Firewalls are a fundamental tool to adequately protect both our PCs, the router and the entire network from external intrusions. Firewalls will allow us to control traffic to and from a destination, incorporating different rules. If the packet received or sent complies with a configured rule, one of the three typical actions of firewalls will be executed: allow the packet (ACCEPT), deny the packet and delete it (DROP), launch a rejection message (reject). Knowing how to configure a firewall, either through the command line or in a graphical user interface is as important as knowing good practices to do so. Today in this article we are going to make a series of recommendations for you to correctly configure your firewall.

Deny traffic implicitly (default)
Firewalls allow two types of policies when it comes to allowing or denying traffic, configuring a restrictive policy with the network traffic that comes and goes is something totally fundamental to adequately protect the computers and also the network. Firewalls can be configured in two different ways:
- Permissive policy : any traffic from any IP and interface is allowed, only what is explicitly blocked in the firewall will be blocked.
- Restrictive policy : no traffic from any IP address or interface is allowed, only traffic that is explicitly allowed in the firewall will be allowed.
For security, we should always configure the firewall policy as “restrictive” , in fact, many default firewall softwares are already configured with this policy, even professional routers and firewalls, that is, we have an implicit rule at the end that indicates a “deny all”, as is the case with Cisco routers or firewall-oriented operating systems like pfSense. Therefore, if we do not have a “allow something” rule, automatically all traffic is denied by default, in order to have the best possible security.
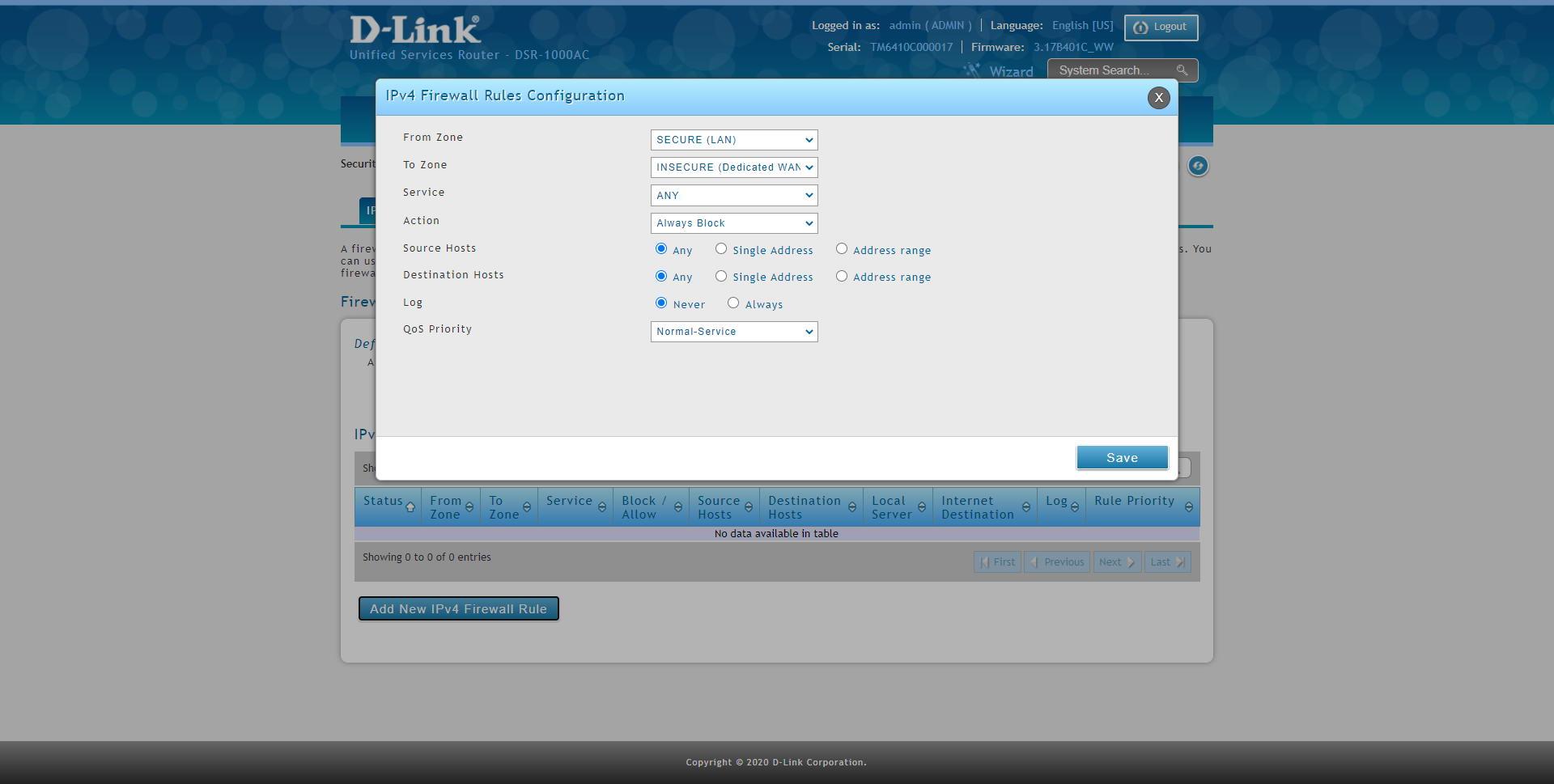
System and network administrators should always configure the firewall to allow only the minimum traffic essential for the proper functioning of the system, and block any other traffic that is not necessary. In this way, the vast majority of rules that we have in the firewall will be “allow” and not “deny”, because we will have an implicit deny at the end of the list.
