A port scan can reveal valuable information about our local network and the services we have running on that local network. Therefore, by checking the open UDP ports on our router, and on certain hosts on the network itself, we can get a general idea of how that network is. In this way, a cybercriminal could know if we have a server on it or find an open port through which to violate our security.
Why it is very important to check open UDP ports
There are very important protocols that use UDP ports to communicate, some of these protocols are the popular DNS (Domain Name System) protocol and also the SNMP (Simple Network Management Protocol) protocol. Both protocols use DNS ports by default that we must close if we are not using them, and we should even control them if we are using these protocols.

Securing the DNS protocol
DNS servers usually use UDP port 53, although we also have the possibility of using other ports such as TCP 53, and even if we use DNS over HTTPS or DNS over TLS, the ports are different and governed by TCP instead of UDP . UDP port 53 is widely used to receive DNS requests, and to respond to them, it is essential that, if we do not have a DNS server activated, we block any type of incoming communication that uses this port through the firewall, since we could be facing a port scanning to try to get very valuable information to later attack said server.

In case of having the DNS server configured, it is very important to also protect it correctly with the firewall, to avoid DoS attacks that could cause the DNS server to stop responding, with the firewalls we could limit the number of requests per second that we can receive, discarding all the others, and even making “bans” of IP addresses so that they do not send us more information.
A really useful tool to protect the DNS server from DoS attacks is Fail2ban . This tool helps us to analyze the real log of the process, and depending on the log, it will be able to detect possible denial of service attacks to later block those source IP addresses in the firewall. In this way, Fail2ban protects the DNS server in a reactive way, as soon as it detects a traffic higher than “normal”, it will automatically tell the firewall to block any request from a certain source IP, leaving the DNS server available for the rest of equipment.
DHCP also uses the UDP protocol, it must be protected
Another widely used protocol is the popular DHCP (Dynamic Host Control Protocol) protocol, a protocol that dynamically and automatically provides us with private IP addresses on our local network. This protocol makes use of UDP ports 67/68 for receiving and sending information. A possible attacker could continuously send us DHCP Discover in order to saturate the DHCP server, or directly scan the network in search of the DHCP server to find out what version of the process we are using and if there is any known vulnerability to later exploit it.
As a recommendation, if we are not going to use the DHCP server, it is best to disable the process, and if we do use it, we must make sure that we always use the latest version available and that it is free of vulnerabilities.
How to protect the SNMP protocol and prevent attacks
Another widely used protocol in networks is the SNMP protocol . This SNMP protocol is in the application layer and allows the exchange of management information between network devices, in addition, the SNMP protocol is not only in PCs, but also in almost any network device such as routers, manageable switches, servers , printers, modems and even VoIP phones. Thanks to this protocol, network administrators will be able to monitor if there is any type of problem, using monitoring systems such as Nagios, Icinga2, Zabbix among many others that exist, and not only allows to see the configuration and monitor the status of the entire network, It also allows remote configurations.
Due to the very nature of SNMP, it is very likely that this process is working with administrator permissions on a server, PC or on your router, since, if SNMP allows the configuration of a host to be changed, it is mandatory that it has permissions to it. Currently there are two widely used versions of SNMP, the SNMPv2c that we can find in most devices such as routers, manageable switches, modems and VoIP telephony, and also the SNMPv3 version that we find in these same devices as long as their firmware supports it. The SNMPv3 protocol adds a large number of security measures, incorporates authentication with data encryption, and all communications are encrypted point-to-point to guarantee confidentiality, previously with the SNMPv2c protocol all data traffic is done in clear text.

