
In recent years, networks have evolved towards management directly from the Cloud, some IT administrators in companies no longer deploy equipment such as switches or APs that are managed locally, but are managed directly from the manufacturer’s cloud. This has many advantages, such as an easy and fast installation based on the serial number, continuous monitoring from the cloud without the need to configure monitoring systems ourselves, and access to the configuration from anywhere. Today in this article we are going to show you how you can protect your network from attacks if you manage them from the cloud.
What is network management from the Cloud or cloud?
Local networks have evolved from local management, where we had to access the different switches locally, and where we had a software or hardware WiFi controller for access points, to centralized management from the cloud. In a centralized management in the Cloud or cloud, we can manage the entire network from the main router to the different access points that we have connected to the switch, and all this through a control panel with which we will access via the web, or also through an app on our smartphone.
With a network management in the Cloud we can configure in a global and automatic way all the switches and WiFi access points that we want, in this way, we will not have to go switch by switch making the same or similar configurations, now we can apply it to all switches simultaneously, saving IT administrators a lot of work and also a lot of time. The same happens with the APs, although for a long time we have had the WiFi controllers to centrally manage different WiFi access points, now it is even easier with the management in the Cloud, because we can have several APs deployed by different «Sites »And manage them all from the same control panel.
Managing networks from the cloud has many positive aspects, such as:
- Zero-touch deployment, we will be able to register the APs and switches before connecting them to the electrical network, registering their serial number in the cloud to add them to the inventory.
- Continuous and automatic monitoring, with email alerts and Push notifications.
- Automatic firmware updates, on demand or on a specific schedule.
- Records with all changes made to the configuration.
- Role-based administration, to delegate configurations to other IT colleagues.
- Wired and advanced WiFi traffic reports, where we can see in detail what is happening on the network.
- Remote access from anywhere, it is only necessary to access the platform via the web or with the mobile app.
- Management of several sites with the same user account.
Of course, it also has some negative aspects, such as always depending on an Internet connection to make any changes, for continuous monitoring or to upload the records in real time, in addition, we will always depend on the manufacturer of the solution, and, in some cases, we must pay for the use of the cloud and not only is it enough to buy hardware equipment.
Now that we know the main characteristics of managing your network in the cloud, let’s see how we can protect it from cyberattacks.
Security recommendations for cloud management of your network
To properly protect your professional local network with a Cloud management, the same security recommendations are followed as in a local management , that is, we must correctly segment the network traffic using VLANs, we will have to correctly configure the Spanning-Tree to avoid attacks To this protocol, we should also enable protections such as DHCP Snooping and even mitigation measures for ARP Spoofing attacks among others, of course, controlling the ports of the switches with Port-Security is something fundamental. All these security measures are still in force in a cloud management, because all these protocols are still present, the only thing that changes is in the face of the administration of the different teams.
With local management, the most common is to have a VLAN with a subnet specifically dedicated to managing the different equipment (router, switches and WiFi access points), and access to this VLAN can be done from the administration network from one or more computers directly, making use of HTTPS to have point-to-point confidentiality and authenticity, another very interesting option is to connect via VPN with IPsec, OpenVPN or WireGuard directly to a server that is located in this management network, and «jump» to the management of the different devices directly from here. Of course, it is not only important to properly isolate the administration network from other users, it is also very important to use robust user credentials, with good passwords to avoid problems.
The communication of the different devices such as switches and APs with the manufacturer’s cloud is done via HTTPS , therefore, it makes use of TLS v1.2 or TLS v1.3 connections, so we will have confidentiality, authenticity and the integrity of the the data transmitted, in order to avoid possible attacks on the communication of the devices with the manufacturer’s cloud.

To remotely access the local management of a network, an attacker should violate the firewall with the corresponding attack mitigation rules, and also with their IDS / IPS, however, with management from the Cloud, the only thing they will have What to do is attack this management in the cloud, trying to perform brute force or dictionary attacks on our access credentials. We delegate the security of the system to the manufacturer itself, which will make every effort to prevent this type of attack, as Google, Microsoft or any other company does, in this way, to correctly protect the security of your managed local network. From the Cloud it is essential to correctly protect your access credentials:
- Use a strong password for access, following the basic password creation policies.
- Change the password from time to time.
- Enable two-factor authentication for added security. If our password is leaked, they will not be able to access without this second authentication factor.
