Typically, most users set up an unlock method first. However, there are people who may be overconfident. The problem is that anyone in our environment could at one time or another pick up our phone and look at what they want, invading our privacy. Even people who share your passcode could be making a huge mistake.
Today, we can check in different ways if someone has been able to pick up our phone without permission and gossip about everything we have stored. For this reason, we will explain each of the options that will be within our reach to find out if someone other than us has used the phone. We will even give you extra help to know specifically who has spied on our mobile.

From the settings
First of all, we will not always have to resort to applications in our phone’s app store to look for software that helps us find out who is the culprit, but it will be easier to know from the different options that we have in the settings of our device mobile. And it is that there are some simple possibilities to know the time of use , or even, using logic. Therefore, pay close attention.
In battery options
The first trick that we will have up our sleeve will be the battery section itself of the device settings. Within this, we will find different sections that are related to optimized charging, energy saving … Among many other options. However, the one that interests us is the first one that will appear called Usage Details.
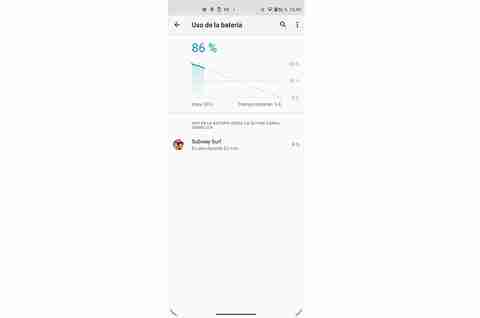
Once we click on this button, we will enter a menu in which we will see the percentage of the battery that we have left, as well as a graph of the energy that the mobile device has been using. Although, the most interesting detail is that it will show us the use of the battery since the last full charge . That is, we will see the applications that have been used, as well as the time that they have been used. In addition, it will be in order, this means that, if you have used a game for the last time, the first one on the list will appear.
With Digital Wellbeing
Although our great ally in these cases will be the Digital Wellbeing section of Android phones. In this tool, we will have a Control Panel in which we will see a graph of the time of use that we have made of the phone. In addition, if we click on the time, it will allow us to view a graph for each day. And not only this, but we will see the number of times a specific application has been opened.
So this option will be ideal if we distrust that someone is on our phone to see our social networks or our WhatsApp conversations. And the best of all is that, if we click on each one of them, we will see the approximate time in which it has been opened through a graph, as we can see in the following image.
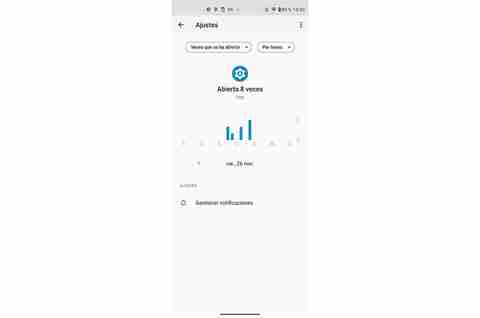
Open apps
If you are one of those who never close apps, you may have bad or good luck. It will also depend on the memory you have. And, if you open multitasking to see all the apps, you will be able to see the latest apps that have been opened on your phone. For example, if in a day you had not opened Twitter a single time, but suddenly you see in the multitasking that it has been opened, I am sorry to tell you that someone has used your phone without permission.
How to avoid it?
It is clear that the simplest option is to use a blocking method. However, not a few users use too simple a pattern or password. So we must not only rely on these types of unlocking. Therefore, we will give you two clear ideas with which you can ensure that no one else can use your phone, you will even discover who has tried to access your mobile.
Lock method
This is one of the first options that any phone offers us when we configure it for the first time, so it will be for a reason. Basically, we will be safeguarding all our data, not only of the people we live with or when we are at work, but it will also be good to have an unlocking method so that, in the case of theft or loss, no one can have access to our telephone.
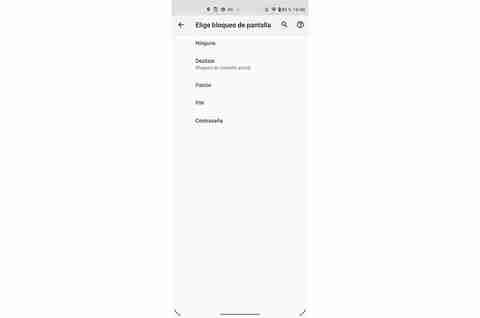
Therefore, we recommend that you configure it as soon as possible so that your new mobile is totally safe. Therefore, it will be the turn to configure the protection of the device so that no one saved can access the phone. In addition, mobile phones offer us different possibilities for this, although it will also depend on the technology of the device itself, but as a general rule we can configure a fingerprint sensor, facial recognition, pattern, PIN and password.
And not only this, but we can combine a fingerprint + pattern / PIN / password (to use the latter in case the fingerprint does not work well) or Face unlock + pattern / PIN / password (same as in the previous case) . Therefore, we recommend using one of these options, but it will be important to establish a complicated pattern, as well as a PIN or password that is difficult to guess.
Anti-spy apps
Apart from all the mechanisms that mobile devices offer us to know if someone has been able to use our mobile phone, as well as there are tools for our own within the terminal software to avoid this, we may need extra help to find out who he is. gossip ‘ who does not stop picking up the phone.
Within the world of apps, we will find different applications with which we can have direct evidence, and at all times, if someone has tried to unlock our smartphone. For example, automatically taking a selfie of the culprit. To do this, we bring you two options, ‘ Who has taken my mobile? ‘and’ Third eye ‘.
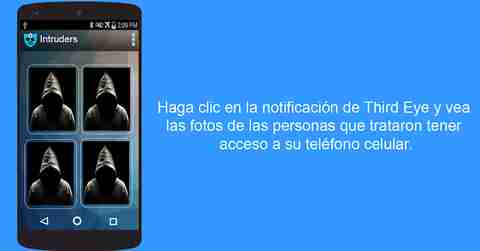
Both apps work the same way. These apps will ask us for a series of permissions in order to function correctly. Also, both options are free. But, the most important thing is that we will be able to record the number of times that an attempt has been made to unlock the smartphone and it has failed, so, depending on the number of attempts, an automatic photograph will be taken. If you want to do the test yourself, here are the links to download them: