When we have a home or professional network with manageable switches and WiFi access points, it is very important to provide the network with the necessary security to avoid or mitigate possible attacks from future clients, whether they are wired clients or wireless clients. Today in this article we are going to talk about the security measures that you can take to protect your network, configuring the switches and also the WiFi access points in a specific way, in order to have the network as secure as possible.
General configuration of the local network
When we talk about an advanced home network or a professional network, it is essential to have a correct segmentation of it using VLANs . It is absolutely necessary to have a router / firewall that has support for VLANs with the 802.1Q standard, which is the one currently used, thanks to this support for VLANs, we can configure a dedicated subnet for each of the VLANs, and allow or deny the access between the different VLANs that we have.

A highly recommended practice to have the best possible security in a network is to have a specific subnet and VLAN for the management of the different devices of the local network, that is, of the switches, WiFi access points that we have and the controller WiFi by software or hardware. Everything that is management, administration and monitoring of the different network equipment should be contained in this VLAN.
Thanks to the routers / firewalls with VLAN support, it could be configured to prevent access from other VLANs to this management VLAN, with the aim that no one can access the web configuration menu of the different devices, access will not be allowed either. via SSH or perform the typical ping. That is, all communication from the rest of the subnets such as “marketing”, “guests”, “workers” will not have access to this specific VLAN.
By default, in all computers (routers, switches and APs) VLAN ID 1 is the management and administration VLAN, this VLAN ID is recommended to change it for security and apply the corresponding access control lists to allow or deny access . For example, if we use a professional router such as the DSR-1000AC, we can configure the VLAN ID that we want and use a specific subnet, the rest of the switches must be in this specific subnet.
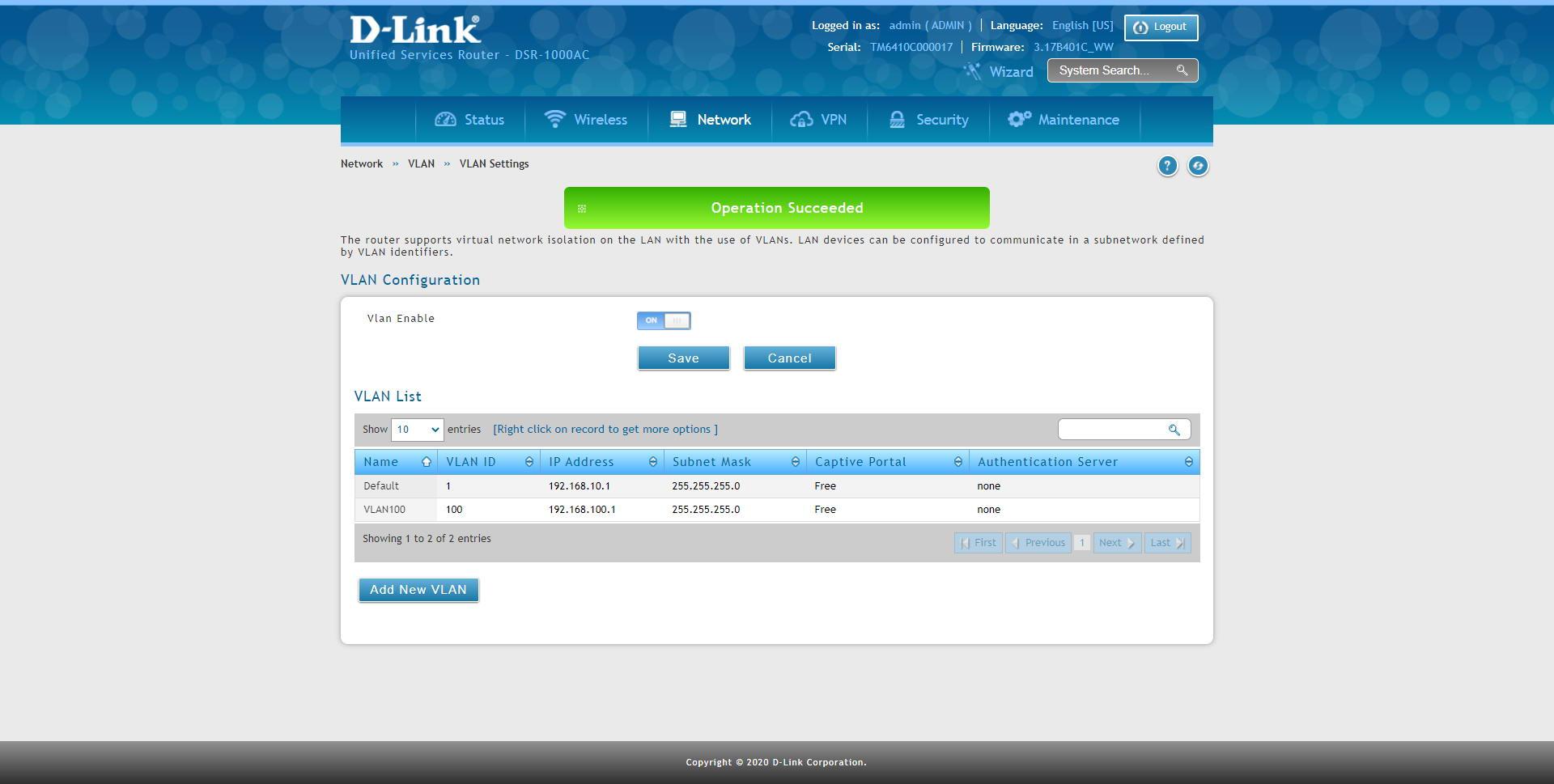
Let’s imagine that we create VLAN ID 10 on the router / firewall and also on the switches to be the management one. In the router or firewall we must create this VLAN ID and pass all the VLANs through an interface in “trunk” mode, that is, with the VLANs tagged so that the switch “understands” the different VLANs that we are passing to it.
