The NTP (Network Time Protocol) and SNTP (Simple Network Time Protocol) are two fundamental protocols for the proper functioning of the Internet. Both protocols allow all the devices on a network, such as computers, servers, switches, routers, Smart TVs or any other device connected to the Internet, to be able to have the correct time on your system, with the aim of not having problems when browsing. online or perform any task. Today in this article we are going to explain in detail both time protocols, the differences between NTP and SNTP and also how they are configured in the different devices.

What is NTP (Network Time Protocol) and how does it work?
The NTP protocol is the first protocol that was launched to synchronize the clocks of the different computer systems , NTP not only works on computers or servers, but they are a fundamental part of routers, switches, WiFi access points and any type of network equipment, such as firewalls. NTP was one of the first Internet protocols that was born in 1981, and it is still used to synchronize the clocks of different computer systems. The NTP protocol allows you to synchronize the time with different NTP servers that are deployed all over the world and that are accessible through the Internet, in addition, the NTP protocol allows you to synchronize the time even if we have a very high or variable latency, since it incorporates mechanisms to avoid time lags due to this latency.
The NTP protocol makes use of the UDP transport layer protocol on port 123 to communicate with the different NTP servers around the world . A very important detail is that this NTP protocol makes use of UDP port 123 both in the source port and in the destination port, so we must take it into account if we have devices behind a firewall or if there are control lists of access in the different manageable switches of the local network. If you have a device that uses the NTP protocol, and a manageable switch with the different network attacks enabled, you need to disable the ” Blat Attack ” attack for the NTP protocol to work properly. This «Blat attack» consists of blocking TCP or UDP packets that have the same source and destination ports, exactly what NTP does when using UDP 123 source and destination ports. Therefore, we must take it into account at the time to configure our network.
