We have seen it over the last few years, and it is that the creators of malicious code are launching more and more dangerous products. This is the case with this virus, an element that even resists formatting of the Windows computer.
This type of malicious elements that can attack our PC are among the most feared in the world of technology. Precisely for all this, most users take a series of precautions such as installing antivirus and other security solutions.

Keep in mind that some of these take control of the computer, others steal sensitive data, or some simply damage the operating system. In this specific case we are going to talk about Moonbounce , a virus that can resist the format of the units and the reinstallations of Windows. We are talking in these lines about a new malware that has spread in recent days. Named as Moonbounce, it is malware that can survive formatting drives , for example.
Keep in mind that it is not a Trojan or a normal virus that affects Windows. In this case we find a complex bootkit that has as its objective the firmware of the motherboard itself or UEFI . Therefore, this allows it to survive changes made to disk drives or to the operating system itself. We must know that the aforementioned motherboard has its own storage chip, the flash memory. This contains the software needed to boot up and communicate with the rest of the PC’s hardware.
How to delete Moonbounce virus from PC
In fact, one of the major security companies, Kaspersky , claims that this Moonbounce malware was created by a hacker group called APT41 . This group in the past was involved in cybercrime campaigns around the world. The bootkit was first spotted in spring 2021 and is more advanced than the previous two of its kind.
To give you an idea of what we are talking about, Moonbounce targets the CORE_DXE in the BIOS of the PC’s motherboard. Thus, it is executed when its boot sequence is started and the malware intercepts certain functions to implant itself in the operating system. After that, it communicates with a remote control server and delivers a malicious payload to neutralize system security.
Attackers can use Moonbounce to spy on users, archive files, collect network information, etc. To all this, we must add that the main antiviruses cannot track the infection on the disk. This means that it runs in memory without relying on files on the drives.
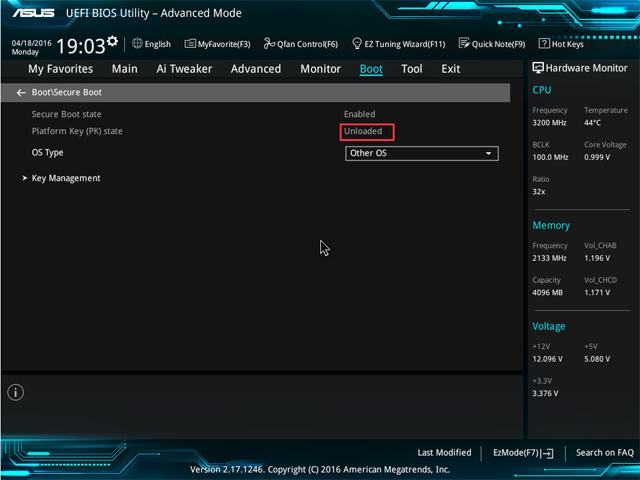
And it is that this type of malicious code is difficult to eliminate, but not impossible. One of the main reasons is that antiviruses are ineffective outside of the operating system. Therefore, one of the measures to get rid of this malware is to enable BIOS secure boot . We can also add a password to this component which blocks unauthorized firmware updates.
In the event that we did not enable secure boot or set the password before the potential attack, we can always flash the UEFI to get rid of the annoying malware.