In a forum of cybercriminals they have presented a new tool that allows phishing or malware attacks, by allowing sent messages to enter directly into the victim’s inbox, bypassing all the anti-spam and security measures of the main providers email. This tool is known by the name of Email Appender , and it is capable of creating phishing emails and even custom malware, so that it reaches our email inbox directly. Do you want to know how this new tool works?
This software represents a worrying threat, as it increases the success rate of malware attacks. Thus, it enables more sophisticated phishing and business email compromise (BEC) campaigns. Furthermore, it opens the door to technically simple attacks similar to ransomware.
How Email Appender Was Discovered, Risks, and Background
Security analysts at Gemini Advisory discovered that a cybercriminal was introducing Email Appender , a tool that implants emails directly into the destination mailbox. The attackers ‘goal is to place personalized, malware-infected phishing emails into victims’ mailboxes, without actually sending the email. This prevents email security platforms that inspect messages on your destination mail server, and therefore can block it. This tool provides an easy way for cybercriminals to implant emails in our inboxes.

The person responsible for this threat created another simpler tool called GetMailer Pro in 2019. This software is intended to emulate the leading email clients in order to create and deliver automated bulk emails. The difference with Email Appender is that it is not able to bypass the anti-spam and anti-fraud filters used by the recipients’ email platforms. GetMailer Pro uses a user interface similar to that of the new software. A subscription format is also offered, although due to its lower efficiency it sells for half the price.
How Email Appender works
An attacker who wants to use this software must start by acquiring a list of valid credentials in the form of e-mail addresses and their associated passwords. Here we have the initial screen of the program:
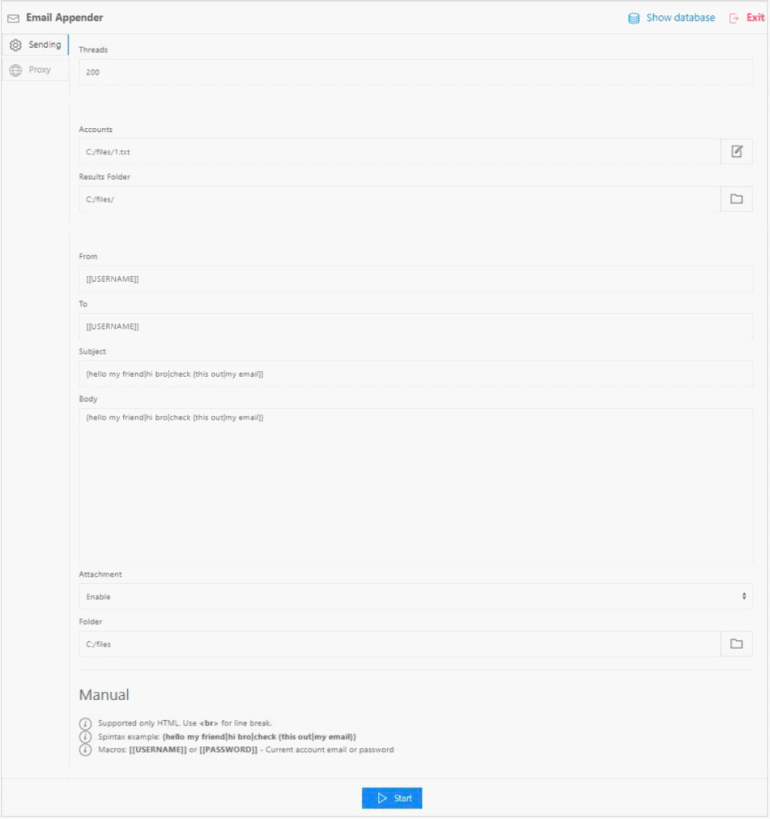
Then the attacker uploads the email login credentials to Email Appender. The software then verifies that the credentials are valid and connects to the email accounts through the IMAP protocol. This is the standard protocol that email clients use to receive messages from a mail server.
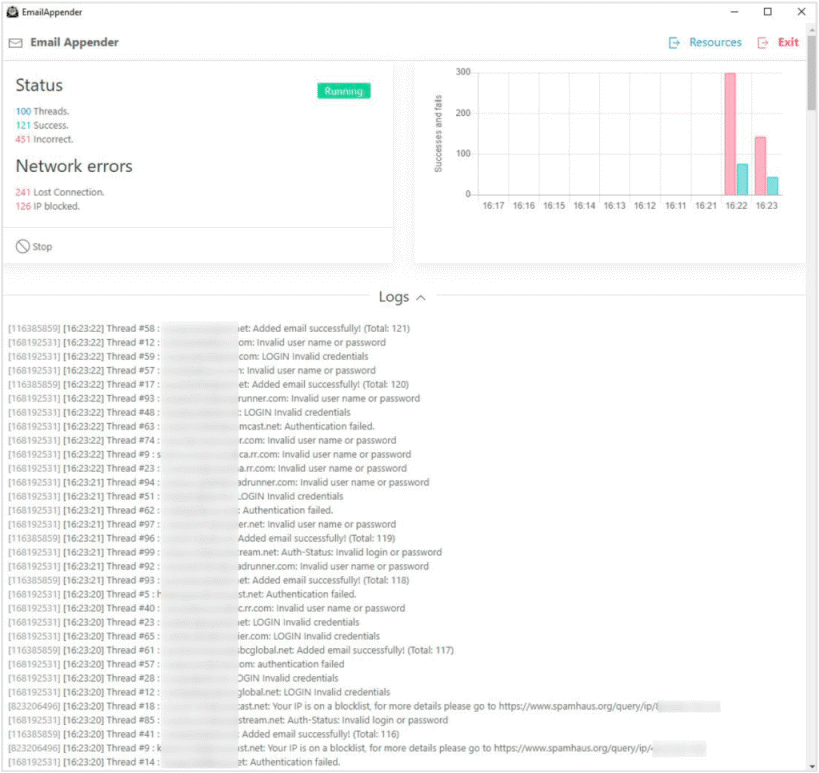
They can then customize the email messages for their criminal purposes, and then push the messages in bulk to the compromised accounts. One technique they can use to improve their credibility may be in the sender field. Here you have the Email Appender tool at work:
Prevention, types of attacks that we can suffer and more
Regarding the risks presented by the links within an email, we can face different risks. One of them would be identity theft through a phishing attack. In the context of email, phishing is based on the victim thinking that the malicious email they have received is legitimate. Then, click on the link, enter your username and password and the account is already in the hands of cybercriminals.
Another would be the Business Email Compromise (BEC) which is another specific type of phishing that takes advantage of compromised business emails. For example, a criminal could pose as a senior manager by misleading the victim to obtain confidential information. It can also be used for data hijacking, in this case, if the victim does not agree to the attackers’ requests, they could publish their emails with confidential information.
The Gemini Advisory researchers released a demonstration video showing how even low-level attackers could use Email Appender to successfully carry out an attack.
As for the best way to prevent an account, it would be to use multi-factor authentication (MFA) , in this way, in addition to entering the username and password, we must also enter a code generated by an authenticating application or a 2FA key. In this article we have a tutorial in which we explain how to use MFA authentication with your Google account .