Normally public Wi-Fi networks have captive portals to authenticate us, if we do not authenticate ourselves against these captive portals, we will not be able to access the Internet. If we are in a public place, cafeteria, hotel, restaurant or any other place with public Wi-Fi connectivity, it is very likely that captive portals exist.
These portals usually ask you for personal data such as full name, email, age, among other things, depending on where that network belongs. If you skip the captive portal, or close the authentication window, you will not be able to access the Internet, even if you have local connectivity. Today in this article we are going to show you the dns2tcp tool, which will allow us to avoid this type of captive portals, and have an unlimited Internet connection
It is good to remember that the DNS protocol fulfills the function of resolving the domain names that we want. This is extremely useful because, if it did not exist, in the address bar of our browser we should always write the IP addresses, and that is practically impossible to maintain. In this guide, we will specifically talk about DNS tunnels that will help us bypass access limitations like firewalls and captive portals.

However, it is possible to launch these types of tunnels because the network administrator has not made the appropriate configuration settings to block it. A practical method to know if we can carry out the DNS tunnel is to enter the command line and execute the following:
nslookup www.google.com
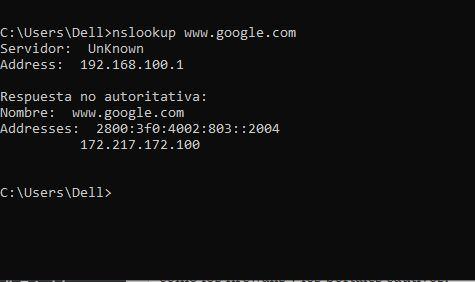
Press “Enter” and you will see data as in the shared capture. If so, you can launch the DNS tunnel. The first thing we will need is a tool called dns2tcp , this tool is used to establish DNS connections. Precisely, this will help us to ignore any captive portal that is configured on public networks.
The main condition for the tool to work correctly is that port 53 UDP is enabled by the firewall, otherwise it will not work and we will not be able to evade the captive portal or the firewall. Below, we will demonstrate the operating scheme to better understand how the captive portal barrier is avoided:
- When the dns2tcp client starts, the SSH secure resource is required through port 2222 using the TCP transport protocol. All TCP traffic that is generated is masked and takes the form of bogus DNS requests .
- Next, a SOCKS proxy is opened through port 1080.
- Those fake DNS requests are passed to the dns2tcp server which is responsible for unmasking them, and manages to send them to the original destination.
- When the destination responds to the request, that response first goes through the dns2tcp server to be encapsulated in a false DNS response .
- The masked response is passed to the dns2tcp client which uncapsulates it and finally passes it on to the user
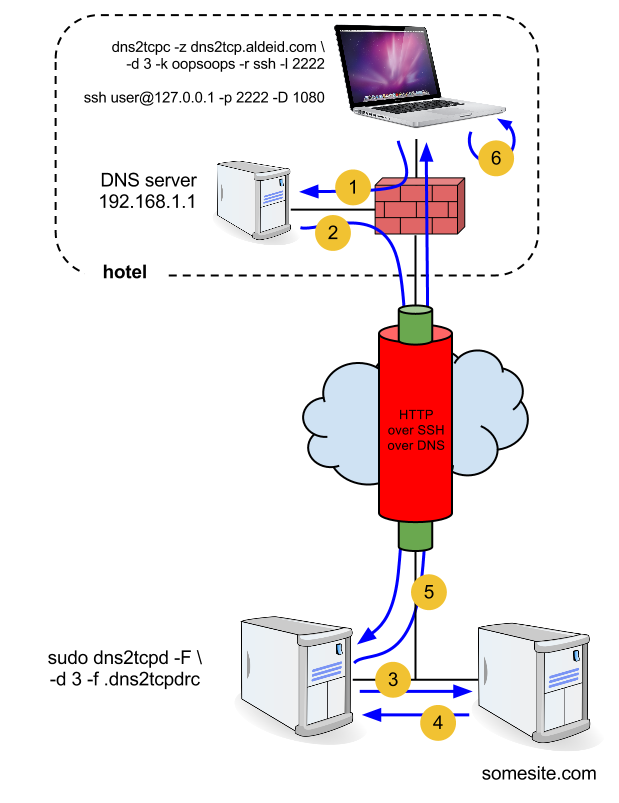
The end of this scheme is that said user can access the websites they want.
