
Normally in our homes we use WPA2-Personal or WPA3-Personal security, this type of security consists of configuring a “master” key that all wireless clients will use, this key is called a pre-shared key, and all clients who want to connect must know it and put it on your devices to connect. In many home routers we have the possibility of configuring WPA2-Enterprise or WPA3-Enterprise, in this case, authentication is done through username and password, and it is necessary to use a RADIUS server to authenticate clients. Today in this article we are going to show you how we could configure WPA2 / WPA3-Enterprise on any router using a NAS to authenticate Wi-Fi clients.
Locate and configure the IP of the NAS that will have the RADIUS server
The first thing we must do is locate the NAS server on the network, it is very important to know its private IP address, because in the wireless network configuration we will have to enter this IP address to authenticate the wireless clients. It is highly recommended that this private IP address never changes, therefore, we have two possible options:
- Put fixed IP on NAS server
- Configure the router’s static DHCP, and set a static IP address at all times.
In this way, we will force this NAS server to never change its private IP address, something very important for everything to work properly.
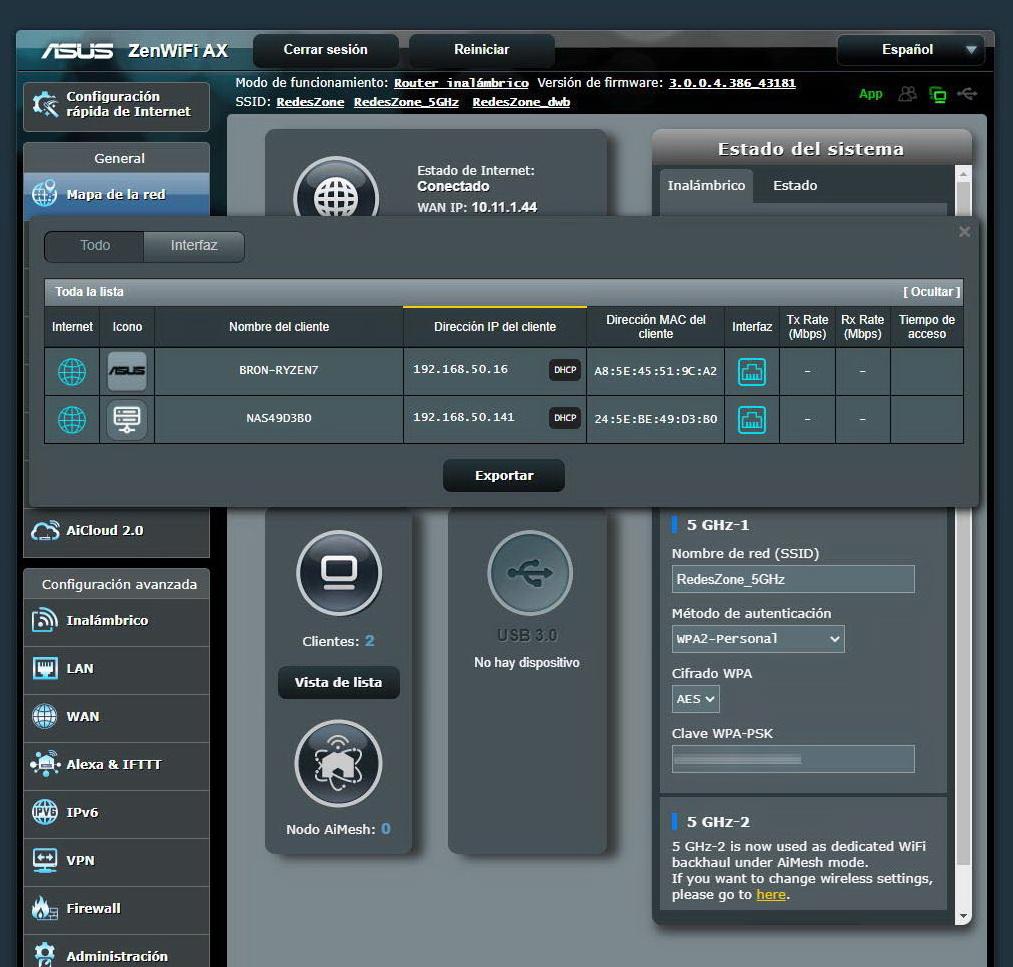
Once we have correctly configured the NAS or the router so that the NAS server never changes its IP address, we are going to configure the server.
Configure the FreeRADIUS server
FreeRADIUS is the software par excellence to configure a RADIUS server with very advanced options, this software has support for different types of authentication and it works really well. A very important feature is that it is compatible with any operating system, which is essential for maximum compatibility.
Configuring this server is very complex, you have to configure configuration files in an advanced way, create a certificate authority and more. If we use a NAS server like the QNAP, it will greatly facilitate the task of not having to configure a server on a computer, on a Linux-based server or on a Raspberry Pi. All QNAP NAS servers support the ability to easily and quickly configure a server.
All we have to do is go to the section ” Control Panel / Applications / RADIUS Server “. Once inside, what we have to do is enable the server and allow access to the system’s user accounts, although the latter is optional and not necessary.

