When using a computer, mobile or any device connected to the network, there are many threats that we can find. There are many types of viruses, Trojans, and malware in general. Obviously not all act the same and it is important to know to what extent they can damage the operation of a computer, steal data or infect other devices on the network. In this article we are going to talk about backdoor Trojans. We will see how they work and what to do to avoid them.
How a backdoor Trojan works

We can say that there are different methods to attack a computer equipment. It may happen that we find a virus that causes the system to malfunction, a keylogger that collects all the passwords, a ransomware that encrypts the files … In the case of a backdoor Trojan, what is going to allow the attacker is to have a full control over that computer, remotely.
If we are the victims of a backorder , the hacker behind that threat is most likely going to gain access to our infected system. Basically what it does with this Trojan is to create a back door, first undetectable by the victim, which will grant access.
It should be noted that not all Trojans are the same. We can see, for example, exploit Trojans, which take advantage of vulnerabilities in systems or applications, or also rootkits, which hide certain actions in the system and thus the antivirus cannot detect them. Backdoor Trojans are yet another of the different types. What could an attacker do if they have infected our computer with a backdoor Trojan? The main thing to keep in mind is that you will be in full control in most cases. This means that you will be able to execute commands, send or receive files, read information, erase data … If you want, you could turn off the computer at any time or open programs at will.
One of the main problems is that this type of threat is usually very stealthy. That is, we can have the computer infected and not realize it until after a while. An attacker may be reading all the messages we send or have access to folders for weeks, but we don’t know.
Signs That We Have Trojans
So how do I know if I am infected? Although it is a type of threat that will not always show us some quick evidence, we can take into account some things that help us understand that we are victims of a backdoor Trojan or similar.
Logically the first thing is to see that the equipment works badly . For example we see that when opening programs it goes very slow, when we open web pages they take longer to load than normal, the system takes a long time to turn on or off, etc. We could also detect it if programs have disappeared or have stopped working correctly. This can even affect the antivirus itself. Perhaps the attacker, to have full access without restrictions, has disabled Windows Defender or whatever program we have to be protected.
Another clear indicator is when we see Internet consumption in real time, something that we can easily see in Windows if we enter the Task Manager, go to Performance and there we click on the Internet. It will show us the data consumption at that moment. If we see that there are strange peaks, an excessive consumption when we are really not doing anything, it may be a sign. Something similar happens with the activity of the hard disk . We can also analyze it if we go to the Task Manager, Performance and this time we see the Hard Disk section. There we can see the activity time and the graph. If we detect something strange, it may be that an intruder has sneaked a backdoor Trojan into us and is using the system.

What to do to avoid backdoor attacks
After seeing what a backdoor Trojan is and how we can detect if we are victims, we will also see what to do to protect ourselves. We are going to give a series of interesting tips to increase the security of our computers.
Have the equipment always updated
The first thing you should do to avoid backdoor Trojans is to always keep your devices up to date . This is very important, as bugs sometimes appear and hackers take advantage of them to sneak malware and control computers.
Not only do we have to update what is the operating system, such as Windows, but also the programs we use and the device drivers. It is important, among other things, to update the network card driver. This will help not only that there are no security problems, but also that the performance is optimal.
