If in Windows 10 we do not install any firewall on the computer, the Windows firewall itself will act by default. Today in this article we are going to show you each and every one of the configuration options that we have available in the Windows 10 firewall. We can create different input and output rules, with different protocols, and applied to different types of profiles (domain, public and private), so we will have a high configurability.
Accessing the Windows 10 Firewall Advanced Menu
The first thing we must do is access the advanced configuration of the Windows 10 firewall. To do this, we go to «Control Panel», and click on «Windows Defender Firewall». We can also choose to write the word “firewall” in the Windows search bar, and it will automatically take us to the main menu of the Windows 10 firewall.
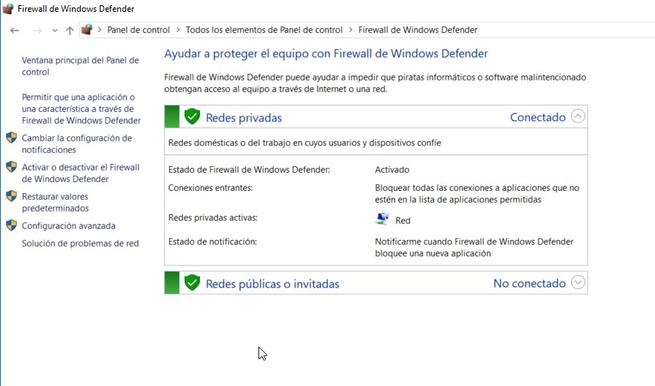
Once we are in the main menu of the Windows firewall, we can see if we are connected to private or public networks, and the policy of action that we are having in those same moments. In the main menu of the firewall we must click on ” Advanced Configuration ” which is on the left side of the menu.
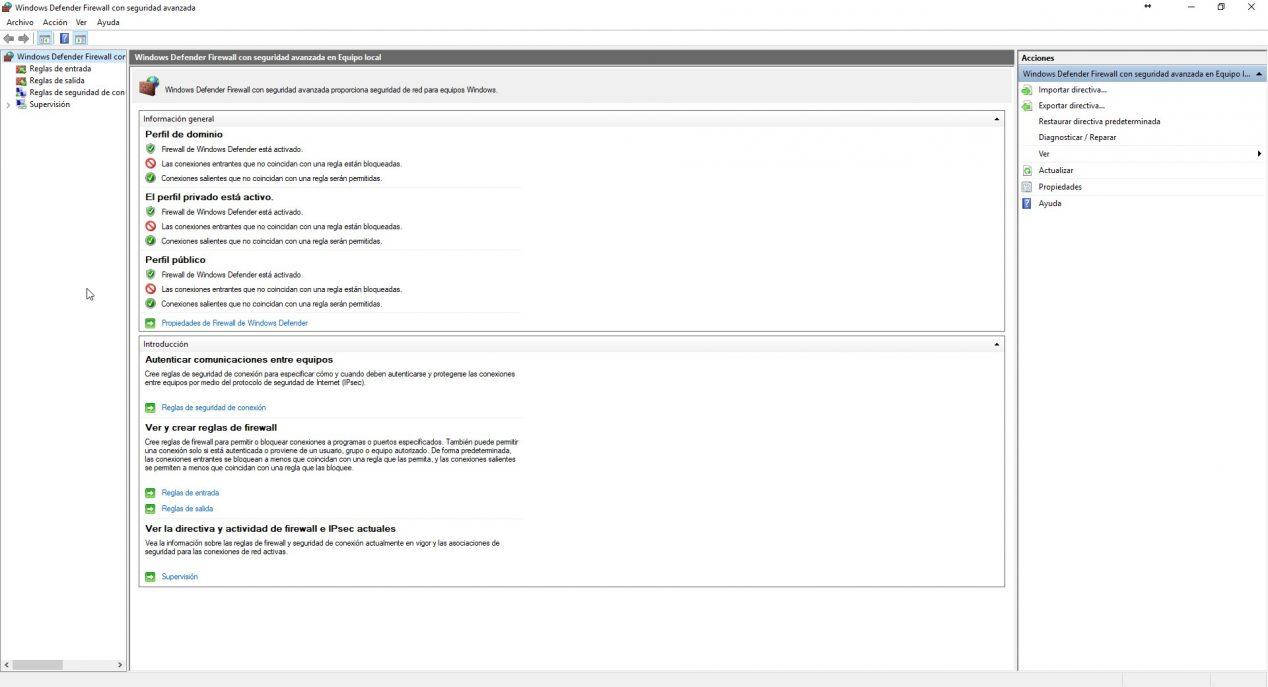
In the advanced configuration menu of the Windows 10 firewall we will have access to all the inbound and outbound rules, and the summary of all the rules created both inbound and outbound in the firewall.
