We currently have a lot of free software available that we can test. However, while most are generally legitimate, they are sometimes used for illicit purposes. Cybercriminals, in their quest for profit, sometimes disguise their malicious software in seemingly harmless applications or programs. Perhaps on some occasion, when analyzing your computer with a malware detection tool, you have found something called a PUP on your system. Here we are going to discuss what the PUP malware threat is and how we can avoid it to keep our computers safe.
In this tutorial we are going to talk about the main ways in which we can find it, as well as a series of tips to prevent it from ending up installed on our computer.

What is PUP malware
To understand what PUP malware is, we have to understand well what each of the two words that compose them mean. PUP stands for P otentially Unwanted Program which, translated, means potentially unwanted application. These are programs that do not benefit users and that can cause:
- Slow down, track or saturate our team.
- The change of the home pages.
- Redirect to websites.
- Alter the result of our searches.
Another thing that also characterizes them is that the installation is done with the authorization of the user. This does not mean that the user is not being deceived, since sometimes, with legitimate software, harmful software is also added.
These potentially unwanted programs usually camouflage the installation of that unwanted software in two ways:
- Noting it in the Agreement with the end user. We often look too far at these types of documents.
- Camouflaged within the various installation screens of the program or in the advanced installation options.

As for malware , it refers to malicious software or any type of software that can perform harmful actions on our computer system without the user’s knowledge. Thus, cybercriminals can perpetrate information theft using Trojans, cause a computer to malfunction, or blackmail a user by encrypting their data with ransomware.
PUP malware could be defined as a potentially unwanted application that will end up installing harmful software on our computer without our permission. The PUP is somewhat less dangerous, but it can affect privacy and receive too much publicity. We must both try to eliminate them from our teams.
Why are both malware PUPs and regular PUPs dangerous
At the time that we are going to install a program we must walk with a thousand eyes and take our time. As we explained in the previous section, you have to try to read the license agreement and be attentive to everything. The other important point is the installer screens, whether or not the desired software is installed may have to do, for example, with leaving a box checked or not.
A typical example that many of you may have noticed on occasion is that, after installing a program, a browser extension has been installed. Sometimes it is clear that it is from a certain program and may have some utility. However, it may also be the case that they end up threatening our privacy.
Therefore, malware and other types of PUPs will pose the following threats to our computers:
- Changing the system settings , here we find that our home pages can change and hijack our browser’s search engine.
- The insertion of unwanted applications together with the software that we do want to install. This can be with or without permission from the developer. Keep in mind that cybercriminals sometimes manipulate the installer.
- The espionage of our activity in which they could observe our web browsing habits and then sell them to advertisers.
- Abusive or intrusive advertising in which cybercriminals to make a profit place their own advertising on the websites that the user visits.
- The introduction of malware , an example would be P UP.Optional.Delta, which is a browser hijacker that can deactivate our antivirus, the firewall, and also reduce the general performance of the system.
This last category is the one that would be most related to PUP malware
How should I install a program so as not to be a victim of PUPs
When installing a program you have to have common sense, be patient and be cautious.

The first thing we have to do is download the latest version of the program from the developer’s website . In this way we avoid that a third party has been able to manipulate it by introducing malware or other PUPs. The next thing we need to do is carefully review the license agreement in case we find anything suspicious.
On many occasions when we install a program we can do it in different ways:
- Using standard, quick or recommended installation . It does everything for you automatically and it will install all the components by default. If there is any PUP I would install it too.
- Using custom installation . Being requires the most effort and attention, but it is also the safest. In it, generally all the boxes are activated, which means that all the elements will be installed. We must read them one by one and dispense with those that constitute a risk to our security or those that we are not going to use to save hard disk space.
We do not always find facilities of this type. There is also a type of simple installation that some of its screens have activation boxes that if you do not deactivate it, it will install additional software. Generally, if you go very fast, you have a good chance of not deactivating that box and that harmful software ends up on your computer.
What other additional measures can I take to protect my equipment
As we have already seen, an essential part to prevent PUP malware or any other potentially unwanted software is to be very careful during the installation process. Our first line of defense should be to have an operating system with the latest updates installed and have an updated antivirus installed .
It may also be the case that we are a careful person and committed to safety. However, sometimes that may not be enough because other people occasionally use your PC or laptop. In those cases a solution may be to create guest accounts so that they do not install anything without your permission.
A good idea in Windows is to go to Add / Remove Programs and review the installed software. If you are sure that you do not need it or it may be dangerous to uninstall it. Another very convenient option is to have antimalware software installed . A free example that we could use is Malwarebytes. In the same way that we periodically scan our computer for viruses, we must also do it for malware.
This is an example of Malwarebytes looking for threats on our computer.
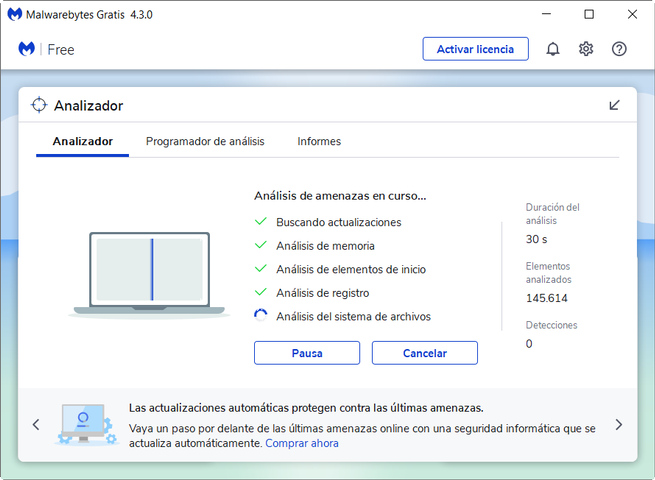
These are the results I have obtained after analyzing my PC:
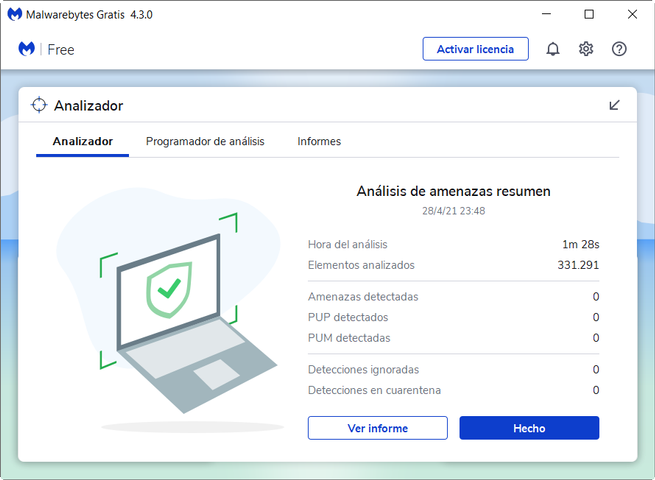
If you look at detected PUPs, it says 0. That means that I am free of PUP malware or any other type of PUP. In the event that malware is detected, most of this type of software will quarantine those executable files and / or folders where that PUP is installed.
It could also be the case that this assessment is unfair. In that case we should manage a tool that is usually called exclusions, white list or list of allowed sites. There we will have to put the location of the folders or files that we want to allow. Finally, in this article we recommend not allowing any unless we are very sure that it is not malicious software.