The BGP (Border Gateway Protocol) is one of the fundamental protocols of the Internet, since it is in charge of exchanging routing information between the different autonomous systems that exist in the world. For example, each Internet operator has its own AS, and to communicate with another operator’s AS, you need to use the BGP protocol.
If this protocol is not configured correctly, it could cause interruptions on the Internet, or the traffic routes could be changed so that all the traffic from a certain AS passes through another without requesting it. Cloudflare has launched a free tool to check the security of the BGP protocol easily and quickly.

BGP protocol: what it is, what it is for and how it works
The Internet is divided into autonomous systems (AS), an autonomous system is a set of routers from the same operator that exchange routes between them to get from an origin to a destination. It is essential that an operator within his AS, has perfectly updated routes, since otherwise, we could have loss of connectivity to a specific destination.
An AS is like a “small” Internet that only allows the operator in question to communicate, for example, if you are a Movistar client and want to communicate with another Movistar client, all traffic will pass through the AS, not going out to the Internet ( in principle, it depends on how it is configured). For example, each operator in Spain has at least one autonomous system (they could have several AS at their disposal).
Within an autonomous system, the routers of the operators exchange the different routes to get from one origin to a destination internally, without using other AS. The routing information is provided dynamically by routing protocols interior gateway (IGP – Interior Gateway Protocol), this routing is internal to the AS itself, and make use of specific protocols such as OSPF or IS-IS in the vast majority of cases, but there are also other IGP protocols such as RIP or EIGRP.
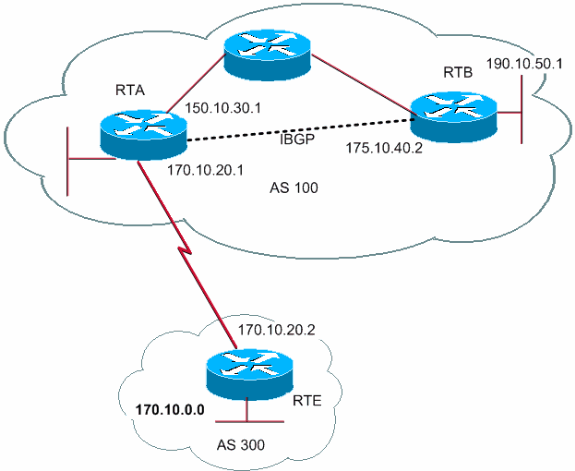
The BGP (Border Gateway Protocol) is an external , external gateway protocol or is also called a “border”. This protocol is used to exchange routes between different AS , this task is essential so that we can have connectivity from one source to a destination, when traffic must pass through different AS.
For example, if our operator is Movistar and we want to communicate with someone who has Vodafone, it is necessary that our traffic goes through the Movistar AS and also that of Vodafone to reach its destination correctly. While IGP protocols share routes within the AS, BGP is responsible for sharing routes to other ASs to have connectivity between different operators.
When we are configuring a BGP protocol, we will have both internal connections (iBGP) that are made within the AS, as well as external sessions (eBGP) that are made between different AS.
Some characteristics of BGP are that it guarantees a choice of loop-free routes, it makes routing decisions based on the network policies that are defined (traffic engineering), such as the number of AS jumps from origin to destination, although We can use the LOCAL-PREF attribute to modify this behavior, the routes can also be modified based on other attributes that exist in BGP.
Why is BGP not secure?
The BGP protocol, if not configured correctly, can lead to attacks like the BGP hijack. If you have to go through B to get from source A to destination C, it is possible that node B will “trick” node A to make its traffic go through a different AS, or that it will not directly provide you with the correct route and run out of connectivity, because you can’t get to C in any way if B doesn’t provide you with the information. The BGP Hijack works exactly like this, hijacking the BGP session and sending false information to an AS so that it never reaches its “neighbor”, or that it arrives in a malicious way (passing through a router of another AS under our control, for example) .