The configuration of a management VLAN in the switches, or also known as “Management VLAN” is configured in several ways:
- We have a specific “Management VLAN” menu, where we will select the VLAN where we want the management to take place. The private IP address that we put in the switch must be within the range of the management VLAN 10, or use the DHCP client to obtain the IP address automatically.
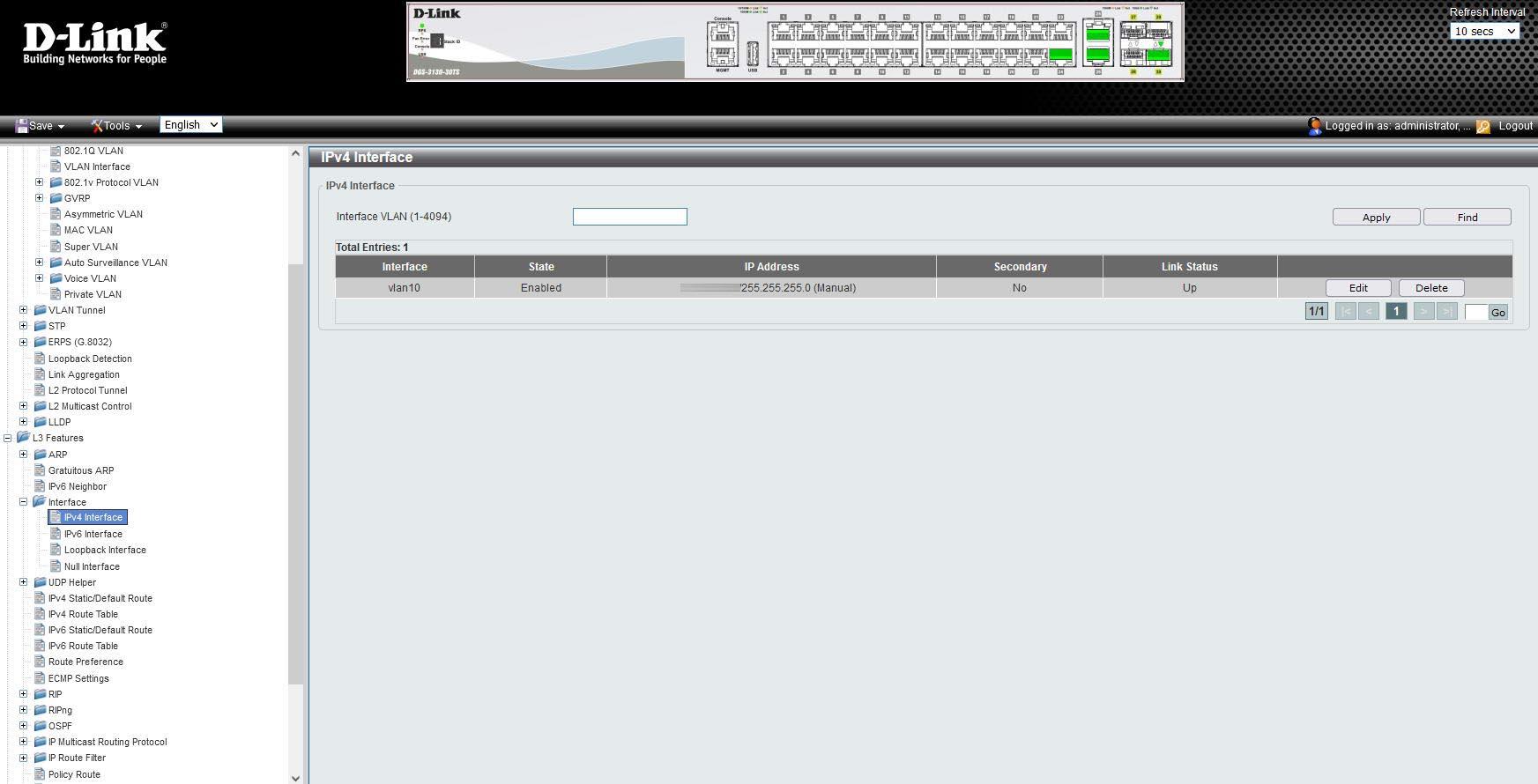
- If we have a switch with L3 functions, we must create an «IPv4 interface» with VLAN ID 10 and provide a private IP address within the range of management VLAN 10, or use the DHCP client to obtain the IP address automatically.