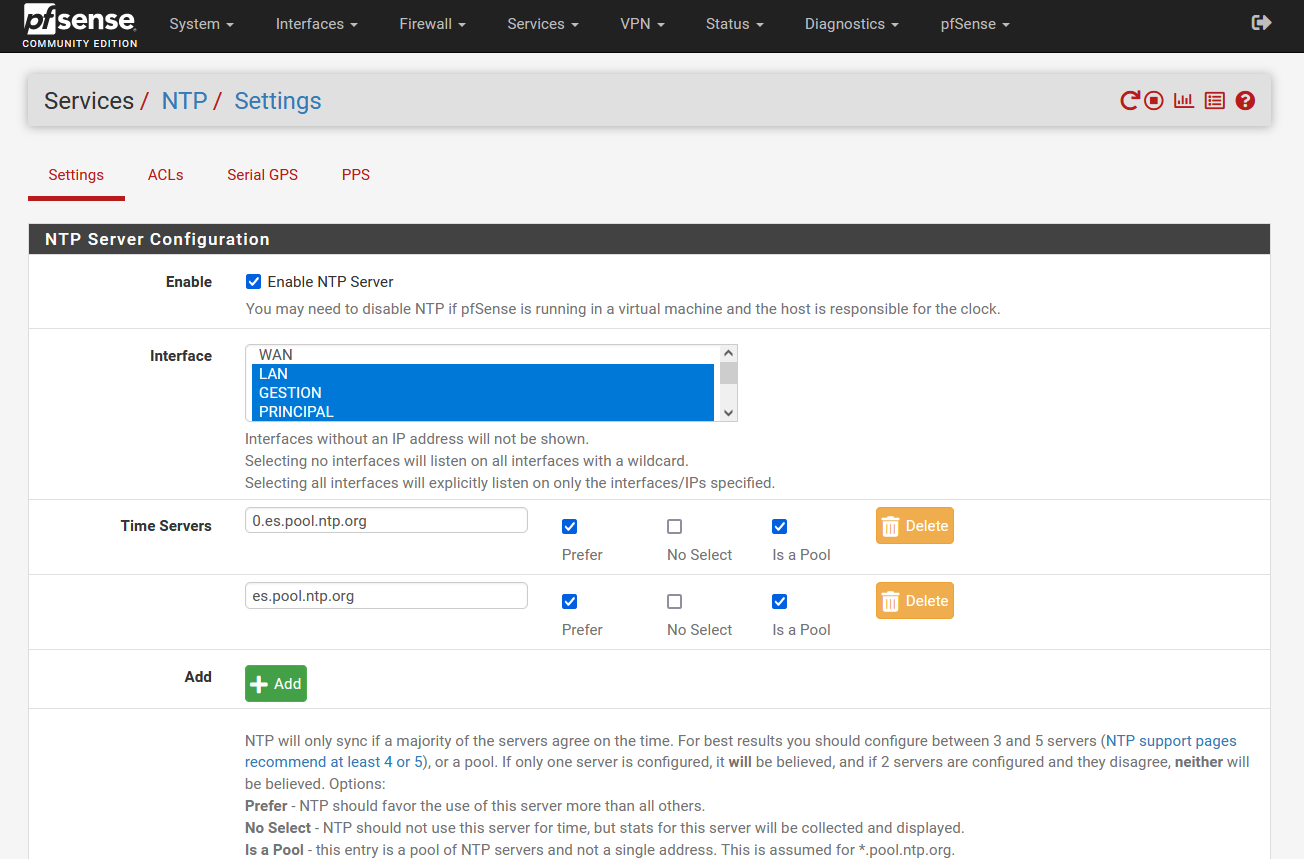
The current version of NTP is version 4, since, over time, this important protocol has been updated and improved. The NTP protocol makes use of the UTC time scale (Coordinated Universal Time), including support for leap seconds, in addition, the latest version of NTP allows to stay synchronized with a maximum difference of 10 milliseconds through the Internet, in the case of being on the local network it is possible to approach up to 200 microseconds of accuracy, although it will depend on how your network is configured. In different operating systems such as Windows, Linux or macOS, the NTP protocol is always running to correctly synchronize with the time servers.
Over time, security problems related to the NTP protocol have been detected, both in the implementation in the different operating systems, in the NTP clients of the different computers, as well as the intrinsic security of the protocol itself, which it does not use. any type of authentication or data encryption for the exchange of messages. NTP servers are susceptible to Man in the Middle attacks, unless the packets are cryptographically signed, the same goes for the computers themselves, it could perform MitM attacks to modify the time on the end computers. The NTP protocol sends all the information in plain text, it does not have any type of encryption, authenticity or the integrity of the data is checked. To avoid this, the Network Time Security (NTS) protocol has been designed, which is the secure version of NTP using TLS and AEAD to protect communication, and that no one can impersonate an NTP server to misconfigure the time on our system .
What if I don’t have the correct time on my system?
Keeping the correct time on a computer system is very important, otherwise some software might not work, and it might even carry out some computer attacks on us. If in our operating system we do not have the time configured correctly, we could have the following problems:
- Impossibility of browsing the Internet with any web browser, depending on the configured time, it will continuously indicate errors in the different SSL / TLS certificates of the webs.
- Problems with some software that needs the correct time to work.
- We could have problems with Windows updates.
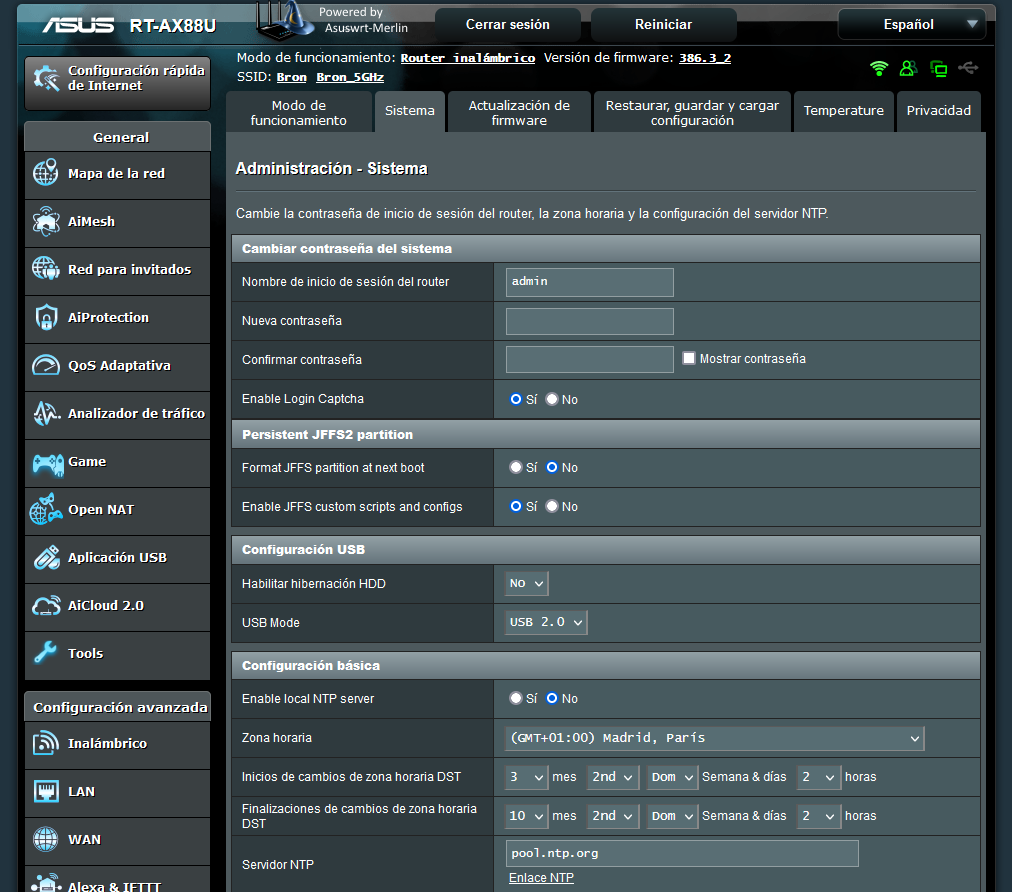
In routers and firewalls, not having the correct time also means not being able to establish VPN tunnels if digital certificates are used, because it is possible that the time is outside the date and time of creation of the certificate or its expiration, in addition, all the records they will appear with an incorrect time, so we must also take that into account. In the case of the NTP-manageable switches we have the same, we could not see the records correctly with their date and time, nor could we program the PoE to turn the access points on and off. Finally, another network equipment that could be harmed are the WiFi controllers, we could not see what hours there is more traffic, because the time is wrongly configured.
As you can see, we have many problems when it comes to not having the correct time in a certain computer system.
What is SNTP (Simple Network Time Protocol) and how does it work?
The SNTP (Simple Network Time Protocol) protocol is a less complex implementation of the NTP protocol , it uses the same protocol and serves the same purpose. This protocol is widely used in embedded equipment such as home routers or home switches, where the full capability of the NTP protocol is not required. Currently the protocol used is SNTPv4 and is defined in RFC4330.
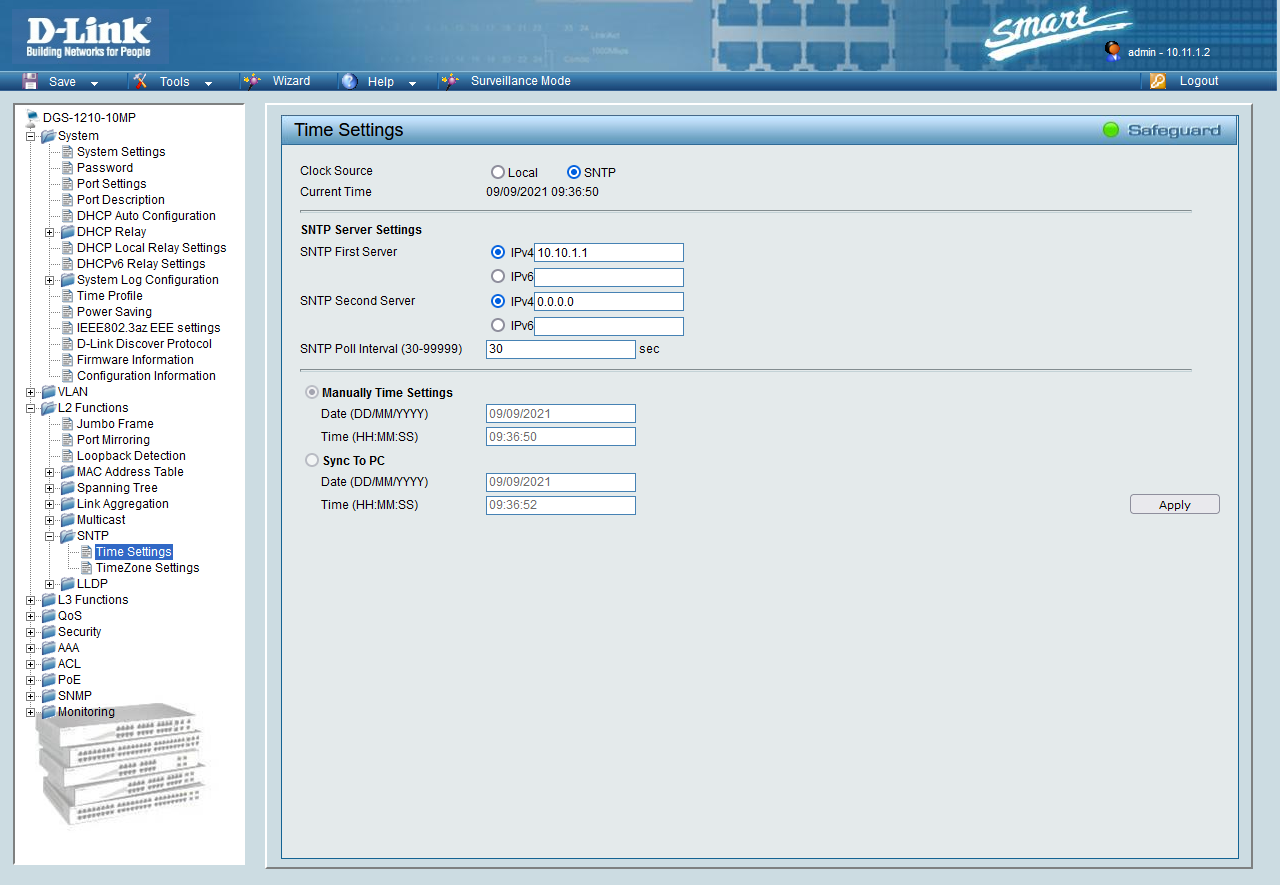
SNTPv4 allows simplified access for servers and clients that use current and previous versions of NTP and SNTP itself, access is identical to the UDP / TIME protocol, so adaptation should be very simple. This protocol is designed to work in a dedicated server configuration that includes an integrated clock radio, in addition, latencies have been improved and controlled, the exact time can be entered in several microseconds without any problem.