Advanced firewall configuration Windows 10: Main options
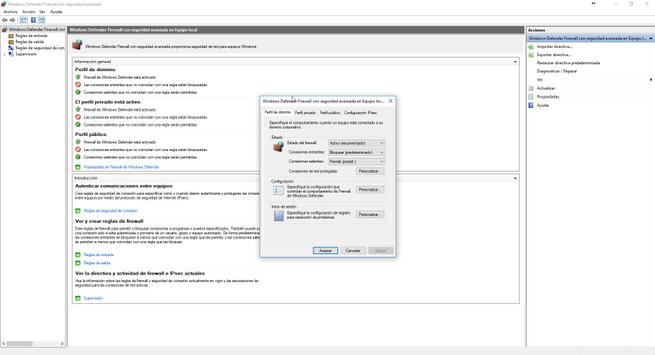
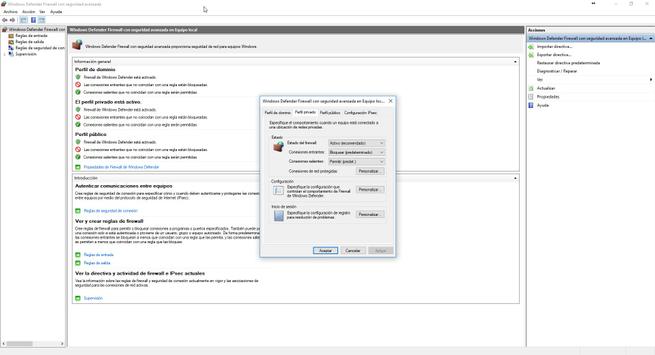
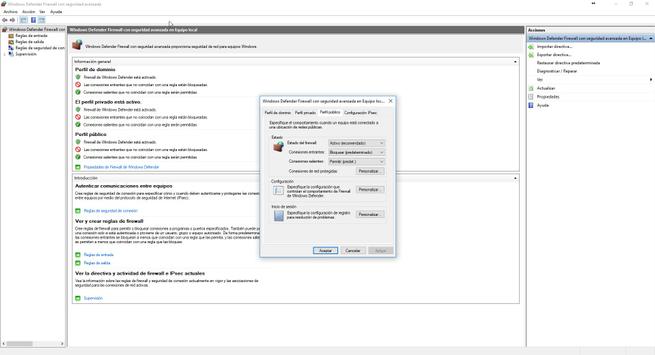
In the main menu of this advanced configuration we have the default policies of the three profiles that we have available: domain profile, private profile, public. Depending on the profile that we have assigned to our local network, we will have some permissions or others.
By default, all profiles are configured with a restrictive policy in the inbound rules . This means that all incoming connections that do not match a rule that you have predefined, or that we have defined, will be blocked. Regarding the outgoing rules, use a permissive policy , this means that all outgoing connections that do not match a rule will be allowed, and only those that we have specifically defined to block them will be blocked.
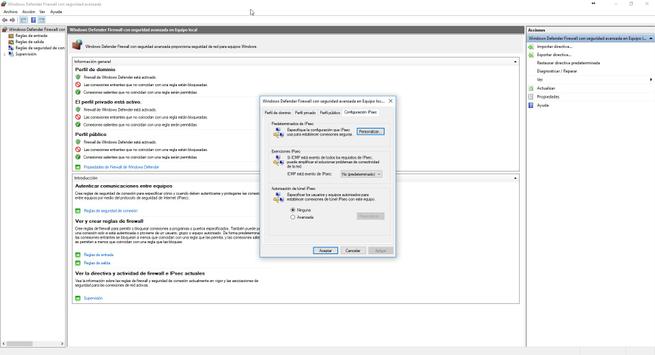
If we click on the ” Windows Defender Firewall Properties ” button, we can change the global settings of all profiles. We will have the possibility to enable or disable the firewall depending on the assigned profile, change the policy (permissive or restrictive) of both incoming and outgoing connections, and also other actions such as detecting protected network connections where we select the installed network interfaces, configuration of the firewall notifications, and the destination of the logs registered by the firewall itself. Finally, we can configure the policy to follow if we establish an IPsec VPN tunnel with the computer itself, since this type of connection, being authenticated, is reliable and we can configure the firewall to be more permissive if we want.
In the ” Supervision / Firewall ” section we can see each and every one of the rules that we have registered in the Windows firewall. All active rules will appear here, and we can see their configuration in detail. If we want to modify one of these rules, we will simply have to click with the right button of the mouse on the specific rule, and click on «Properties» to modify it as we want.
