We are sure that all of you have ever had to “open a port”, or rather, do “port forwarding” on the router, since all the computers on the local network are behind the NAT. To be able to access these devices that are on the local network from the Internet, we have to “open a port” or do “Port forwarding” on the router, otherwise, we will not be able to access this service from the Internet (SSH server, FTP server , OpenVPN server etc.) Today in this article we are going to explain what it means for a port to be open, how they could attack open ports and what they could do.

What does it mean for a port to be “open”?
Communications at the transport layer level, using mainly TCP and UDP protocols, make use of what is known as “Internet socket”. This socket constitutes a mechanism by which two processes (applications, for example) can exchange data through the local network or through the Internet. Any data flow that uses TCP or UDP requires at least the following information:
- Source IP
- Port of origin
- Destination IP
- port of destination
In a local network, in a completely automatic and transparent way, ports are continuously being opened and closed by the different processes to be able to communicate with other computers. For two processes to communicate, it is necessary for one process to be able to “locate” the other to obtain services or provide services to you.
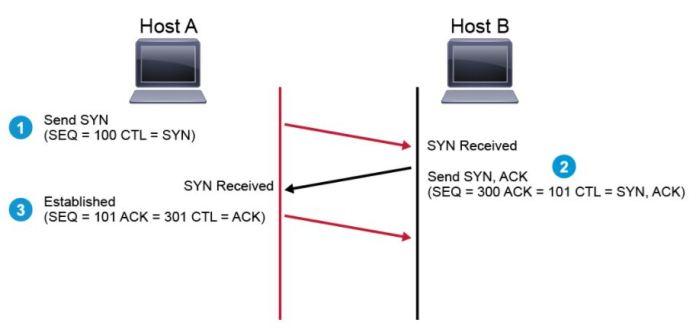
When we define that a “port is open”, it can be in two very different scenarios:
- An open port on a local computer , for example, on our computer or on a local server. In principle, all ports should be closed because the firewall is normally configured restrictively (everything blocked except what is specifically allowed).
- An open port in the NAT of the router . Normally in the router we do not have any “open” port, or rather, we do not have in the “Virtual Server” or “Port Forwarding” section any port to any computer. By default in any router this table is empty, however, we can register different rules to open ports to different computers.
When do we need to open ports locally?
If our local computer acts as a “something” server, such as, for example, an FTP server, a web server, an SSH server, a VPN server, a database server, and much more, we will have to have a port or several ports open on it. firewall so that the different computers on the local network or Internet can access our services, otherwise, they will not be able to access because the firewall will block this communication and connections will not be established.
Normally in a home environment, if we set Windows 10 or a Linux-based operating system as “Private network” or “Home network”, the firewall is disabled and all incoming connections will be allowed. However, if we have it as “Public network” the firewall will be activated and will block all incoming connections that we have not previously made outgoing, therefore, we are facing a “restrictive” firewall.
When do we need to open ports in the router’s NAT?
If we have a computer on the local network that acts as a server «for something», as in the previous case, and we want these services to be accessible from the Internet, it will be necessary to do a «port forwarding» or also known as «open ports ». In this way, if someone opens a socket with the public IP address and a corresponding external port, that data flow will automatically be forwarded to the computer for which we have “opened the ports”.
Any router by default does not have any rules to perform port forwarding, we will have to do it specifically. In addition, a very important detail is that if your operator has CG-NAT, even if you open a port on the router externally, you will not be able to do anything to access the internal resources of the local network.
How do you attack a port?
You cannot really “attack” a port, what is attacked is the service behind that “port” that is listening to accept incoming connections. For example, if we have port 5555 open and an FTP server is configured here, what we will do is attack the FTP service, but not the port. The port is still a “door” to the information, what is truly attacked are the services behind these ports.
The term attacking a port is commonly used, when it really should be said “do a port scan” to check which ports are open on a certain computer, to later attack the services behind this specific service. To do a port scan there are many methods, but, without a doubt, the best that we can use is to perform a scan with Nmap, the quintessential host discovery and port scanning program, in addition, it would also allow its exploitation through of NSE that is an add-on to Nmap with the possibility of cracking different services and exploiting known vulnerabilities.
Nmap is a very easy-to-use program, just install it on any Linux-based operating system to start its operation, it is in the official repositories of each distribution, therefore, just execute the following command:
sudo apt install nmap
Once installed, we will have to execute the specific command to see if a port is open, filtered or closed:
nmap -p PUERTO IP
We could also scan a range of ports as follows:
nmap -p PUERTOINICIAL-PUERTOFINAL IP
For example, if we have a web server with HTTP and HTTPS running, it is completely normal that we have ports 80 and 443 open, like this:
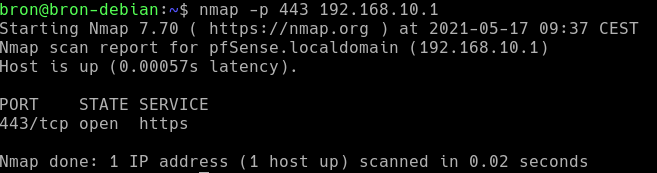
Checking open, filtered or closed ports with Nmap is easy, however, we would recommend you read the complete Nmap wiki where we have detailed step-by-step manuals of the different types of port scanning that we have available.
What can a cybercriminal do with a port that is open?
When we have an open port, there can be several cases around what a cybercriminal can or cannot do. If we have an open port, but there is no service behind it listening, it will not be able to do anything at all, however, the open port number could be “saved” in case we do put a service to listen in the future.
If we have an open port and there is a service behind listening, it could perform many actions:
- Make use of a legitimate way to check its operation
- If the service requires authentication, it could perform a dictionary or brute force attack to access the service.
- Perform a denial of service attack to cause the service to stop working properly and to stop providing service.
- Exploiting a security vulnerability in the service, either to illegitimately access the resources of the service, to enter the system, and even to escalate privileges and take full control of the server.

As you can see, with an open port and a service running behind it, a cybercriminal can perform many malicious actions, therefore, it is very important to protect the services behind this port, to protect them, it is advisable to perform the following actions:
- Correctly configure the firewall to allow access only to those who really need it, for example, you can filter by countries.
- To mitigate DoS attacks, you can configure firewall rules to deny too many simultaneous connections to the same source IP.
- You can install a program like fail2ban to detect multiple login attempts, then tell the firewall to block the source IP.
- Hardening the service that is listening, be it an SSH server, FTP or web server, there are always advanced settings in these services to protect them even more.
- Hardening the operating system that is hosting the service, defining robust authentication policies, updating the system, and even using advanced systems such as SELinux among others.
There are many security measures that we can apply to a system and service to be more secure, but you must bear in mind that 100% security does not exist, therefore, you must be prepared for an incident and be able to recover the system.