When we have an Internet connection with an operating system aimed at professional environments such as pfSense, it is totally necessary to externally verify if the Internet connection is working correctly, to rule out configuration problems in the VPN servers or in the VPN tunnels that we have configured. Thanks to UptimeRobot we will be able to remotely check if the Internet connection works well, but first we will have to make very specific configurations in pfSense so that the operating system does not detect false attacks.
What is UptimeRobot and how will it monitor the connection?
UptimeRobot is a completely free web service that will allow us to monitor the Internet connection remotely, this service has dozens of servers spread all over the world, which will try to connect with our team through TCP, UDP and even ICMP to check that the Internet connection is working properly. The free version allows us to check up to 50 hosts in 5-minute intervals, enough for a home environment and for small and medium-sized companies, although it is possible that in your company you need to know more quickly if the Internet connection drops. If you buy the premium version, you can configure one-minute intervals to check if the Internet connection is working well, and you will have more hosts to monitor, all centralized in the same account.


In this article we have previously discussed this service in depth, however, if we are using an operating system such as pfSense, which is highly configurable and is capable of detecting denial of service attacks and brute force attacks, it may detect these connections as possible attacks, and directly block communication from the source IP. The same happens if we have an IDS / IPS configured in pfSense itself, it may detect it as a threat. If the operating system blocks the source IP address and does not “reply” to UptimeRobot, then it will detect that the Internet connection is down, when it really is, giving us a false alert.
One feature that we really liked about UptimeRobot is that it will allow us to receive notifications by email, Telegram, Twitter, Slack, Microsoft Teams and more, so we will always have a notification if there is a problem. In addition, we can always install the official UptimeRobot app for Android and iOS:
Once we know everything that UptimeRobot can do for us, let’s see how to correctly configure pfSense to avoid false attack alerts.
Configure pfSense so UptimeRobot is not blocked
Although UptimeRobot has several servers spread all over the world in order to monitor the different hosts and avoid false positives, in many cases this is not enough, especially if we have our pfSense firewall configured very well. All the checks carried out by UptimeRobot are carried out from Dallas-United States, however, when a drop is detected, the rest of the nodes around the world will check if the connection has really dropped or not. However, in this article we have verified that this is not enough if you use pfSense, since it is continuously telling us that the Internet connection is working correctly, and that it has been dropped, the check is oscillating between both states.
In our case, the verification of whether the Internet connection is up is carried out with some «checks» on the SSH server of the pfSense operating system, which we must enable. We will only have to enable the SSH server and configure a specific listening TCP port, for example, port 2222 for SSH. This port will be accessible through the Internet from any source, with the aim of managing the operating system from anywhere.
To solve the problem of false positives, we must enter the pfSense operating system configuration web interface:
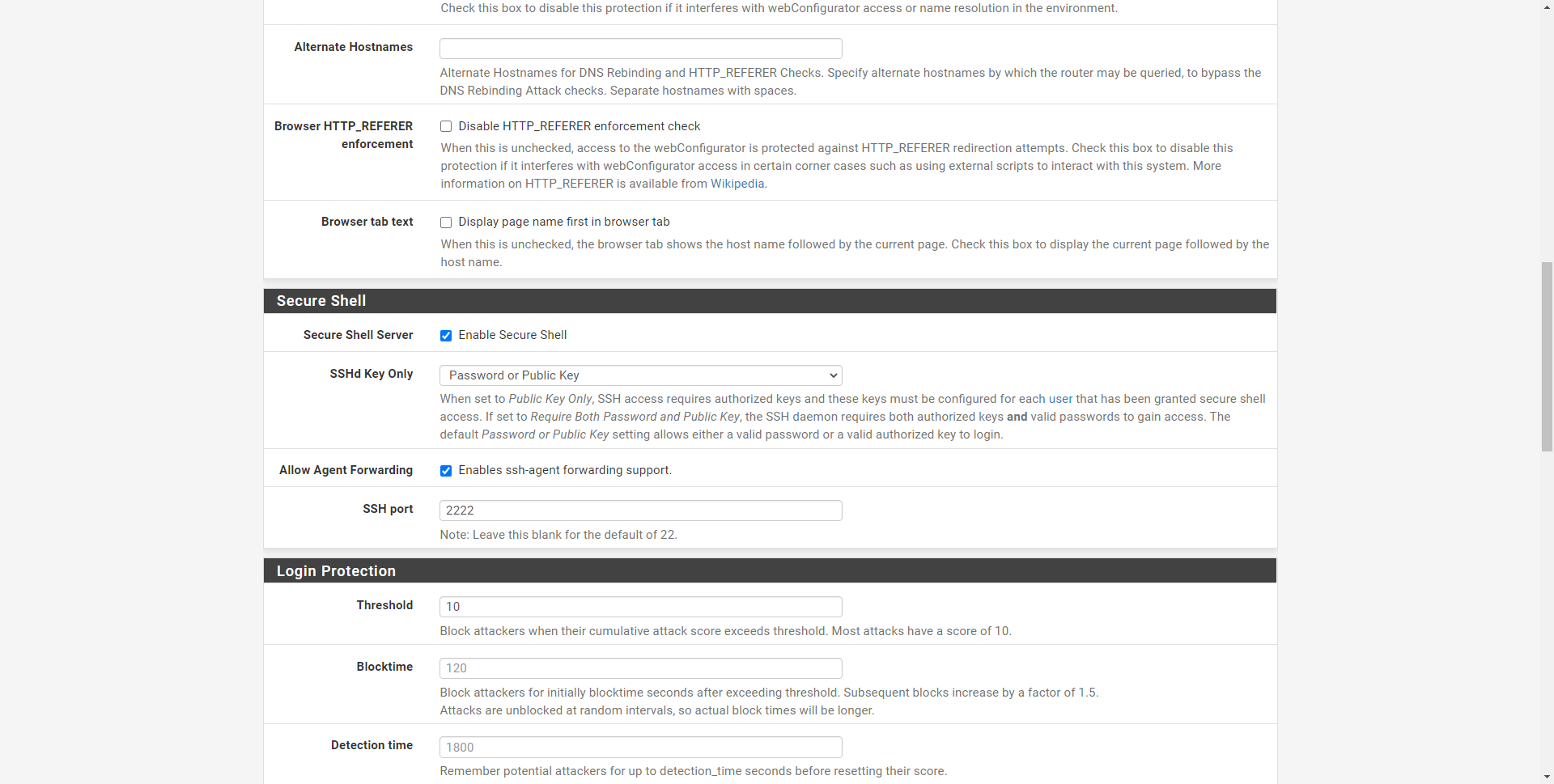
We go to the SSH section and make sure that it is enabled, and that it is listening on port 2222, or on any other port.
