BitLocker is a security tool that allows us to encrypt data disk partitions, disk partitions where the operating system is installed, and even the entire hard disk or SSD, with the aim of protecting all data with robust encryption based in AES. Depending on the advanced configuration we make, we can configure AES-128 or AES-256 to protect all the information. Today in this article we are going to show you how to activate and configure BitLocker through the command line, using the popular command prompt or CMD in Windows.
What is BitLocker and what does it provide us?
BitLocker is a Microsoft security program that provides protection to hard drives or SSDs using data encryption, this technology comes by default in versions of Windows Vista onwards, therefore, the latest version of Windows 10 also incorporates this functionality as important. For Microsoft server operating systems, we have BitLocker installed by default in Windows Server 2008 onwards.

Thanks to this Microsoft technology, we can encrypt the data on internal or external hard drives, as well as USB flash drives, and all this using a secure symmetric encryption algorithm such as AES, in its different versions that can be configured through internal operating system options. In this article we have previously explained everything about BitLocker, since we have taught you to activate it and configure it in detail through the graphical user interface.
There are several ways to enable BitLocker on a disk drive:
- Control Panel
- Activities Center
- File Browser
- Command line with command prompt
- PowerShell
Today we are going to show you how to activate and configure it through the command line using the command prompt or CMD in Windows operating systems.
Enter the Windows command console
This time we are going to see how to activate BitLocker from the command line, for this we will use the Manage-bde command; In order to execute this command we need administrator permissions, so we have to enter the command line with administrator permissions, for this, In Windows 10, we click on the magnifying glass icon on the taskbar and type CMD.
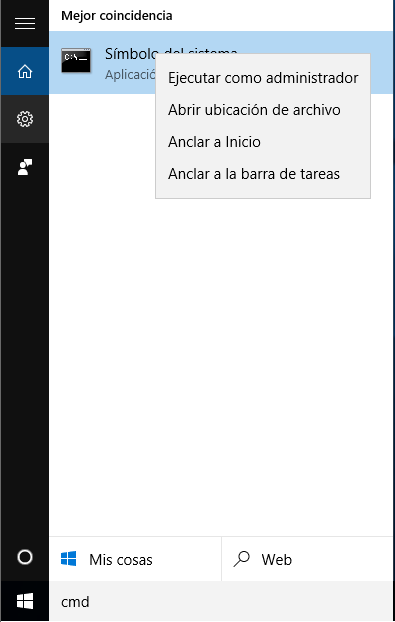
At the top we see the application found, «Command Prompt», by clicking with the right mouse button on it a context menu appears in which we will choose the option “Run as administrator”. When choosing this option, it asks us for confirmation that we want to run the operating system command console with administrator privileges.
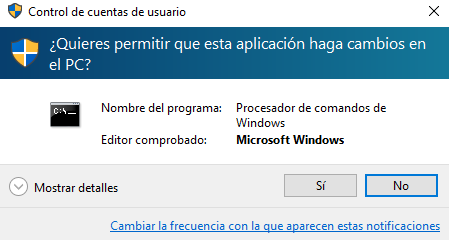
We click on the “Yes” button and the Microsoft Windows command console window opens.
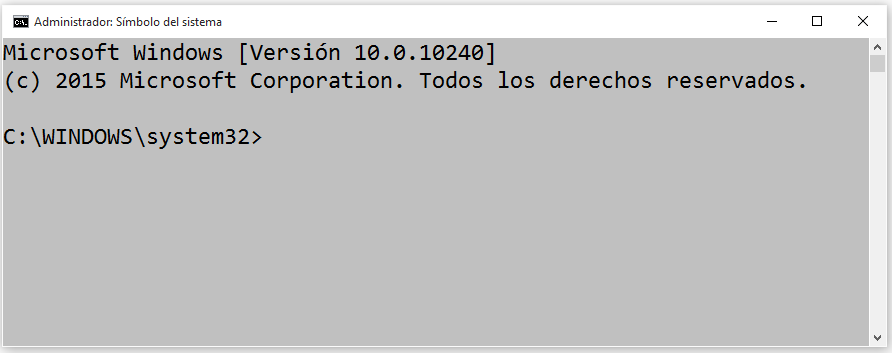
Once we are in here, we can start executing the different commands to activate, deactivate and configure BitLocker in detail.