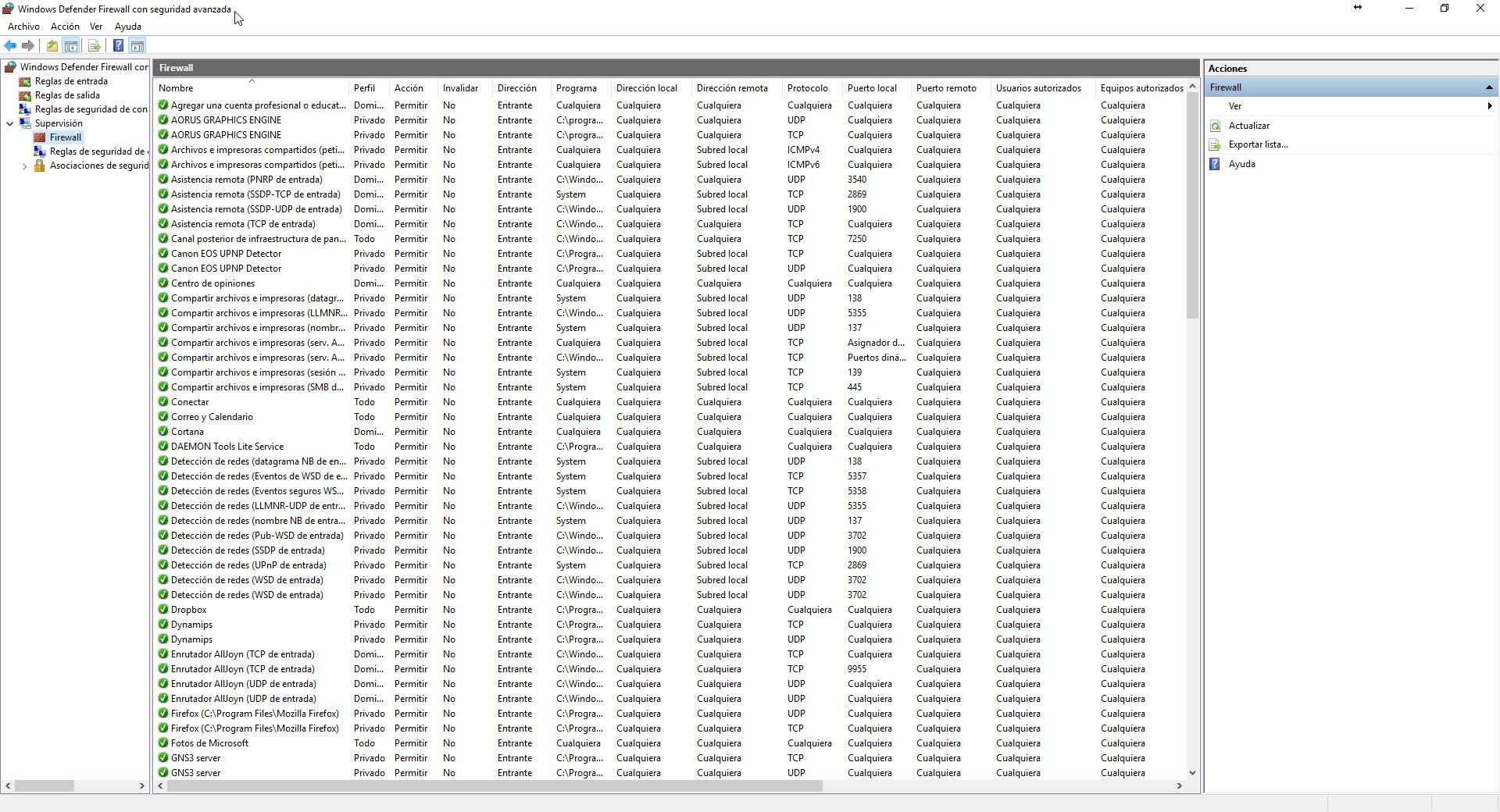
Inbound rules and outbound rules
In the “Inbound Rules” and “Outbound Rules” section, we will have each and every one of the rules that are currently registered, however, some rules may be disabled, therefore, they are not in use. Only the rules that have a green “check” are those that are enabled, those that do not have that “check” are disabled.
It is very important to know how to define the rule correctly depending on the direction of traffic. If, for example, we want to prevent connections from outside to us, we must register rules in “Inbound rules”. On the contrary, if we want to block any communication from us to the outside, we must register a rule in “Outbound Rules”. It is very important to know well the direction of traffic, because we could register a rule that is never followed.
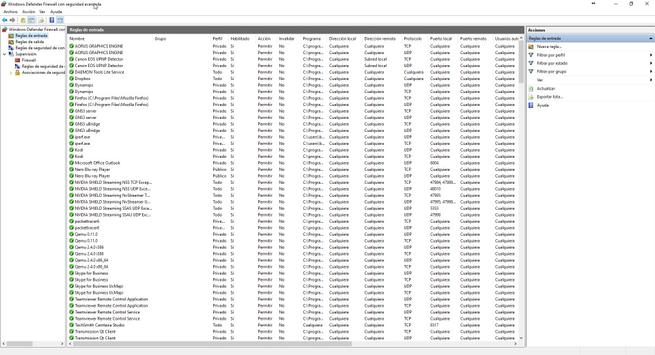
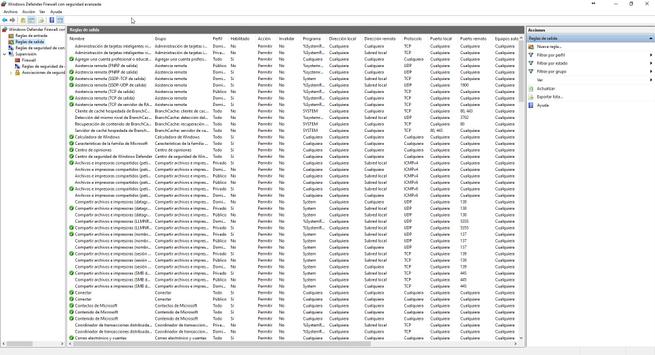
How to create a custom rule, both in “Inbound Rules” and in “Outbound Rules”
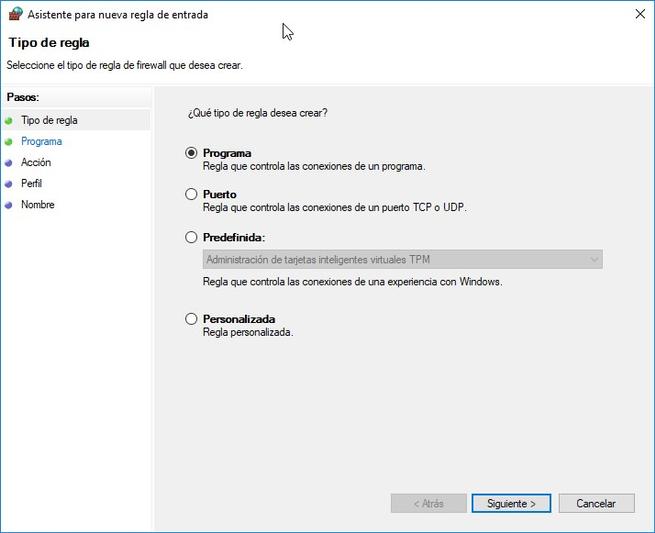