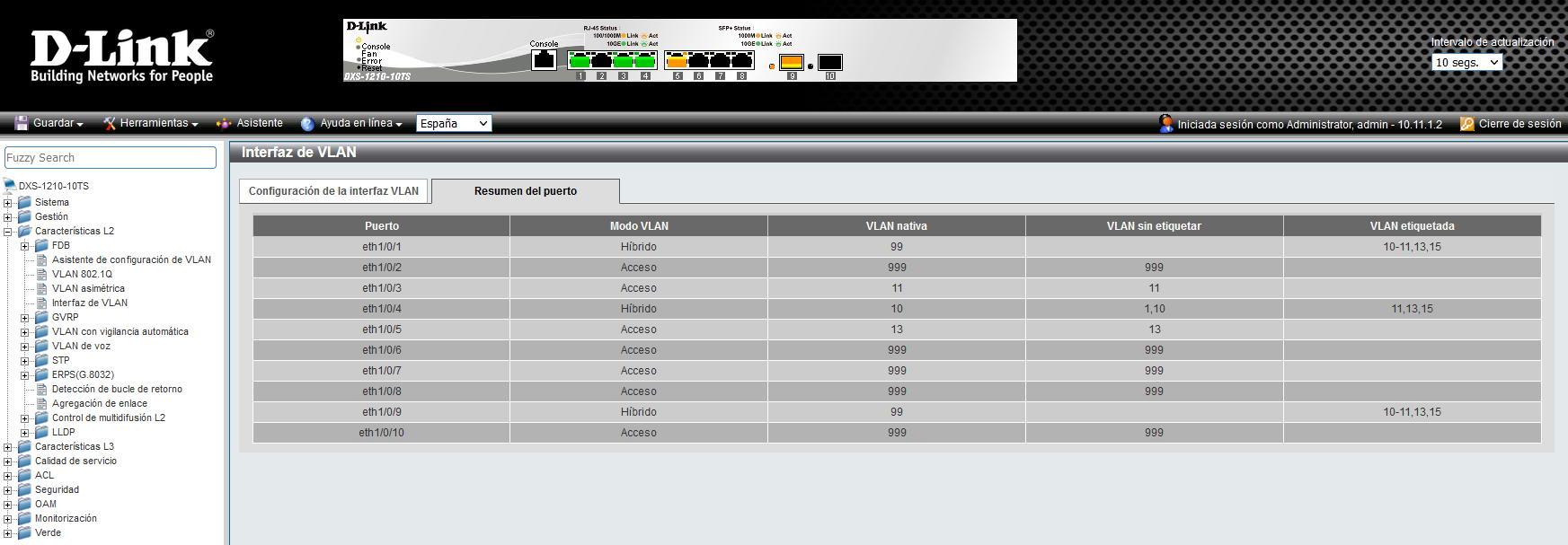
For example, we have used the D-Link DGS-3130-30TS switch this time, as you can see, we have the different VLANs configured, and ports 25 and 26 as «Tagged»:
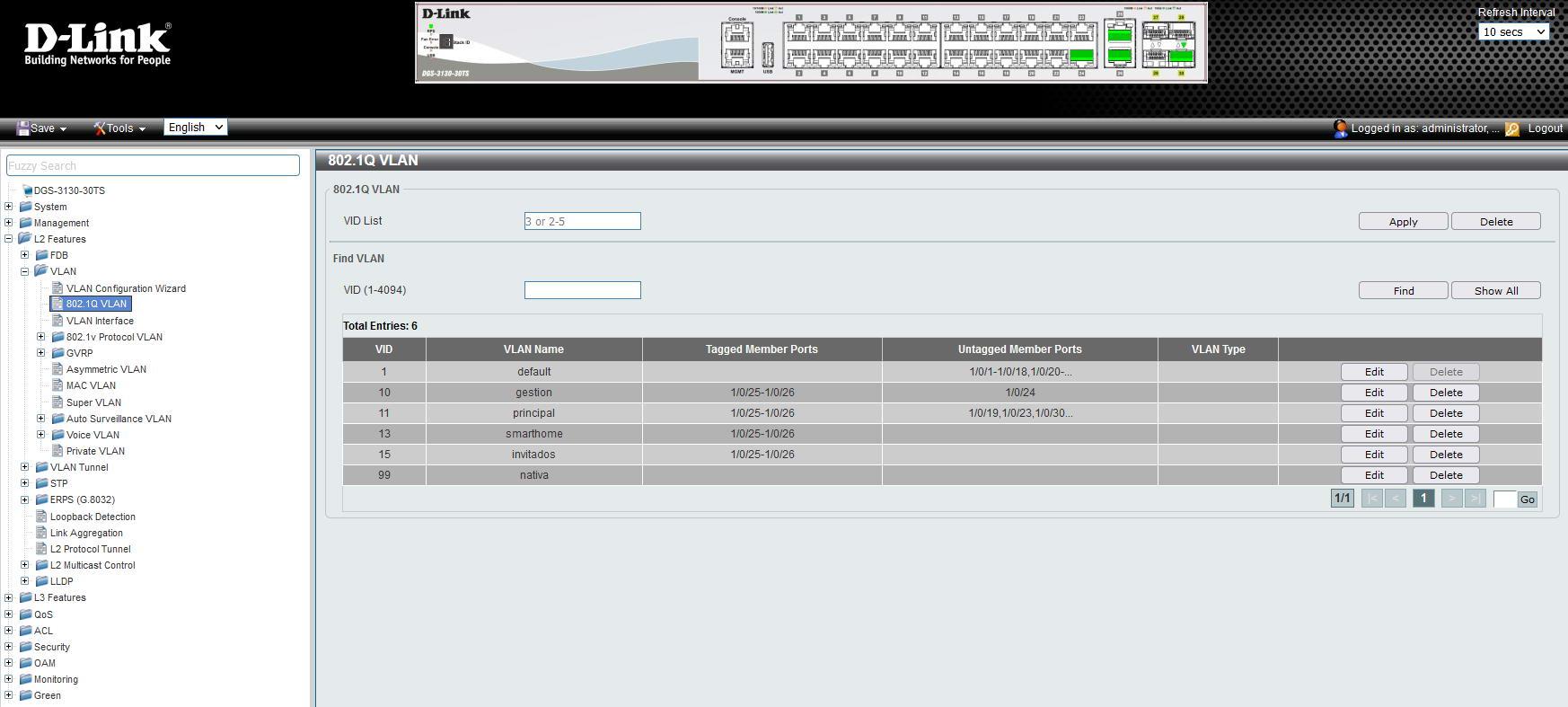
In the “IPv4 Interface” section we create a new interface with the VLAN ID that we want, we put an IP address for the administration and at this time we will be able to administer this device only through this VLAN and with this specific IP address.