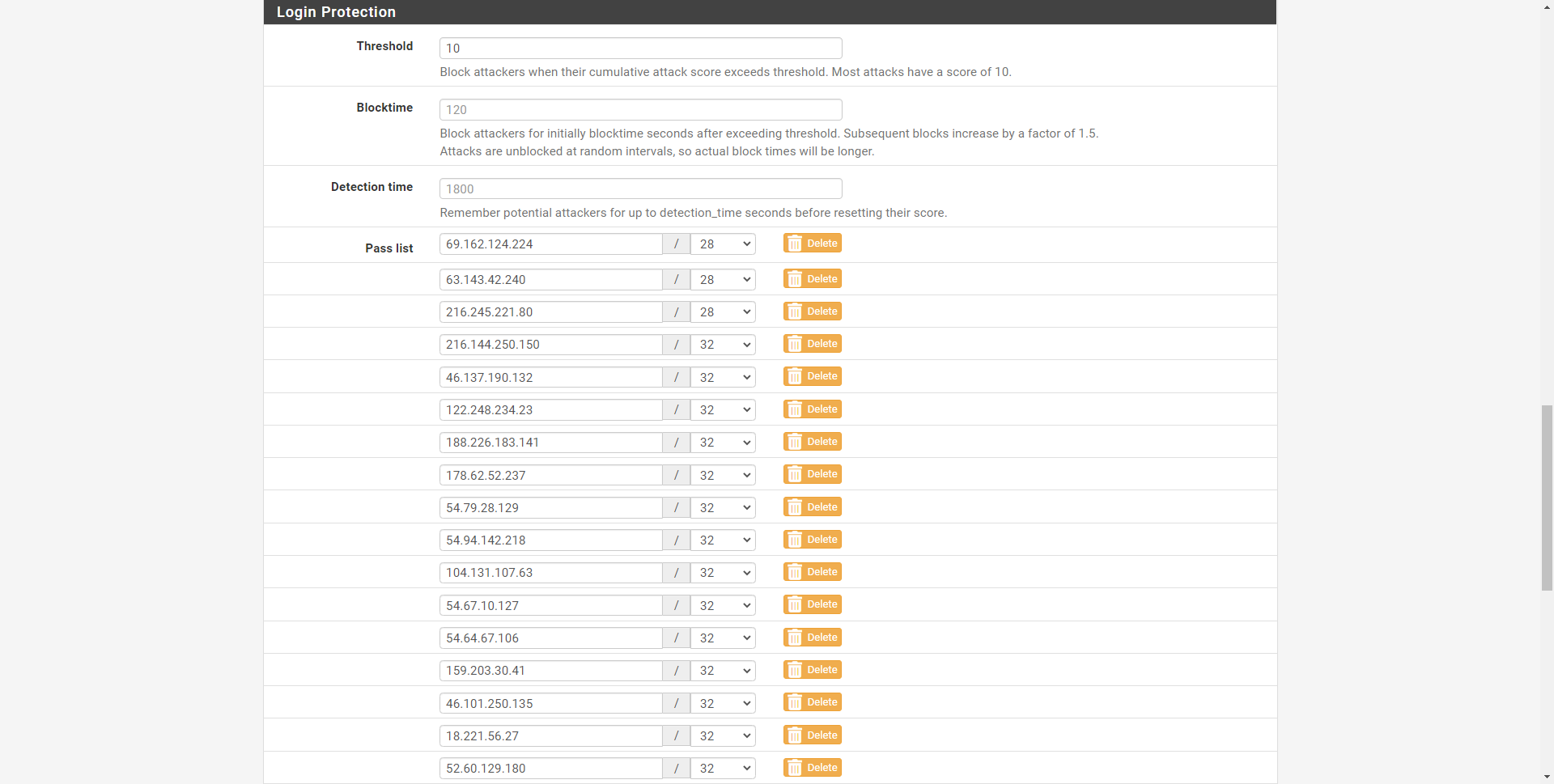
In the “Login protection” section, we must add each and every one of the source networks and IP addresses of UptimeRobot. In this «pass list» we will have the list of all the source IP addresses that can perform «checks» against the HTTPS web server or the configured SSH server, bypassing the restrictions of the «login protection» that we have configured.
