Without a doubt, e-mail has become a very important part of our personal and work life. In relation to our work, we use it to connect with our colleagues and also with other people to do business. Regarding our private life, it is also important because it may contain certain of our banking information, purchases or other sensitive information. Cybercriminals are aware of the potential of our email accounts, and they will try to trick us into using them. In this tutorial we are going to learn to know when an email is official or a threat.
A very important tool to distinguish if an email is official or a threat is common sense. In the same way that when we go down the street, we do not disclose our information unless it is strictly necessary, nor should we do so online. This is because they can collect information from us, for example, in forums and social networks and then carry out social engineering attacks.

Common sense is the first thing to use
An email can appear to us as something that we simply read and that has very little risk. Well, that is not true, since, on some occasions, through this route we can receive malware that ends up compromising the security of our computer. The first thing we have to do is carefully observe the sender of the e-mail . If it is a threat that it seeks to infect, they often have a strange direction. In those cases we usually find ourselves with many nonsensical numbers and letters. However, it is sometimes done in a more sophisticated way by trying to imitate a legitimate email address.

Also the subject of the message must be analyzed, observing if it makes sense and is expressed correctly. The next step we must take is to look at how the body of the message has been prepared . Here we have to look at a series of clues that can help us determine if the email is official or false. What can make us suspect that it is not to be trusted would be:
- Finding ourselves with a sentence with spelling mistakes, or that seems to be a bad translation.
- They play with urgency and ask that we take concrete action promptly.
- They ask for too much personal information from us
- We receive attachments, the most dangerous are the executables and are those with the extension .exe, .bat or .com.
Therefore, if we find this type of evidence in our mailbox, it is most likely a threat.
The danger of links in email and phishing
Sometimes we have doubts as to whether the email is official or not. So we have doubts about whether or not to click on that link. In this article, as a general rule, we recommend not clicking on that link until we are sure that it is legitimate. In addition, in case of doubts we can always do the same by entering through the official channels to that email account, social network or other type of service.
One of the most popular are Phishing attacks where the cybercriminal through deception techniques gains the victim’s trust by posing as a trusted person, company or service. We come across a case of identity theft whose goal is to make that user click on a link.

Thus, after clicking on that link, the victim is usually redirected to an attacker’s website with an almost identical appearance to the original, where they are asked to enter their credentials. Once you have done this, your username and password details are passed on to the cybercriminal. Sometimes, by hovering over the link, without clicking we can see that it takes us to a strange domain. Therefore, we realize that it is dangerous and we do not press it under any circumstances.
Analyzing the origin of the email to know if it is official
On some occasion you will have received an email from Google in which an incident has occurred or asks us to check something. The first step we usually take is to carefully observe the sender. In this case using the Google account we would see something like this:
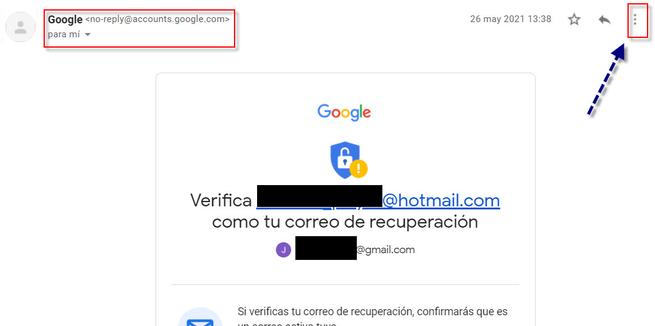
Before starting to do anything, a good idea may be to see if we find information on Google or on that person’s social networks or email. You don’t always get something, but sometimes it works. Then we will look closely at the email address and analyze it. Here we have to find out if any letter is missing or a subdomain has been added such as google-com.es or any variation that is strange to us.
