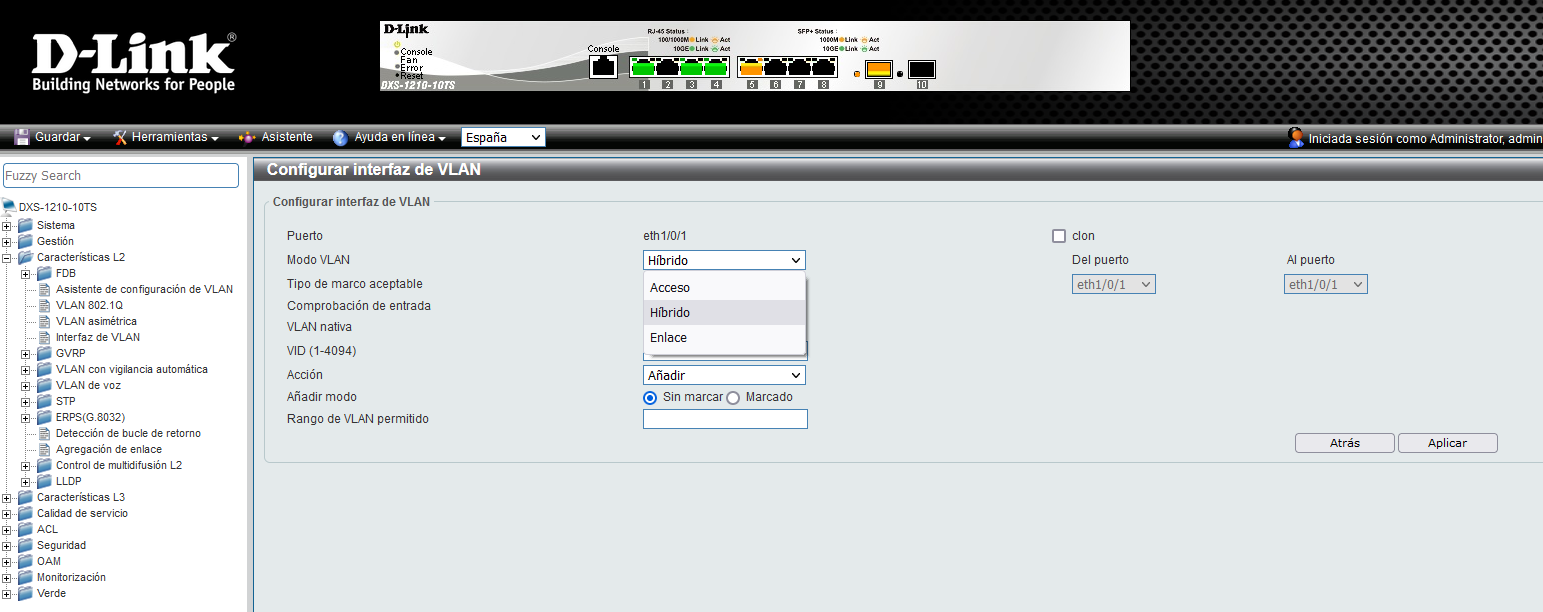
When we are using this standard, the switches also allow you to configure the physical ports in different ways:
- Access : these are the ports where we will connect the PCs, printers, smartphones and the end devices. This access port will have a VLAN configured as “untagged”.
- Trunk or trunk : takes one or more VLANs from one computer to another, for example, if we want to connect a switch with another switch and “pass” all the VLANs or some of them, we will have to configure it in trunk or trunk mode, and select the VLANs that we want to pass as «tagged».
- Dynamic : depending on the type of packet the switch receives, it will be set as access or as trunk. It is not recommended to configure the ports of a switch in dynamic mode for security to avoid possible attacks.