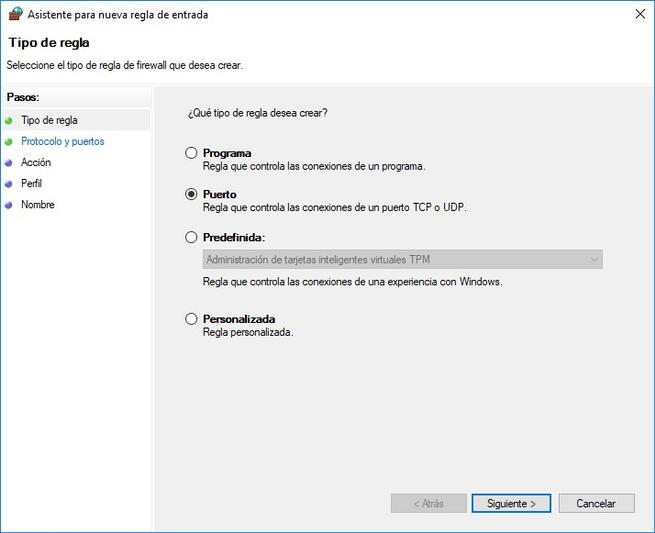
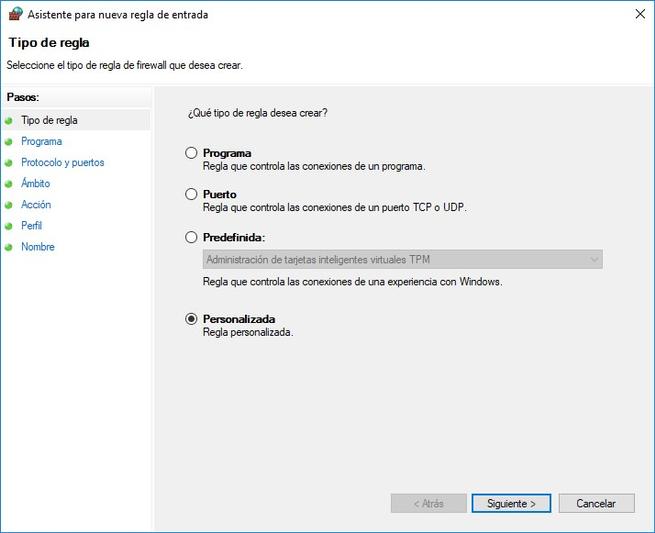
Although we have a large number of rules that are registered but are not being used, we will be able to easily create a custom rule based on various parameters. The Windows 10 firewall will allow us to create up to four different types of rules:
- Program: Rule that controls the connections of a specific program
- Port: rule that controls connections from a TCP or UDP port
- Predefined: we can select predefined Windows rules for your services.
- Custom: rule that we can configure in detail with all the parameters.
To create a new rule, right click on “Inbound Rules” or “Outbound Rules” in ” New Rule “.
Program Rules
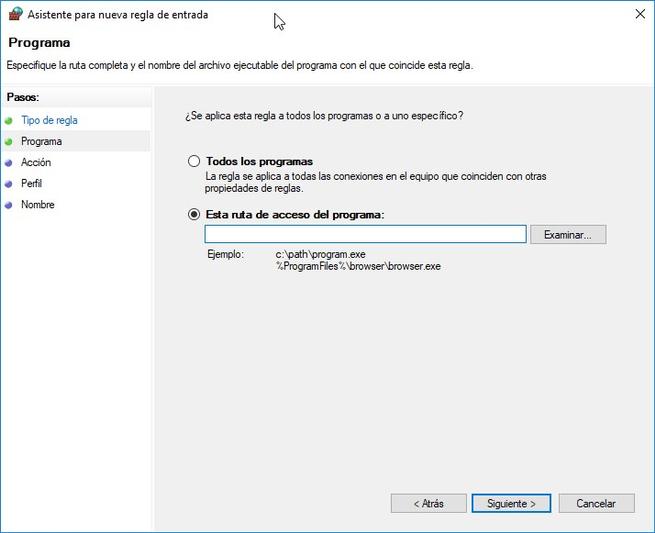
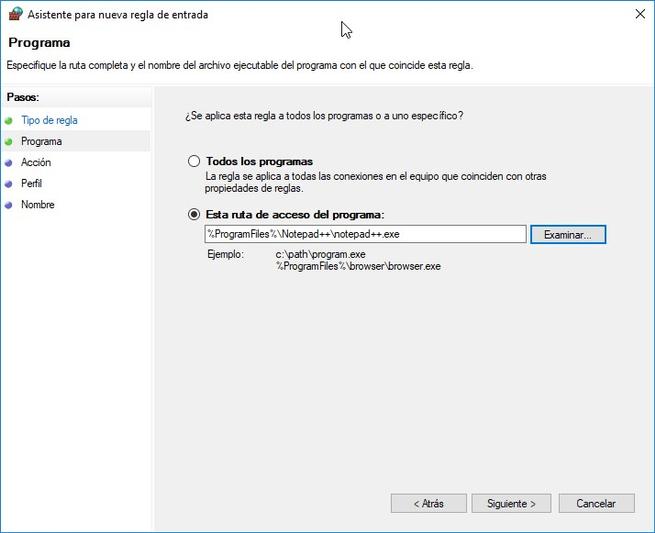
If we create a new “program rule”, we can allow or deny the connections of a certain program, both in the input rules and in the output rules. This option is ideal to avoid the need to know the TCP or UDP ports used by a certain program.