Ubuntu startup, installation and configuration on AWS
If we want to put this into practice, we need a server that has the dns2tcp tool installed and its own domain that must point to the server’s public IP (dns2tcp, too). We can use an extra computer that we have, or use more functional and economic resources such as a Raspberry Pi. To the latter, we could install the Linux distribution that we want, such as Raspbian among others.
However, opting for additional hardware represents an extra expense. So, we can choose free alternatives like Amazon Web Services . In this tutorial we will focus on the most important part of creating the DNS tunnel: the server where dns2tcp is hosted. If we don’t have this, there is no way to start.
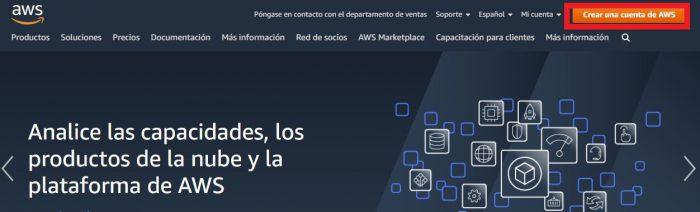
The first thing you should do is enter the AWS portal and create a free account. You can access multiple solutions for one year without paying a subscription. An important detail is that in one of the steps you must enter your credit card information, but don’t worry, there are no charges. Then go to My Account and select the AWS Management Console option.
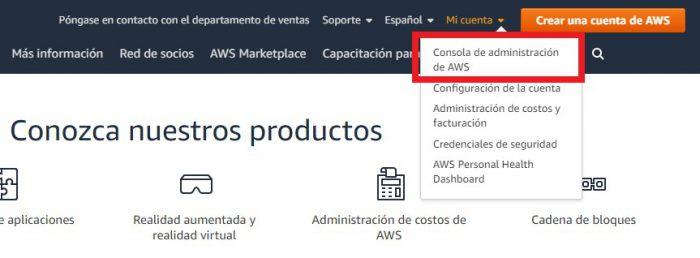
Among the multiple options that you will see, you will choose the first one that is EC2. Needless to say, EC2 is managed by instances . Those instances are like containers where the virtual machines we create are housed. They can be different versions of Windows Server or Linux servers. If you are interested in learning more, we suggest exploring the myriad of virtualization options.

It will take us to the dashboard dedicated to the EC2 service and we will go to Instances .
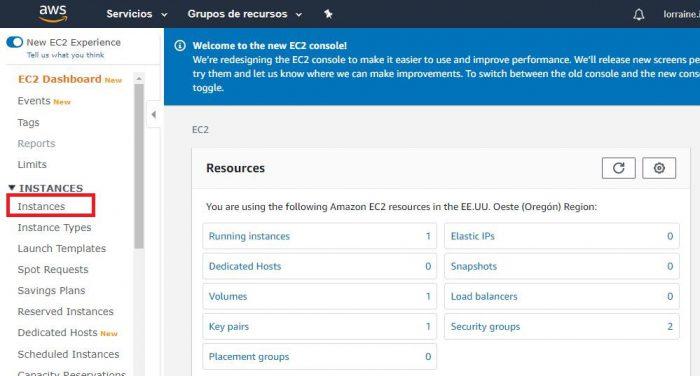
Let’s go to the blue Launch Instance button
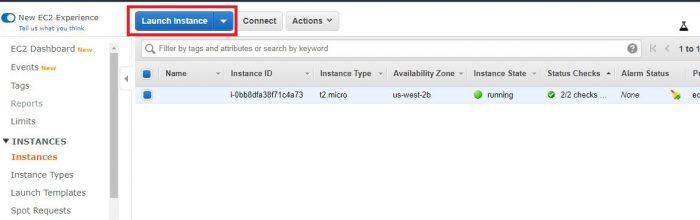
We now have a creation wizard for our instance . This is the instance that will contain our virtualized server, which in turn will host the dns2tcp tool.