All commands to manage BitLocker
In this tutorial you will learn all the commands that you must use to perform different actions with BitLocker, such as, for example, activate it in our operating system, verify the use status of BitLocker, we can also configure it to encrypt a disk drive or partition, as well as a flash memory. The fundamental command to perform all these tasks is “manage-bde”, and we will use it throughout the tutorial.
Next, you have all the details to make the most of BitLocker technology to protect all the data contained in the different disks.
Enable BitLocker from command prompt or CMD
Manage-bde is a command line tool that allows us to enable BitLocker encryption on internal boot, internal data and external disk drives, including USB flash drives. Manage-bde has even more parameters than those shown by the BitLocker tool run from the control panel.
manage-bde /?
It shows us a list of all the parameters that we can use.
manage-bde -status
It shows us the encryption situation of all the disks connected to the system.
manage-bde -status F:
It shows us the encryption situation of the disk connected to drive F.
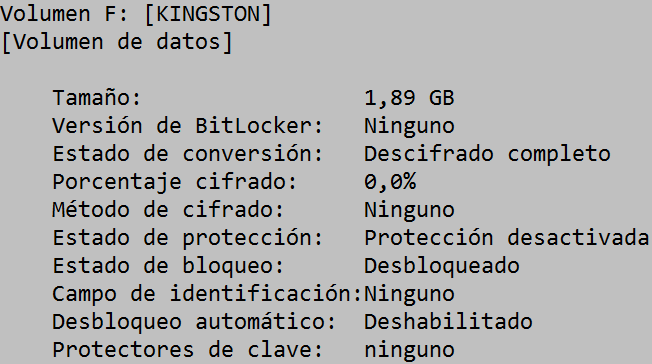
To activate the encryption of a disk with BitLocker it is necessary to provide “protectors” for the encryption, these protectors can be of several types:
- An unlock password (with the minimum security requirements: length 8 characters, uppercase, lowercase, numbers and special characters).
- A recovery key.
- A recovery password.
- A digital signature certificate.
At the very least, you will need to provide an unlock password protector and recovery key as we saw when using BitLocker from Control Panel, Action Center, or File Explorer.
From the command line we can do it in two ways:
Option 1
Providing the unlock password and recovery key in the command “Manage-bde –on <disk drive> -pw <password> -rk <path for recovery key>”.
manage-bde -on f: -pw -rk g:
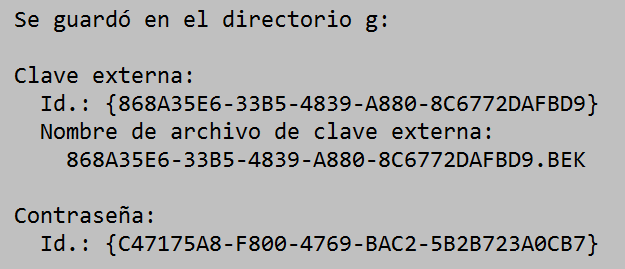
The above command asks us for an unlock password and generates a recovery key on disk “G:” and then begins the encryption of disk “F:”. The disk where the recovery key is stored cannot be a BitLocker-encrypted disk.
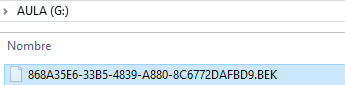
In the indicated location it saves us a .BEK file with the recovery key and shows us on the screen information about the added protectors: the recovery key and the password. An identifier appears in the file name that BitLocker will ask us to use the recovery key that corresponds to a specific encrypted disk.
