Nmap is the best host discovery and port scanning tool out there today. Nmap will allow us to obtain a large amount of information about the computers on our network, it is able to scan which hosts are up, and even check if they have any open ports, if they are filtering ports (they have a firewall activated), and even know what operating system is using a certain target. Do you want to know everything about Nmap and how to use it? In this article we explain everything you need to know about this tool.
Main features
Nmap is a completely free and open source utility, it allows us to discover networks and hosts, as well as perform security audits. This program is compatible with Linux, Windows and macOS operating systems, but in all of them it is used through the command line, although we have the possibility of installing ZenMap, which is the graphical utility of Nmap to do port scans through of the graphical user interface. If you do not want to fight with commands through the console, this graphical user interface could be useful for the first steps with this great program, however, when you have more experience, you will surely execute all the commands directly from the terminal.

Nmap allows us to detect hosts on a local network, and also through the Internet, in this way, we can know if these hosts (computers, servers, routers, switches, IoT devices) are currently connected to the Internet or the local network. This tool also allows us to perform a port scan to the different hosts, see what services we have active in said hosts thanks to the fact that it will tell us the status of their ports, we can know which operating system a certain computer is using, and we can even automate different tests pentesting to check the safety of the equipment.

Nmap has different types of port scanning, they can be through TCP segments, UDP datagrams or ICMP packets, in addition, it allows to perform scans in a hidden way so that they are difficult to detect by firewalls. Of course, we will be able to do port scanning on certain specific ports, between port ranges, IP address ranges, possibility of using TCP null, FIN, Xmas and ACK packets in addition to SYN, to locate open TCP ports.
Other features that this tool offers us is the possibility of making a complete network inventory, and even checking if a certain host or service is still up and running. This program was designed to scan a large number of hosts, therefore if you need to scan multiple targets you will have no problems. This program is very flexible, it incorporates dozens of advanced techniques to scan hosts and ports, in addition, it also allows audits through NSE (Nmap Search Engine), so it is really powerful.
Nmap has various states on the ports that will appear when we do a port scan. It is essential to know what each state of Nmap means, because with any port scan, it will return different states.
Port status with Nmap
- Open – An application is actively accepting TCP or UDP connections. The port is open and can be used, pentesters will be able to use this open port to exploit the system. It is the default state if we do not have a firewall blocking access.
- Closed : A port that is closed is accessible because it responds to Nmap, however there is no application running on that port. It is useful for discovering that a host is up, or as part of detecting an operating system. For the system administrator, it is recommended to filter these ports with the firewall so that they are not accessible. With regard to pentester, it is advisable to leave these ports “closed” to analyze later, in case they put a new service.
- Filtered : In this state Nmap cannot determine if the port is open, because there is a firewall filtering Nmap packets on that port. These filtered ports are the ones that will appear when we have a firewall activated. Nmap will repeatedly try to try to connect, which makes port scanning quite slow.
- Open | Filtered : Nmap does not know if the port is open or filtered. This occurs because the open port does not send any response, and this lack of response could be from the firewall. This status appears when we use UDP and IP, and we use FIN, NULL and Xmas scans.
- Closed | Filtered : in this state it is not known if the port is closed or filtered. This state is only used in IP Idle Scan.
Once we have seen the main features of Nmap, and the status of the ports that we have available, we are going to install and use it.
Download and install Nmap on any system
The first thing we have to do to use this powerful program is to download it and then install it. In the Nmap download section you can find all the links, binaries and source code for installation in Windows, Linux and MacOS operating systems. We currently have this program available in all the repositories of Linux-based operating systems, so its installation is really simple. We have installed this program in Ubuntu, but simply by executing the installation command of your operating system followed by “nmap”, you will install the program without difficulties.
sudo apt install nmap
Once installed we can use it from a terminal, either in Windows, Linux or macOS. In all the examples that we will give you below, we have used the Ubuntu operating system, but we have the same commands available for Windows and macOS, without any changes.
