
Cloud computing has grown in popularity among enterprises due to its scalability, cost savings, and comprehensive flexibility. These days, businesses are keeping their data in the cloud and serving it straight from there. That means this data might also include personally identifiable information (PII) in some cases. However, there are risks associated with cloud data storage, such as unauthorized access, data breaches, and data loss. As a result, it is vital to put strong security measures in place to secure sensitive data kept within the cloud.
Encryption is the most effective strategy for improving the security of data kept on the cloud. Encryption is the process of converting plaintext data into a format known as ciphertext that can only be deciphered via a specific key.
The term “bring your own key”, known as “BYOK”, refers to one of the most widely used cloud data security best practices in which clients upload their own encryption keys to the cloud. This strategy is utilized to improve data security and an organization’s level of control over data stored in the cloud.
When using BYOK, the client generates and keeps control over the encryption keys used to encrypt their data. Therefore, the customer maintains sole control over who has access to their data and the ability to decrypt it. As a result, this strategy provides an additional layer of defense against data breaches and illegal access to sensitive information. In addition, it can assist businesses in meeting the regulatory compliance requirements for data security.
How BYOK Encryption Enhances Cloud Data Security
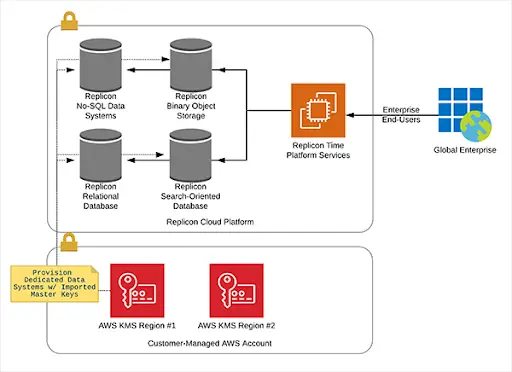
Many cloud service providers offer encryption, but they typically manage the keys themselves. To enhance cloud data security, a best practice is to use Bring Your Own Key (BYOK) encryption, also known as Customer-Managed Keys (CMKs). BYOK encryption gives organizations greater control over their data and encryption keys. With this approach, organizations can create, manage, and delete their encryption keys as needed, which ensures full control over their keys and encrypted data. As a result, BYOK encryption is an effective way to bolster the security of data in the cloud.
BYOK encryption also helps organizations meet data security rules set by the government. For example, many governing bodies require organizations to use certain encryption standards to protect sensitive data. BYOK encryption lets organizations use their own encryption keys instead of relying on the cloud provider’s keys, which helps them meet these requirements. It also protects data while it is at rest and while it is moving. This makes it harder for hackers to intercept or steal data and protects the integrity of the data by stopping it from being changed or messed with.
Benefits of BYOK Encryption for Businesses
There are a lot of benefits that are associated with the usage of BYOK. Organizations that store PII and other sensitive data over the cloud can get proper control of their data using BYOK. Additionally, there are benefits such as proper security, compliance, etc. Let’s discuss these in more detail.
Proper Data Security
The use of BYOK encryption offers organizations the ability to have complete and proper control over the data that is being stored in the cloud. By using conventional encryption methods, the cloud provider is the one in charge of managing the encryption keys, which directly indicates that the cloud provider has access to the keys and potentially has access to the data as well. As a result, even if the cloud provider’s security is breached, the organization’s data are still at risk of being stolen.
On the other hand, if a company uses BYOK encryption, it indicates that it has full control over how its data is encrypted. Furthermore, they have complete control over the data because they are the ones managing the keys. This provides a high level of protection to the firm while also lowering the likelihood that sensitive data is accessed by someone unauthorized to access it.
Flexibility to choose Encryption Algorithms
The organization benefits greatly from the flexibility provided by BYOK. As the organization is the one making use of the encryption keys, this indicates that they have the ability to select the encryption method that best suits their needs. Organizations have the option of selecting the key length, which provides both improved security and greater flexibility.
Some businesses use a unique combination of data, such as PII and other types of sensitive government data. BYOK encryption solution enables clients to customize their protection to correspond with the requirements of their organization. Because of this versatility, businesses are free to select the encryption method that works best for meeting their own requirements for data safety. Defining the kind of robust algorithm that a company uses is another way in which this assists businesses in gaining the trust of their customers.
Conclusion
When it comes to protecting data in a cloud environment, organizations can take advantage of the many benefits of BYOK encryption. Business organizations employing BYOK encryption have more control over the security of their data since they can manage their own encryption keys. The risk of data breaches decreases and regulatory compliance becomes easier thanks to the higher degree of control.
Furthermore, BYOK encryption offers companies more adaptability, better data governance, greater performance, easier integration, security against insider threats, and higher trust. Overall, BYOK encryption is a flexible, affordable solution that may assist organizations improve the security and privacy of their data and the confidence and loyalty of their customers.