Today we have various methods to use biometric authentication. Some of the most used today are facial recognition, fingerprint and iris recognition. However, there are some more such as vascular biometrics based on the pattern of our veins and also those based on the recognition of voice, handwriting and signature. On the other hand, cybercriminals are working to breach these security systems to take advantage of it. Whether they are more or less successful depends on how they are implemented. In this article we are going to talk about whether they could spoof facial recognition.
The first thing we are going to do is find out what a facial recognition system is. Then we will see if it is possible to supplant facial recognition and what would happen in the event of such an action.
What is and how does a facial recognition system work?
We could consider a facial recognition system as a program run by a machine, such as a computer or a smartphone, and that is going to be in charge of automatically identifying a person thanks to a digital image. This procedure is carried out through an analysis of the facial characteristics of an individual, extracted from the image of a photograph or a single frame from a video source and then compared with a database.

Facial recognition is currently an area of research where image processing, pattern recognition, computer vision and neural networks are very important. On the other hand, 2D projection techniques can be used to carry out this process, although other more complex and safe techniques could also be used by using 3D techniques. One difficulty with this procedure is that it can be done in real time, and as it requires a lot of workload, it is not always possible. The time will depend on the machine that does it, and whether its databases are larger or smaller.
Impersonate facial recognition, is it possible?
Previously, this facial recognition system had been widely adopted at the business level. Currently, things have changed and it is already very common to also see them on devices such as smartphones and tablets.
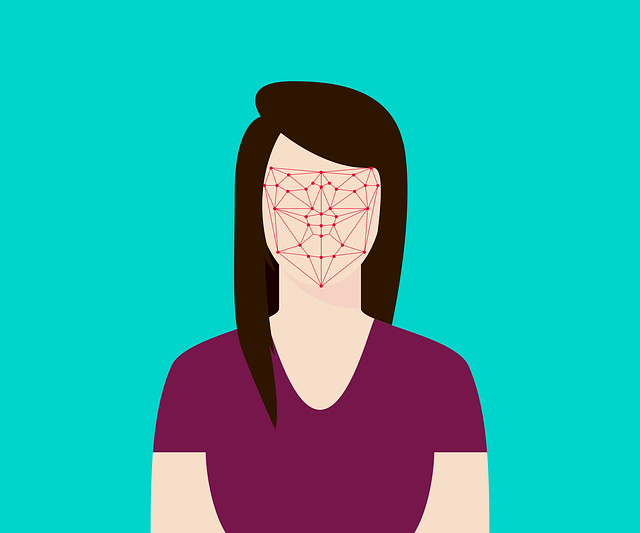
The problem is that this face unlock is not always as safe as it should be. This system is usually based on the comparison of a certain number of points on our face. The higher the number, the safer it will be, and if it also implements 3D techniques, the better.
In some cases, our images can be obtained through what we publish on social networks and used to supplant facial recognition. For this reason, we must be careful with what we upload publicly and perhaps at some point you will be interested in knowing how to erase the trace on social networks.
The risks of biometrics when it is compromised
Another of the most used ways to log in is the use of credentials. Thus, by means of a username and password we access an account. Security is based on that password being robust and that we use it in a single place. In the event of a security breach, we could easily replace it with another. This does not imply that they have been able to access our data and violate our privacy. That is why from this article we recommend activating two-factor authentication if it is available for our account.

On the other hand, in biometric authentication such as facial recognition, things are very different. In the event that a hacker succeeded in spoofing a person’s facial recognition, we would have a serious problem. The reason is very simple, our biometrics cannot be replaced. In this case we cannot change our face so we can say that biometrics does not always solve our problems. From that moment on, they could supplant facial recognition whenever they wanted and we would have no other option than to have to change the security system.
Finally, with the aim that images published on the Internet cannot be used to supplant facial recognition, new developments are being made. The procedure would consist of modifying an image without the human eye detecting it. What they do is use a tool to slightly change those images without us being able to find the differences.