Option 2
The second option is providing the unlock password and recovery key first in the command “Manage-bde <disk drive> –protectors –add -pw <password> -rk <path for recovery key>” and enabling BitLocker then on said disk unit with the command «Manage-bde –on <disk unit>»
manage-bde f: -protectors -add -pw -rk g:
The above command asks us to enter and confirm an unlock password for drive “F:” and then generates a recovery key and saves it to the specified path, drive “G:”. Then we activate BitLocker on the disk «F:» by executing the command:
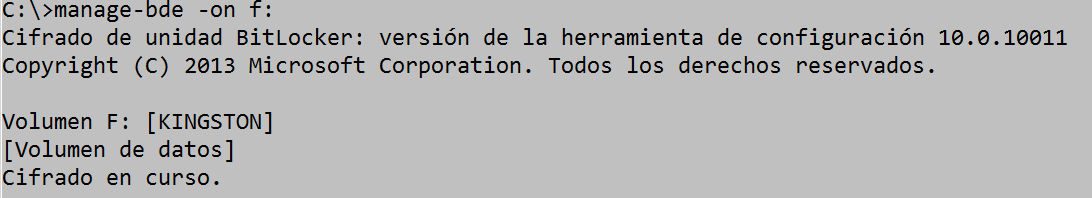
manage-bde –on f:
The system tells us that the encryption of drive F has started:
And a dialog box shows us the progress of the encryption process.
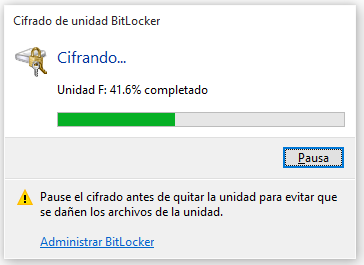
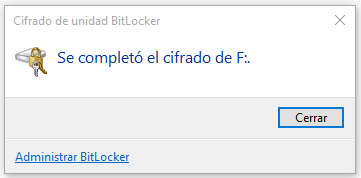
We can run the command “fvenotify.exe <disk drive>” to show the above dialog box in case it does not appear. The following image shows the result of running “manage-bde –status f:”.
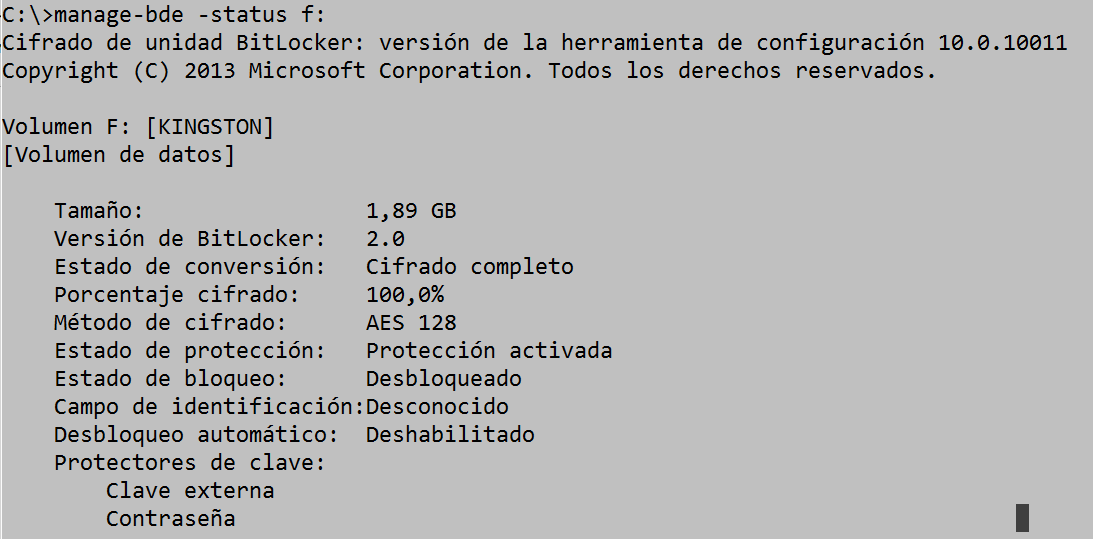
Once we have learned how to enable it, now we are going to take other essential actions to manage BitLocker correctly.
Add a recovery password protector
Optionally, we can add a numerical recovery password to the encrypted disk which, like the recovery key, allows us to unlock an encrypted drive in case we have lost the unlock password. For this we will use the –rp parameter, in either of its two options:
manage-bde -on f: -pw -rk g: -rp
Other possibility
manage-bde f: -protectors -add -pw -rk g: -rp manage-bde -on f:
In the following image we see how to add a recovery password to an already encrypted disk.