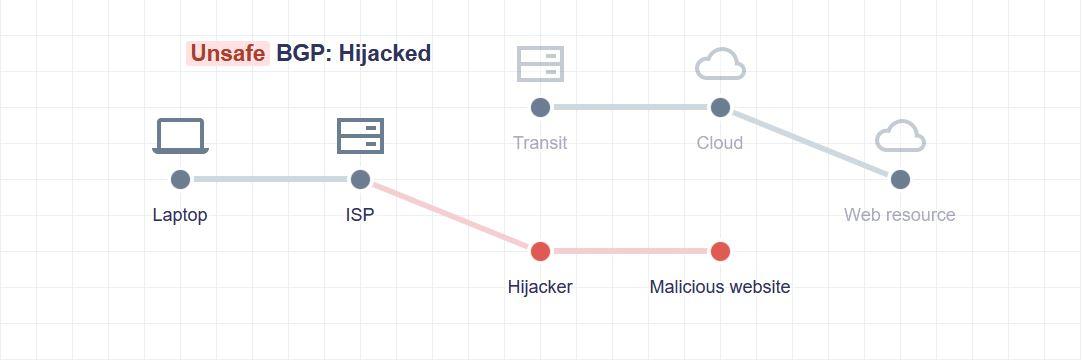
In order for BGP to be secure, we must protect the propagation of routes in a malicious or erroneous way (due to human failure, we may leave connectivity to an entire AS). It is essential that the different BGP routers have the possibility to validate the information they receive in some way, so that they can reject these unwanted routes on their own, and not change their routing.
By default, BGP does not incorporate any security protocol to avoid this, the implementation of incorrect route filtering depends on each AS. Normally when we lose the routes it is due to human failure, but it could also be due to the action of a cyber criminal, as has happened in the past. BGP can be secure if all ASs advertise only legitimate routes, that is, when they are “yours”.
RPKI to the rescue
RPKI (Resource Public Key Infrastructure) gives us the solution, currently there are millions of routes on the internet, so checking them manually is an impossible task. This security framework is capable of associating a route with a specific autonomous system. RPKI uses cryptography between the different BGP routers so that the nodes validate the information in a secure way before passing it to the routers, to ensure 100% that it is a legitimate route. We recommend you read more about RPKI on the Cloudflare blog where you will find technical information.
How the tool works to detect if our ISP uses BGP with RPKI
This tool is in charge of checking if our operator is implementing BGP in a secure way, what it does is announce a legitimate Cloudflare route, but they make sure that this announcement is not valid. If we can load the website where we host that route, it means that we can reach it and that our ISP has accepted it as valid, otherwise, we will not be able to access it because the operator has marked it as invalid.
The first thing we should do is get on the web is BGP safe yet? and click on «Test your ISP», as you can see here:
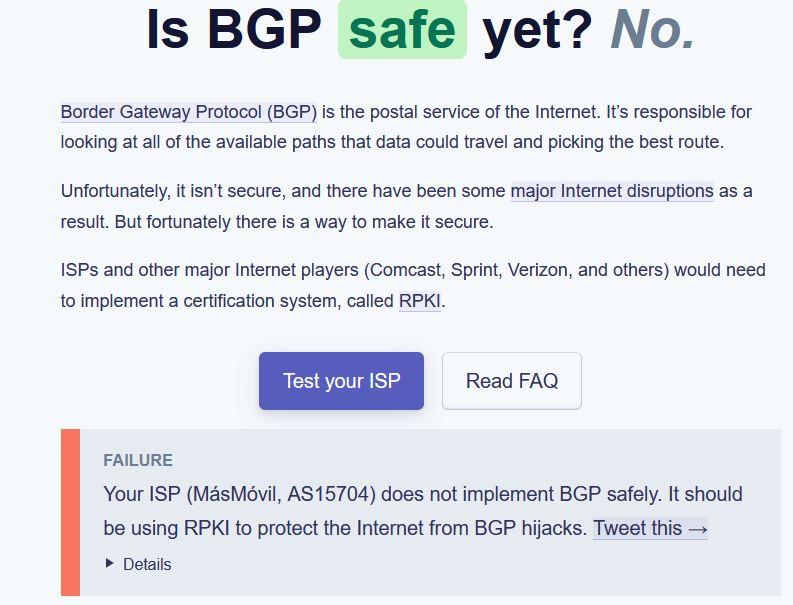
After a few seconds, it will inform us of the result of the test that we have carried out, our operator is Masmóvil, and it seems that it does not implement these BGP protections:
Just below, we will get a ranking with different Internet operators in the world, and it will indicate if they have BGP configured correctly or not. For example, other operators in Spain such as Vodafone, Orange or Movistar do not have these BGP protections either, judging by Cloudflare tests. Some operators (or companies with AS) that have done their job very well are Telia, NTT and also Cloudflare, although others such as Cogent or TATA are partially safe since they do peer filtering.