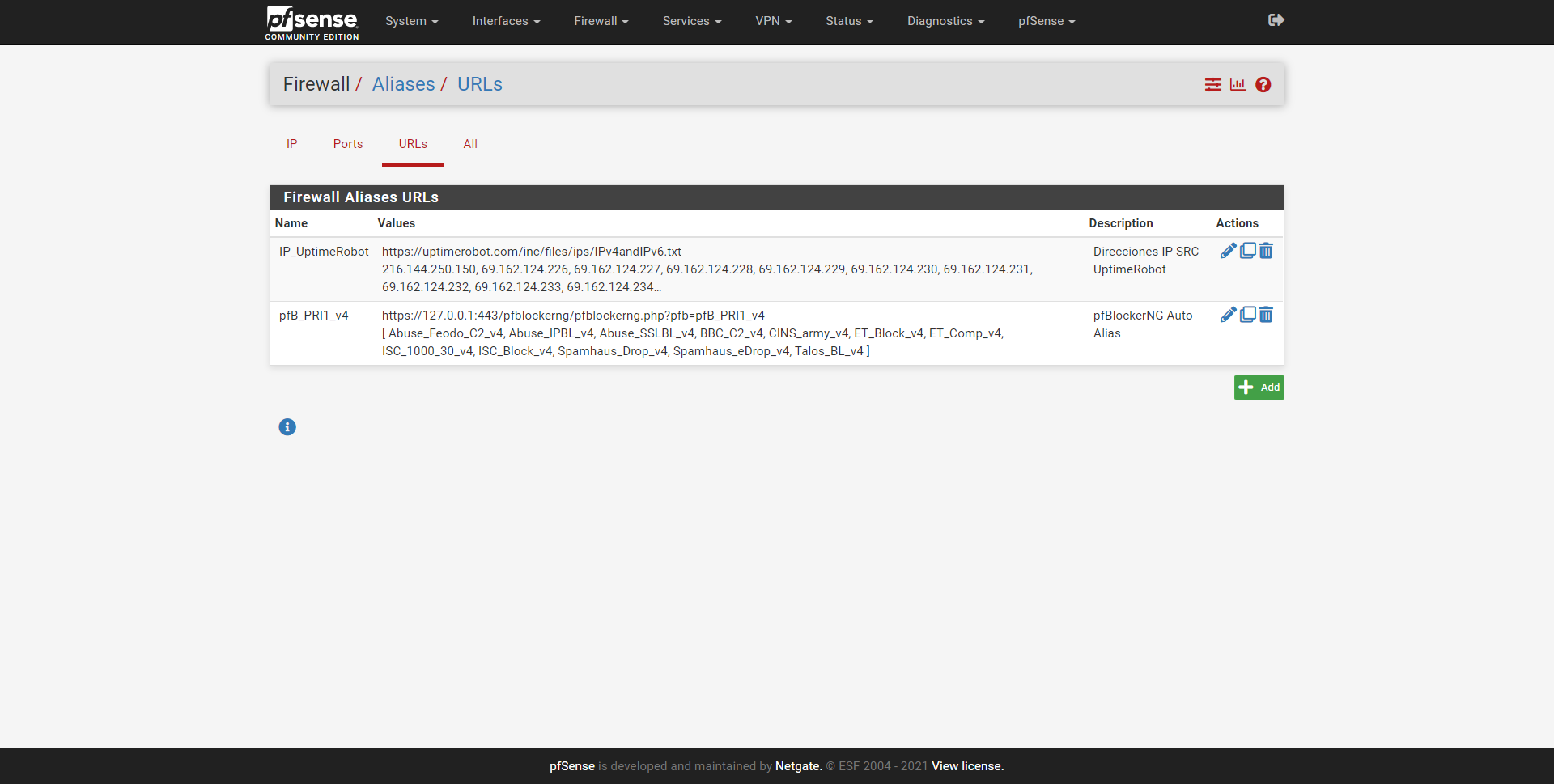
On theofficial website of UptimeRobot we have the list of all the source IP addresses that they use, we will simply have to enter range by range or IP address by IP address. We also have the IPv6 addresses that they use, just in case in your case you have IPv6 to access the Internet. Finally, they also provide us with a txt file with the list of all IP addresses to facilitate the configuration of the firewalls.