Once we know how we can protect our Cloud management account, we are going to show you the main options available in Nuclias Cloud, Aruba Instant On and also in EnGenius Cloud, the three cloud management solutions that we recommend the most in this article.
Security Settings in Nuclias Cloud
Nuclias Cloud is the cloud network management solution from the manufacturer D-Link, the first thing we have to do is register on the platform via the web, then we go to our user by clicking on our name. Within the “My Profile” section we can change the password that we have previously set, D-Link forces passwords to be greater than 8 characters, therefore, it is a very good security measure. The maximum is 64 characters, so we can use the password generator of the main web browsers to create a strong password.
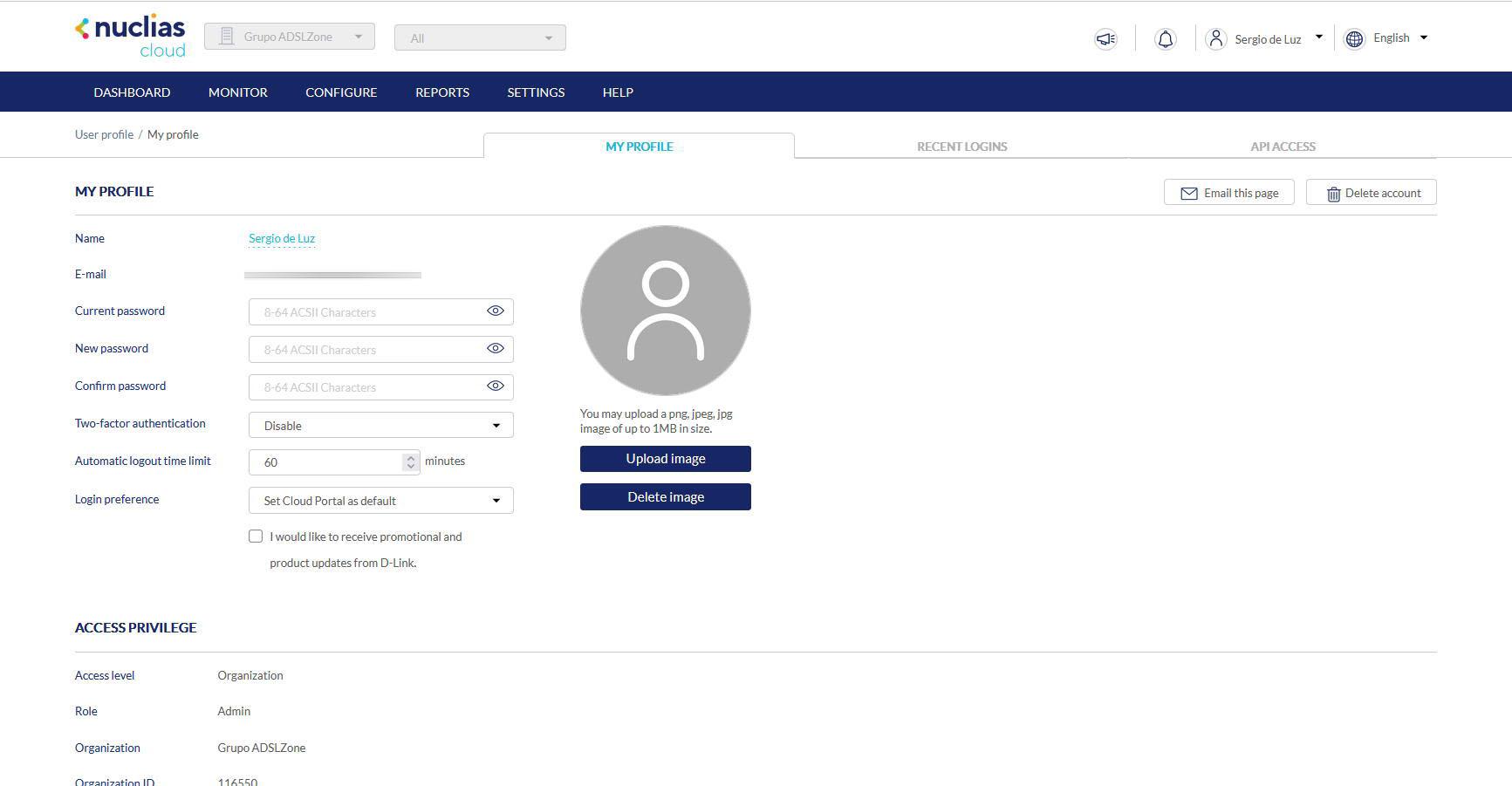
Nuclias Cloud supports two-factor authentication, in addition, it allows you to choose between authentication via Email or using Google Authenticator, or any other app for authentication with TOTP (Temporal One Time Password) codes, in this way, we can further protect our D- account. Link in the cloud. Our recommendation is to use Google Authenticator, because the generation of the codes is something instantaneous, and we do not have to wait until we receive the email in our inbox.