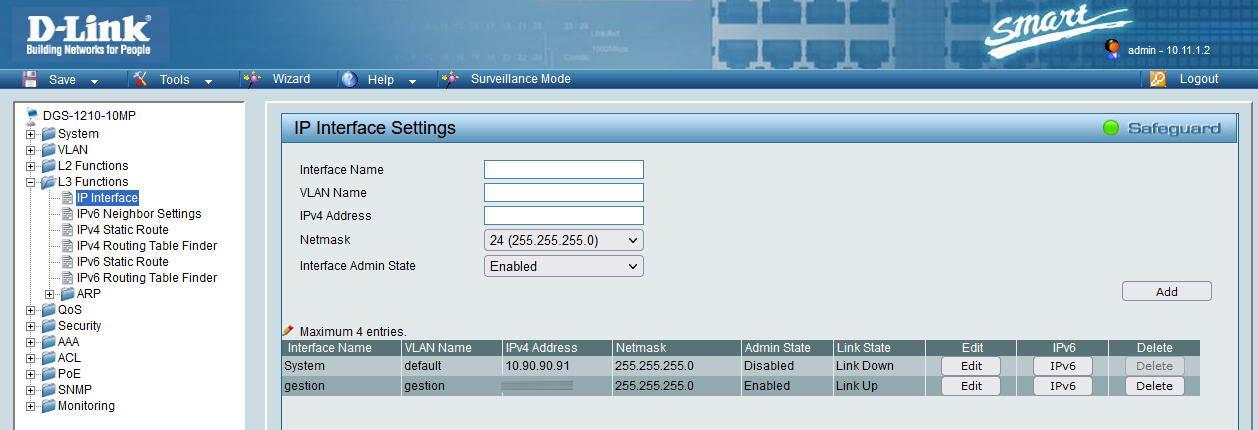
In simpler switches that are “Smart” like those in D-Link’s DGS-1210 range, we also have this functionality with similar options available. In this case, it does not allow us to remove the default VLAN of the interface, but we can disable the administration, therefore, we would be in the same scenario. As you can see, in this case we can also register the VLAN that we want for administration, in fact, it allows us to register up to 4 IP Interfaces in this smart switch.
This is the first step to correctly configure network security, properly segment the network into subnets, with different permissions thanks to the access control lists or rules in the firewall. Now we are going to see what security measures we can take on manageable switches.
Configurations on the manageable switches
Managed switches are responsible for stopping a large number of attacks that could compromise networks, it is very important to configure these devices properly and with the best security to avoid possible problems in the future. There are a large number of attacks that aim to bypass security measures, we are going to explain the main attacks and how we can adequately mitigate them.
The first thing to keep in mind is to use strong user credentials on the switch , that is, to have an administration password long and complex enough to avoid problems with brute force or dictionary attacks, however, if done right clients will not have communication with the management website. Another important security measure is the ability to create other user credentials with different levels of permissions , so that not all network administrators log in as administration (super user). Finally, it would be advisable to enable administration via HTTPS to have point-to-point encryption, from the browser to the switch, in addition, if you are going to enter the administration via commands it is totally necessary to enable SSH instead of Telnet , the latter does not provide any security type.
Manage ports and trunks
There is an attack called Switch Spoofing that aims to negotiate trunks automatically, to receive all the traffic of all the VLANs that we have registered in the switch, in this way, an attacker could have access to all the traffic of the different virtual networks (VLANs) that we have. To mitigate this attack, it is essential:
- Disable switch ports that will not be used.
- Do not negotiate trunks automatically.
- The ports that are not as trunks, put them as ACCESS explicitly.
There is another attack called Double Tagging that would allow data to be sent to a VLAN that is not really accessible. To avoid this attack, the following is recommended:
- The ports that are not in use, put them as ACCESS explicitly and in a VLAN created in the switch and that has no real use (VLAN 999 for example).
By making these basic recommendations, we will avoid a large number of possible attacks.
Port-Security
The Port-Security security feature is responsible for managing the computers that connect to a specific physical interface of the switch, allowing the following:
- Limit the number of MAC addresses that can connect to this port.
- Allowing only MAC addresses that appear on the whitelist.
Port-Security is responsible for protecting the port, in addition, we have several violation policies in case the number of MAC addresses is exceeded or an incorrect MAC address is connected:
- Shutdown: the port can be shut down automatically, then the administrator will have to manually turn it off, or wait a certain time until it comes back up on its own. Depending on the switch, we will have more or less options.
- Restrict (restricted): the traffic of the MAC address that has violated the applied policy is blocked, increases the violation counter to verify what has happened on the port.
- Protect (protected): the traffic of the MAC address that has violated the applied policy is blocked, it does not increase the counter.