Depending on the port configuration that we are going to choose, we will have to fill in different parameters to correctly configure the VLAN. For example, if we select the access mode (to pass the VLANs as untagged to the end device that we connect), it would be like this:
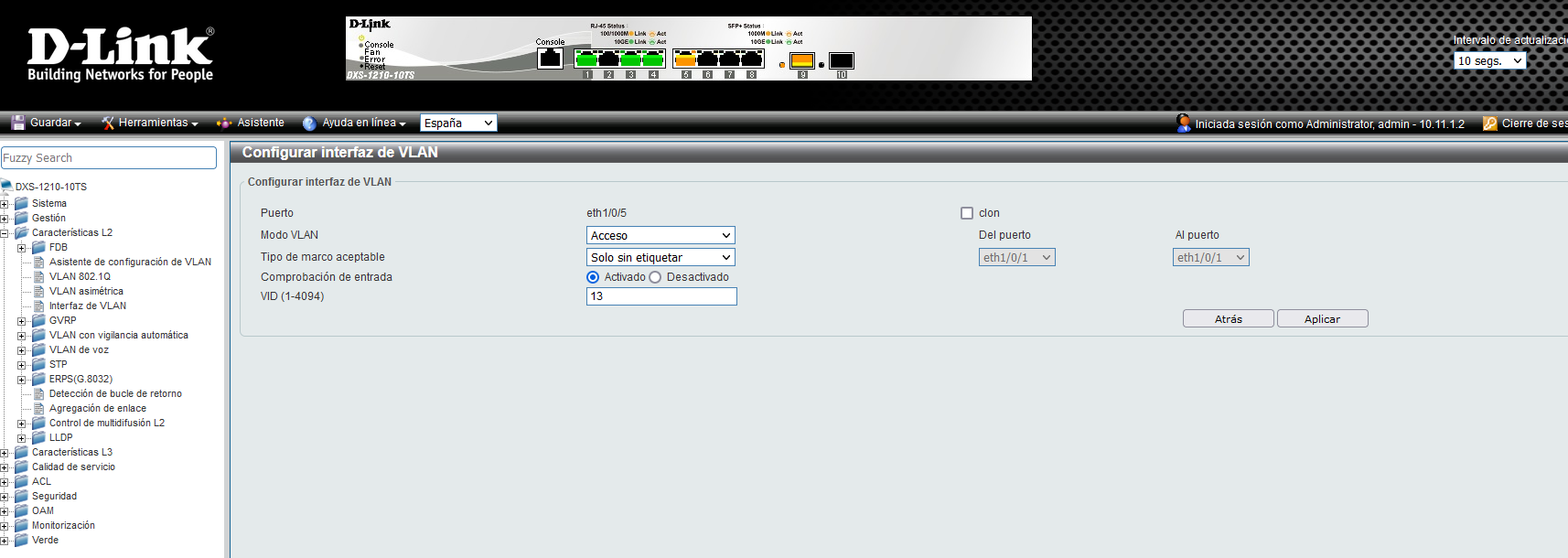
As you can see, when selecting access mode we must put the VLAN ID configured to remove the tag and pass all the data to the final device. An important aspect is that the advanced switches will allow us to configure the types of frames that they accept inbound, in this case, the normal thing in an access port is to allow only untagged frames.
Ports configured as “untagged” is synonymous with a port configured in access mode, and a port configured as “tagged” is synonymous with port in trunk mode where we pass one or more VLANs to it.
Another very important feature of the 802.1Q standard is the Native VLANs, these native VLANs are a VLAN ID that is not put as tagged in the trunks. If an untagged frame arrives at a port, it is considered to belong to the native VLAN. This allows interoperability with old devices, in addition, all traffic management of protocols such as VTP, CDP, Link Aggregation and others is managed through the native VLAN, which by default is the administration one.
Port-based VLANs
Also known as Port Switching in the configuration menus of routers and switches, it is the most widespread and used by very low-end switches. Each port is assigned to a VLAN, and users who are connected to that port belong to the assigned VLAN. Users within the same VLAN have visibility over each other, although not to neighboring virtual local networks.
The only drawback is that it does not allow dynamism when locating users, and in the event that the user physically changes location, the VLAN should be reconfigured. In port-based VLANs, the decision and forwarding is based on the destination MAC address and associated port, it is the simplest and most common VLAN, for this reason low-end switches usually incorporate port-based VLANs and not based on the standard. 802.1Q.
MAC-based VLANs
The reasoning is similar to the previous one, except that instead of being an assignment at the port level, it is at the MAC address level of the device. The advantage is that it allows mobility without the need for changes to be applied to the switch or router configuration. The problem seems pretty clear: adding all users can be tedious. Only the highest-end switches allow VLAN based on MAC, when the switch detects that a certain MAC address has been connected it will automatically place it in a specific VLAN, this is very useful in cases where we want mobility.
Let’s imagine that we connect with our laptop on several Ethernet ports in our office, and we want it to always assign us the same VLAN, in this case with MAC-based VLANs it is possible to do so without having to reconfigure the switch. In large business environments, this functionality is very common to correctly segment computers.
Before finishing, we would like to tell you that, currently, professional WiFi access points and WiFi controllers (whether local or in the Cloud) support VLANs, in this way, we can provide them with a trunk with one or more VLANs to later configure an SSID for each of the VLANs that we have configured. For example, with Nuclias Connect, which is the centralized management platform for WiFi access points from the manufacturer D-Link, we can configure the APs so that they receive all VLANs via LAN, and later assign each VLAN to a specific SSID that we create.