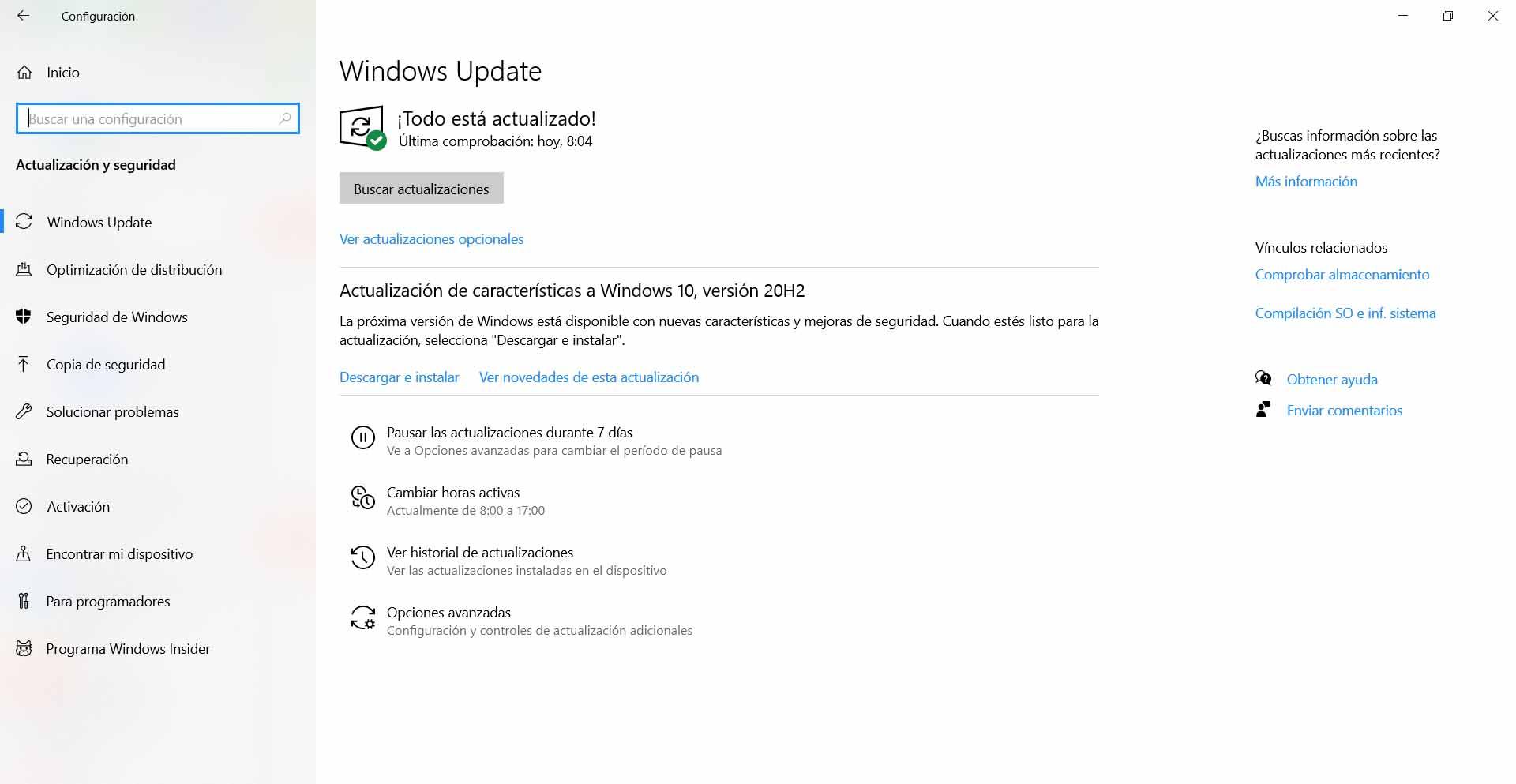
To update Windows we must go to Start, enter Settings, Update and security and there it will automatically show us the latest version available. If there is something pending to update we can execute it.
Use security programs
Of course, security programs are very important. For example antivirus such as Windows Defender, Bitdefender, Avast … These tools are very useful to prevent the entry of threats such as backdoor Trojans, but also to detect malware that is already on the computer.
Whenever you suspect that there may be a virus or similar on your computer, it is very important to run the antivirus and completely analyze all folders and files. This will help prevent hacks from occurring.
Check the system periodically
Even if we have everything up to date and use good security programs, something can always escape. For this reason, it is also essential to check the system from time to time. How can we do it? For example, looking at the installed programs and checking that there is nothing wrong, seeing the consumption of Internet data, the use of the hard disk, etc.
Carrying out a regular review can help detect problems early. This will remove a possible backdoor Trojan before it can steal data or further compromise security.
Common sense
On the other hand, something that can not be missing is common sense. We must avoid making mistakes that can help attackers. In most cases they are going to need us to do something to sneak in a backdoor Trojan.
For example, we could mention a fake link that we open by email, download an attachment, click on an insecure page … All of this could contain malware and serve as an entry point for attackers.
Ultimately, backdoor Trojans are a significant threat that can allow an attacker to remotely enter your computer. They could have access to all files, read messages, install programs, turn off the device … We have seen what we can do to avoid being a victim and be protected.