SNTP has evolved over time, improving its performance and also its compatibility with the different underlying protocols. For example, the only significant change in SNTPv4 compared to previous versions are the headers to adapt to the IPv6 protocol. Some optional extensions have also been added to the basic NTP Currently, when we configure the NTP server in the different NTP clients that exist throughout the world, the operation and the exchange of information can be carried out both using the NTP and SNTP protocols, the operation it is the same since we have compatibility.
Differences between NTP and SNTP
The main difference between NTP and SNTP is that the latter does not require any type of state storage for very long periods of time, something that the NTP protocol does. A very important difference for network administrators is the operation of communications, to allow or deny traffic on firewalls or create access control lists on manageable switches.
The NTP protocol works with the UDP protocol on port 123, this UDP port 123 is used in communication both at the source and also at the destination. As we have explained previously, if you have activated the «Blat attack» in the switches, and you have a device that uses the pure NTP protocol, it is surely blocking the traffic only from the NTP without your knowing it.
The SNTP protocol works with the UDP protocol on port 123, the communication uses a random UDP port as the source , and the UDP port 123 as the destination. According to the SNTP standard, the source port can be anything but 0 in order to perform multiplexing, of course, the server answers correctly on the source port chosen by the client in the first communication so as not to have problems with the NAT that they have the routers. The objective of this important change is to allow the identification of a specific client, so as not to have problems with NAT, and to prevent the switches with the Blat Attack activated from blocking communications.
As you have seen, the NTP and SNTP protocols are two fundamental and very important protocols for computer systems, it is essential to have the time configured correctly, either in your desktop operating system or in the different network equipment you have.