Apple has traditionally been the company with the most secure operating systems. However, for a year now, Android has become a more secure operating system, where the vulnerabilities found in Google’s operating system are paid much more expensive. The fault lies with the Apple browser , which has a serious vulnerability that allows spying through the camera .
Apple is in charge of maintaining Safari . Your browser is closed source, unlike what happens with Chrome. Therefore, the Google browser has many more eyes on it, finding possible vulnerabilities. In the case of Apple, the company is on its own, and the seven vulnerabilities that Ryan Pickren , a former security engineer at Amazon Web Services (AWS), have discovered, demonstrate this.

7 vulnerabilities to spy on the camera on iOS and macOS
Of the seven vulnerabilities found in Safari ( CVE-2020-3852, CVE-2020-3864, CVE-2020-3865, CVE-2020-3885, CVE-2020-3887, CVE-2020-9784, and CVE-2020-9787 ), three of them allow a hacker to access the camera of a Mac or an iPhone when the user clicks on a malicious link .
Almost any application requires specific permissions to access the camera and the microphone , except those of Apple itself, such as Safari. Thus, Pickren gradually discovered the vulnerabilities until he managed to access the camera. For example, in the case of Safari for iOS, the browser can access the camera without asking, and with new technologies such as MediaDevices Web API (used in WebRTC broadcasts), websites are allowed to take advantage of this permission. This is how for apps like Skype or Zoom , but it allows access to the camera if a vulnerability is found in the system.
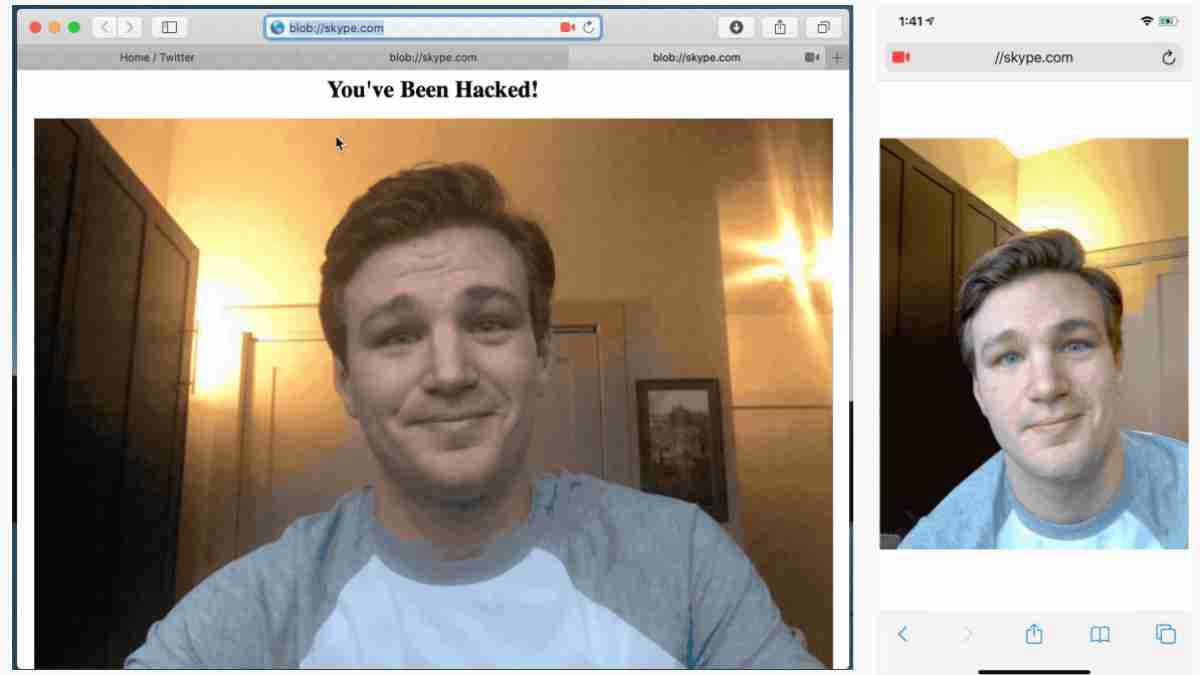
The CVE-2020-3864, CVE-2020-3865, and CVE-2020-9784 vulnerabilities were fixed in Safari 13.0.5 released on January 28 , while the other four (CVE-2020-3852, CVE-2020-3885 , CVE-2020-3887, and CVE-2020-9787) were patched on March 24 with Safari 13.1 . The problem is that, although they have been fixed, in the future new ones may be discovered that give access to the camera, since Safari is still a vulnerable browser.
Apple has paid him $ 75,000
Apple classified the vulnerability as “Network Attack without User Interaction: Zero-Click Unauthorized Access to Sensitive Data,” for which they paid $ 75,000 . This figure contrasts with that offered by Zerodium, a private company that then resells vulnerabilities to spy companies. A remote code execution and local privilege escalation vulnerability costs $ 500,000. The fact is that it was necessary to interact with the link at least once by clicking on it, so Apple’s choice for that category may have been to pay a higher figure and prevent researchers from being tempted to send the vulnerability to private companies that pay even seven times more.
Source> Ryan Pickren