Another way to get more information would be looking at the “header” or “header” of the email message itself. Here we have a lot of technical data that we surely do not know how to interpret or understand. However, one of the relevant data that it offers us is the IP address of the mail server from which the message was sent. If we want to see it, using our Google account in Gmail, after selecting the email that we want to check, we will click on the icon with the three vertical options points. Then we will click on “Show original” to see the header of that e-mail:
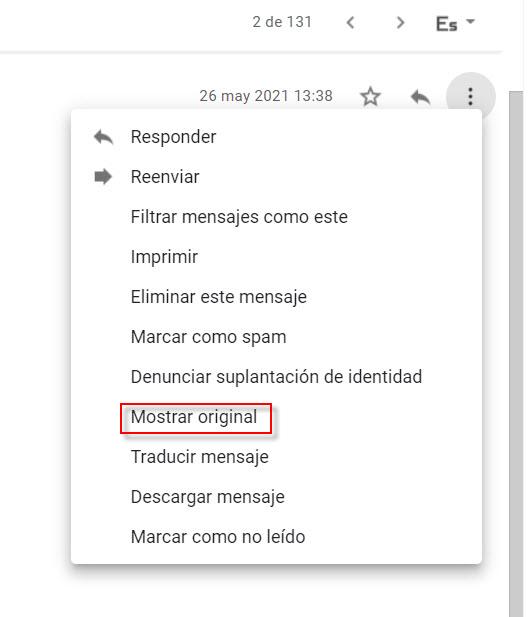
Here we have the results it offers us:
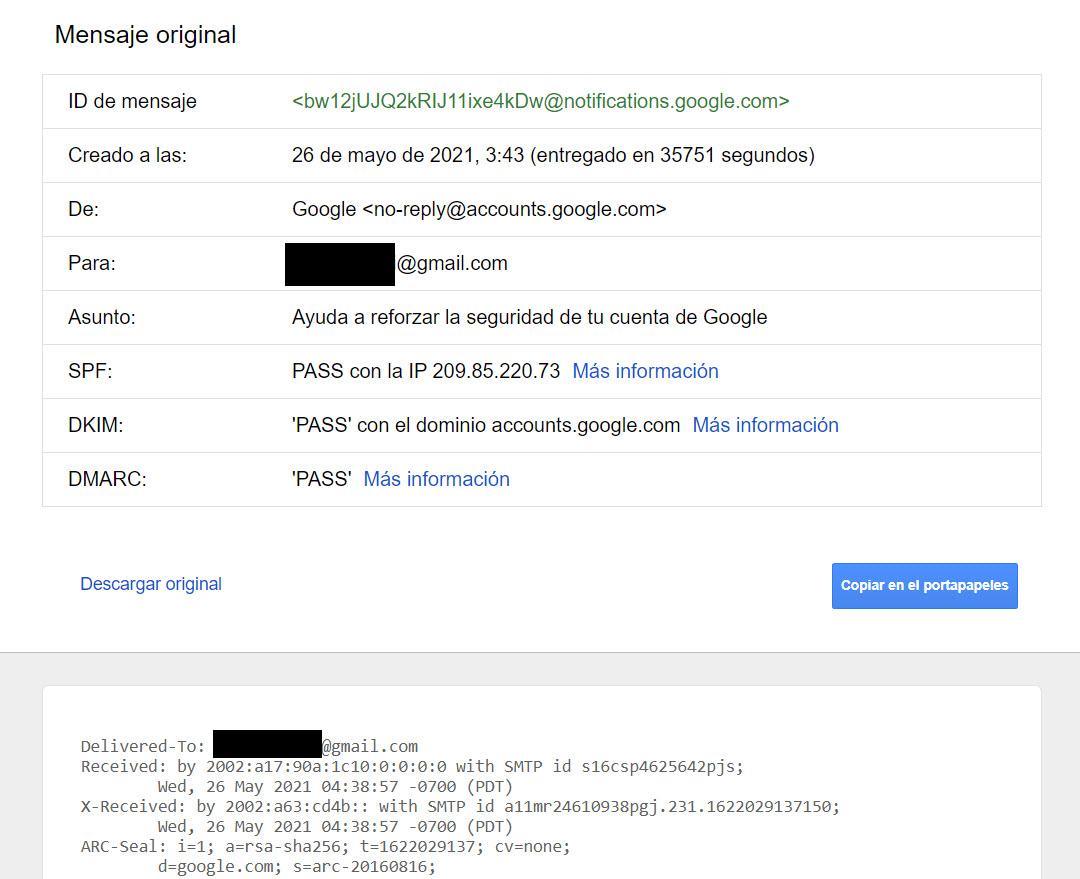
In this information we can see very important information to verify that an email is legitimate, such as the SPF, the DKIM and also DMARC. An important detail is that, if the email does not have these options in PASS, it could not be a real email. Normally important entities and large companies, have these characteristics enabled in their mail servers that indicate that they are legitimate emails.
We could also do the same in other mail clients such as Microsoft or Yahoo! as follows:
- Microsoft accounts such as Hotmail : we select the message to be investigated, we click the right mouse button to choose the View option, there we touch View message origin .
- Yahoo Mail : we choose a message, click on More , there we select See plain message .