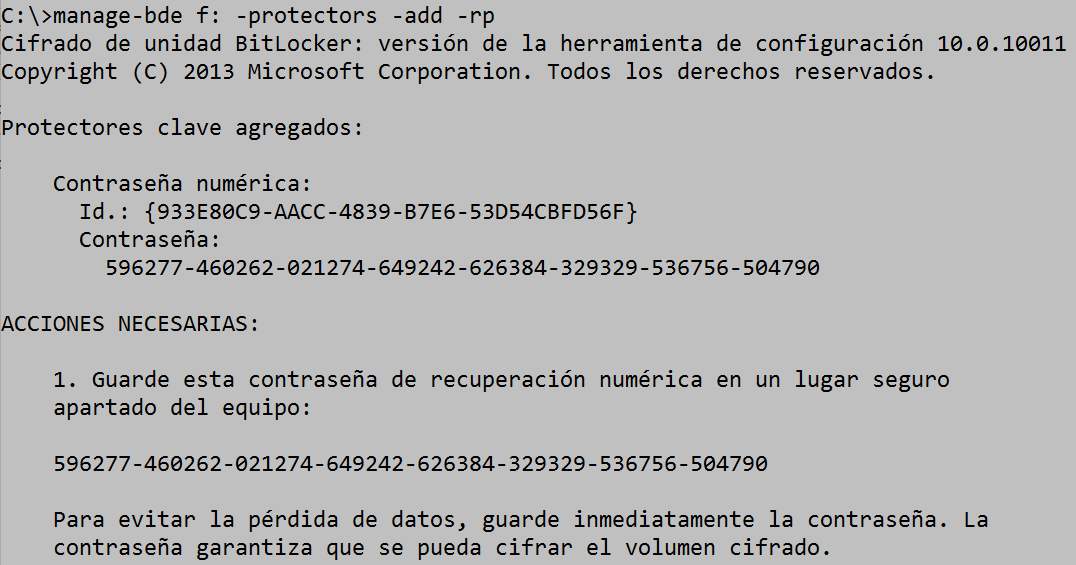
Showing the methods of protecting an encrypted disk
From the command console we execute the following sentence:
manage-bde f: -protectors –get
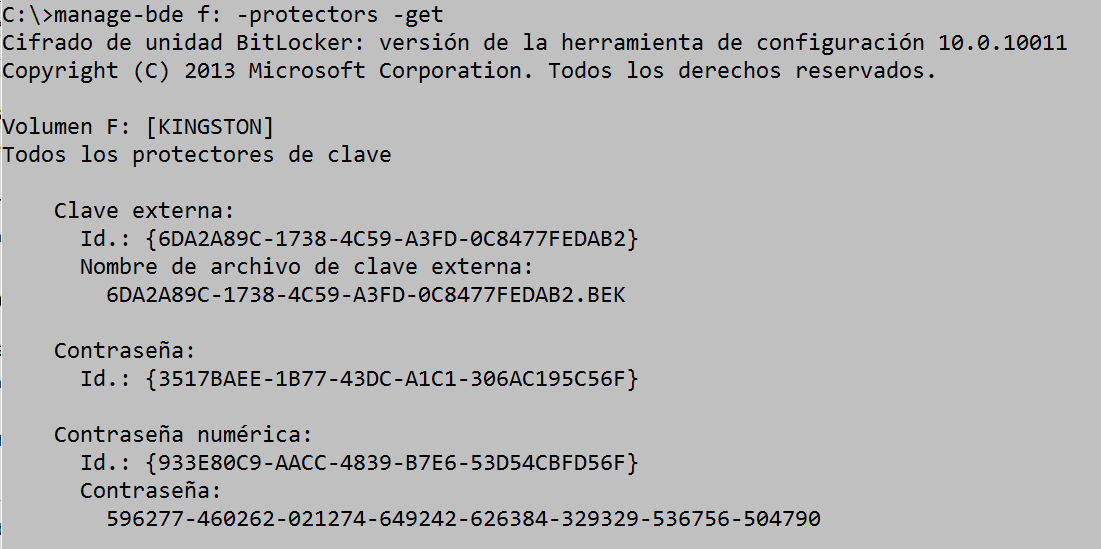
Lock, unlock, and auto-unlock an encrypted disk
With the previous commands we have seen how to activate a BitLocker on a disk, by default the encrypted disk is unlocked and we can use it directly. In case of ejecting the disc, when reconnecting it to any computer, it will indicate that the disc is encrypted and will ask us to write the unlock key. The following commands allow us to handle the encryption disk lock.