Optimize the created rules and order them
Another very important aspect is that all firewalls evaluate the different rules sequentially, from top to bottom, therefore, we must follow some recommendations so that the rules work correctly:
- The more specific rules should go on top , above the more general rules. For example, let’s imagine that we want to allow a certain IP, but block the rest of the computers on the same network. First we must put “allow the IP” and then “block the subnet”. If we put the most general rule first (block the subnet), the strictest rule (allow the IP) will never be fulfilled.
- The most general rules should go below the more specific ones .
Another recommendation when configuring a firewall is the order of the rules , the rules that are to be “checked” the most should go as high as possible, and the least “checked” rules at the bottom, to optimize performance. of the firewall , because the operating system has to check everything from top to bottom.
- The rules that are going to be fulfilled the most times, place them as high as possible.
- The rules that will be followed the least, below.
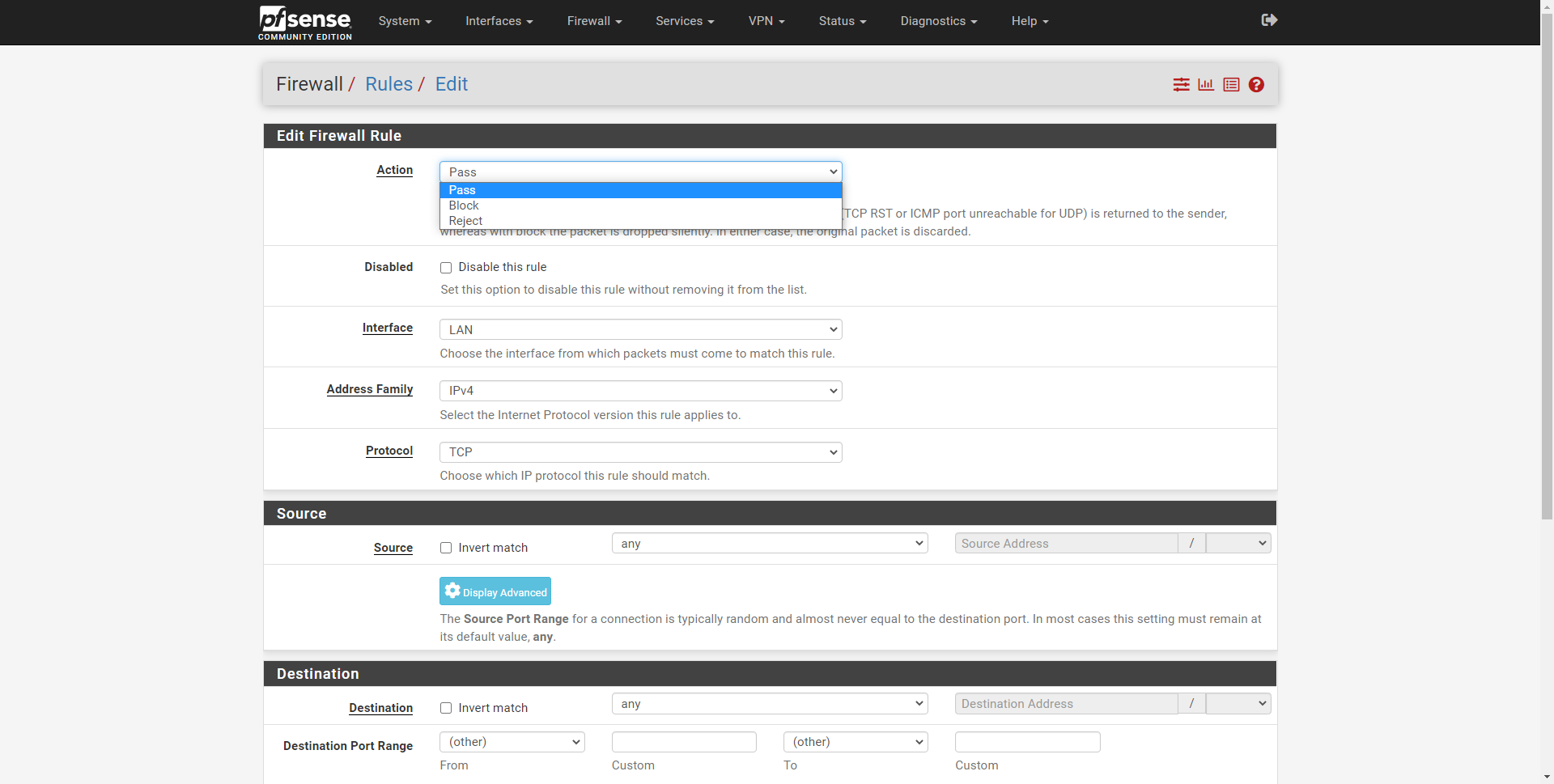
Depending on the operating system and the firewall, we may have different firewall policies on different interfaces. For example, in the professional pfSense operating system, the Internet WAN interface has an implicit deny, however, everything coming out of the LAN is allowed by default. We can also do the same on Linux-based systems such as Debian through iptables or nftables, configuring the default policy in the different tables and chains.
The list of rules as short as possible
When we configure a firewall, it is highly recommended that the list of rules that we are going to incorporate be as short as possible, in order to be able to manage and maintain them correctly. If we have a total of 10 rules that we could “summarize” with only one rule, making use of “Aliases” or sets of IPs and ports, much better. It is always advisable to have the minimum number of rules for several reasons:
- Faults can be detected more quickly.
- Rules management will be easier by having few rules.
- Firewall performance, the system will not have to check 100 rules but only 5, therefore, the performance will increase and the CPU consumption will decrease.
Check that the rules are still in force on the network
It is highly recommended to check the firewall rules with some frequency, to verify that the requirements to allow or deny the traffic that we want are still met. If we are in a static environment where there have been no changes, then it will not be necessary to maintain these rules on a regular basis, however, in networks that do change, we will have to take care of it.