Once the server is activated, in the “RADIUS Clients” section we must directly register the router that will forward all the authentication to the server. The data that we will have to put are the following:
- Name : we put a name to the client
- IP address : we put the private IP address of the router, in our case, 192.168.50.1
- Prefix length : we put 32, indicating that only that IP address will be the client.
- Secret key : we define a strong password, it is the authentication key between the router and the FreeRADIUS server. This password is not the customer’s.
The configuration would be as follows:

Once we have configured the client, now we will have to create the users. In this case we will have to create a user for each WiFi client that we are going to connect to the wireless network, we will have to indicate the user’s name and also their password. All clients that are in this list of «Users» will have permission to authenticate in the server, and therefore, get WiFi connectivity without limitations of any kind.

Once we have configured the server, we must go to the router to configure it correctly, since we must set the WPA2-Enterprise or WPA3-Enterprise authentication, and indicate different data.
Configure the router with WPA2 / WPA3-Enterprise and RADIUS authentication
The first thing we have to do is go to the ” Advanced / Wireless Settings ” section. In this menu we will have to select the type of encryption WPA2-Enterprise and several additional menus will be displayed automatically that we will have to complete:
- Authentication method : WPA2-Enterprise
- WPA encryption : AES
- Server IP address : 192.168.50.141
- Server port : 1812
- Connection secret : 123456789 (in our case, it is the password that we put on the server in the “RADIUS Clients” section).
Next, you can see how it would look in our case:

All this information that we have indicated should be reflected in the “RADIUS Configuration” section with the frequency band that we have configured. Here we will see the private IP address of the server, port and also the connection secret.

Once we have correctly configured the router, right now we can authenticate the different WiFi clients with their corresponding username and password that we have created previously. We are going to show you how to connect a Windows 10 computer and an Android device.
Connect a Windows PC to WiFi using WPA2-Enterprise
In order to configure a WiFi network with WPA2-Enterprise we will have to manually configure the connection to the network. We have to go to the ” Control Panel / Network and Sharing Center ” section. In this menu we have to click on « Set up a new connection or network «.
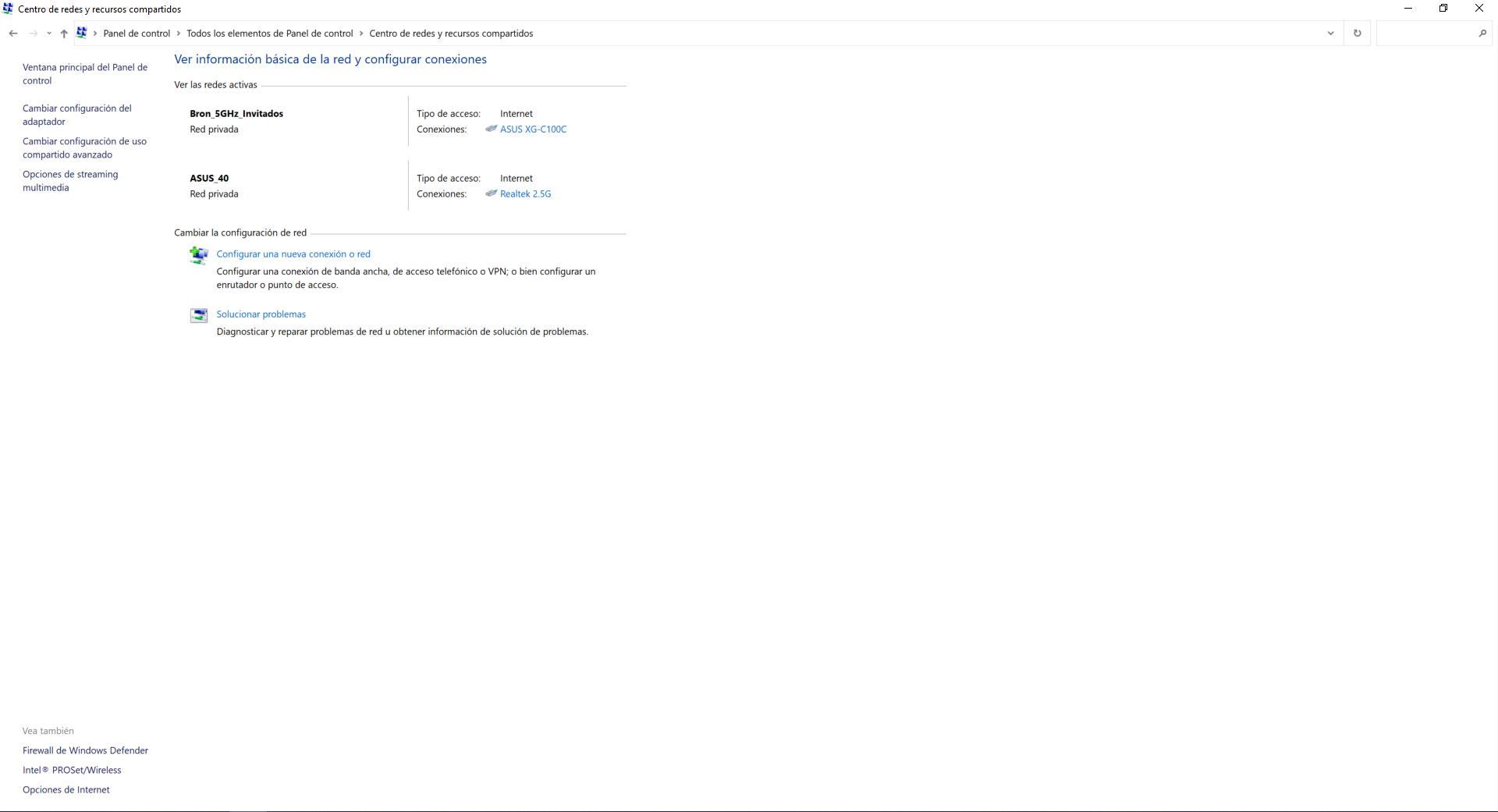
In the list of available options, we have to click on ” Manually connect to a wireless network ” and click on next.

