Millions of employees of organizations around the world have migrated to remote work, therefore, organizations have mobilized in this regard to provide their systems with adequate security in their systems.
The chances of a cyber attack increase exponentially, and not only large organizations are targeted by cybercriminals, small and medium-sized companies are also targeted, as they tend to be companies with fewer security measures than the “big” ones.
Consequently, as a network administrator or computer security specialists, we must have the necessary tools to keep our infrastructure safe. Today in this article we are going to show you everything that Security Onion has, a complete suite of network audits completely free and open source.
It is a Linux distribution that is oriented to threat detection, security monitoring and log management. One of the most outstanding features of Security Onion is that it has multiple tools included by default, so we will not have to install anything or make life too difficult for its implementation. For example, you can access Elasticsearch, Snort, Zeek, Wazuh, Cyberchef and NetworkMiner among other tools. On the other hand, it is very simple to implement, because it has an installation wizard that allows this suite to start up in minutes.

One of the reasons why Security Onion should be considered for network and security audits is the ability to bundle multiple top network security tools into one package . This not only makes it easier to manage, but also makes it easier for organizations of all kinds to access a comprehensive solution. In other words, a complete solution that guarantees that those responsible for network infrastructure and security have the complete picture.
This suite not only contains reactive tools, such as incident response or forensic computer security. It also contains proactive tools that help us know what happens to our network. What vulnerabilities do you have with different vulnerability scanners , what ports are open unnecessarily and a long etcetera.
However, a very important aspect that is clearly reflected in your documentation is that this tool is not magic. Nor is it a tool that does it all for you, optimizing and automating network processes are undoubtedly a great benefit, however, we should take the time to learn about tool suites like this one. Also, get the most out of them.
What tools does Security Onion contain?
Now we will talk about some programs present in Security Onion. Some of the built-in programs are, for example, netsniff-ng , this tool captures all the information related to network activity. In addition, it adapts to the storage capacity of your infrastructure by deleting very old data in order to save space. Packet capture is useful for discovering vulnerabilities and suspicious events, only with packet capture is it possible to detect situations such as data leakage, phishing events, intrusion into network traffic and many more.
On the other hand, it has tools for intrusion detection and prevention systems (IDS / IPS). On the one hand, it has rules-based tools, which are Snort and Suricata , these two tools work based on rules, which help to detect intrusions for subsequent blocking by the firewall. So what happens is that the tools detect such intrusions and cross-reference their systems’ “footprints” in their databases, thereby effectively detecting any evidence of irregular network traffic.
On the other hand, it has an analysis-based IDS / IPS tool like Zeek . It is responsible for monitoring activity on the network, in addition to collecting connection records, DNS requests, network services and software, SSL certificates, etc. Likewise, it collects activity logs from HTTP, FTP, IRC, SMTP, SSH, SSL and Syslog protocols.
One of the advantages of this tool is that it can analyze event data in real time. A very interesting example cited by its documentation is that you can import information into Zeek, which can later become a script that has the ability to read csv files (file separated by commas) that contain data from collaborators of an organization, and that is Cross paths with activity logs such as Internet file download events, logins, etc. In this way, Zeek becomes a bridge to be able to feed other tools such as antivirus, antimalware, SIEM and more, so that action against security threats is more direct and effective.
Wazuh is another IDS tool available, its distinction is that it is based on hosts. The latter means that it is installed on endpoints , that is, on each user’s computers. For your peace of mind, this tool is compatible with both Windows, Linux and mac OS. With Wazuh you will have a complete overview of each host that is active on the network. It is capable of analyzing the event logs of each host, in addition to file integrity reviews, network policy monitoring and rootkit detection. Its effectiveness becomes even more proactive thanks to the alerts issued in real time and its actions in the face of threats.
As we can see, it is important to have this variety of IDS / IPS tools as it helps the successful identification of cyber attacks. Added to this is the possibility of knowing the exact origin of them, so our network infrastructure improves based on the information provided by these tools.
Data analysis tools
As it is possible to see, Security Onion has multiple sources to be able to generate data regarding the activity on the network. However, what can we do with this data? The best idea is to analyze them and you have 3 tools for this.
