
There are many scammers who take advantage of Internet vulnerabilities to affect as many people as possible. The more people they harm, the more benefits they will get. Companies always try to update their software to the latest version. However, there are people who forget this and that is where cybercriminals take advantage to carry out their cyber attacks.
The Atlas VPN service has carried out a study on the most vulnerable products of two large companies such as Microsoft and Google during the first six months of this year.
Google and Microsoft, the most affected
Cybercriminals were able to do serious, though not critical, damage. The Atlas VPN report is based on mobile security and the most common weaknesses in cybersecurity today. This graph shows the companies that have suffered the most cyberattacks.
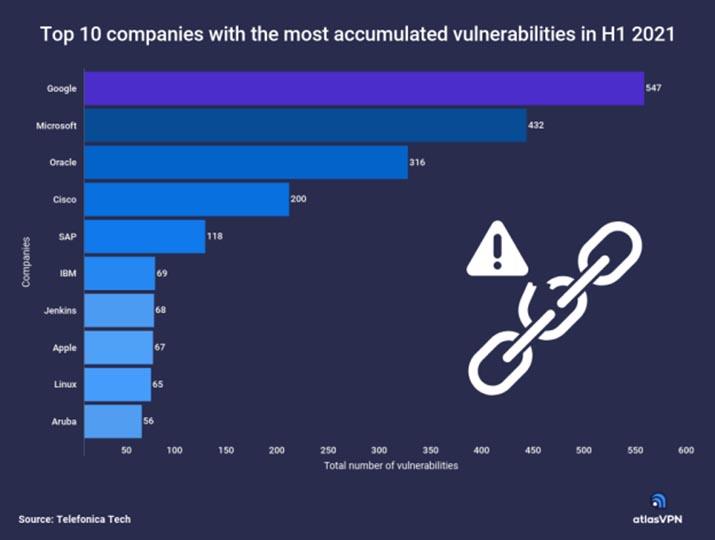
In the case of Google , the company had up to 547 vulnerabilities during the first half of the year. The most exploited product by hackers was Chrome. This is one of Google’s most popular products, as it is the browser used by millions of people around the world. By using it so many people, many of these people who use it can become victims of a scam.
Microsoft suffered a total of 432 vulnerabilities . Specifically, Microsoft Exchange Server was the service that had the most ransomware attacks. Oracle also recorded up to 316 vulnerabilities in total. Most of the attacks took place on Oracle WebLogic Server, which is a platform for developing, deploying, and running Java-based business applications. Bugs can lead to cybercriminals making remote attacks.
On the other hand, the network hardware company Cisco had up to 200 vulnerabilities. Finally, the producer of software for the management of business processes SAP had a total of 118 vulnerabilities.
Attacks with different level of danger
All of these attacks do not have to have a critical effect on the business, but most are notable for their relevance or danger. Vulnerabilities that can become a serious attack receive increased attention from hackers and companies to correct the attack in the shortest possible time. In the following image you can see the different attacks according to their level of danger.
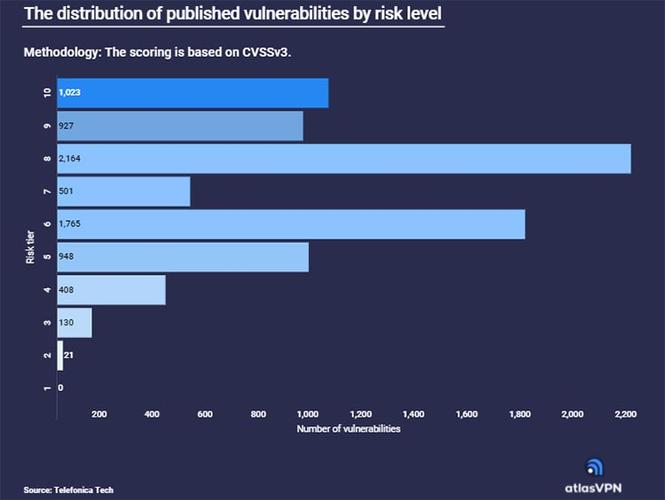
Of all the vulnerabilities found in the first half of 2021, a total of 1,023 had a risk level of 10. The vulnerability was found in the security company’s F5, BIG-IP and BIG-IQ services. With the attack, complete control of the system was gained.
The National Vulnerability Database found 927 Level 9 attacks. The weakness was found in the firmware of the Draeger X-Dock gas detector which is responsible for storing encrypted embedded credentials. With the extraction and use of the credentials, a hacker could execute arbitrary code on the system.
The highest number of vulnerabilities detected would be level 8, with 2164. The bug was found in Windows Defender, which, in fact, had not been discovered for 12 years until now, so it was attacked. By attacking this program, a cybercriminal could gain the privileges of a user other than an administrator.
Finally, there were 501 level 7 vulnerabilities and 1,765 level 6 vulnerabilities. The latter have too low a level of danger.
Cyber attacks on Google or Microsoft products allow cybercriminals to track millions of systems. However, large companies continue to work to have the best possible security systems that allow these cyberattacks to go in vain.