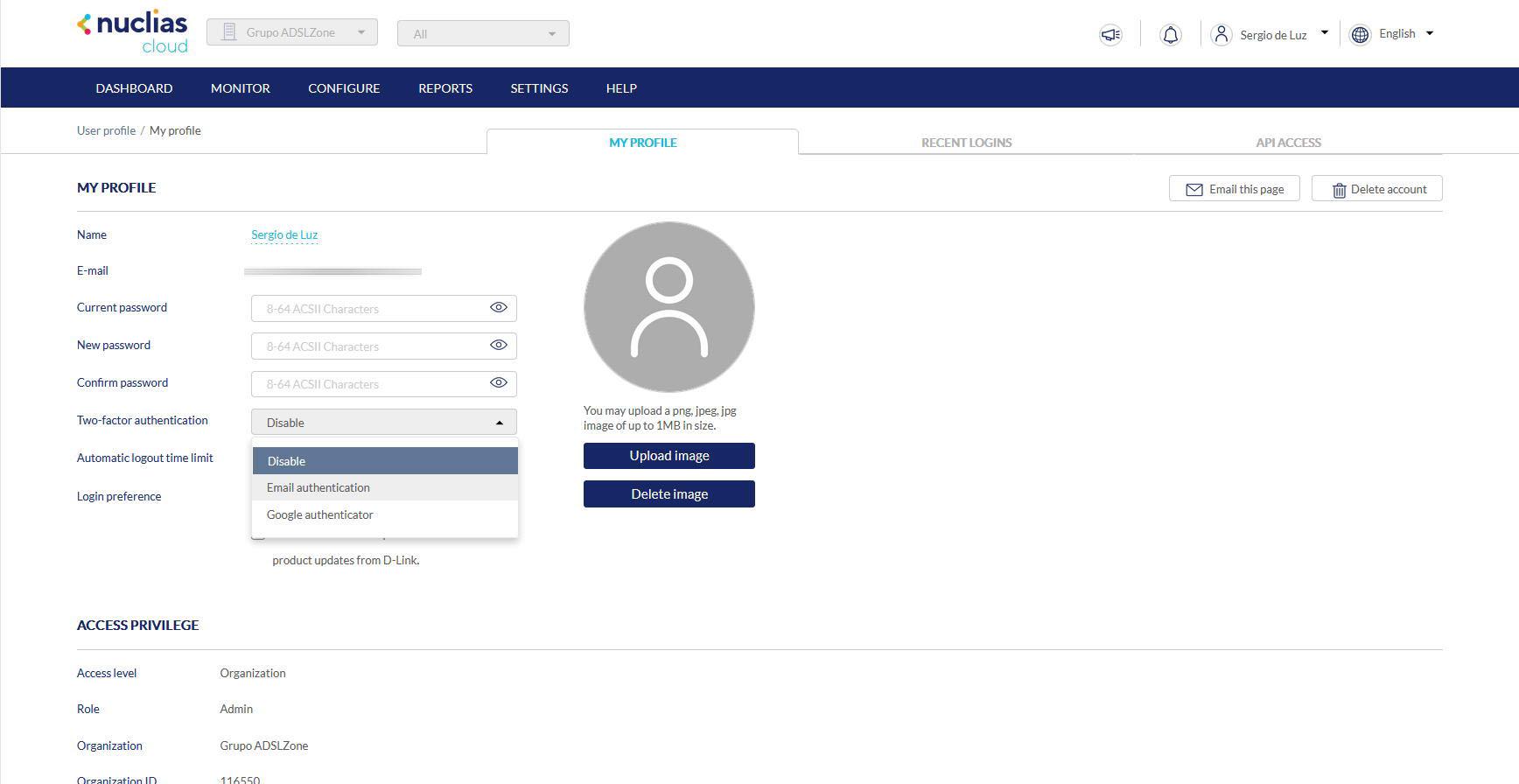
These are the only options to protect the user’s account, the rest of the options such as mitigation of brute force or dictionary attacks are delegated to the cloud service, and we cannot configure anything at all. Nor can we configure the account so that only IPs from Spain can log in with our account, something that would be highly recommended to mitigate automated attacks.
