Every day thousands of devices are infected by malware, viruses and ransomware. What is not common is that the malware itself warns you that you are infected. And that is what has happened with TrickBot , which by mistake of its programmers warns you that you are infected.
As you can imagine, this is a serious error from the creator of the malware, but at the same time, it is also something positive for us since we can proceed to eliminate it using the appropriate tools. The programmers of the well-known TrickBot malware made a very serious mistake during their programming. The mistake is that they forgot to remove a test module that warns victims that they are infected and that they should contact their administrator.
The way TrickBot works is through a malware infection that is usually distributed through malicious spam emails. Once installed, the first thing it will do is run silently on the victim’s computer. Once done, the next step will be to download several modules that perform different tasks on the infected computer.
These modules that have been installed will allow malware to perform the following actions:
- Stealing the Active Directory Services database from a domain.
- Collect browser passwords and cookies.
- Steal OpenSSH keys and enable it to spread laterally across a network.
However, things can get worse because we know that you can do more. TrickBot will end its attacks by allowing access to ransomware such as Ryuk and Conti.
TrickBot programmers made an unforgivable mistake
Vitali Kremez of Advanced Intel analyzing a recent release of the TrickBot malware has discovered that the developers of the threat are mistakenly distributing a trial version of their grabber.dll module that steals passwords.
Once this module is installed, what it does is display a warning in the victim’s default browser. It indicates that the program is collecting information and that you ask your system administrator for more details. Here you have a recreation of what would appear on your screens.
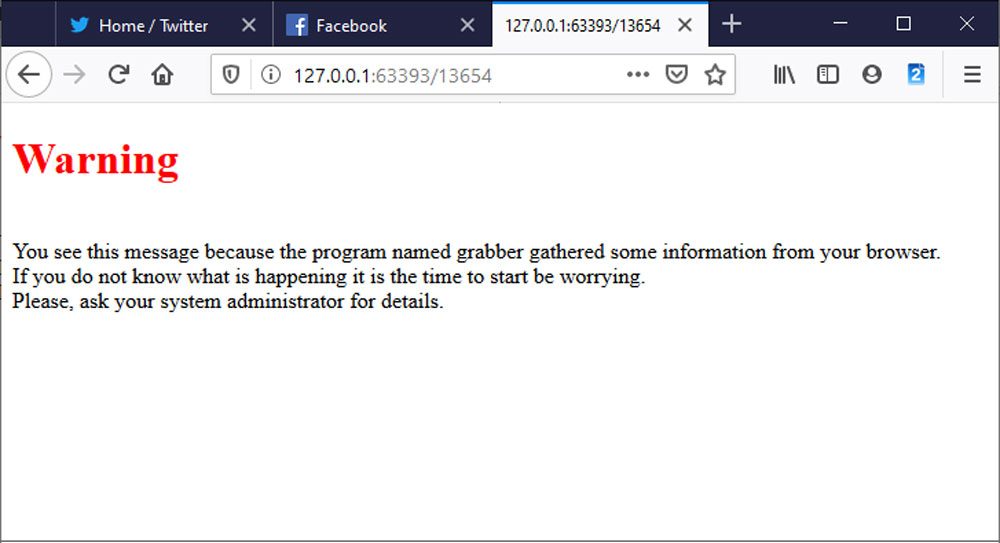
This case that we have discussed before is not an isolated case. A Reddit user asked just over fifteen days ago looking for a solution to his problem because his Firefox browser was warning him about a program called grabber.
In case you don’t know, Grabber.dll is the password for TrickBot and the cookie theft module. With it, what you are trying to do is collect the saved credentials and cookies from Chrome, Edge, Internet Explorer and Firefox browsers. Thanks to these stolen credentials and cookies, developers could use them to log into the victim’s accounts.
Kremez Research and Recommendations on TrickBot.
Kremez was able to extract the following documentation embedded in the module and that you can see in the following image.
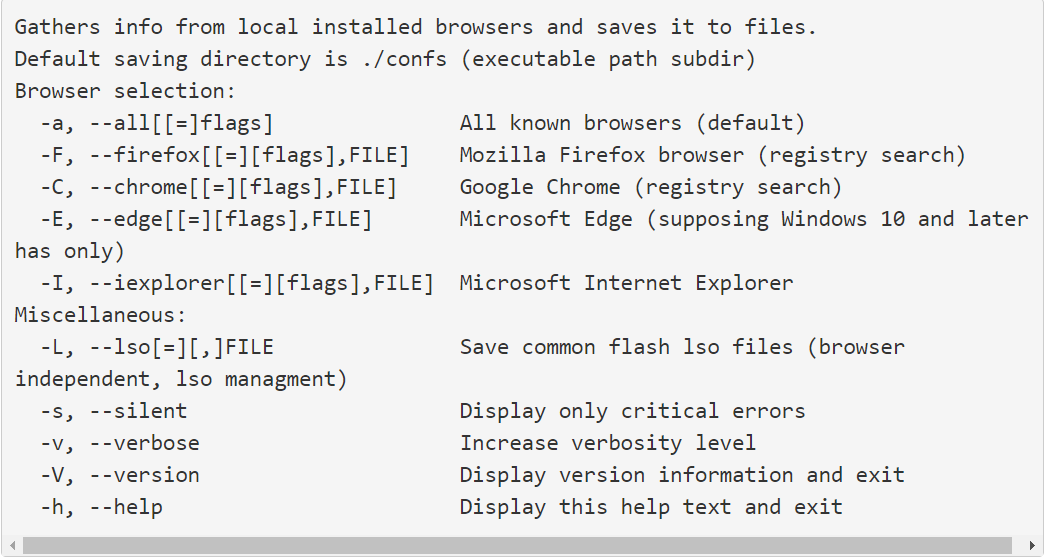
If you want to know a more detailed technical analysis of this grabber.dll module, Kremez has published all the information in a blog on the Advanced Intel website.
According to Kremez that test module appears to have been developed by the creators of TrickBot. The reason why you think this is because it is coded the same way as other modules. In addition, he also believes that the programmers of the threat were testing a new version and forgot to delete it when it was released.
If you see this TrickBot warning, the first thing Kremez recommends to victims is that they immediately disconnect their computer from the network. Then the next step they have to take is a scan with their security software installed.
Once the threat has been removed from your computer we must do more. Victims must change their passwords for any site, external or internal, whose credentials are saved in the browser. In addition we must also do the same with the passwords with which we log in to that browser.