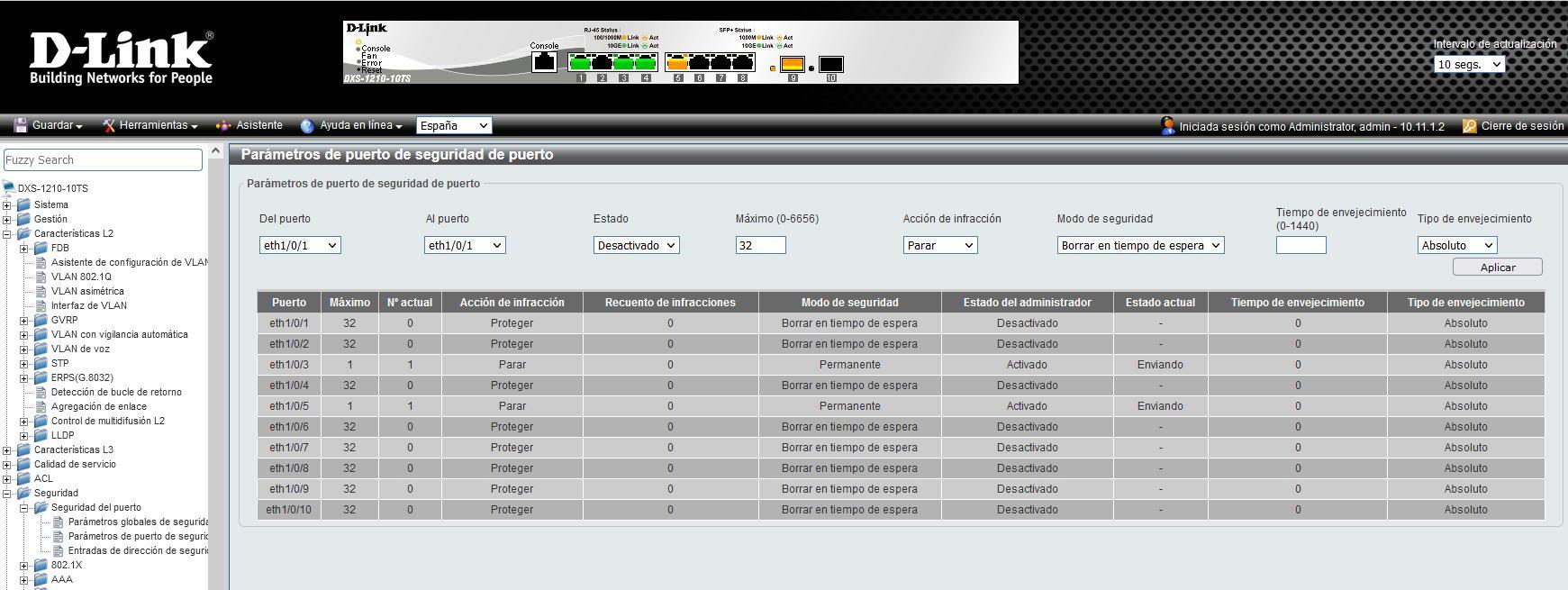
It is generally in “shutdown” mode by default.
Do you use Spanning-Tree in your switches?
In the event that you are using the Spanning-Tree protocol to avoid loops at the L2 level, it is highly recommended that you configure the ports correctly to prevent a cybercriminal from becoming the root switch, and passing all network traffic through it. The specific configurations that you must make to mitigate these attacks that can be made to us are:
- Activate the bpduguard function : this function prevents an STP frame from being received on a certain port, it will automatically block the frames. This must be done on non-trunk ports, otherwise we will block the port.
- Enable root guard feature : This feature prevents a new device from becoming the root or root switch of the network. If a frame is received indicating that a switch is going to become root, if this function is activated on the port it will automatically block the frames and ignore it.
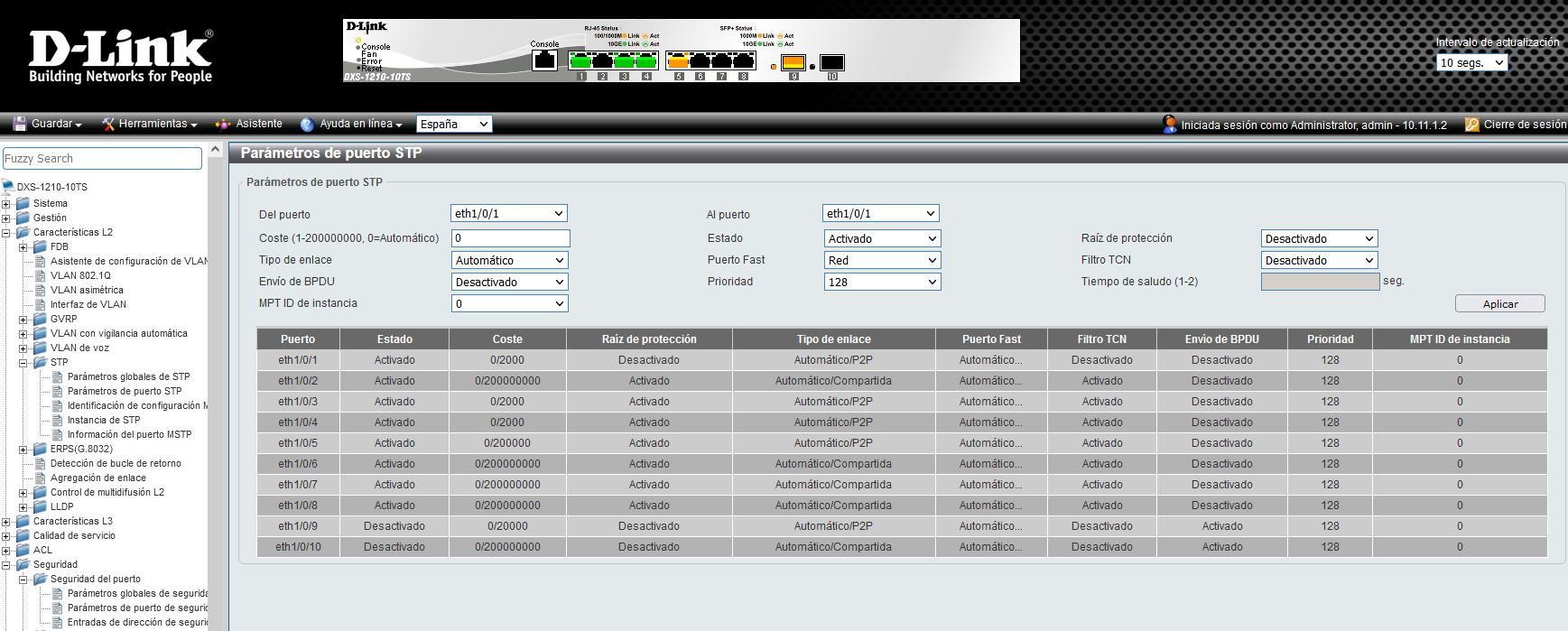
This security measure is quite important, but if you don’t use Spanning-Tree (or RSTP, MSTP) you won’t have to do any configuration.