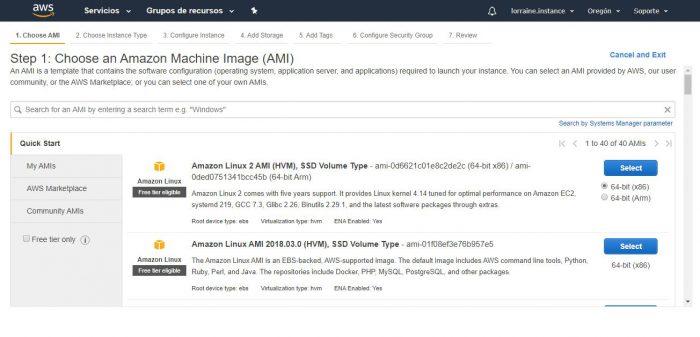
In this case, we will choose an Ubuntu Server and we will not worry so much about the version to use. Since we are only testing. Then we click on the blue Select button.
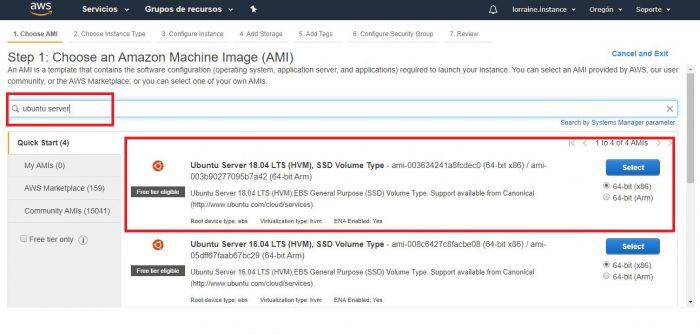
We choose the option that is eligible for use with the free plan (the one with the label Free tier eligible) .
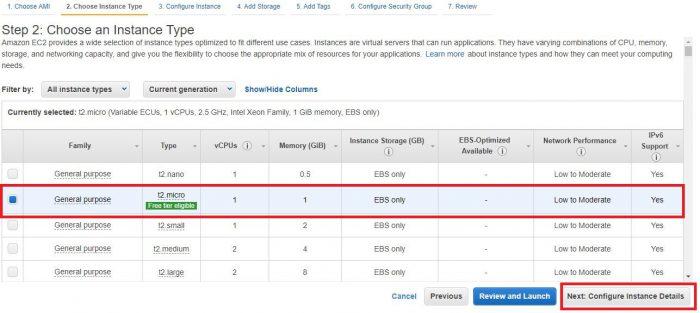
Later on, steps will appear that we don’t need to pay attention to this time. However, we will get to step 6 (Security Groups) and add a new rule that will allow the creation of DNS tunnels: the DNS protocol (UDP)
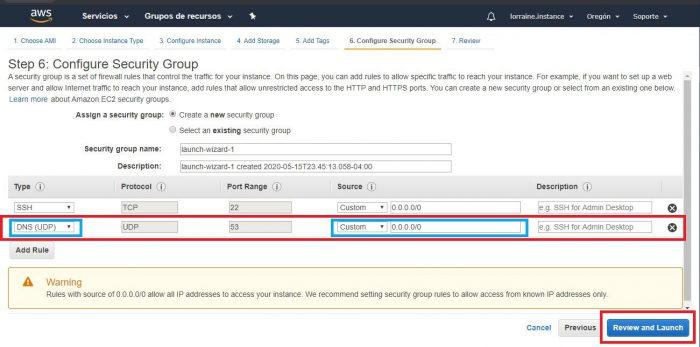
Once we choose that option it will automatically indicate its port number, which is 53. Where it says Source we can indicate the Custom option and next to it we put the IP 0.0.0.0/0 . Then click Review and Launch .