Now we will have to enter the name of the WiFi network to which we are going to connect, this network name or SSID must be exactly the same as in the router. In security type we choose “WPA2-Enterprise”, the encryption type will be AES obligatorily, it does not allow to change it. The “Security key” section will be disabled, it is completely normal.
Now we click on « Start this connection automatically » to disable it, and the same with the option of « Connect even if the network does not broadcast its name «.

When clicking on next, we have to click on ” Change settings ” as indicated by the Windows wizard. We will get a menu with everything we have configured so far.

In the “Security” tab we choose the option “Microsoft: Protected EAP (PEAP)” and click on “Configuration”:

In this menu we will have to click on « Verify the identity of the server by validating the certificate » to disable this option. We leave the rest of the options as they come by default.

When we connect to the WiFi wireless network, it will now ask us to log in, we will have to enter the username and password that we have registered on the server in the “RADIUS Users” menu.

Once we enter the credentials, if we have not made a mistake when entering the user credentials, we can perfectly see that we have logged in and have an Internet connection without problems.

Once we have successfully configured a Windows PC, let’s see how to connect an Android smartphone.
Connect Android smartphone to WiFi with WPA2-Enterprise
In Android smartphones we have to click on the WiFi network to which we want to connect, it is not necessary to manually add a wireless network as it does in Windows operating systems. In this case, as soon as we click on the WiFi wireless network, different configuration options will appear. We have to fill it in the following way:
- EAP method: PEAP
- Phase 2 authentication: MSCHAPv2
- CA certificate: Do not validate
In the “Identity” section we will have to enter our username that we have registered on the server, and in “Password” we will have to enter the access code. We will automatically connect to the WiFi wireless network, and we will be able to surf the Internet without any problem, making use of WPA2-Enterprise and the type of 802.1x EAP encryption that our smartphone indicates to us.



Another possible configuration on these smartphones would be the following:
- EAP method: TTLS
- Phase 2 authentication: MSCHAPv2
- CA certificate: Do not validate
In the “Identity” and “Password” section we will also have to enter our credentials, as before.
As you have seen, configuring WPA2-Enterprise authentication on a router is very simple, and much more if we use an authentication server like the one integrated in QNAPs. However, we cannot download the CA to install it in each and every one of the WiFi wireless clients, therefore, we could still suffer a Rogue AP attack where a cybercriminal impersonates the legitimate access point, something that if we had the CA in our system would not pass because it is validated before establishing a connection. In order to have this security, it will be necessary to set up our own FreeRADIUS server from scratch, or in a system like pfSense where we do have all the configuration options available.