DHCP Snooping
A malicious user could create a rogue DHCP server in our organization, and provide IP addressing to different wired and even wireless clients. To mitigate this, it is absolutely necessary to enable the DHCP Snooping functionality, one of the most important security features that switches have.
DHCP Snooping allows you to filter “untrusted” DHCP messages by building and maintaining a table of legitimate DHCP Snooping associations. An “untrusted” message is a DHCP message that is received from the network, from outside the network or the firewall, and can be part of an attack against our own network. The DHCP Snooping Association Table contains MAC addresses, IP addresses, lease time, and inbound interface of the legitimate DHCP server.
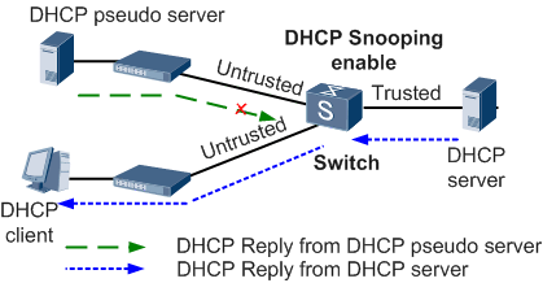
It could be said that DHCP Snooping is like a firewall between untrusted hosts and DHCP servers, in this way, if an untrusted host sends a DHCP Discovery message, it will be allowed to pass, but the corresponding messages will not be allowed to pass through. DHCP server like DHCP Offer and DHCP Ack. Depending on the switch configuration options, DHCP Snooping could be configured generally on the switch, and DHCP Snooping could also be configured per VLAN. When enabled on a switch, the switch acts as a Layer 2 bridge intercepting all DHCP messages that should not be sent by a client.
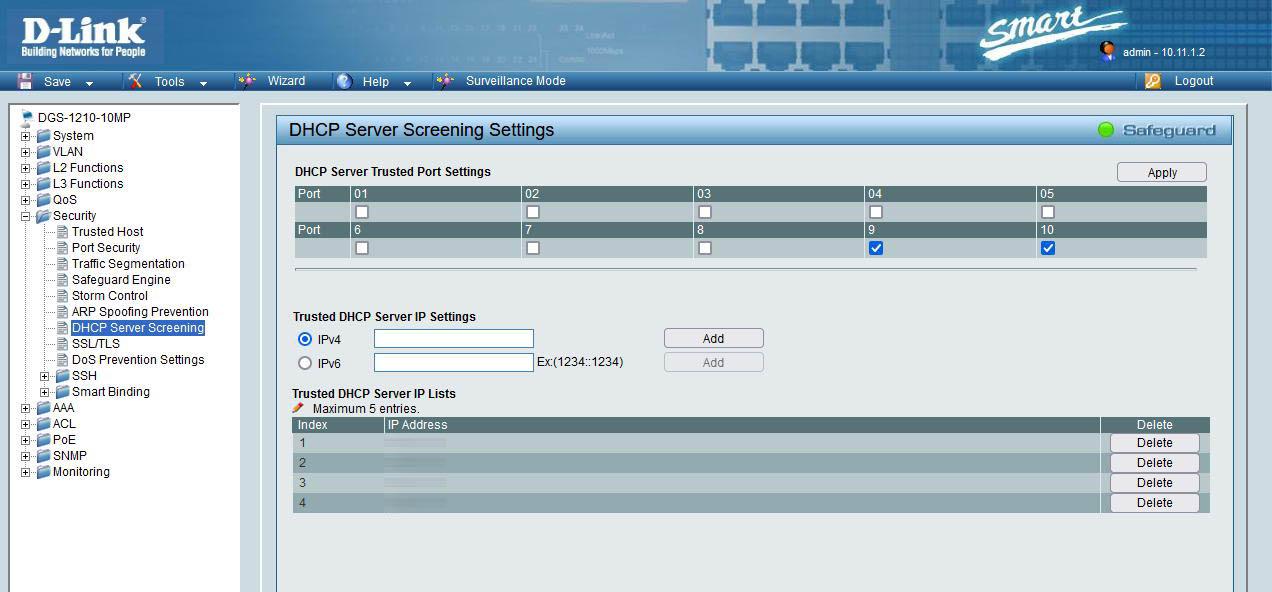
In the previous image you can see that there are untrusted clients on the network, by default, all ports are “untrusted” when DHCP Snooping is enabled. When the client PC sends a DHCPDISCOVER message and DHCP Snooping is enabled, the Switch will only send the DHCP broadcast message to the “trusted” ports and blocks any DHCP OFFER or ACK on untrusted. When you configure DHCP Snooping on the switch, you are configuring the switch to differentiate between “untrusted” and “trusted” interfaces.
Anti ARP Spoofing
The switches also incorporate security measures to prevent ARP Spoofing attacks or also known as ARP Poisoning. In this way, if we register the combination of “IP, MAC and port” in the router, a cybercriminal will not be able to deceive a victim with the default gateway (the router) to capture network traffic. It is very important to register in this section all the gateways or critical equipment that we have on the network such as servers, in this way, they will not be able to carry out an ARP Spoofing attack.
