Apple is one of the technology companies with the largest presence worldwide. The iPhone is one of its flagship devices and millions of people around the world use it. Some of its main features are the long durability of the devices, in addition, the user interface is very modern and intuitive. The latter, above all, can mean a problem in terms of user safety.
This guide will tell you what you need to know to avoid being a victim of cyber attacks like Phishing . However, even if you are not an Apple user, the shared information will be very useful if you use Android.

Many of the people who use iPhone use the default email client to manage their messages on a daily basis. One of the features of iOS Mail is that the interface is very clean, and has almost no information in small print. Let’s take a look at a reference screenshot from Apple’s official site below:
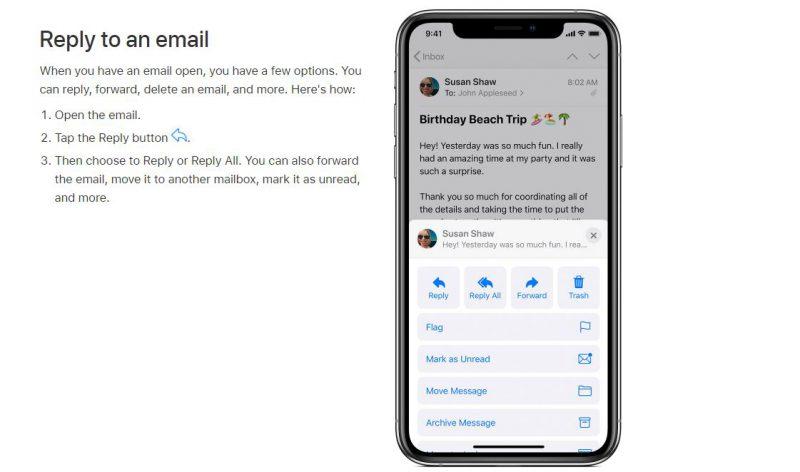
Up, we can read who is the sender. In the case of the example, it is Susan Shaw . It can be a name of someone we know or the name of a person who sends some type of newsletter on behalf of a certain organization. What’s dangerous about this is that we can’t see the person’s email address detail at first glance. We must keep in mind that a cybercriminal can impersonate even the President himself, in order to attract our attention and follow what is indicated in the content of a malicious email.
More than one person would say that the solution is somewhat obvious: we must click on the person’s name to display the email detail. Others might say that when you click “Reply” , when you are going to write a reply message, the email appears there. However, not everyone thinks the same way and does some activities without much thought. More than anything, because we are used to doing everything very quickly, without stopping at the fact that you could lose or violate your data in a matter of seconds, although that is the least that could happen.
Although you may think otherwise, Apple users are not spared from Phishing. It is important to take essential steps to prevent it, in order to have a more secure email experience. Likewise, Android and device users with other operating systems must also have a well-established security awareness, since the risks of attacks increase every day.
Is it possible to receive malicious email from a legitimate sender?
If it is. This is one of the great allies of Phishing, it is only necessary that a user can receive a message from a suspicious sender, and that the message contains a malicious program. This program infects the user and appropriates their email account. From there and through instructions, the infected user can send malicious messages to other users with content specially created to mislead even the most attentive. It is like a botnet that is created by spreading malicious software by email.
However, there is another method called Forged «From» Address . In other words, it is an ” altered sender . “ You may receive an email from a particular email address, however the exact sender is not the original. Originally, the communication protocols that give life to emails do not check whether the person who sends a message does so from a certain address.
How to know if they have altered the sender and avoid Phishing
We will demonstrate an example using Gmail . Like any other email client, spam messages are stored in a separate folder, so you can better identify and delete them as soon as possible. Keep in mind that this example works in any case , regardless of whether you have an iPhone or not.
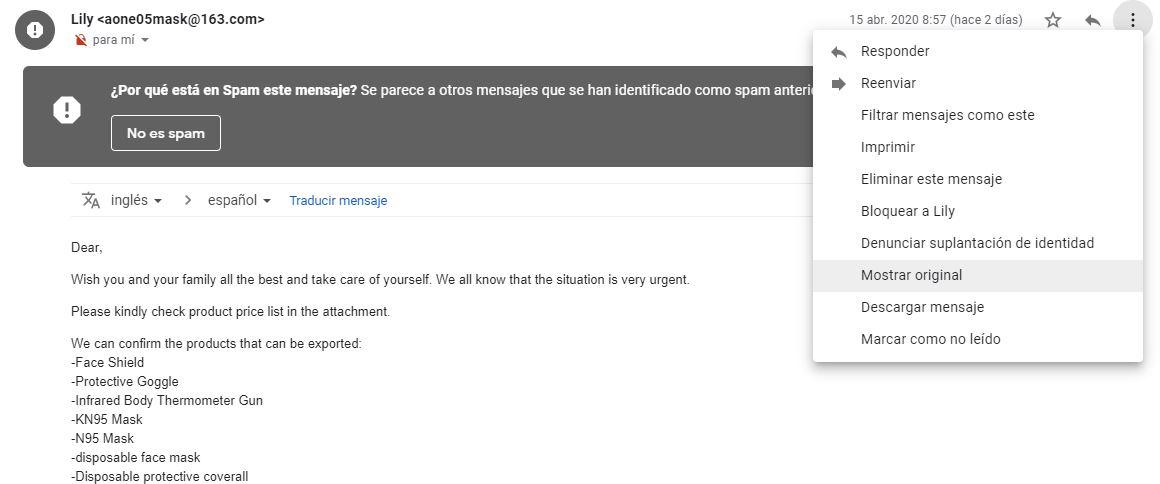
- We enter our Gmail tray.