Protecting access to your Aruba Instant On account
In the case of Aruba Instant On, in the “Account Administration” section we can also change the password easily, in this case, the minimum number of characters is 10, in addition, it is mandatory to include a number, a capital letter and a symbol of those indicated, in order to create a very robust password and protect it against possible brute force or dictionary attacks. In addition, it will also allow us to activate two-factor authentication, for this, we will simply have to click on “Configure two-factor authentication”, enter the password and follow the steps.
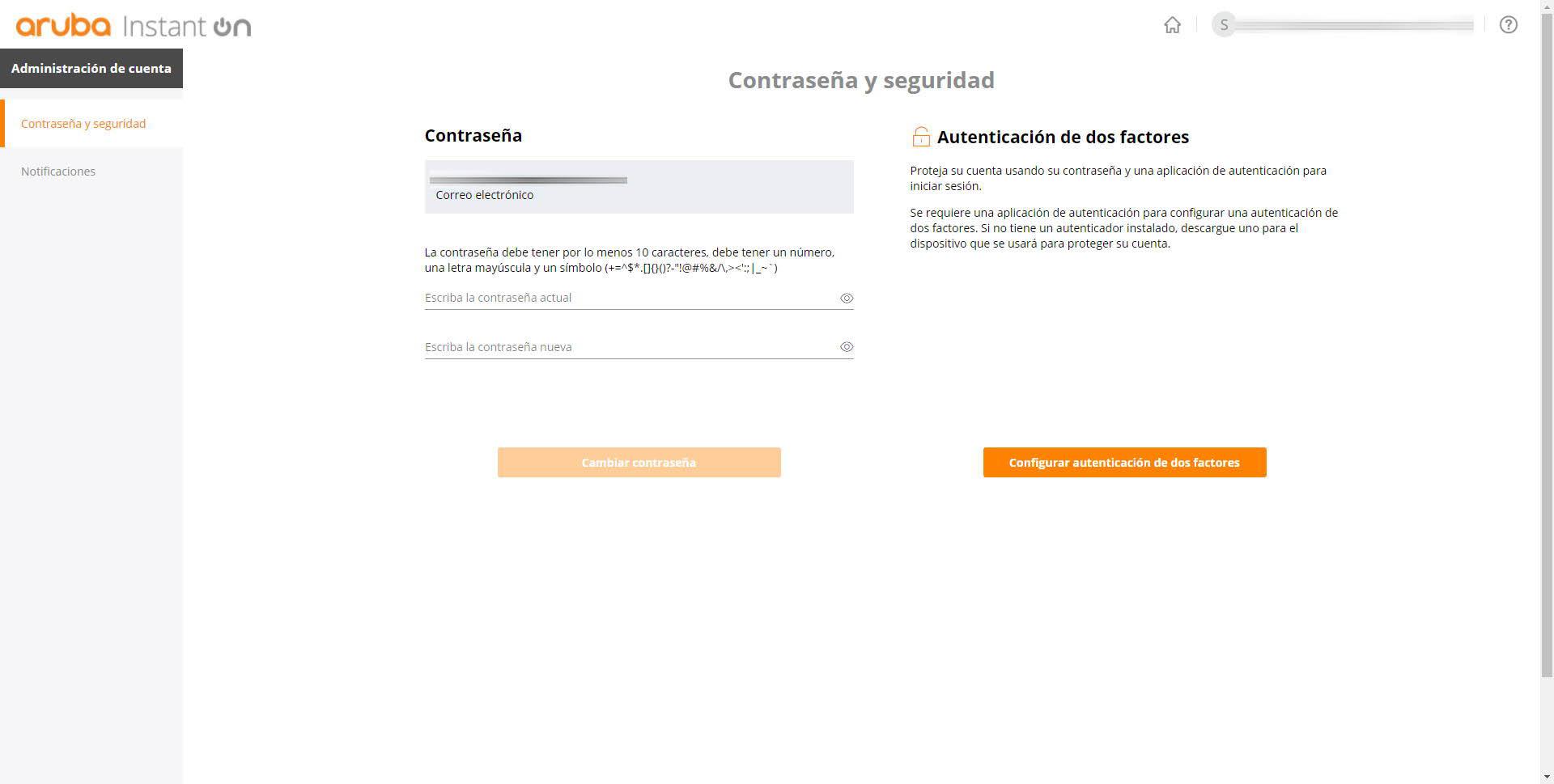
In this case with Aruba Instant On we can only use an authenticator application, such as Google Authenticator, Latch or Authy among others, we will not have the option of the second authentication factor via email. We will have to scan the QR code with the app or enter the code manually.
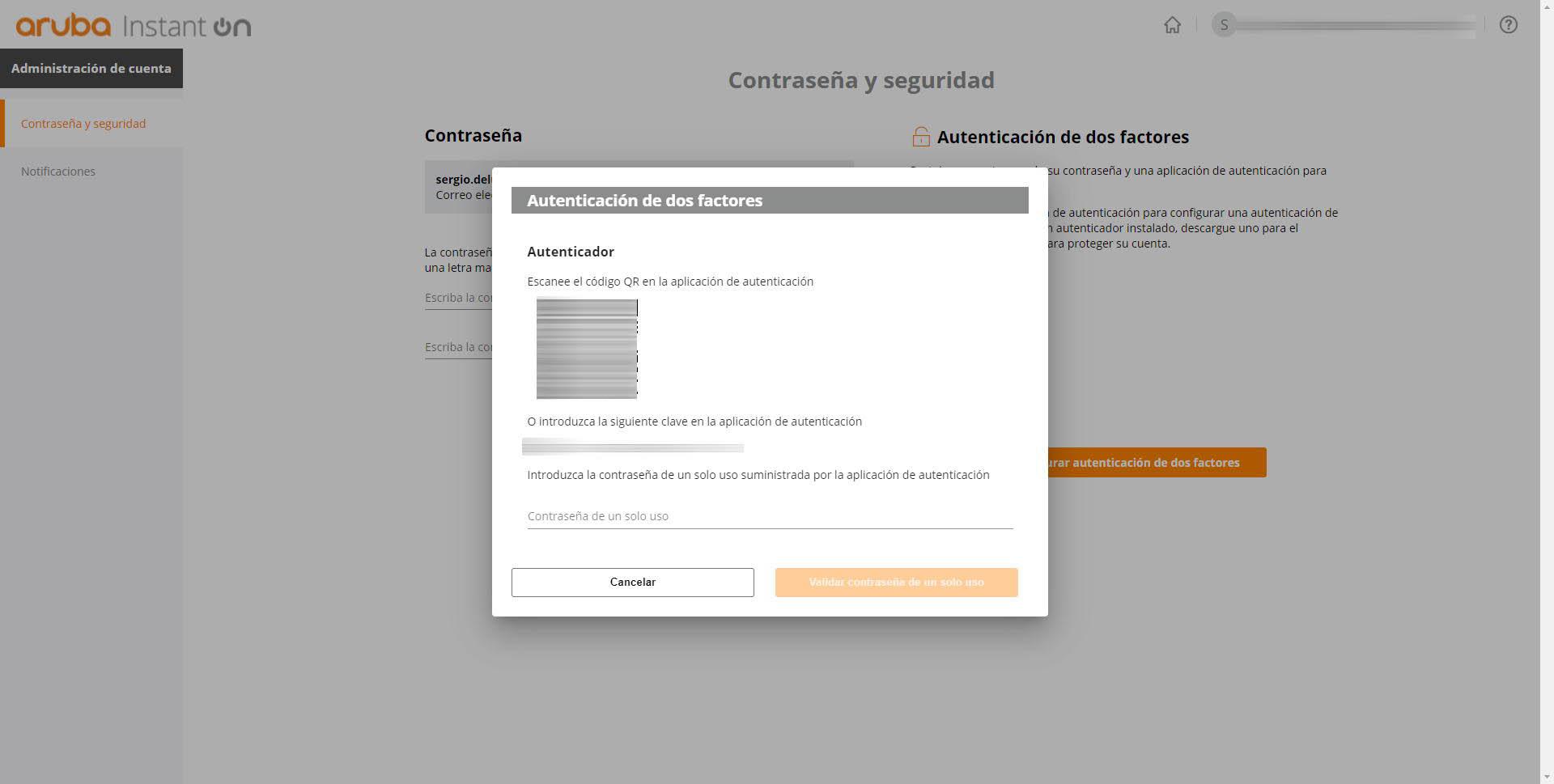
As you have seen, Aruba Instant On also incorporates the basic security measures to protect our account in the cloud, something totally necessary to protect the management of our network.