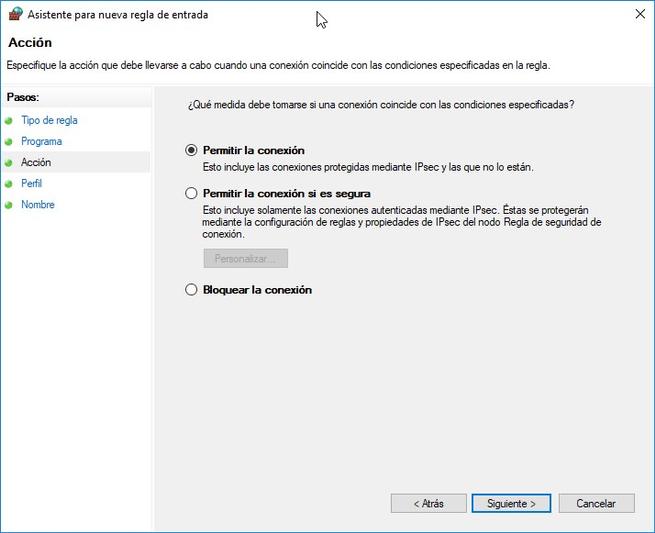
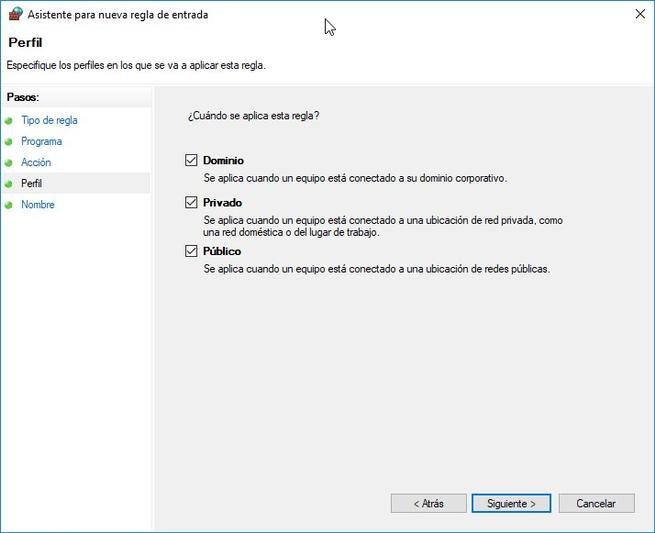
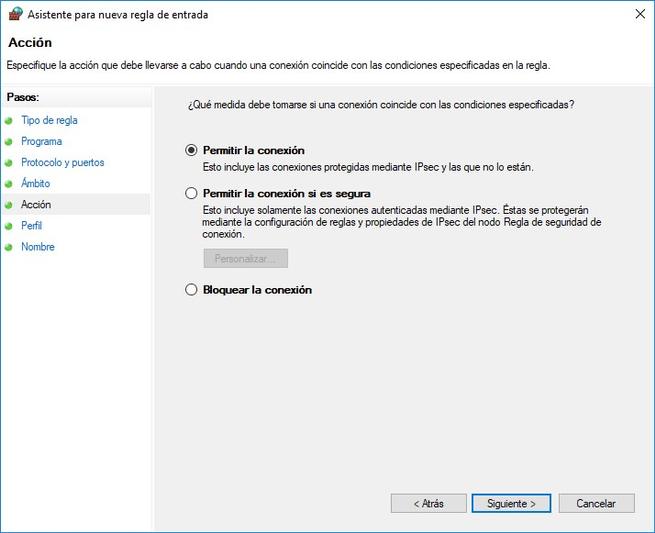
We simply have to indicate if we want this rule to affect all installed programs, or only one in particular. Once chosen, we must decide if we want to allow the connection, allow the connection if it is secure (if we use IPsec), or block the connection. Once we have defined whether we want to allow or deny the connection, we must decide in which profile (domain, private or public) we want this rule to apply. For example, we may be interested in blocking connections only on public networks.
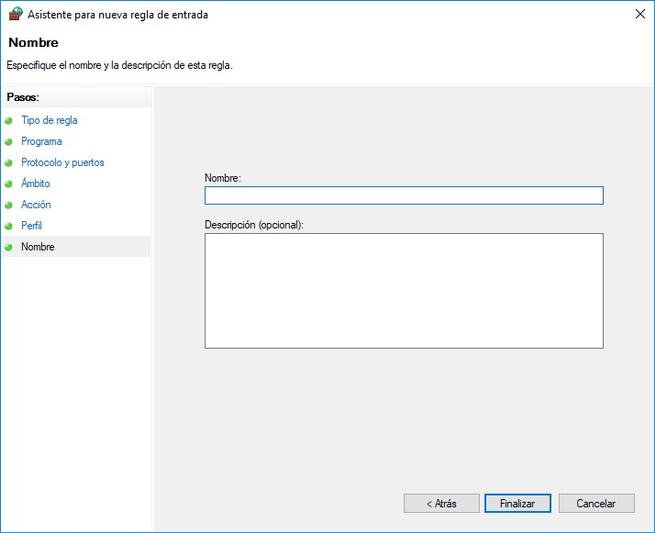
Finally, we must provide a name to the rule, and also an optional description to quickly know what that rule does.