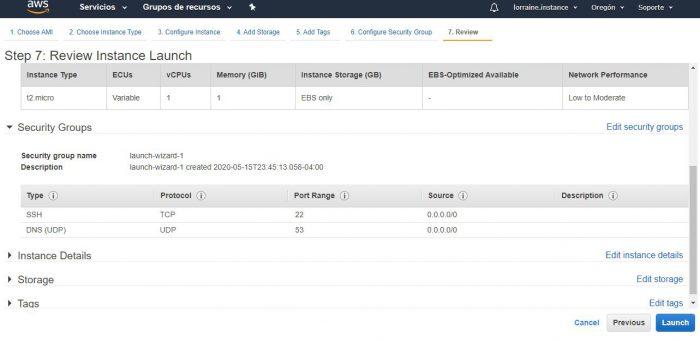
A final revision step will appear and you must click Launch . As we will see below, in reality, this is not the last step. What we will do now is generate the key pair (consisting of a public key and a private key) that will allow us to connect securely to our instance that we just created.
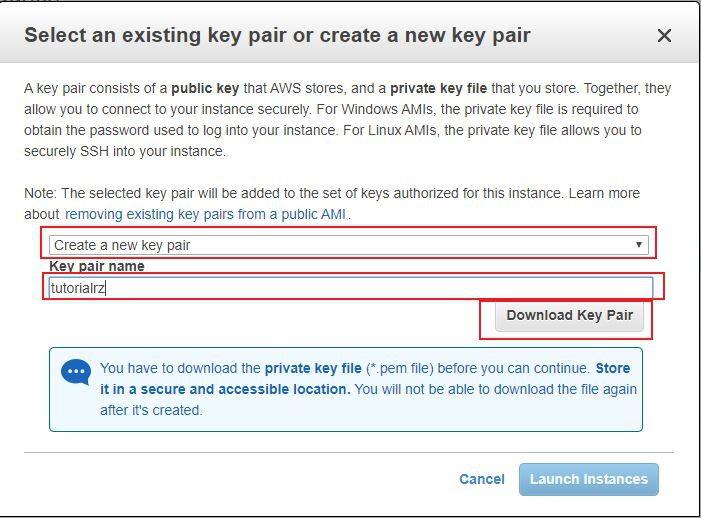
In this step you must select the Create a new key pair option so that it can provide us with a new key pair. Where it says Key pair name , we indicate the name of the pair that we want. We recommend using a name that we can easily recognize the file when we search for it. Something very important that indicates there is that the file will be generated for a single time, so it is convenient to save it in a location on the computer that is safe and that we can remember. Then we click Download Key Pair to download the file and Launch Instances
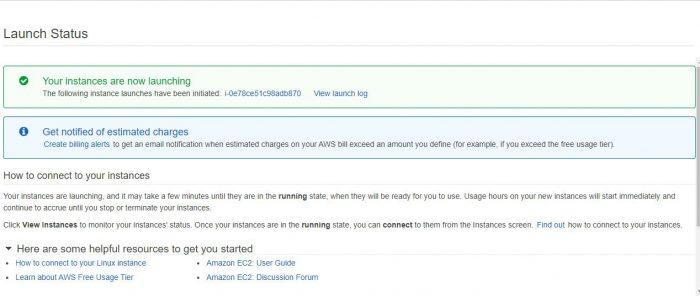
After a few minutes, you will verify that the status of the newly created instance will be ready to launch it and, therefore, have access to our virtualized server. What is highlighted in red is what will warn you if you can already launch your instance. If it appears as it is as the example capture, you can start. You must select the instance you have created and click on the Connect button.
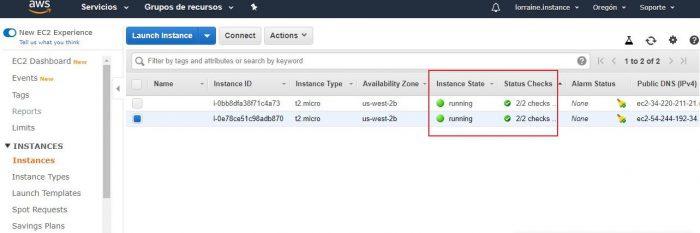
A window will appear that will give you options to connect to your instance. In this case, we are going to demonstrate how to connect using an SSH client. Therefore, we will need a program called PuTTY .