Nmap usage examples
Quick port scan
If you want to perform a quick port scan to a specific host, we must type the following command.
nmap [ip]
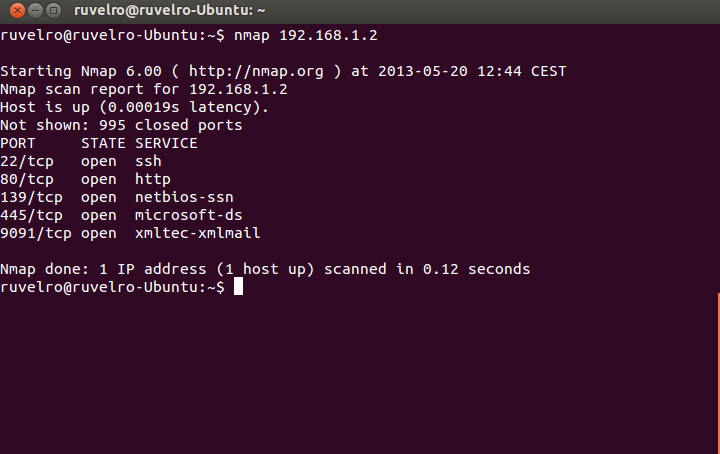
For example, if we want to perform a quick scan of the main ports to a host with IP address 192.168.1.2, the order would be the following:
nmap 192.168.1.2
The program will return the ports that are open on the target computer.
Scan a range of ports
Instead of scanning all ports, we can set a range of ports to check. For this we will execute:
nmap -p [rango] [ip]
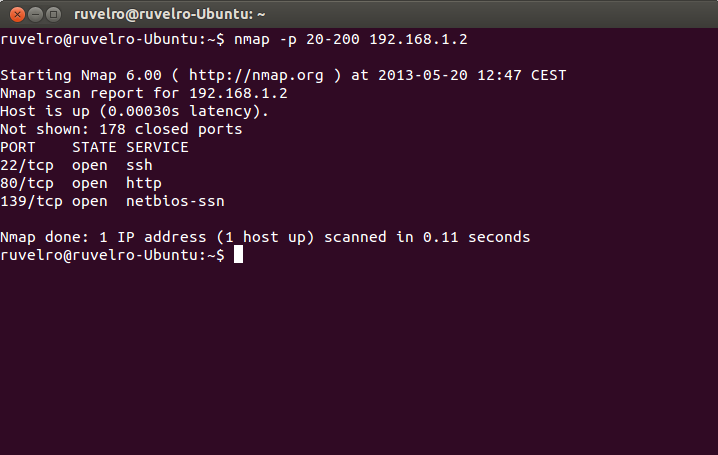
If we want to perform a port scan from TCP 20 to TCP 200 at the IP address 192.168.1.2, just execute the following command:
nmap -p 20-200 192.168.1.2
The program will indicate within that range which ports are open.
Detect operating system and more host data
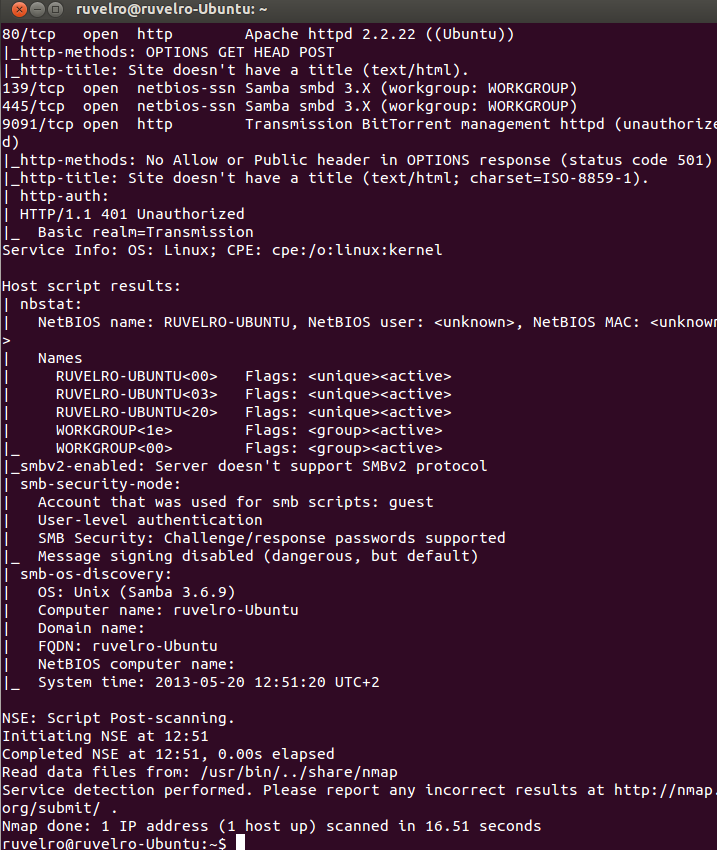
We can tell Nmap to detect the operating system. It does this by sending packets and analyzing the way it returns them, being totally different in each system. Along with this, it will carry out a port and service scan for vulnerabilities. Also, the scan will return useful information. For this we must execute:
nmap -A -v [ip]
If we want to perform this scan to the IP address 192.168.1.2 we can execute the following command:
nmap -A -v 192.168.1.2
List of all commands s
This program is really complete, so far we have used the basic commands to discover hosts and also to see if it has open ports, however, this does not stay that way, and we have a large list of commands to make the most of this tool.