Suspicious emails and threats to our security
We do not always find that this email is official, sometimes it is dangerous. Sometimes it may just be spam or junk mail. However, we must not be careless because sometimes they are Phishing attacks. Other scams are where we are promised a grand prize in a contest that we have not participated in, or incredible offers. This would be an example of this style and what we would see in the subject of the email:
![]()
The message that it shows us if we open it is the following:
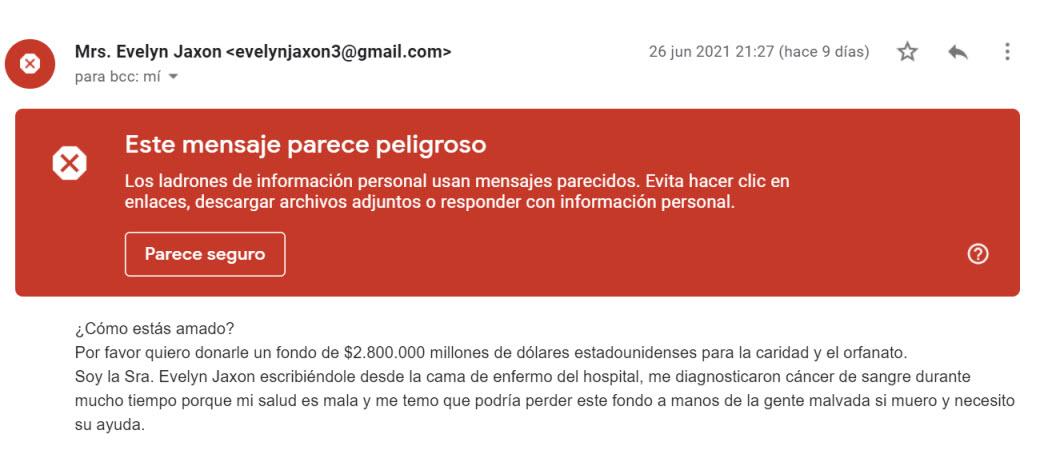
Here our Google account alerts us that it is not convenient to respond with confidential information or download attachments. In addition, it can be intuited that the text seems translated, and since the name is in English, it gives more reasons to believe in it. If we continue investigating using the Google search engine, we see how there are websites that classify it as a supposed scam:
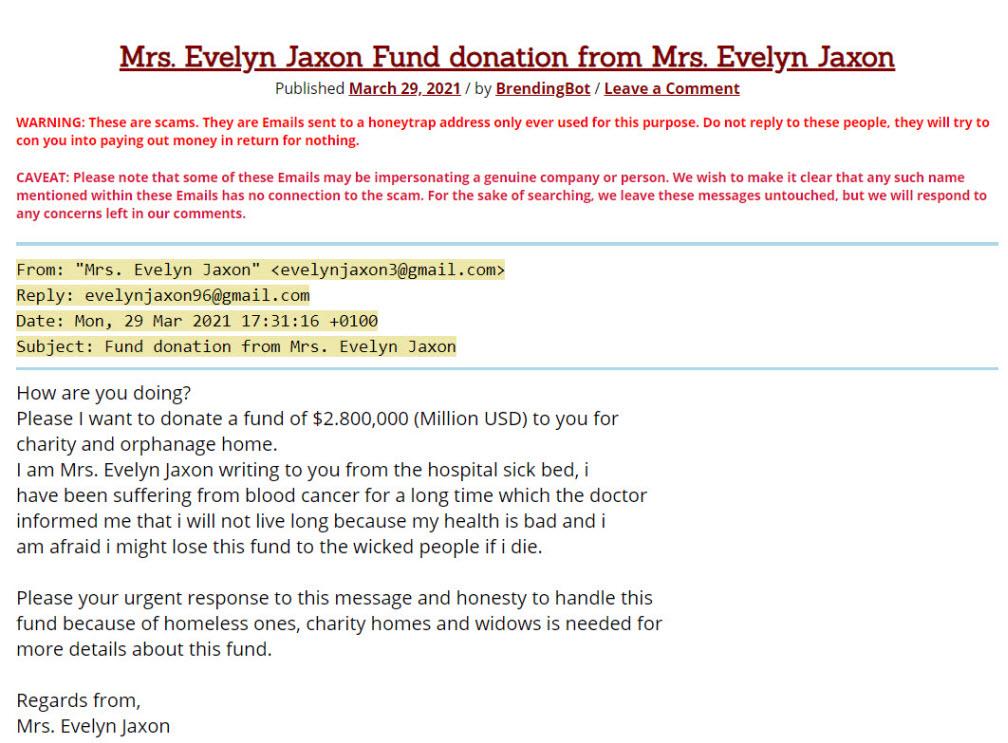
On the other hand, other tools that we could use to contrast an IP and domain would be using Who.is. By using it we will be able to obtain information as interesting as the owner of the domain.
Finally, to find out if an email is official from an entity or company, or a scam, we could use Hunter , a free online tool with certain limitations. Thanks to it, we can find the email address of the employees of a company. It offers us 25 free searches per month.
We will do it from its web page , and after the search it will offer us a list with all the e-mails of its workers, in this way, we can see if a certain sender of the e-mail really belongs to a company or not.