Install PuTTY in seconds
In order for us to connect to our Ubuntu server that we had created using the AWS instance, we will need this program. Specifically two, PuTTY and PuTTY Gen. Access this link and look for both programs, they are quite light and do not require too many installation steps.
Now let’s go to PuTTY Gen , this tool will help us convert the key pair file that we had downloaded when we finished creating our instance in AWS. To have a context of why we do it is that PuTTY supports key pair files in .ppk format, once we have done the conversion, this file will help us to connect via SSH to our virtual Ubuntu server.
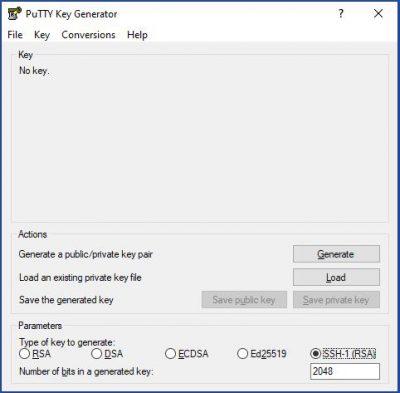
At Parameters , we choose the RSA encryption algorithm that is used for SSH-2. However, nowadays it is recommended to create SSH keys with Ed25519 or with ECDSA since they are the most secure. Then, in Load , we are going to look for the .pem file that we had created earlier in AWS.
When we want to open the file, make sure it is possible to view all the files and avoid problems finding it. You open it and in seconds, you will see a notice that it has been imported successfully:
You click OK and then you will click the Save private key button since this is the key that will serve to authenticate you and connect to your Ubuntu server. You will see a warning notice, but you can click Yes without embarrassment, name the file as you prefer and save it.
How to connect to our virtualized server with PuTTY
Now, let’s find the PuTTY program and we will have a window like this
As we have mentioned, we are going to connect using the SSH protocol. What we need to do to avoid doing the next step over and over again is to fix our generated private key file with PuTTY Gen so that we can connect successfully whenever we want.
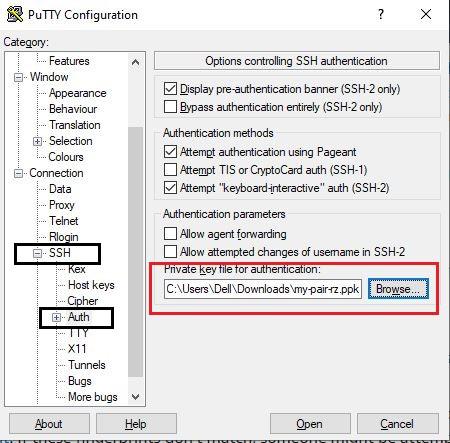
We look for the SSH section that is in Category , then Auth and where it says Private key file for authentication we upload our .ppk file that we have just converted to PuTTY Gen. We go back to AWS and look for the instance we just created, select it and click Connect . Once again, the window that we have seen above appears and we copy the information mentioned in step 4 , which is our public DNS.