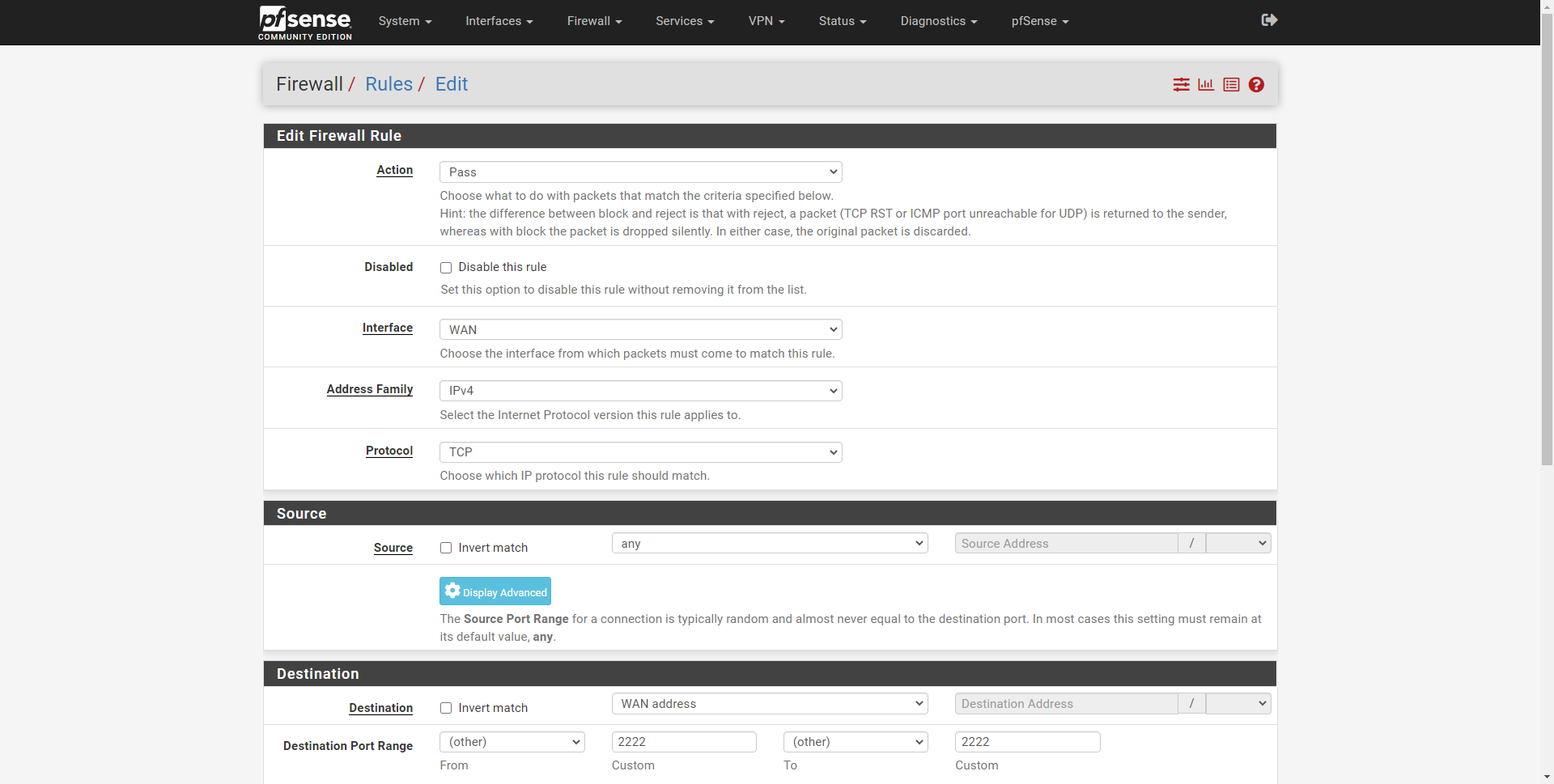
When we enable the SSH server in pfSense, if we want them to access from the Internet with any source IP address, we will need to create a rule in the ” Firewall / Rules ” section, in this rule we must put:
- Action: Pass
- Interface: WAN
- Address Family: IPv4 and / or IPv6.
- Protocol: TCP
- Source: any
- Destination: WAN Address
- Destination Port Range: the port of the SSH server where it is listening, in our case, 2222.
We would also recommend logging all the packets that the firewall receives, activating the option “Log packets that are handled by this rule”, finally we will give it a description and click on save.
