There are many threats that in one way or another can put our computers at risk. We can be victims of very varied attacks and it does not matter what type of operating system or device we use. In this article we are going to talk about keyloggers . They are a very present problem in the network and that can compromise passwords. We are going to explain how to know if we have a keylogger in Windows and, most importantly, how to avoid it.
What is a keylogger
A keylogger is malicious software that has been designed to collect keystrokes from passwords that a user enters into the system. It is one more technique for key theft.

Keep in mind that this type of threat can be present on different operating systems and devices. However, in this article we focus on Windows as it is the most used on desktop computers.
It can infect us in many different ways . For example, we can receive a malicious file by email, download software from insecure sites that actually turns out to be malware, fraudulent links on social networks … In short, the methods that can be used to sneak this type of malware are different.
Therefore, we can say that a keylogger is software created maliciously to record keystrokes . They can collect our keys for a wide variety of services such as email, applications, social networks, online services … In addition, we must indicate that not only passwords, but also bank account keys or any PIN that we use.
How to detect keyloggers in Windows
It is very important that we know how to detect these types of threats so that they do not affect us. If we are victims of this problem and before it can act we have found that it is present in our system, we can avoid compromising our passwords. Luckily we can take into account some actions in Windows for this.
Use task manager
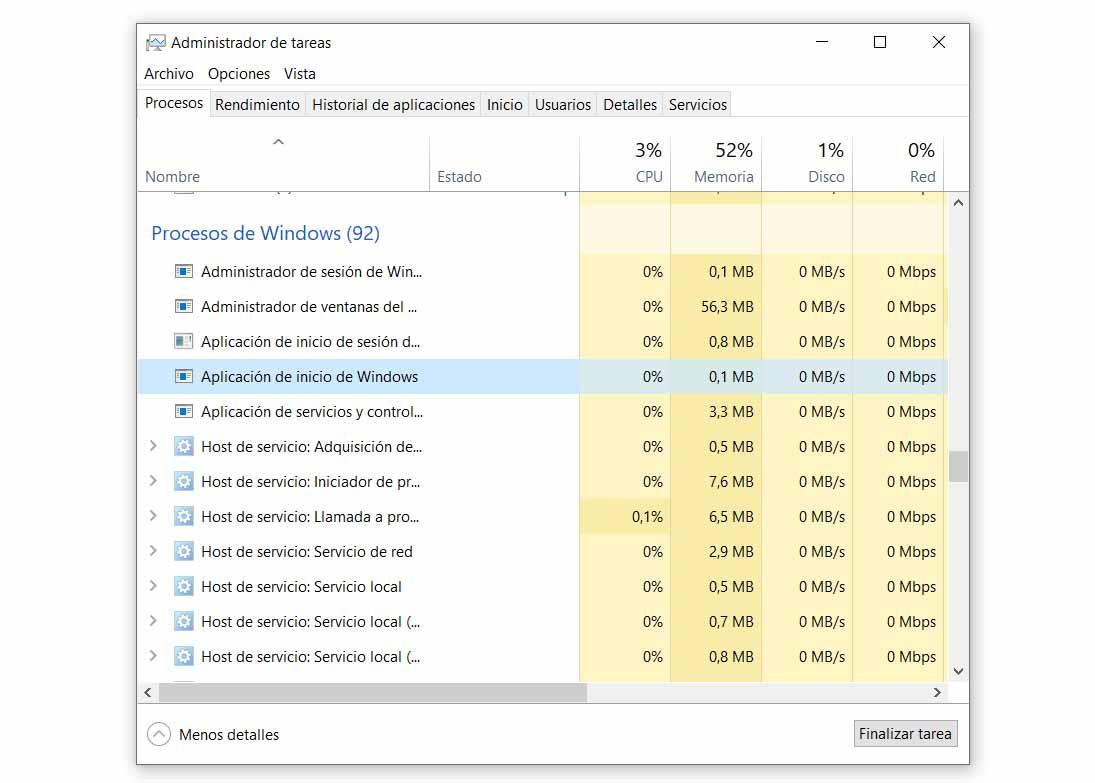
One of the options is to use the task manager . There it shows us all the programs and processes that are running. Tools such as the browser or any application that we are using will appear. But it can also show us processes that are foreign to us.
Is there something running that it shouldn’t? A very common clue is when we find the Windows Startup application process duplicated. It is within Windows Processes. In case we see a process called Windows Startup Application (1) or similar, it means that someone may be within our team. It could be a keylogger.
Detect threats with antivirus
Another classic option is to use an antivirus to detect threats. We already know that there are many security tools that we can use. There are both free and paid and for Windows there are a large number of alternatives.
The idea here is to run a full scan of your computer to detect potential threats, malware, and problems that may exist. One more way to detect a possible keylogger in the system in time.
This is something that we must do periodically, but also whenever we detect an anomaly in the equipment, a malfunction, the installation of a program, etc.
Use the command line
We also have the ability to use the Windows command line to detect suspicious Internet connections. For this we go to Start, we write CMD and we execute the Command Prompt.
We have to run the command netstat b . There will appear all the websites and Internet applications connected to our computer. We can see the IP addresses to detect some unknown and suspicious remote location.
View installed suspicious apps
It is possible that when installing a program some additional application is hidden. Have we seen anything suspicious? A keylogger may be hidden in an application that we have installed and we don’t really know why.
Therefore, it is always convenient to review all the programs that we have installed. A way to control at all times that there is nothing strange.
How to avoid keyloggers
Now we are going to move on to the most important point: how to avoid being a victim of keyloggers. The objective is none other than to avoid being infected by this type of malware that can seriously compromise our security.
Use security tools
Something fundamental is to use security tools . We have many at our disposal. Many antivirus that are available for all types of operating systems and devices.
Having programs that protect us is very important to prevent the entry of malware, but also to detect and eliminate it. Therefore our advice is to always have this type of software in our systems.

Keeping equipment updated
Another very important issue is keeping the equipment properly updated . On many occasions, vulnerabilities emerge that are exploited by hackers to exploit them and carry out their attacks.
It is essential that we always have the latest versions installed. In this way we can avoid problems that affect not only performance, but also security. One more way to avoid keyloggers in Windows.
Install official software
As we have mentioned, on many occasions keyloggers arrive through programs that we have installed. To prevent this from happening we must install software only from official sites .
It is true that sometimes we can access a wide variety of software on third-party sites, but they are not always guaranteed. It is important to make sure that what we are downloading is legitimate.
Common sense
Last but possibly most important, common sense . These types of threats usually enter through mistakes made by users. It is essential that we take care of the way we browse, that we do not download files that can be dangerous by mail or that we do not access fraudulent pages.
If we always keep common sense in mind, we can avoid many problems that compromise our systems.