If in a certain network we are going to eliminate a server or PC, and it is in the filtered firewall, we must check if we want to continue allowing or denying that traffic, that is, keeping the firewall updated depending on the network.

Document all the rules in the “description” field
In all the rules that we are going to create in the firewall, it is absolutely necessary to write in the description field what that particular rule is doing. When we go to configure a firewall, we know perfectly what we want to allow or deny, but after 2 or 3 months, and even if someone else manages it, we usually have forgotten or do not know very well what it is. you are allowing or denying, and you have to “pull” the thread to “guess” what that particular rule does.
When we review the firewall configuration in the future, we will appreciate having incorporated these descriptions into the firewall or in the configuration documentation, why they are necessary and why we have created them that way. Of course, it is absolutely necessary to keep this firewall configuration document up-to-date, and perform periodic configuration reviews. Whenever we are going to update the documentation, we must make the corresponding changes.
Log the traffic only we need
All firewalls, depending on a certain rule, will allow us to record the network traffic allowed or denied in the firewall (source and destination IP address, source and destination port, and time), in this way, we can see access attempts, allowed or denied traffic and more. At first we may think that recording all network traffic is a good idea, but it is not. It is advisable only to record the traffic that really interests us for debugging tasks or to check if they are attacking us.
If we record a large amount of traffic, we will have a lot of “noise” in these records, that is, records that will not serve us, and we will have to start filtering huge amounts of logs to get to the one that really interests us. For example, computers with Windows or Mac continuously send and receive information from the Internet, resolve several domains hundreds of times and much more, therefore, make sure if you really want to log this web browsing traffic. In addition, if you use dynamic routing protocols such as RIP or OSPF in your network, and you have the firewall in between, you will continuously receive traffic from these protocols, the same if you have HSRP or VRRP for redundancy of the routers.