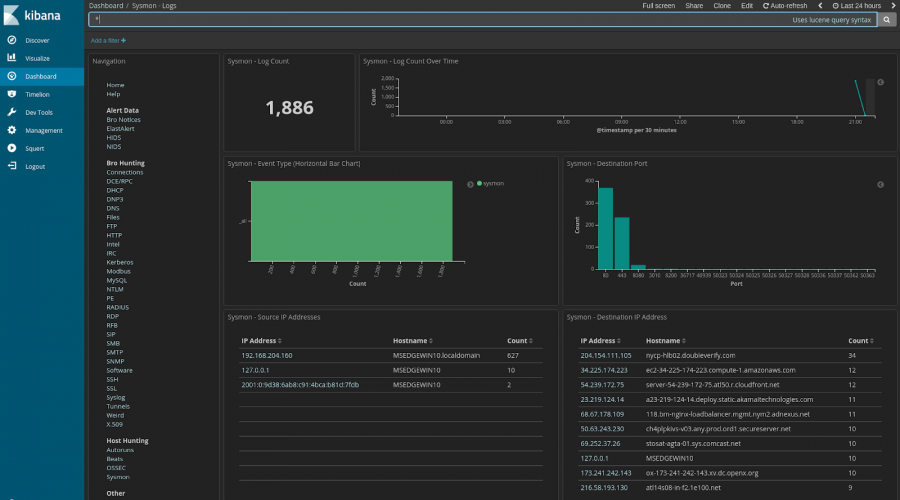
Sguil
It provides visibility with respect to all the data collected. It has a direct link to the tools mentioned above: Snort, Suricata and Wazuh. One of the peculiarities of Sguil is that it acts as a bridge between IDS / IPS tools and packet capture tools. The direct utility of this is that it is more effective in identifying the problem, what to do about it, who should do it and, according to the case, escalate it so that the right people can solve it in a timely manner.
It is easier to have an interface that promotes collaboration between members of the IT and / or computer security team. There is nothing more laborious than identifying a cyber threat and not knowing the reason or the origin. The person in charge who must review everything, may not know very well if the threat is internal or external, so this tool is very useful for this scenario.
Other tools available are Squert , Kibana and CapMe . Virtually all have the central objective of analyzing the multiple data that is generated from IDS / IPS tools and packet capture. Clearly, it is no longer feasible to spend too much time trying to get the most out of the data. If there are tools that can do it for us, nothing better than to opt for them.
How to start using Security Onion?
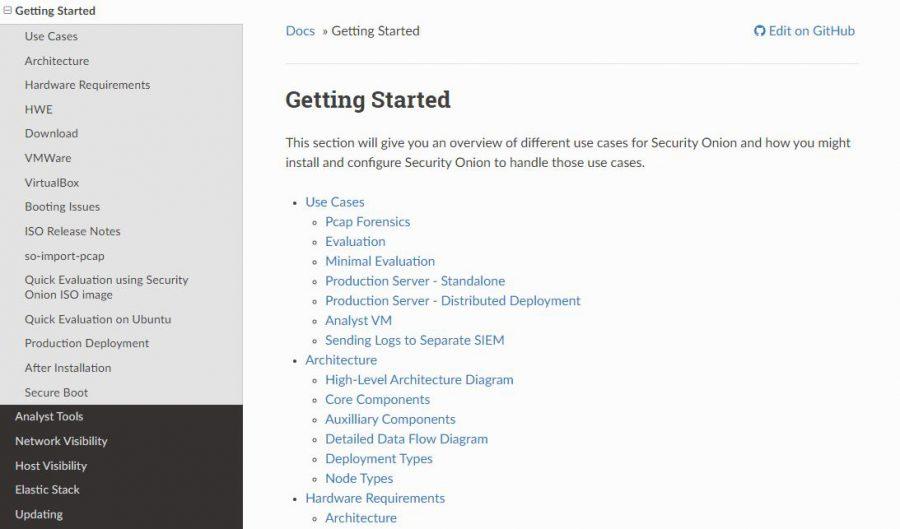
The first thing we have to do is access the download on Github so that you can start as soon as possible. However, it is highly recommended to enter the documentation website. The Getting Started section is characterized by being extremely broad and provides the user with multiple possibilities to get Security Onion up and running.
Don’t have a computer with a Linux distro? No problem, the documentation for this suite includes the possibility of virtualizing using solutions already known as Virtual Box and VMware. For either case, it gives you instructions on how to create the virtual machines from scratch, specifically to set up the Security Onion suite and start conducting network audits.
Another important aspect is that the documentation provides a cheat sheet (notes template) where’ll have the most important commands at a glance. For example, you will know what the maintenance tasks are in general. On the other hand, in the same template there is a summary of important files and the path of each one. This is extremely useful especially when we want to locate the logs of each of the tools in this suite.