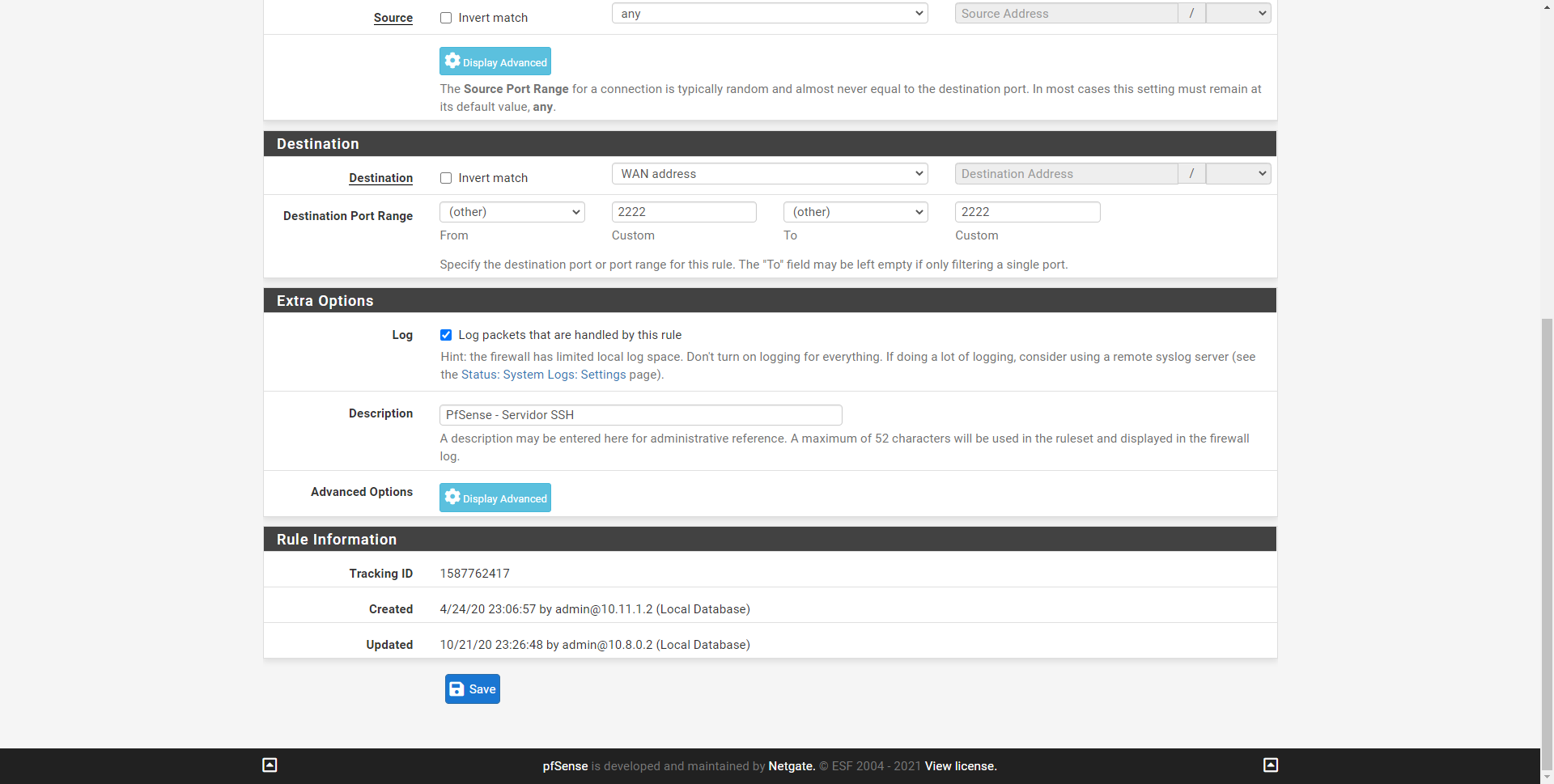
Before finishing, an important detail is that you put the pfSense rule in the WAN section in the correct order, because if we have a general deny all rule above this specific rule, you will be blocking the traffic and it will not work from the outside.
If you view the operating system logs, you will be able to see the source IP address that UptimeRobot is using, as well as the destination IP address and port (us). From here you can check that every 5 minutes it is checking if the Internet connection is working correctly, or rather, if the pfSense SSH server is reachable through the Internet.
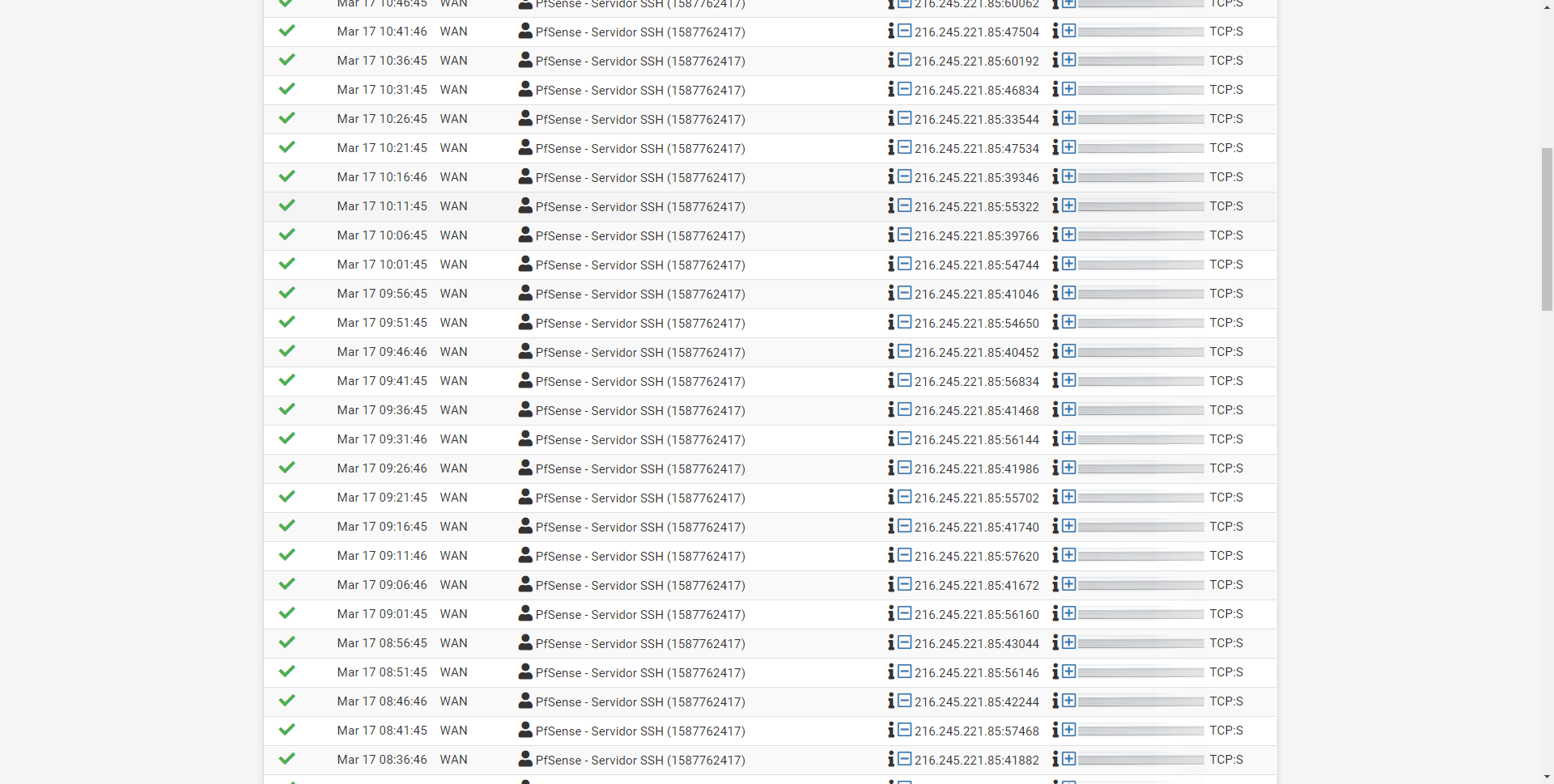
Once we have seen how to correctly configure pfSense, we will remember how to create the rule in UptimeRobot to monitor our pfSense.
Create the monitoring rule in UptimeRobot
We log in to UptimeRobot with our credentials, if you have never used this tool, you will have to register for its “Free” version. In the main menu we can see all the monitoring rules created in the left section, click on ” Add New Monitor ” to create a new rule.