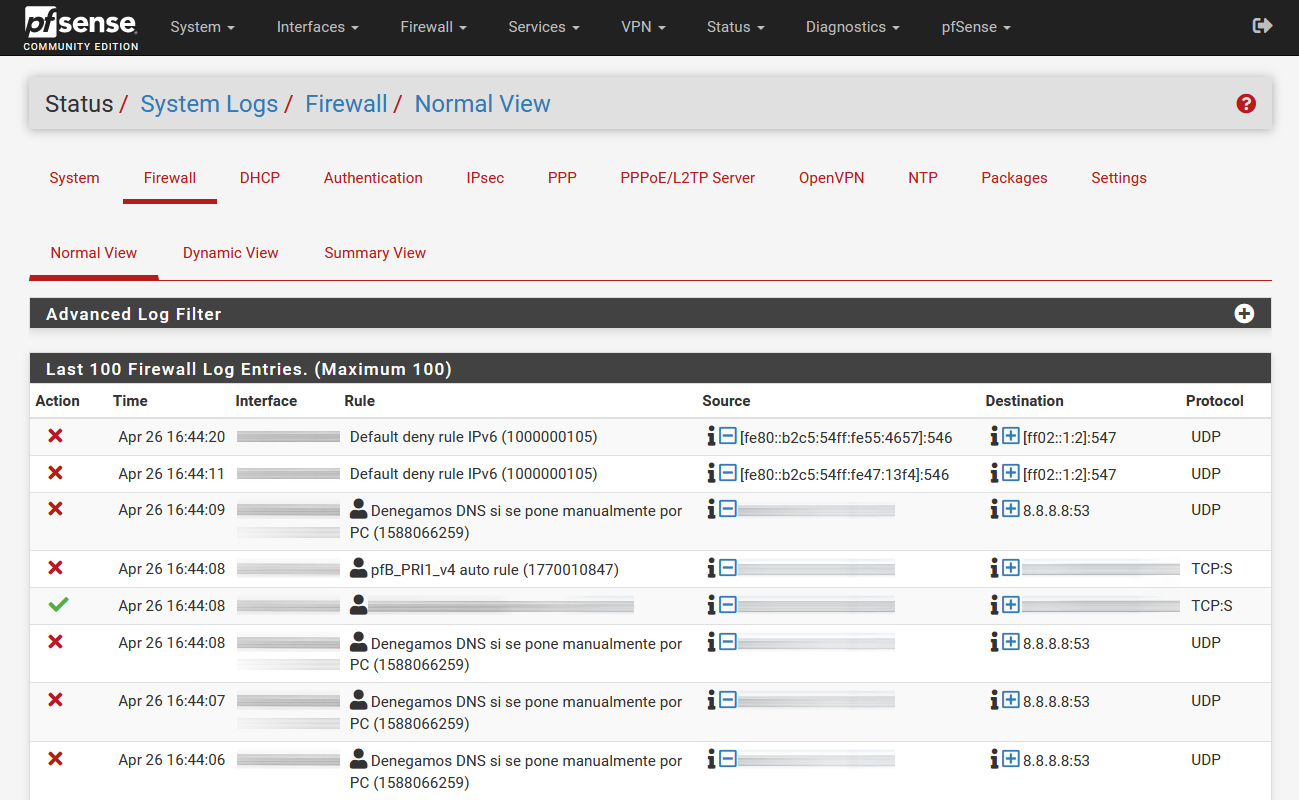
Look closely at the logs of certain traffic
If you log the WAN traffic, you must bear in mind that we will have a complete record of all Internet connections, the most normal thing is to record the packets that are directed to our VPN or SSH server, to detect possible suspicious activities, and not the Web navegation. It is also advisable to frequently look at what appears in the registry, how often does this specific registry appear? Should it leave every 30min or every 60 min?
Finally, another aspect to take into account is that we must not only log the traffic we stop to see who is attacking us, but also the allowed traffic. Should this allowed traffic really pass through or should we block it?
We hope that with these general recommendations you can configure your firewall correctly, whether it is a router, a firewall such as pfSense and even in an operating system such as Windows or Linux, because all firewalls work exactly the same.