The first thing we have to take into account to adequately protect SNMP is that, if we are not going to use it, the best we can do is disable the process, another option is to block the corresponding ports of UDP 161 and UDP 162 completely on the firewall. With these two actions, we will prevent any type of vulnerability found in the SNMP service from being exploited, since the first thing an attacker will do is perform a port scan and check if the SNMP service is active. In addition, we must not forget that, even if the SNMP is in read-only mode, it is possible to receive a denial of service attack if this protocol is not well implemented, as it happened in the Cisco IOS operating system years ago.
Another security measure that we can take is to only respond to the IP addresses that we define, however, UDP is a non-connection-oriented protocol, so performing an IP spoofing is really easy, so this option is a added more and not a complete solution to take. If you use SNMPv3, you will be protected against this possible attack.
At the firewall level, if you use iptables or other firewalls, we can create a couple of rules to limit access to the SNMP server of our equipment, and also limit the output of information to another IP address.
$ iptables -A INPUT -s <direccion ip> -p udp -m udp --dport 161 -j ACCEPT
$ iptables -A OUTPUT -d <direccion ip> -p udp -m udp --sport 161 -j ACCEPT
Of course, in the case of using versions lower than SNMPv3, all communications go unencrypted, although we do have authentication for reading and writing in the different hosts, for this reason, it is highly recommended not to have any access to the management network computer as it could perform a Man in the Middle attack and capture RW SNMP access credentials. Properly segmenting the network into VLANs is something fundamental and that we must not neglect in the design and security of the network. With the SNMPv3 protocol we will have good authentication and encryption with cryptography, but it is susceptible to brute force or dictionary attacks to guess the authentication keys, especially if these keys are short in length, so it is advisable to use long keys. Finally, a very good security recommendation is to use SNMP within an SSH tunnel or directly within a VPN tunnel, whenever this is possible, of course.
The same Fail2ban program that we have previously recommended is also capable of correctly protecting the SNMP protocol against possible DoS attacks carried out by an attacker on the network.
How to check the UDP ports that you have open from the Internet
To check the open UDP ports, the easiest way is to enter a specific website using our usual Internet browser. In this case we recommend doing this port test . In the case of accessing from outside (outside our local network), it is advisable that we first point our public IP using the web which is my IP .
Once we have entered the port test, the first thing to do is put our public IP address if we access from outside. Then we add the port or ports that we want to check. This tool allows you to check port ranges and also use comma separated ports. This time we have chosen the FTP protocol and then we have clicked on start .
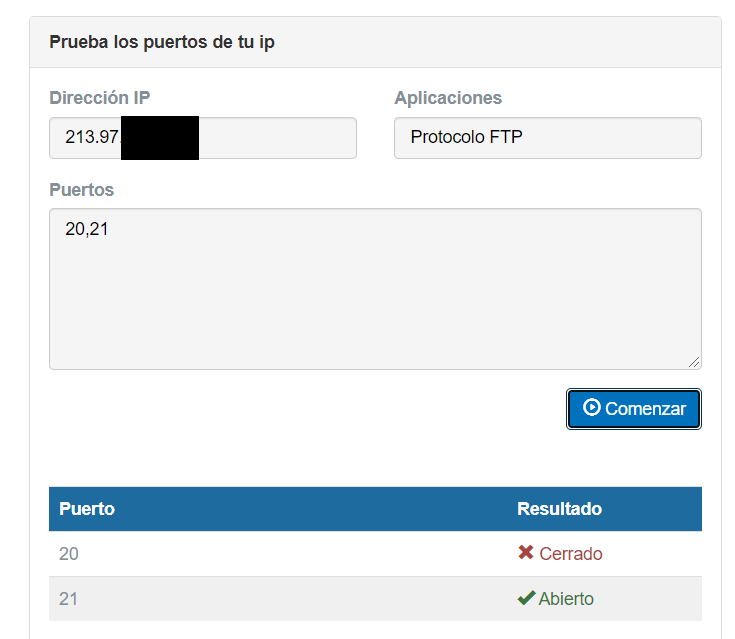
The information reveals that we have port 21 open. This means that, for example, we could have an FTP server generally used to share files with the outside. However, if we don’t have one, the best we can do is close it. This way we avoid a possible attack using that port.
How to check the ports that you have open from LAN
If you are on the local network and the ports are not open to the Internet WAN, although they cannot be accessed from the outside, vulnerabilities could be exploited from the professional local network itself. One of the most popular programs to perform port scans is Nmap, the scan with the UDP protocol is activated with the -sU option, and if we want to perform the scan with UDP and TCP at the same time, we can add -sS also to verify both protocols simultaneously. Simply by executing the following command, we will be scanning all the UDP ports of a certain host:
nmap -sU -v <direccion ip>
Depending on what Nmap receives, it will detect if the port is open (there is a reply), if it is open and filtered (no response is received), if it is closed (if it returns an ICMP type 3 port unreachable error) or filtered (if it receives another ICMP error type).
Starting Nmap (http://nmap.org)
Nmap scan report for 192.168.1.1
(The 997 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
53 / udp open | filtered domain
67 / udp open | filtered dhcpserver
111 / udp open | filtered rpcbind
MAC Address: 00: 01: 02: 03: 04: 05 (this article Router)
Nmap done: 1 IP address (1 host up) scanned in 100.25 seconds
As you have seen, it is also very important to properly protect the UDP ports, since they are a very important vector and used by cybercriminals to violate the security of our network.