Configure security on EnGenius Cloud
In the case of EnGenius Cloud, the top right menu is where we can display the main options for security. Here we will also have the possibility to configure a strong password and activate two-step authentication. The manufacturer does not tell us, in this case, what is the minimum or maximum length of the password that we can enter, however, the most normal thing is to generate one directly with the Firefox or Chrome web browser to have a robust password.
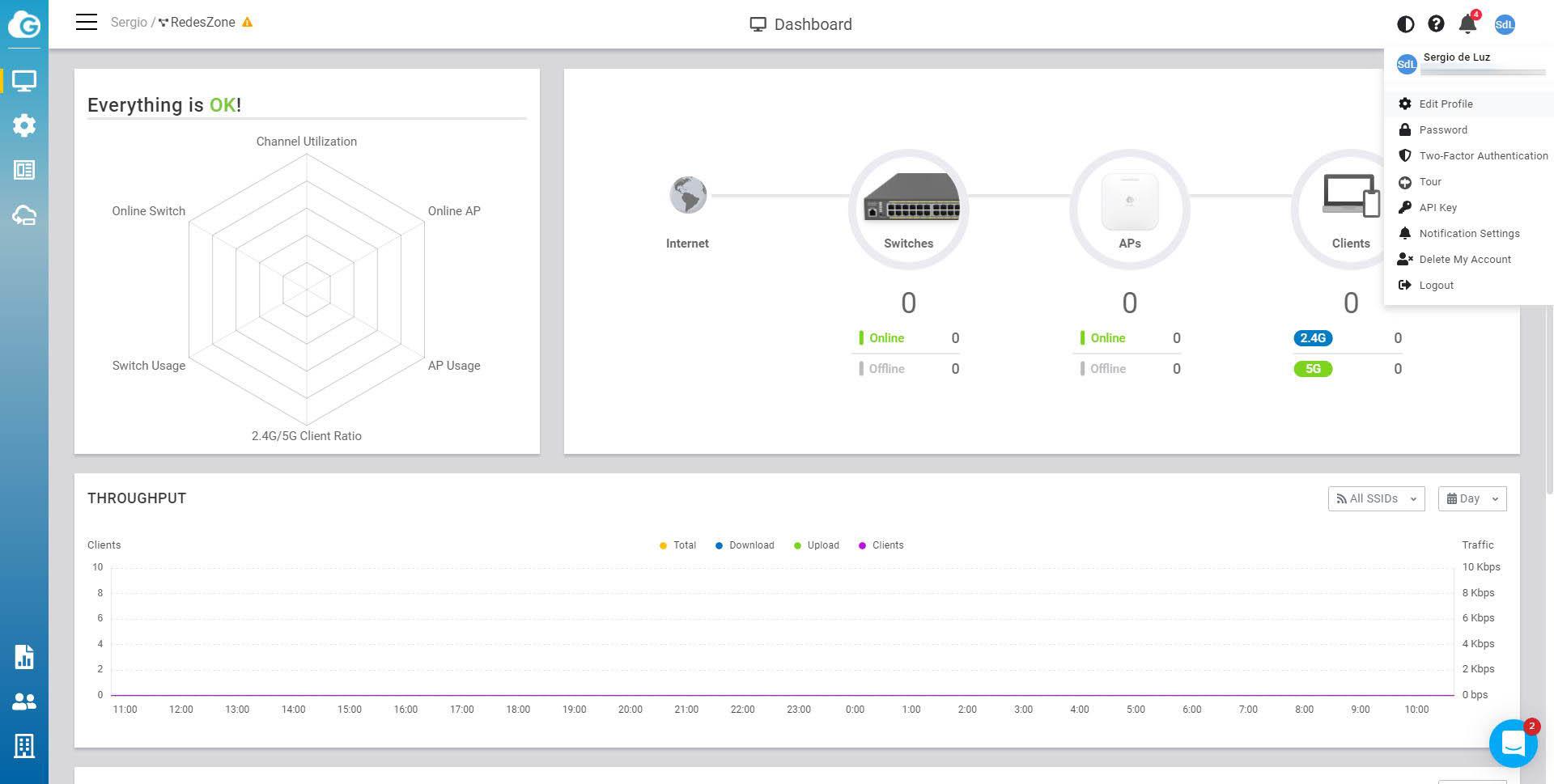
Two-factor authentication is also based on TOTP, using an authenticator app like Google Authenticator or other similar tools. In this way, it is not only necessary to enter the access code, but we will also have to enter the code dynamically generated by the application of our smartphone.
