The popularity of Telegram has not stopped growing in recent years. This year, the app surpassed 500 million monthly active users, where in the month of January alone it was downloaded 63 million times. Therefore, it is not surprising that there are hacking attempts taking advantage of the app.
Specifically, the use that hackers have discovered of Telegram is as a control system for their malware . The first time this type of use was discovered was in 2017, where the cybercriminals behind the Masad malware, which stole personal data, used Telegram to monitor malware activity on infected computers.

Antiviruses do not detect malicious activity on Telegram
Telegram, being a legitimate application, is not detected by antivirus . Hackers can operate anonymously by simply registering a mobile phone. With the app, all types of files can be sent quickly, or new malware can be downloaded onto infected devices. This malware is widespread in the hacking community, and its code has since been used by dozens of new types of malware.
The most recent, ToxicEye , has caught the attention of Check Point Research researchers, who have detected 130 attacks by this remote access Trojan. It is spread through phishing emails, containing .exe files. If the attachment is opened, the malware runs to steal data, delete or transfer files, shut down processes on the computer, capture webcam image and microphone sound, and encrypt files to carry out ransomware attacks.
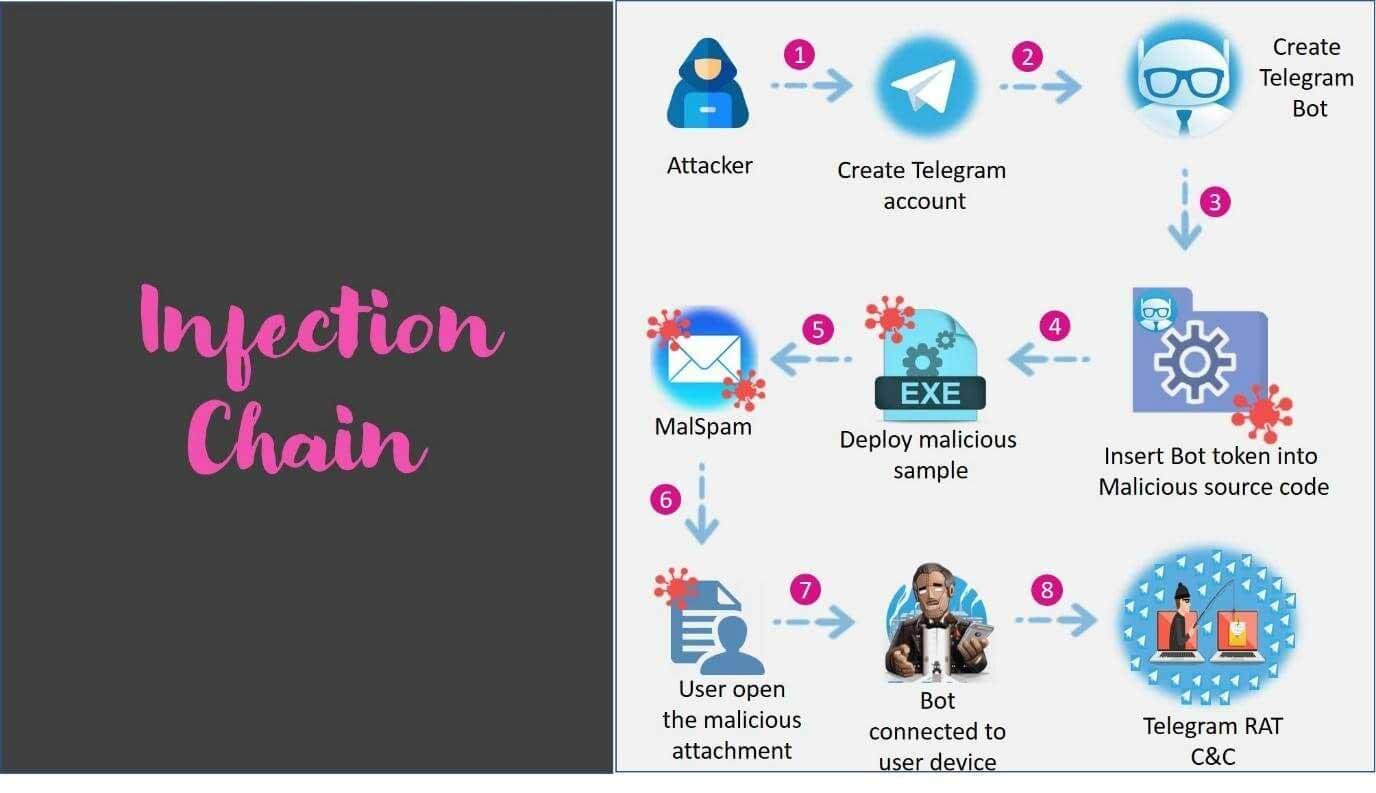
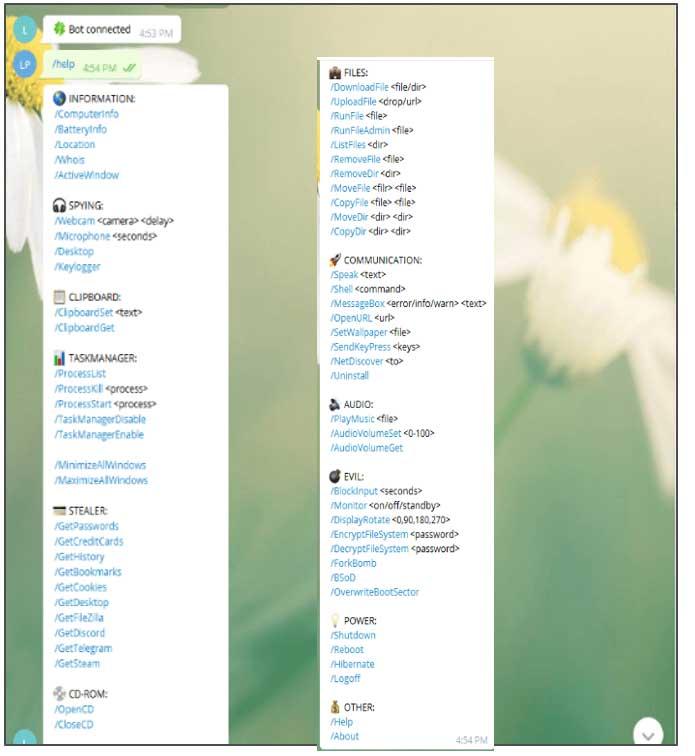
To carry out the process, the attacker creates a Telegram account and a bot , which he uses to control the computer remotely. In the following image we can see all the capabilities that the Telegram bot has, even copying the content of the clipboard, capturing images from the webcam , or being able to obtain all the passwords from our computer. They can also spy on Telegram chats.
Be careful with the emails you receive
From CheckPoint they give a series of tips to detect if we are infected. First of all, we have to look at the path of C: /Usuarios/ToxicEye/rat.exe . If we have it, we have to run an antivirus immediately to delete it, and disconnect the computer from the Internet as soon as possible.
To initially avoid an infection, it is advisable to be careful with the emails we receive, where attackers sometimes do not bother to impersonate companies, but instead send emails with a hidden sender. In the case of text, there are always grammatical errors and numerous syntax problems.
In short, we have that Telegram, thanks to its excellent functionalities, has become a very comfortable tool for hackers, since they can obtain data from any infected computer and send it to them without leaving a trace and without being detected by antivirus as it is legitimate content. Thus, if this Trojan manages to bypass the antivirus and installs itself on the computer, we are completely lost.