Web domains can suffer a wide variety of attacks. Hackers can use different methods with the aim of damaging a web page, modifying its content, causing a denial of service and many other failures that, ultimately, damage its proper functioning. In this article we are going to talk about a list of vulnerabilities known as DNSPooq , which can affect your server’s DNS.
DNSPooq vulnerabilities
On many occasions we find vulnerabilities that can compromise systems, devices and, also, online services. Many security flaws can affect a web page. DNS can be affected by different attacks and this damages web pages.

Dnsmasq is a widely used open source Domain Name System (DNS) forwarding application that is commonly installed on routers, operating systems, access points, and other network equipment. As with many other systems and services, it can have vulnerabilities.
Vulnerabilities known as DNSPooq affect this service. There are seven in total and an attacker can use them to launch a DNS cache poisoning attack. This means that users who use this application must keep their computers protected and properly updated.
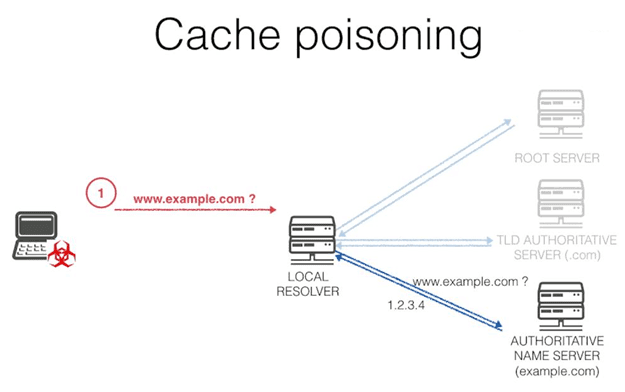
What is a DNS poisoning attack
As we have indicated, vulnerabilities known as DNSPooq can lead to a DNS cache poisoning attack. Now what is this? It is important to know what this security problem consists of and how it affects a web page.
A DNS cache poisoning attack occurs when an attacker tricks DNS resolvers with information that is false. This results in the resolver sending the wrong IP address to users. This means that the client, the person who tries to access a website, is redirected to any other page controlled by the attackers.
This is a very significant issue, as we could compromise security and privacy . An attacker could create a website pretending to be legitimate and redirect the victim there. This could lead, for example, to a Phishing attack with the aim of stealing passwords and credentials.
Ultimately, cache poisoning consists of sneaking false information into a DNS cache. Thus, when trying to enter a website, the resolution will redirect to another page. That site can be totally different or even appear to be the same, an identical copy, to steal information.

Why Fixing DNSPooq and Similar Vulnerabilities is Essential
All of this that we mentioned makes it essential to be able to fix DNSPooq vulnerabilities and other similar ones that may exist. We have seen that there are at least seven bugs that can affect routers, operating systems and devices.
These bugs were logged as CVE-2020-25681, CVE-2020-25682, CVE-2020-25683, CVE-2020-25684, CVE-2020-25685, CVE-2020-25686, and CVE-2020-25687. They had a score between 4 and 8.1.
- Starting with the first one, the CVE-2020-25681 vulnerability has a score of 8.1. It affects Dnsmasq versions prior to 2.83 and is susceptible to a buffer overflow when using DNSSEC. It could allow a remote attacker to arbitrarily write data to memory.
- The second vulnerability, CVE-2020-25682 , received a score of 8.1 as well and equally affects Dnsmasq versions prior to 2.83. In this case they are susceptible to buffer overflow in the extract_name () function due to lack of length check, when DNSSEC is enabled.
- Continuing with the next vulnerability, CVE-2020-25683 , they gave it a dangerousness score of 5.9. Causes a buffer overflow when DNSSEC is enabled.
- CVE-2020-25684 is the fourth vulnerability of its kind. It had a score of 4. This is a lack of proper address / port verification implemented in versions of Dnsmasq.
- Another vulnerability is CVE-2020-25685 . It consists of the lack of query resource name (RRNAME) checks implemented in versions of Dnsmasq prior to 2.83 reply_query feature allows remote attackers to spoof DNS traffic which can lead to DNS cache poisoning. He had a score of 4.
- The sixth vulnerability was registered as CVE-2020-25686 . Multiple DNS query requests for the same resource name (RRNAME) by versions of Dnsmasq prior to 2.83 allow remote attackers to spoof DNS traffic, using an attack that can lead to DNS cache poisoning. It also received a score of 4.
- Finally, the CVE-2020-25687 vulnerability. It also affects versions prior to 2.83.
In short, we must always have the latest versions that can correct problems in our systems and devices. In this case we have talked about a series of seven vulnerabilities called DNSPooq, but it is something that we must apply in all cases.