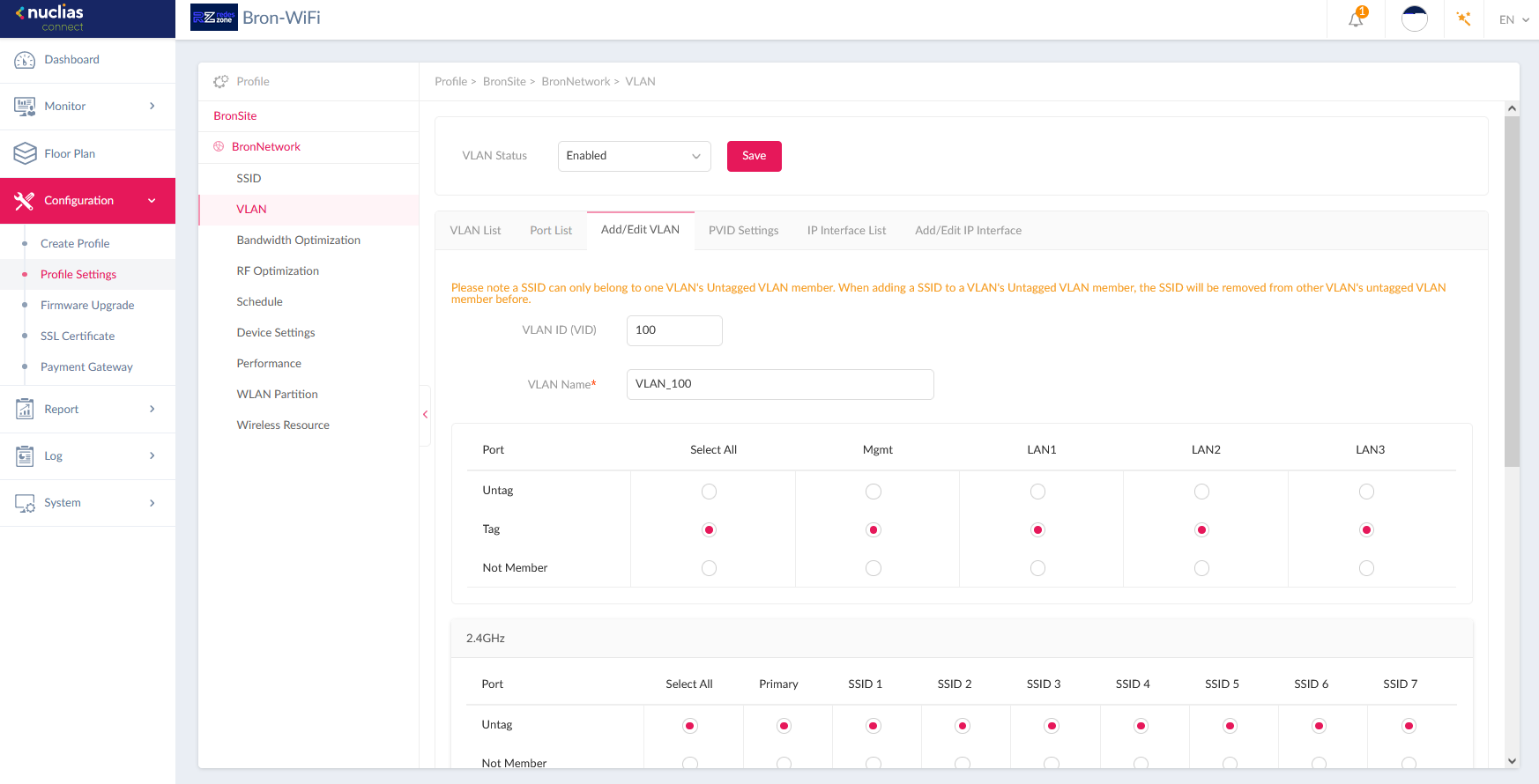
Thanks to this, we will not only be able to segment the wired network, but also the wireless WiFi networks based on the SSIDs associated with the different VLANs that we have. A good security practice would be to create a VLAN with a specific SSID for “Smart Home” devices, such as cable TV or WiFi, IP cameras and other types of devices, so that they are in a specific VLAN and cannot communicate with the devices. computers or smartphones that would be on the main network.
As you have seen, VLANs are a technology that will allow us to correctly segment wired and wireless networks, ideal for having the best possible security, control of all connected equipment, and network optimization to avoid broadcast storms.