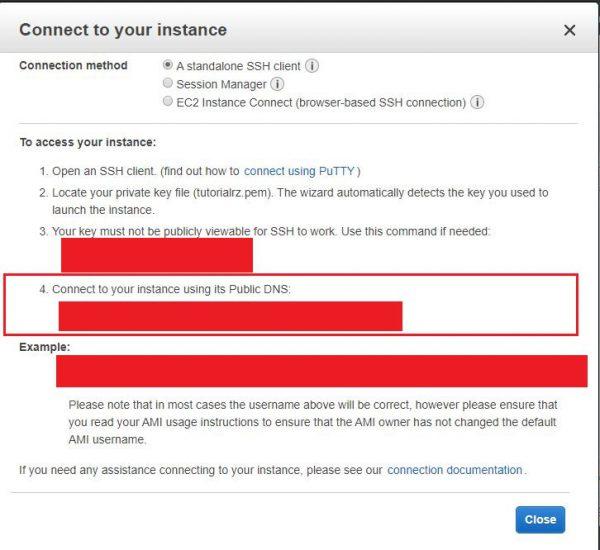
We go to PuTTY and in the Session section, in the Hostname field we put the following:
nombredeusuario@DNSpublico
As we virtualize an Ubuntu server, in user we simply write ubuntu in lowercase followed by @ and the public DNS that we copied before, without spaces
ubuntu@dnspublico-ABC-123-dEf
We keep port number 22 , in Saved Sessions we put any name to record our connection to the Ubuntu server, we click Save to record it and then click Open .
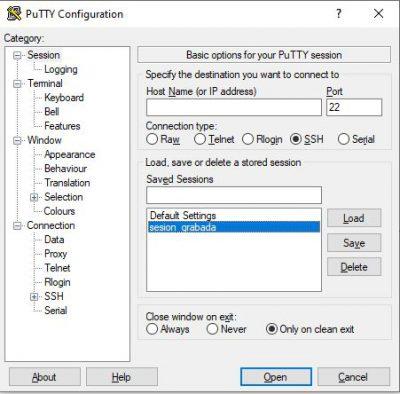
For the first time, you will see a warning and you must click Yes :
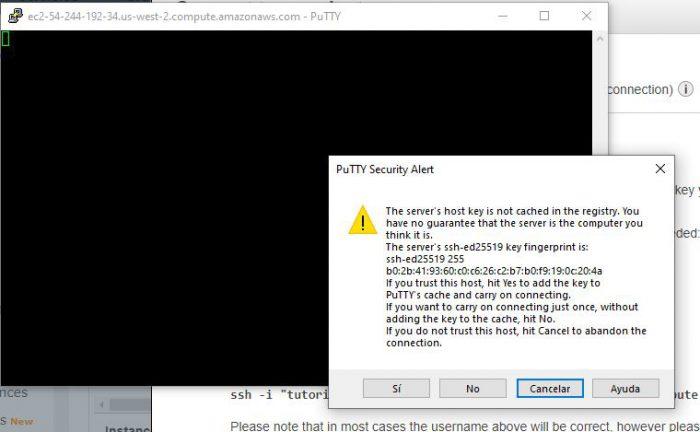
And ready, wait a few seconds for the connection to start and we will see a window like this. We have access to our virtualized Ubuntu server!
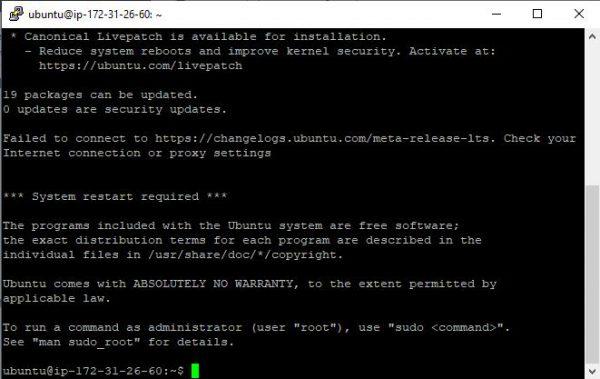
Once we have the virtual machine created in AWS and we have connectivity via SSH, all we need to do is use the dns2tcp tool itself.
Installation and configuration of dns2tcp in Ubuntu
The first thing we will have to do on our Ubuntu server is to install the dns2tcp tool:
sudo apt install dns2tcp
Once installed, both on the client and on the server, we will have to make some small adjustments.