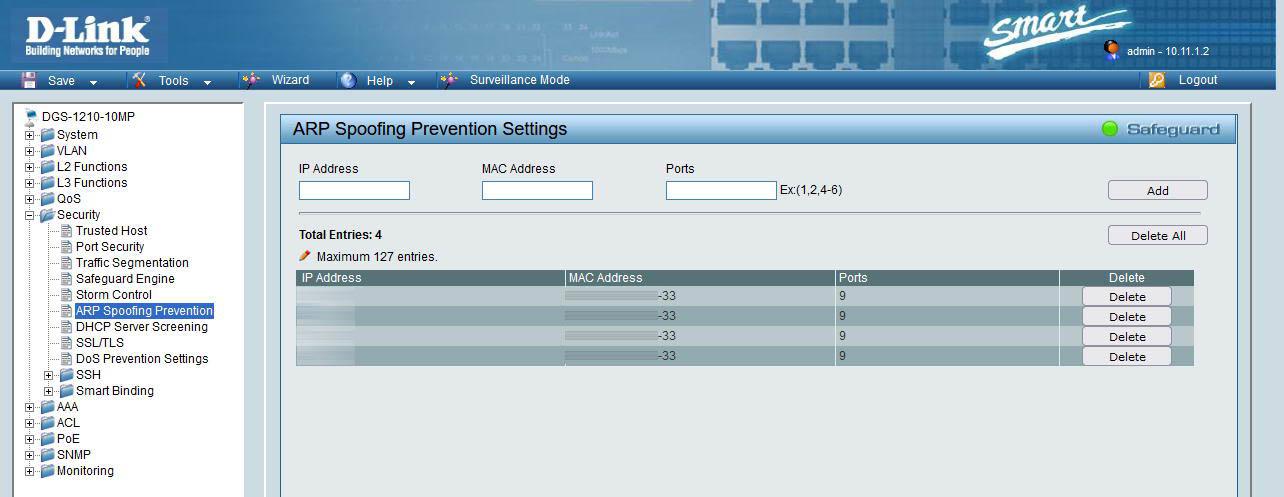
Once we have seen the main security measures that we must take in a manageable switch, we are going to talk about other very interesting measures.
Other security measures
There are other security measures in the manageable switches that will prevent other attacks on the networks, below, we briefly tell you what they consist of:
- DoS attack prevention : the switches allow you to configure all your ports to detect possible DoS attacks with high traffic and very specific traffic. For example, we can avoid Land Attack, TCP Xmasscan, TCP Null-Scan or TCP SYNFIN attacks, among others. Depending on the switch we will have some available attacks or others to avoid them.
- Storm control : the objective of this security measure is to prevent a wired client from sending a lot of unicast, multicast or broadcast traffic. This type of attack aims to block or collapse the network, the switch will take care of preventing it.
- Traffic segmentation : we have said before that we can segment the network into different VLANs with subnets. If we want to isolate a device from a certain port and VLAN 20 (for example) from another device on the same switch that is also on VLAN 20, we can configure “Traffic Segmentation” to avoid communication.
Other more advanced configurations that we can carry out is to authenticate each and every one of the wired clients in a RADIUS or TACACS server, making use of the 802.1X protocol . This protocol allows us to authenticate wired clients that connect to the switch, if they cannot authenticate automatically, all the traffic it produces will be denied. It is one of the best security measures that we can configure in a switch, because it will allow us to authenticate clients.
Once we have seen the main security measures in the switches, we are going to see what security measures we can put in the WiFi access points.
Configuration on APs
The security configuration in the WiFi access points so that clients cannot access them is simple if we have correctly segmented the network into VLANs . Generally, WiFi controllers are used by software or hardware, in order to centrally control dozens of WiFi access points, these WiFi controllers will always be located in the management network, because they will be in charge of managing the WiFi access points in this subnet. .
In the example that you will see below, we have used Nuclias Connect on a DNH-100, which is located in VLAN 10 which is our management VLAN. As you can see, the VLANs configuration indicates that the «Mgmt» port is in VLAN 10, and is as «Tagged» , just like the rest of the VLANs that we receive through the LAN port, so that all the points of WiFi access correctly receive all VLANs from the switch.