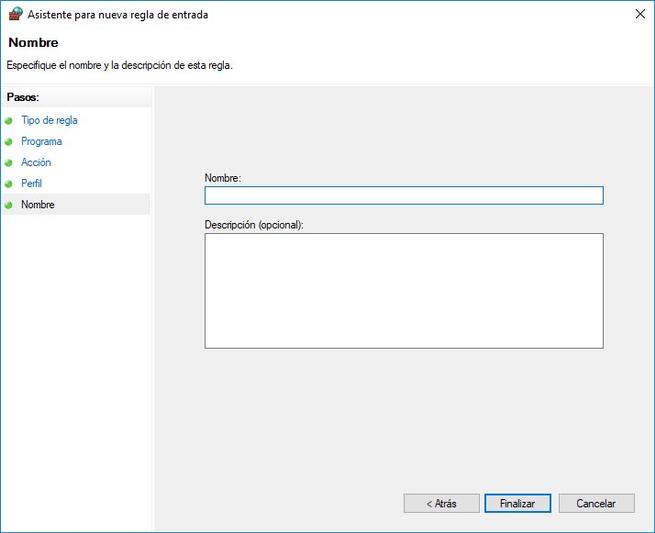
Port Rules
The Windows 10 firewall will also allow us to filter TCP or UDP ports, both in the inbound rules and in the outbound rules.
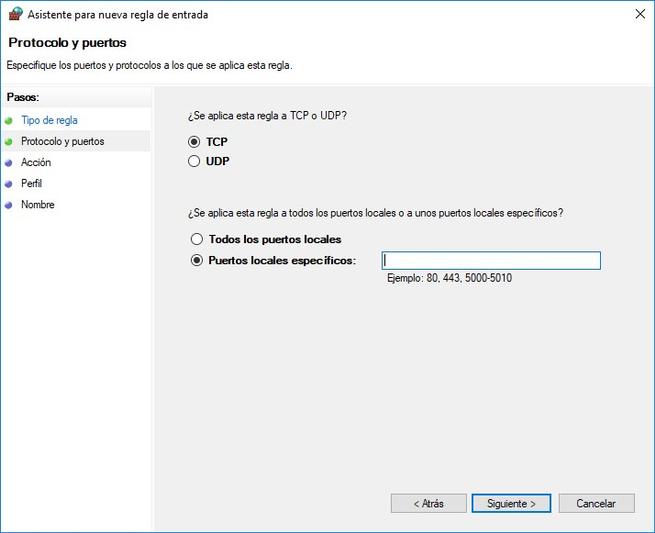
To configure the blocking of any incoming connection through port 21 (for example), we simply have to choose whether we want this port number to be TCP or UDP, and then we define the number 21 in ” Specific local ports “. to allow creating the same rule to block several ports with the syntax «21,20,22» for example, and also a range of ports with the syntax «5000-5100», in addition, we will also be able to define several ports and several ranges ports in the same rule.
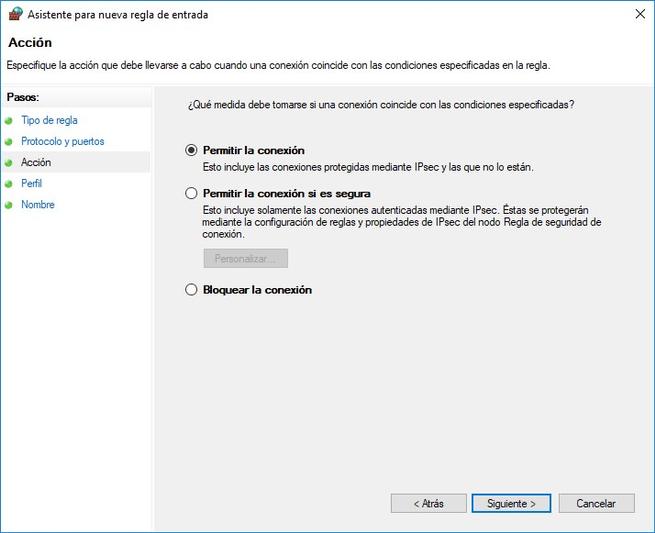
Then we can allow the connection, allow the connection if it is secure (we use IPsec), or block the connection. Next, we define in which profile we want this rule to apply, if in domain profile, public profile or private profile. Finally, we provide a name to this rule, and an optional description, to quickly find out what the specific rule that we have configured does.