Configuration and start the dns2tcp server
We will have to make a brief configuration by editing the configuration file that is located in /etc/dns2tcp.conf and that contains the following:
root@debian-vm:/home/bron# cat /etc/dns2tcpd.conf
listen = 127.0.0.1
port = 53
# If you change this value, also change the USER variable in /etc/default/dns2tcpd
user = nobody
chroot = /tmp
domain = your.domain.tld
resources = ssh:127.0.0.1:22 , smtp:127.0.0.1:25
root@debian-vm:/home/bron#
We have to edit it as follows:
listen = 0.0.0.0
port = 53
# If you change this value, also change the USER variable in /etc/default/dns2tcpd
user = nobody
chroot = /tmp
domain = EL_DOMINIO_DE_AWS
key= redeszone
resources = ssh:127.0.0.1:22 , smtp:127.0.0.1:25
root@debian-vm:/home/bron#
The “key” field is optional, but it is recommended to have an authentication to prevent anyone from connecting. We must execute it in the following way:
root@debian-vm:/home/bron# sudo dns2tcpd -F -d 3 -f /etc/dns2tcpd.conf
18:52:08 : Debug options.c:97 Add resource ssh:127.0.0.1 port 22
18:52:08 : Debug options.c:97 Add resource smtp:127.0.0.1 port 25
18:52:08 : Debug socket.c:55 Listening on 0.0.0.0:53 for domain your.domain.tld
Starting Server v0.5.2...
18:52:08 : Debug main.c:132 Chroot to /tmp
16:52:08 : Debug main.c:142 Change to user nobody
Once this is done, we would only have to connect with our client.
Client configuration to connect via dns2tcp
The easiest way to connect is to run a command line that has everything you need, then you can see in detail which is to connect and automatically create the socket for SSH on port 2222.
dns2tcpc -z EL_DOMINIO_DE_AWS -k redeszone -r ssh -l 2222
Now, we can make the connection with SSH in the following way and the communication will be encrypted and authenticated:
ssh bron@127.0.0.1 -p 2222 -D 8080
Finally, we will have to configure the PROXY SOCKS in our browser, for example, in Firefox it would be as follows:
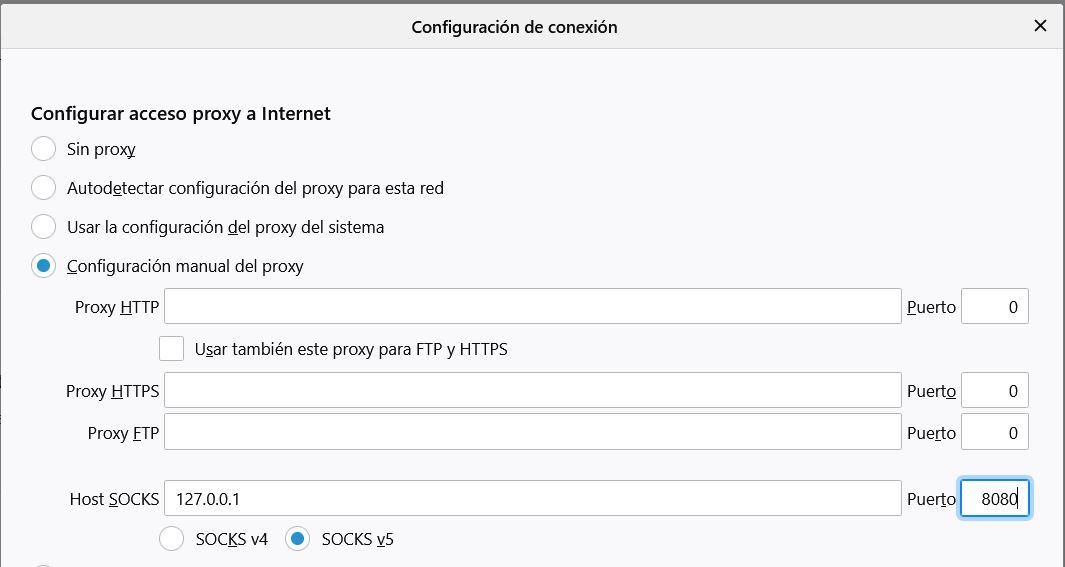
In this way, you will be able to skip captive portals and it is possible that they will also have firewalls, as long as they do not have specific blocks that prevent this technique from being performed.