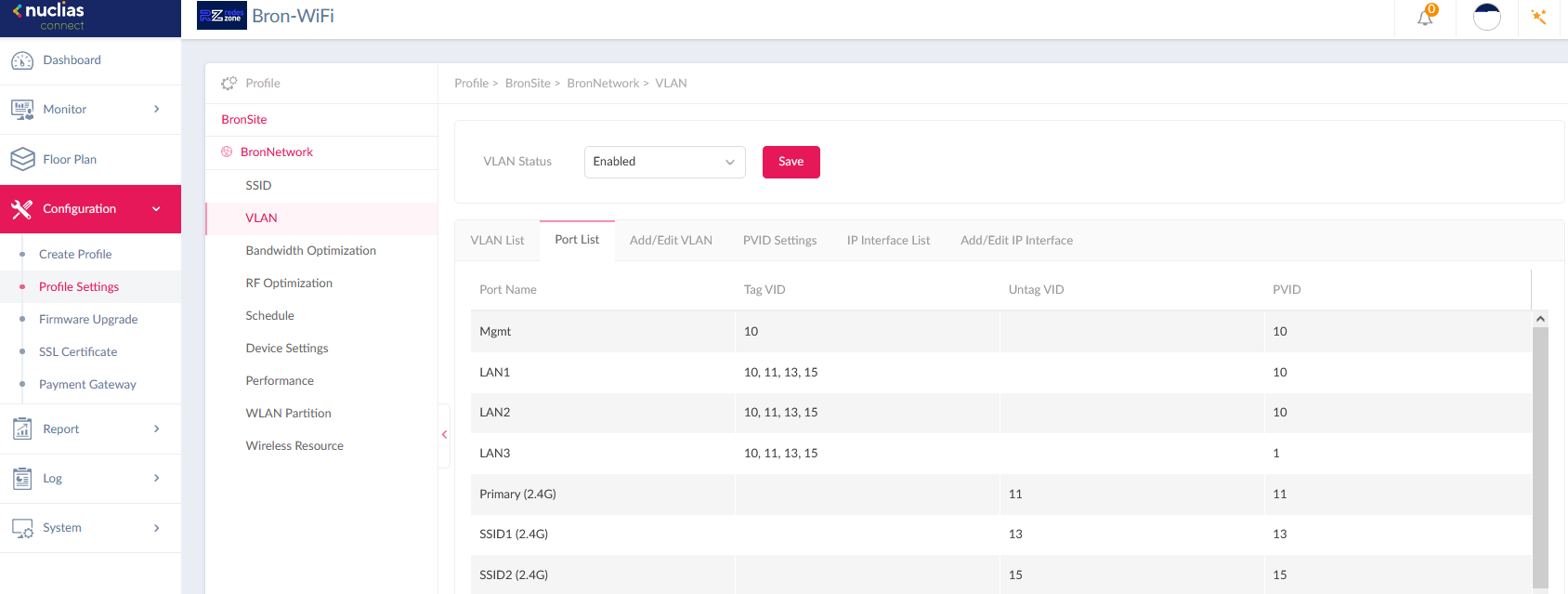
In this case, the VLANs corresponding to the WiFi networks are as “Untag”, otherwise, the wireless clients could not connect correctly. For end clients (WiFi clients, printers, PCs, etc.) all VLANs must always be “Untag”, unless they know how to “understand” 802.1Q as NAS servers do.
Once we have correctly segmented the access points with their internal management network and with the VLANs for customers, we must also protect access to the different access points with their corresponding username and password . In the «Device Settings» section is where we will have to set an «admin» username and a robust password, this will be the password with which you can access the administration website of all the WiFi access points that we are managing centrally.
We can also activate or not the console access to the WiFi access points , in case of not using the console access at all, then it is advisable to deactivate it for security reasons. Any service that is not used is best always disabled. Of course, you must always select SSH and never Telnet, because the latter is an insecure protocol.
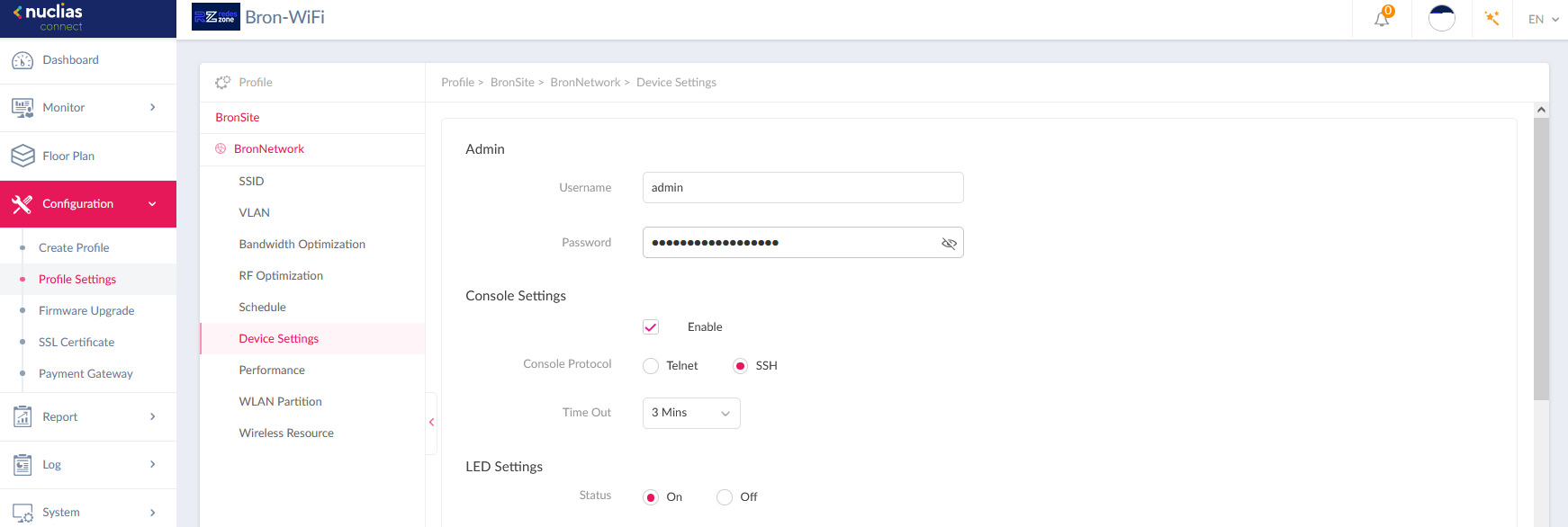
In principle, you should not have access to the WiFi APs outside the management network, so the most important thing is to verify that the administration of the APs cannot be accessed from the client’s networks via the web or via SSH either. . The rest of the configuration options that we can make in the access points depend on the requirements of the WiFi networks, such as the SSIDs to be registered with their corresponding authentication, if we want captive portal, if we want to enable the WLAN Partition to prevent the WiFi clients communicate with each other etc.
As you have seen, we must take a series of security measures both in the switches and in the WiFi access points to maintain the security of the entire network, and also that of the clients.