- We select the Spam folder.
- We click Show original .
Once you have clicked on ” Show original “, a new tab will open where you will get all the information regarding the received email message. Not only will you be able to view the message, but it will also be possible to have a trace of the path of the message content through the different servers, including Google’s.
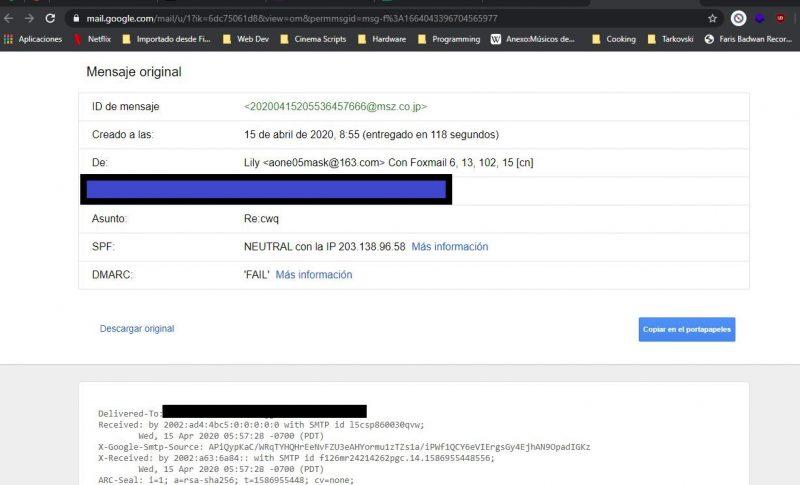
Below you will see a very extensive text. Although it will only be necessary to emphasize some sections. Thus, you can easily check whether the message you have received has the sender altered or not. First, let’s go to the bottom of the page and look at the “From” . Remember that this is the sender of the message.
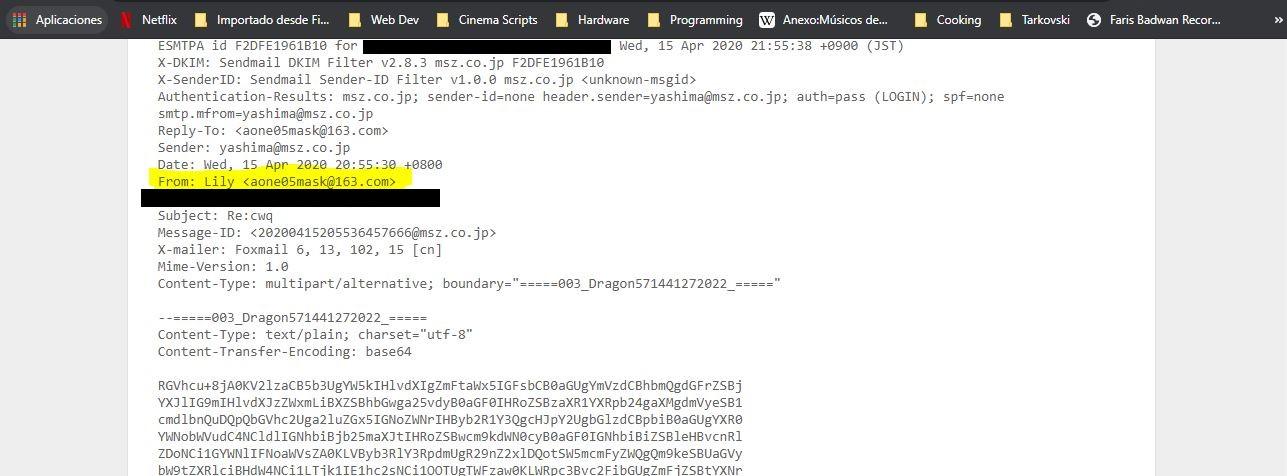
Now let’s look at the two Received above: “Received: by” and “Received: from” . If the sender were an email address “@ gmail.com”, the message should be received lastly by one of Google’s servers and not any other server. If the case is different, we are facing a potential malicious email.
An easier way to identify something irregular or suspicious in a message is IP addresses. If the senders correspond to suppliers or organizations that are from Spain, but the IP points to any other country, such as Singapore, this should generate suspicion. Of course, Singapore is a random example.
We can still be more practical! We simply need to pay attention to the content of our email. If you sense an abysmal sense of urgency to take action like logging in to keep an account active, or to change your password as soon as possible, something is wrong. Phishing is one of the attacks that has proven to be super effective, mainly due to the lack of attention from users.
If there is any activity that involves the use of sensitive data such as a data update or an account problem, the entity must contact the customer by official means. Only a minute or less is necessary to prevent the loss of your data through Phishing. Don’t risk it!