The type of monitor that you should use is “Port”, we give it a descriptive name, we put “Port: Custom Port” to put the port 2222 of the SSH server that we just configured, and the monitoring interval. In the free version of UptimeRobot it will allow us a minimum interval of 5 minutes, logically, the more checks carried out before it will notify us that there has been a problem with the Internet connection, but this is only available in the paid version.
You must not forget to select the alerts to send, we can receive an alert by email, Telegram or another service, as long as you have registered it previously.
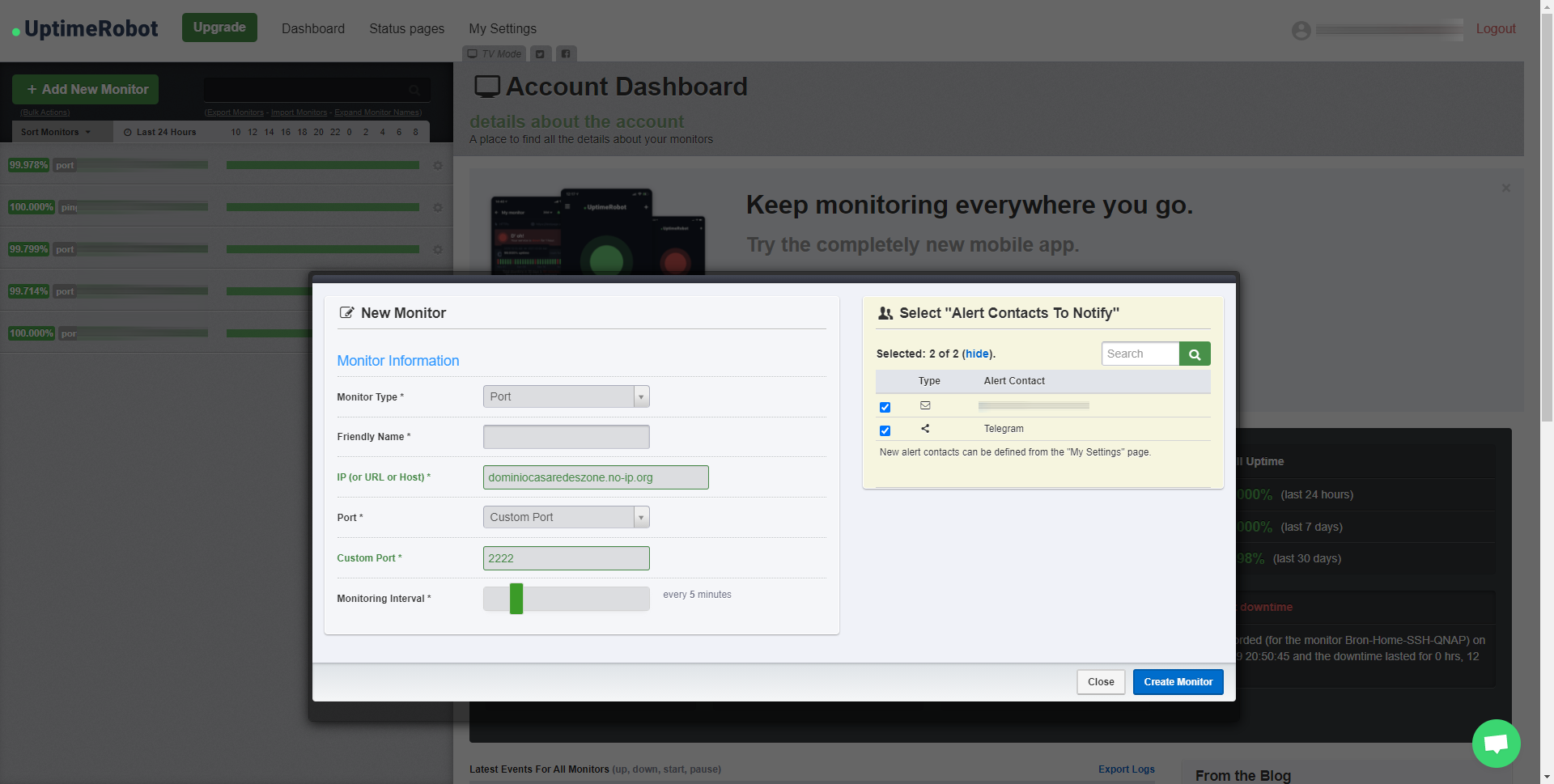
Once we have finished, we click on «Create Monitor» and we will have UptimeRobot working. Now you must check in pfSense that you have received the packet correctly, checking the firewall logs in the WAN section, you can filter the logs by putting the destination port 2222 which is the SSH port, you can also check that the source IP address is inside of the range of IP addresses that we have indicated previously.