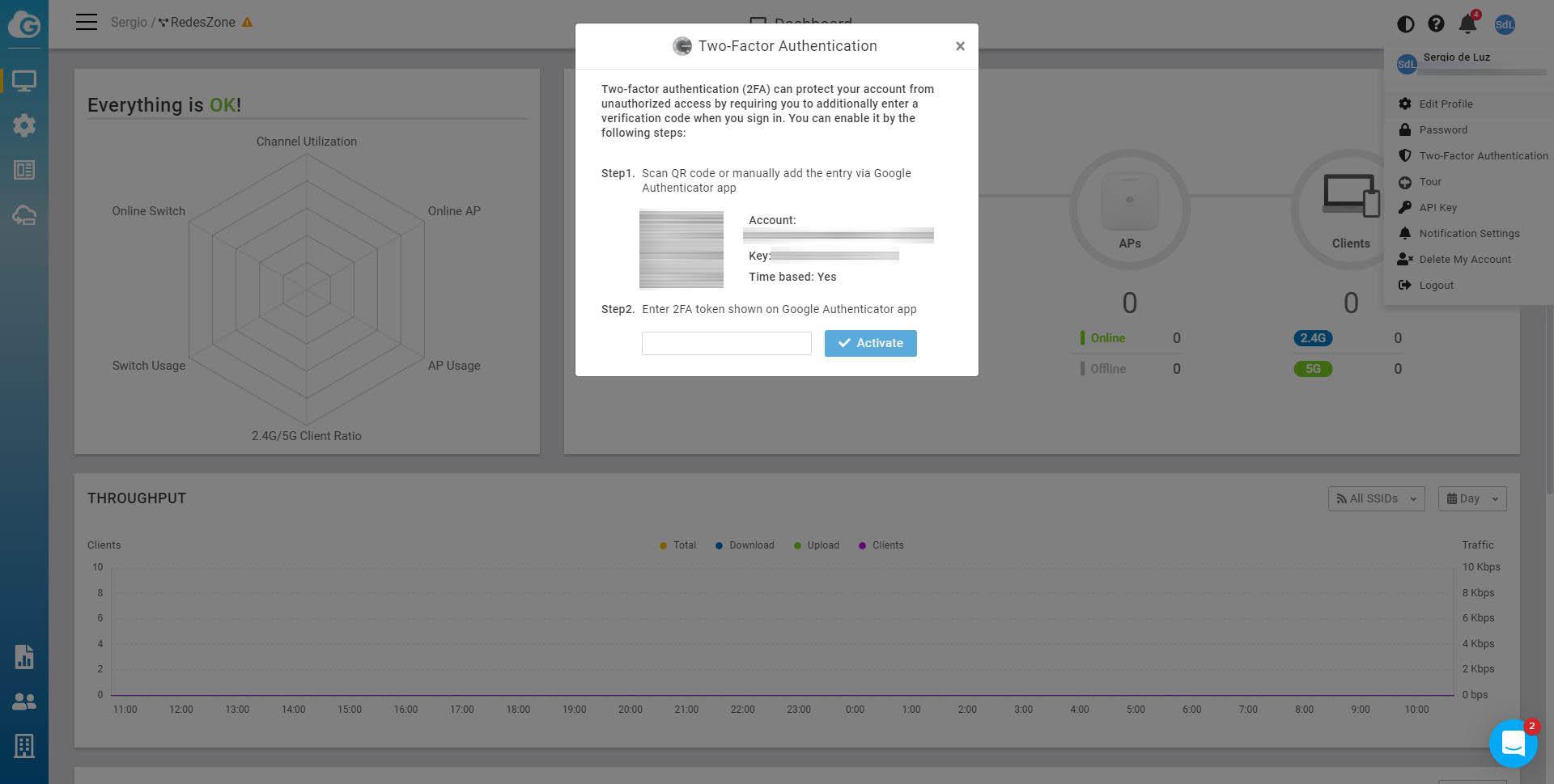
As you have seen, EnGenius Cloud also has the ability to configure two-step authentication, however, not all cloud network management systems incorporate it, such as TP-Link Omada.