This command locks a disk that is unlocked, if it is already locked it does nothing.
manage-bde –lock f:
The following command unlocks a locked disk using the unlock password. It asks us to write the unlock key.
manage-bde –unlock f: -pw
The following command unlocks a locked disk using the recovery key located in the indicated path, it is necessary to indicate the name of the file that contains the recovery key since we can have different recovery keys for different encrypted disks.
manage-bde -unlock f: -rk g:6DA2A89C-1738-4C59-A3FD-0C8477FEDAB2.BEK
The following command unlocks a locked disk using the recovery password that we generated with the –rp parameter.
manage-bde -unlock f: -rp 596277-460262-021274-649242-626384-329329-536756-504790
The –autounlock option allows you to enable or disable the automatic locking of an encrypted disk when it is connected to a computer. In order to enable automatic unlocking, it is necessary that the disk has been previously unlocked by any of the three previous methods.
To enable automatic unlocking we write the following command:
manage-bde -autounlock -enable f:
This command creates an associated foreign key on this disk to allow automatic unlock when connecting the disk to a computer. To disable the automatic unlocking of a disk drive we write the command:
manage-bde -autounlock -disable f:
It is necessary to remove the associated foreign key as indicated by the operating system so that you can disable the automatic unlock completely using the following command:
manage-bde -protectors F: -delete -id {34C63825-A1DB-4175-8F7C-897E4A696CC5}
The command is indicated to us by the operating system itself.
Adding a digital signature certificate as a protector
By means of this protector we can make the encryption of a disk this protected by means of the public key of a digital signature certificate. For this we must have a digital certificate or electronic signature. From this certificate we will need the path where the public key is located, (a file with a .cer extension).
In the following line we see an example of how to add a digital certificate protector to disk “F:” and how we indicate the path where the file containing the public key is located.
manage-bde -protectors -add f: -certificate -cf "g:certcp.cer"
As in the previous examples, after adding the protector to the disk drive we proceed to the activation of BitLocker on said drive:
manage-bde –on f:
Turn off BitLocker on a disk drive
To disable BitLocker on a disk drive, that is, to decrypt a disk drive, it is necessary that the unit is unlocked, then we execute the following command from the operating system command console
manage-bde –off f:
At this time we will have BitLocker disabled on this disk drive, the command is very easy to remember, so we can always run it without having to look at the documentation.
Enable BitLocker on a startup disk
As we saw in the article ” Protecting the data on our disks with BitLocker in Windows 10 “, boot drive encryption has certain peculiarities; in this case we are going to focus on the case that our machine needs a USB flash memory where to store a key to unlock the disk that contains the operating system at startup.
First, you will need to generate a “-startupkey” startup key using the “-protector –add” option of the manage-bde command.
The following command adds a protector of type –startupkey for drive “E:” and saves it to a file in the root folder of drive “F:”.
manage-bde e: -protectors –add –sk f:
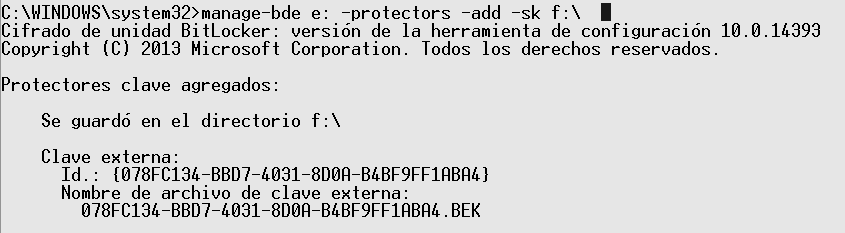
Second, the file with the generated boot key must be copied to a USB flash memory that will be used to unlock the drive that contains the computer’s operating system during startup.
Third, we will activate BitLocker on the boot disk drive and after the restart the encryption will begin, it is important not to remove the USB flash memory that contains the boot key during the whole process and until the encryption is finished.
manage-bde -on C:
As you have seen, we can activate and deactivate this security technology through the command line, ideal for performing all actions through the CMD without using the Windows graphical user interface. We hope that with this tutorial you have been able to learn in detail how BitLocker is used to protect the data on your hard drives, SSDs and also external USB storage drives.