Can I limit SSH connections to only UptimeRobot?
If you want to enable the SSH server only for the UptimeRobot addresses, in order to check if the Internet connection works well, you can limit the SSH connections through the rule in the firewall. If we go to ” Firewall / Aliases ” you can create an alias with all the source IP addresses of UptimeRobot, to greatly facilitate the configuration of the rule. We can put the URL with the text file that we have provided previously, and we put it directly in the URL Aliases (IP):
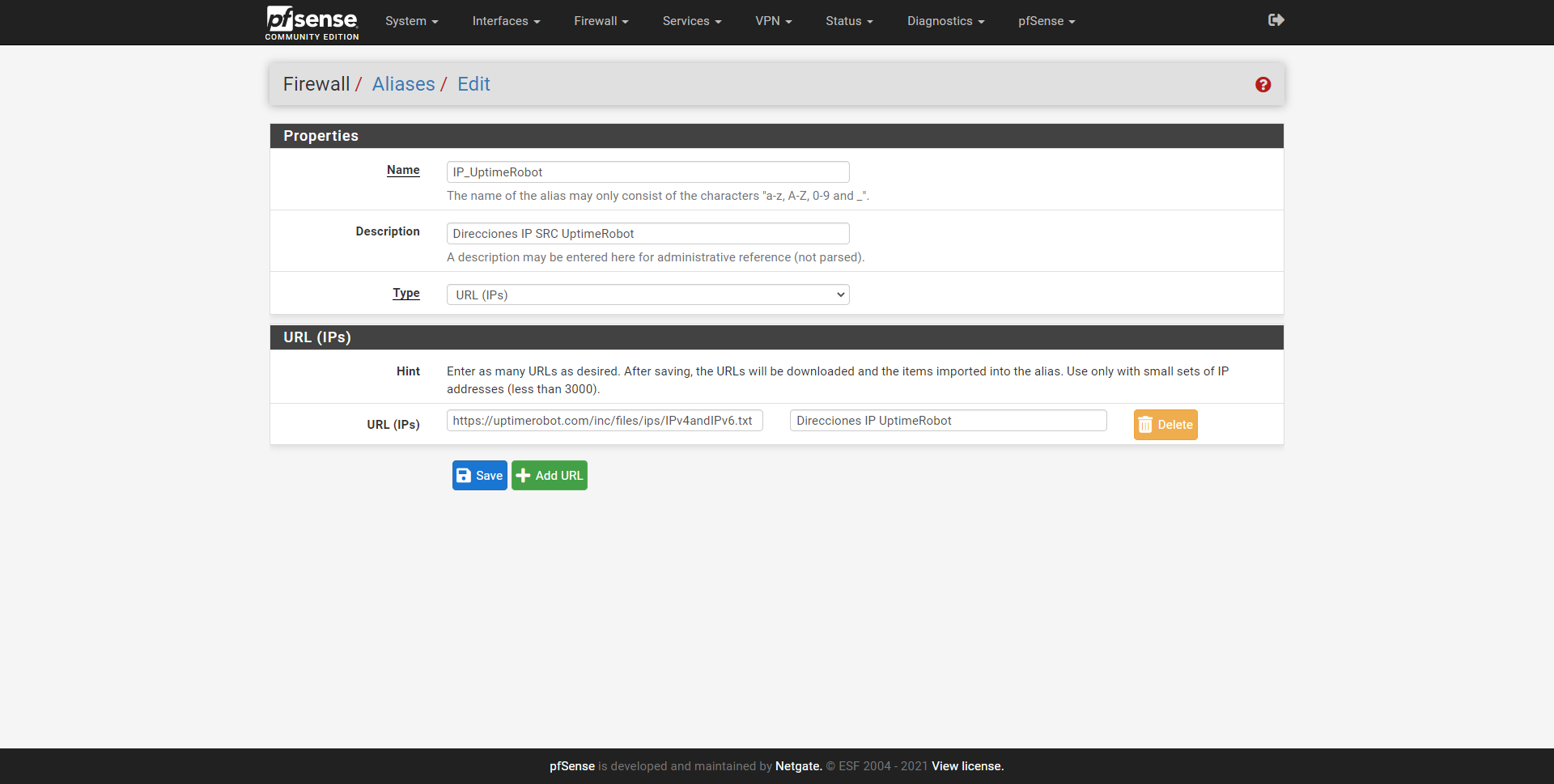
Thanks to this, we will be able to incorporate all the IPv4 and IPv6 addresses automatically and without having to go one by one, to greatly facilitate the configuration. As you can see, in the Aliases / URLs section these public IP addresses of origin used by UptimeRobot will appear already loaded:
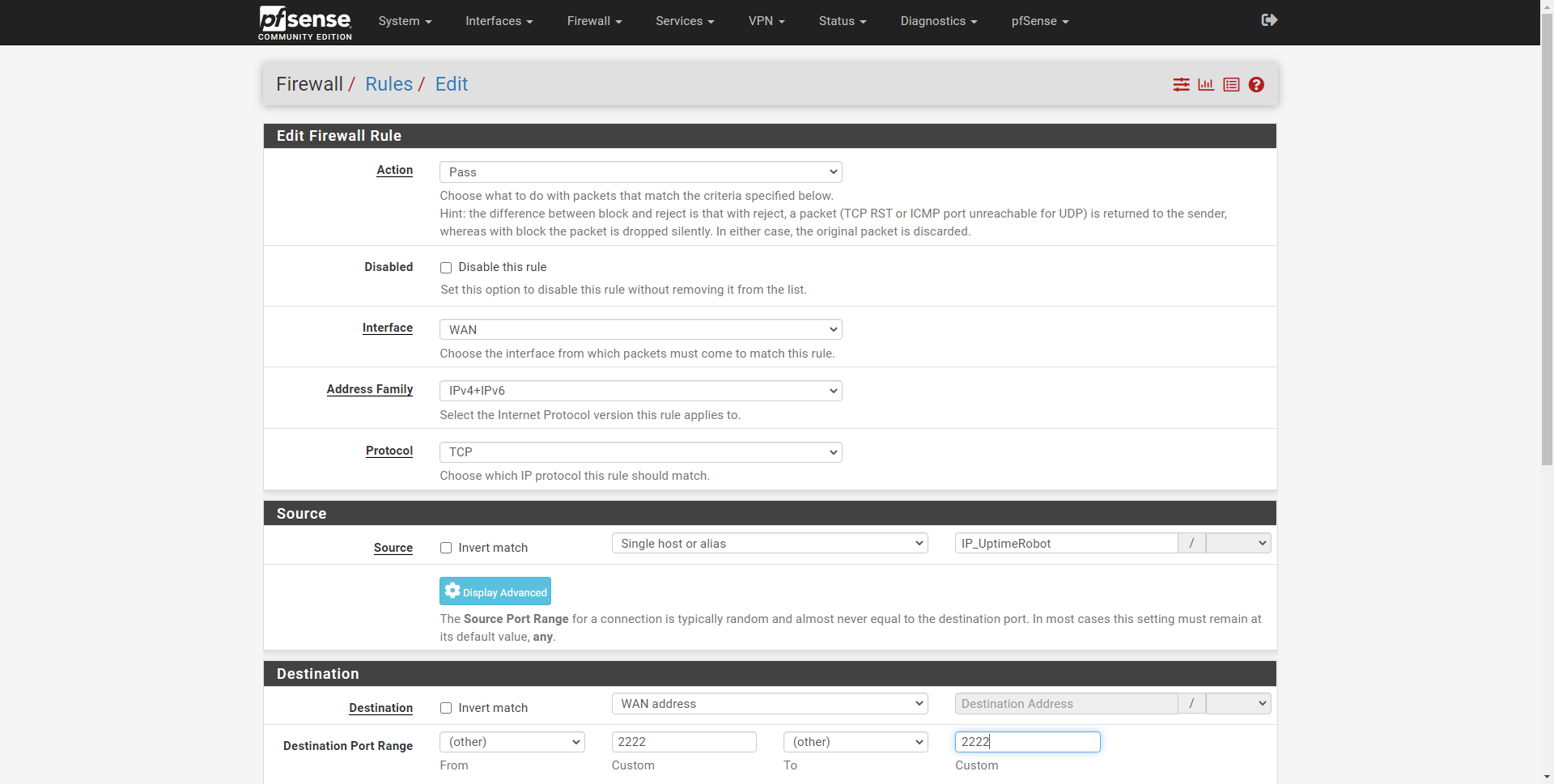
Now we would have to edit the SSH rule, and define:
- Address Family: IPv4 and IPv6, to also cover IPv6 addresses.
- Source – Single host or alias: IP_UptimeRobot
And we click on “Save” and apply changes. Right now, only the source IP addresses defined in the aliases, which correspond to the UptimeRobot IP addresses, would only have access to the SSH server, so as not to leave the SSH server exposed to everyone.
Thanks to UptimeRobot and a good configuration in pfSense to avoid false positives, you will be able to verify that the Internet connection works correctly and you do not have an incident. Of course, the most advisable thing is to put the dynamic DNS domain in the UptimeRobot itself, because if you have a dynamic public IP it will change from time to time, and you can get false positives of loss of connectivity.