TP-Link Omada
In the case of TP-Link Omada, we only have the possibility to set a password to access the cloud, it does not have any two-step authentication system to correctly verify the user’s identity, we will only have the access email and the password that we have configured. Considering that two-factor authentication is present in almost any Internet service, it is inexplicable how it is possible that TP-Link has not incorporated this very important and basic functionality to its cloud management with Omada Cloud.
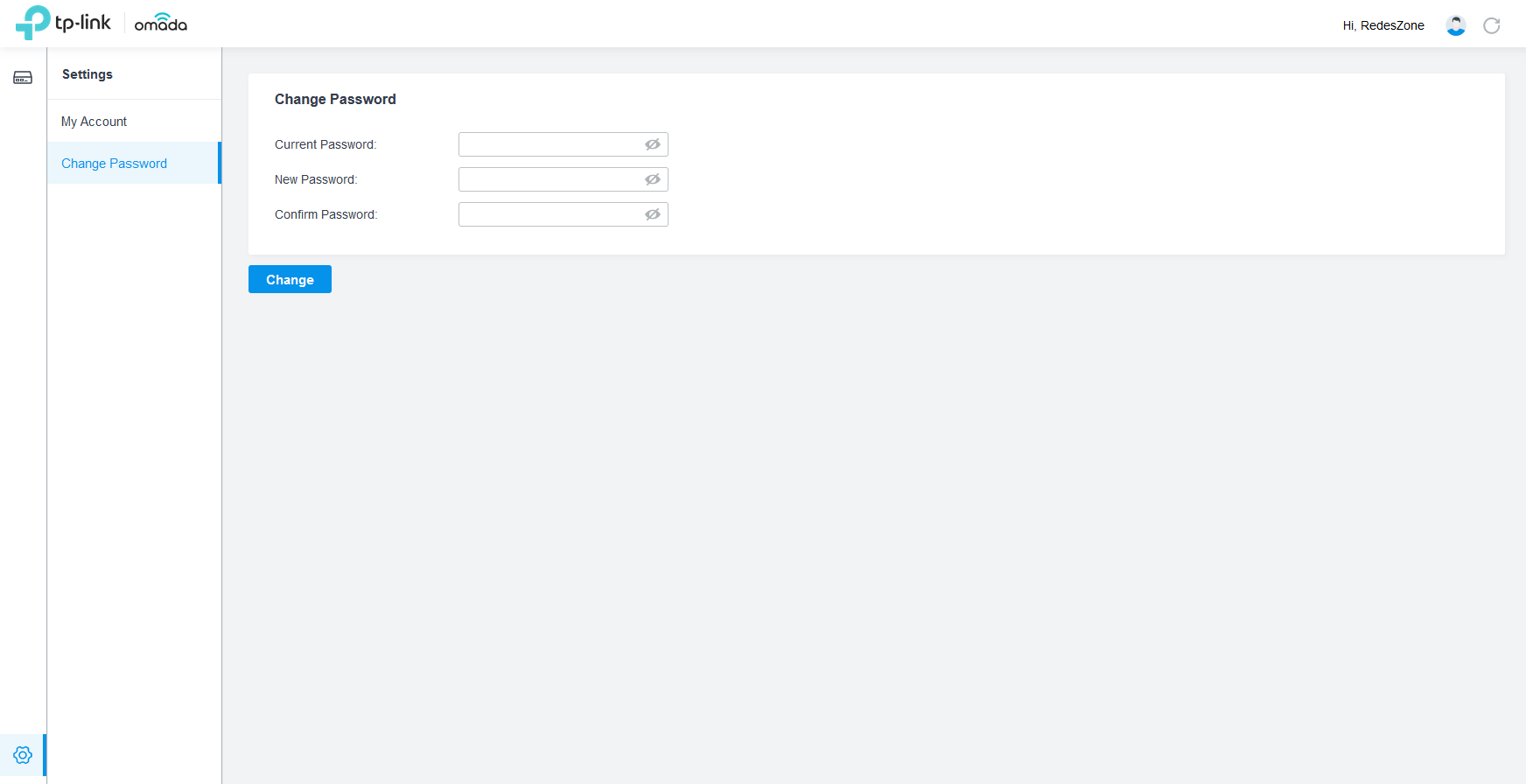
As you have seen, in a Cloud management environment it is not only very important to protect the local network against possible attacks, but also the manufacturer’s own management in the cloud. It is very important to use a strong access password, and activate two-step authentication if we have it available. Nowadays, the most normal thing is to find a platform where two-step authentication is supported, in this case, we have seen that TP-Link Omada does not have this basic security functionality.