When we surf the web we can be victims of many types of attacks. There are many threats that can jeopardize the proper functioning of our systems and our own privacy. This increases if we connect to a public Wi-Fi network. However, browsing HTTPS encrypted pages reduces the risk that our data and information may leak. However, to what extent is this really so and are we safe? In this article we will try to talk about it.
Are we safe on a Wi-Fi network just by browsing HTTPS?
When browsing public wireless networks, the risk that our data may be filtered must be taken into account. We don’t really know who may be behind that Wi-Fi network and what interests it may have. We may run into some type of hacker that is waiting to steal data from users who connect.
The problem is that sometimes users may believe that browsing HTTPS encrypted pages already makes browsing safe. It is true that it is very important that when entering data and personal information in the different pages that we use we do so in pages of this type.
The main issue is that browsing through HTTPS pages and through public networks can also be a problem. Any attacker could collect certain data even though we browse through encrypted pages. This data may include the domain name or the size of the files we download, for example. In short, even if the page is encrypted, they could access certain metadata.
It is true that the username, passwords, forms that we fill out or the messages we send will be protected because the HTTPS communication guarantees us the confidentiality, authenticity and integrity of the connection to the web server. However, there are methods to “skip” this HTTPS in certain circumstances.
The importance of the HSTS protocol
Regarding the last thing we mentioned, the HSTS protocol is of great importance. It is a security mechanism that is designed to secure HTTPS connections at all times. Mitigates SSLstrip attacks that allow you to “lift” the HTTPS connection, and that can carry out possible cybercriminals to access the information and data we send.
This is something that is the responsibility of the person in charge of the web. It is part of the security of the server and, ultimately, of a domain and its subdomains. It must be enabled to really make that page safe. This means that even if we enter HTTPS web pages they could lift that security barrier if the page does not have HSTS activated , and as long as we have previously entered that page when a cookie is saved, or we have the browser pre-configured for a domain in question.
In the case of Google Chrome, which is the most popular and used browser today, we would have to enter chrome: // net-internals / # hsts. Once here we can add domains manually, as well as delete the ones we have saved.
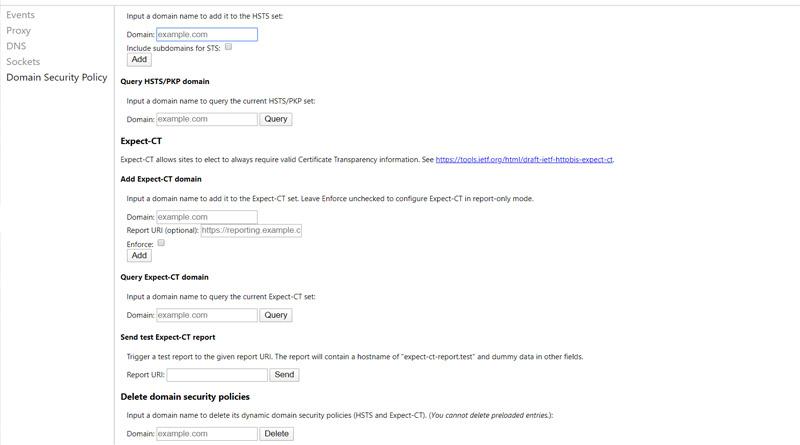
In addition to this we have to enter the domain name in the Query HSTS / PKP domain section and click on Query. The answer should be Not found. With this we will have cleared the HSTS cache in our browser, but it is not advisable to do it for security. If at any given time the browser returns an error when connecting, it is possible that the site certificate has expired, or we are doing a MitM attack.
Applications to decrypt HTTPS traffic
Therefore we can say that a hacker with the necessary knowledge could decipher HTTPS traffic when we connect to a public Wi-Fi network. An example is the SSLstrip application . Basically it allows a Man in The Middle attack to be carried out, and what it really does is to deceive the client by converting the web you want to visit from HTTPS to HTTP. This way you could access the information.
But the case of SSLsTrip is not unique, since there are other tools with a similar purpose. Another example is Breach , a script that uses a technique capable of obtaining information that contains HTTPS packets. In short, even if we browse an HTTPS page on a public Wi-Fi network, our information may be in danger. There are methods through which hackers could lift the barrier and make those connections not as safe as we would like.
Our advice is to avoid entering personal information, passwords and confidential information whenever we browse through wireless networks that may be insecure. It is also convenient to make use of a VPN.