Select objectives
IP addresses or ranges, names of systems, networks, etc.
- Example: scanme.nmap.org, microsoft.com/24, 192.168.0.1, 10.0.0-255.1-254
- -iL file list in file -iR n choose targets randomly, 0 never ends
- –Exclude –excludefile file exclude systems from file
Discover systems
- -PS n tcp syn ping
- -PA n ping TCP ACK
- -PU n ping UDP
- -PM Netmask Req
- -PP Timestamp Req
- -PE Echo Req
- -sL list analysis
- -PO ping per protocol
- -PN Do not ping
- -n don’t do DNS
- -R Resolve DNS on all target systems
- –Traceroute: trace route to system (for network topologies)
- -sP ping, same as –PP –PM –PS443 –PA80
Port analysis techniques
- -sS parse using TCP SYN
- -sT parsing using TCP CONNECT
- -sU analysis using UDP
- -s AND analysis using SCTP INIT
- -sZ using COOKIE ECHO from SCTP
- -sO IP protocol
- -sW TCP window -sN
- –SF -sX NULL, FIN, XMAS
- –SA TCP ACK
Ports to analyze and order of analysis
- -p n-mrango
- -p– all ports
- -pn, m, z specified
- -p U: nm, z T: n, m U for UDP, T for TCP
- -F fast, the common 100
- –Top-ports n analyze the most used ports
- -r not random
Duration and execution:
- -T0 paranoid
- -T1 stealth
- -T2 sophisticated
- -T3 normal
- -T4 aggressive
- -T5 madness
- –Min-hostgroup
- –Max-hostgroup
- –Min-rate
- –Max-rate
- –Min-parallelism
- –Max-parallelism
- –Min-rtt-timeout
- –Max-rtt-timeout
- –Initial-rtt-timeout
- –Max-retries
- –Host-timeout –scan-delay
Service and version detection
- -sV: services version detection
- –All-ports do not exclude ports
- –Version-all test each scan
- –Version-trace trace version analysis activity
- -Or activate detection of the Operating System
- –Fuzzy guess OS detection
- –Max-os-tries set maximum number of attempts against target system
Firewall / IDS Evasion
- -f fragment packets
- -D d1, d2 cloak analysis with decoys
- -S ip spoof source address
- –G source spoof source port
- –Randomize-hosts order
- –Spoof-mac mac change source MAC
Level of Detail and Debugging Parameters
- -v Increase the level of detail
- –Reason reasons by system and port
- -d (1-9) set debugging level
- –Packet-trace packet path
Other options
- –Resume file continue analysis aborted (taking output formats with -oN or -oG)
- -6 enable IPV6 scanning
- -A aggressive, same as -O -sV -sC –traceroute
Interactive options
- v / V increase / decrease level of analysis detail
- d / D increase / decrease debugging level
- p / P enable / disable packet trace
Scripts
- -sC perform analysis with default scripts
- –Script file run script (or all)
- –Script-args n = v provide arguments
- –Script-trace show incoming and outgoing communication
Output formats
- -oN save in normal format
- -oX save in XML format
- -oG save in format to later use Grep
- -oA save in all previous formats
These are mainly the commands available to Nmap. Before finishing, we must say that Nmap has a multitude of options with which to perform complete network analysis. We can consult all the available options by typing:
nmap --help
Nmap is undoubtedly a very simple and complete tool to perform network audits, but this does not end there, we also have Nmap NSE available to perform advanced pentesting.
Nmap NSE: what it is and what it is for
Nmap Search Engine or also known as Nmap NSE, is a large database with thousands of scripts that will allow us to automate pentesting to systems and networks. This set of scripts will allow us to automate many actions, such as carrying out brute force attacks on Samba servers, FTP servers, SSH servers, checking if a web server has a known vulnerability, and much more.
For example, if we want to carry out a brute force attack, based on a list of users (with a file called users.txt) and a list of passwords to test (with a file called keys.txt) to a SSH server of a certain computer that has the IP 99.99.99.99, we can put the following command:
nmap -p 22 --script ssh-brute --script-args userdb=usarios.txt,passdb=claves.txt --script-args ssh-brute.timeout=4s 99.99.99.99
We recommend that you visit the official website of NSE where you will find all the scripts that are currently in this large database, in addition, you will have examples of how to use them.