Predefined rules
In the section “Predefined rules”, we will have several rules that correspond to the Windows operating system itself. If we need to enable or disable a certain service, we can do it directly from here. As you can see, the list of rules is quite extensive:
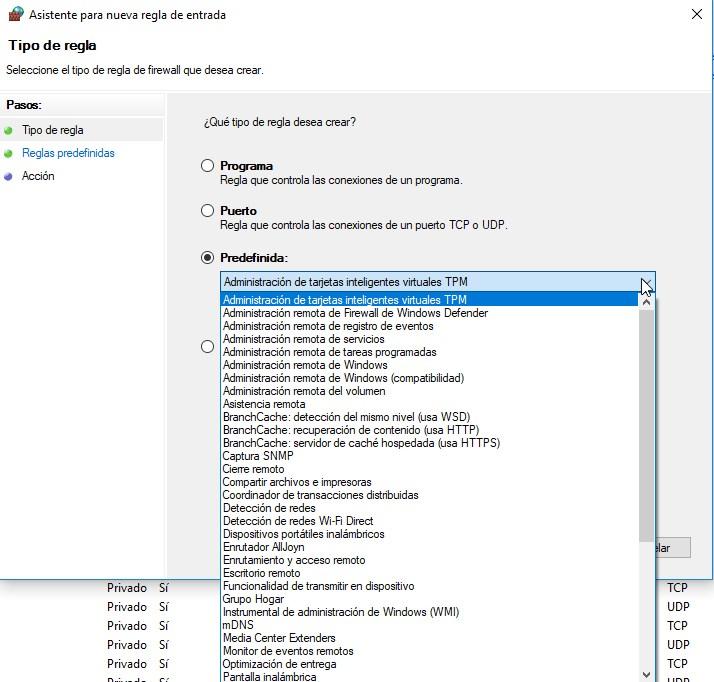
Once we have selected the rule, the following steps are the same as in the previous sections, we must define if we want to allow, safely allow, or deny. Then we define where we want to apply it (domain, private or public), and, finally, provide a name and optional description.
Custom rules
Custom rules are the ones that will provide us with the greatest configurability. In this section, we will be able to allow or block in detail any program, Windows service, IP protocol, IPv6, ICMPv4, ICMPv6 and a long list of available configuration options.
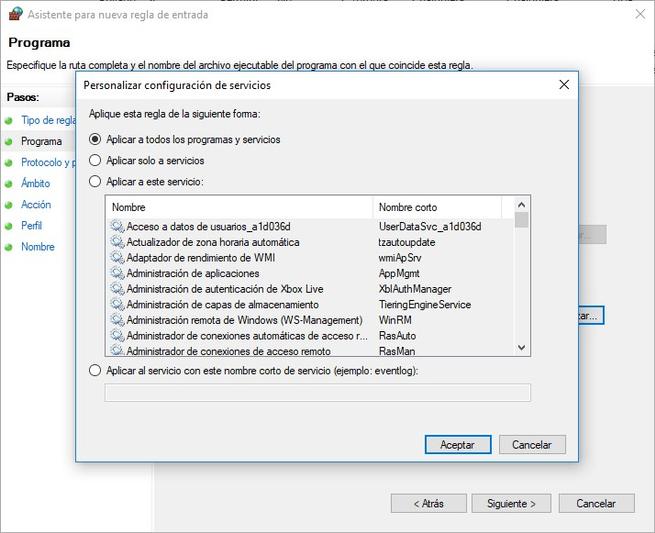
In the first menu we must select “Custom”, then we can choose if we want this rule to apply to all programs, or only to some of them. Furthermore, if we click on “Customize” we will also be able to decide if we want to apply it to all programs and services, apply only to services, or apply to a specific service. Once we have configured this rule, we go to the next menu to continue with the creation of the rule.
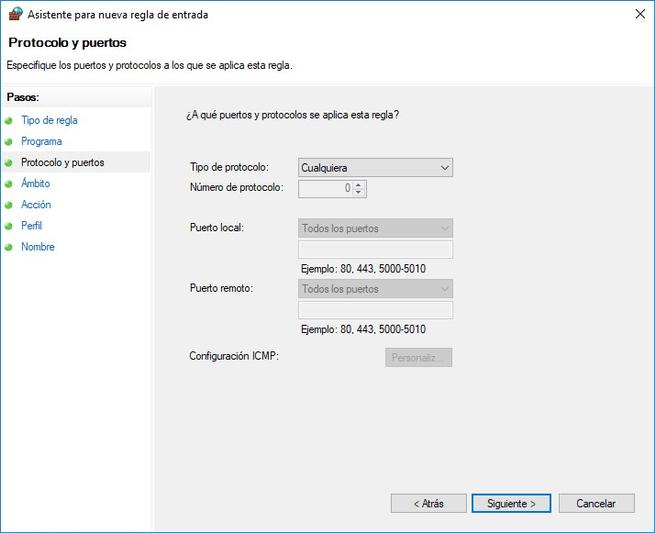
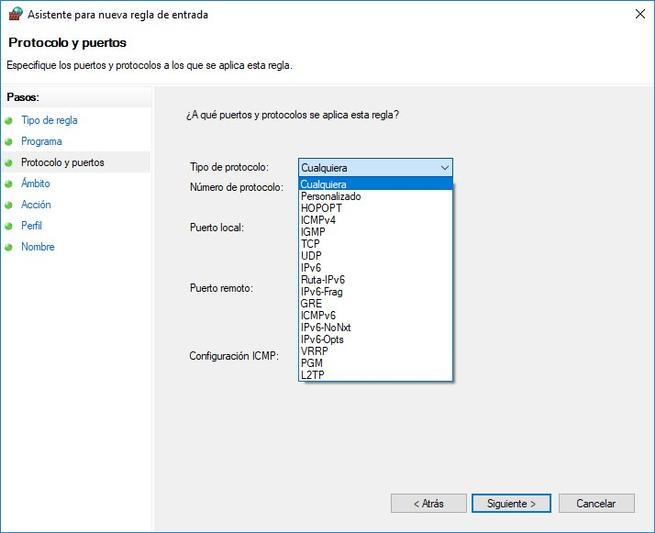
In this menu we are going to configure the type of protocol that we want to filter, we will have a long list of protocols that we can allow or deny, specifically the list of protocols are the following:
- Any: any protocol, filter at the network level.
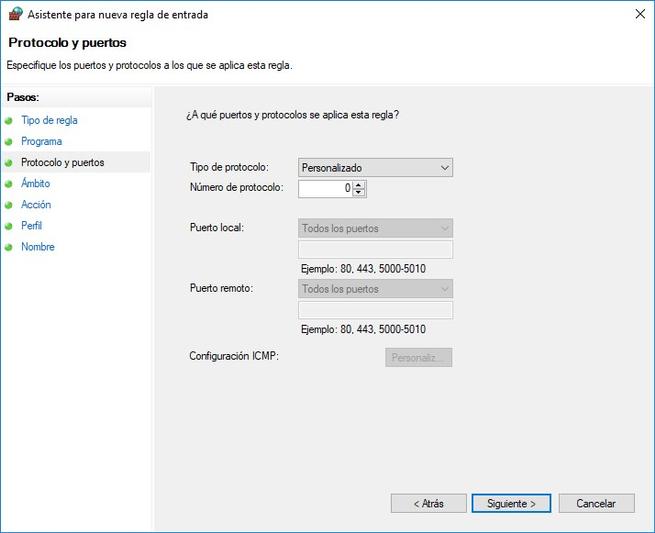
- Custom: we can define the protocol number that we want to block, in case it does not appear in the list.
- HOPOPT
- ICMPv4
- IGMP
- TCP
- UDP
- IPv6
- Route-IPv6
- IPv6-Flag
- GRE
- ICMPv6
- IPv6-NoNxt
- IPv6-Opts
- VRRP
- PGM
- L2TP
Depending on what we have chosen, it will allow us to choose a local port, and a remote port.
Furthermore, if we select, for example, the ICMPv4 protocol, we will be able to choose whether we want to allow or deny all types of ICMP, or only specific ones, as you can see here:
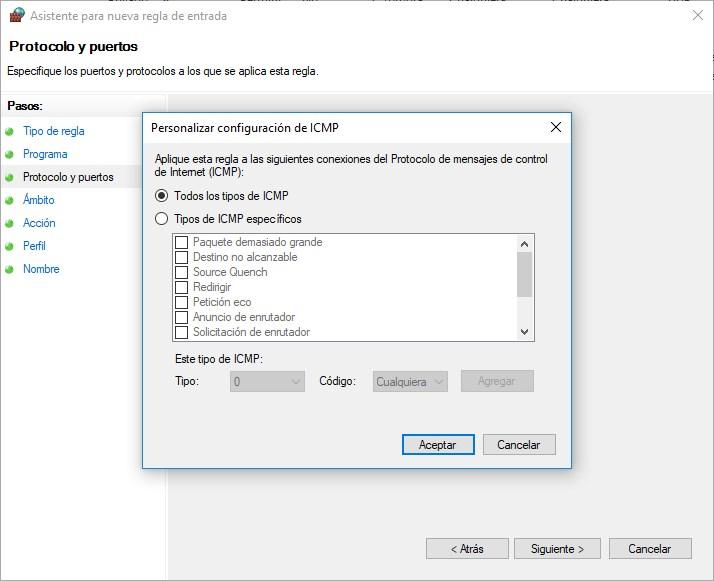
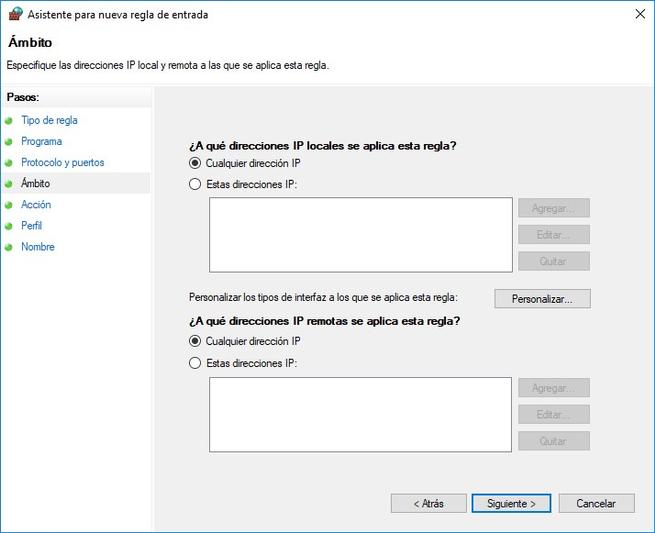
Once we have chosen which protocol we want to use, we will be able to define the local and remote IP addresses where this rule should be applied, in this way, we will have full control of any type of connection that they make to the system, or that we make from the system.
Next, we can allow the configured connection, allow the connection if it is secure, and block the connection, as in the rest of the rules that we have already taught you, and we can also configure this rule to act in the domain, public and domain profiles. private. Finally, we can give the rule a name and an optional description.
So far we have come with this manual of all the configuration options that the Windows 10 firewall allows us to perform. We recommend reading the following articles, where you can see in detail how to use the firewall to block open ports, and even external tools to facilitate the configuration of this firewall.