One of the biggest benefits of Linux is that it allows us to find a distribution that suits our needs. If you need to audit wireless networks, you will find a distribution for it. In this article, we are going to introduce you to WiFiSlax , one of the best distributions for Wi-Fi and pentesting. It is presented as a suite of tools to be able to comprehensively manage all our Wi-Fi network auditing activities. In addition to taking a tour of some of the tools it contains, we will show you how to run it through a virtual machine.
WiFislax is what we need to start learning about wireless network auditing. It is completely free and you don’t need anything to start using it. Being a complete operating system, it is necessary to create a bootable CD or USB and start it on our computer. However, we could also install and run it in VMware or Virtual Box so we don’t need to create a bootable LiveCD / USB.

Is it the same as Kali Linux ? No, although many tools are shared by both operating systems, WiFiSlax has many more pre-installed tools for Wi-Fi audits than Kali Linux, in addition, WiFiSlax has a large number of dictionaries.
With WiFiSlax you will not only find specific tools for its purpose, but you will also have the possibility to install extra modules to add more features. Remember that this is practically an operating system like Windows, Mac OS or other Linux distributions. Next, we will demonstrate a couple of alternatives to install and test it as soon as possible, by using virtual machines.
Start WiFiSlax in Windows 10 using VirtualBox
If you don’t already have VirtualBox on your computer, you can download and install it through this link . It is available for both Windows, mac OS, Linux, and Solaris. Virtual Box is one of the best known and used virtualization software.
On the other hand, you must enter the Wireless Security forum to download the latest version of the Wifislax ISO file. Likewise, and if you wish, older versions can be found on the official portal of this operating system. In addition, a very important detail is that we can install extra modules to increase the functionalities.
Once you have downloaded, you can proceed to create the virtual machine in VirtualBox . Go to the Machine> New option (or you can choose the Ctrl + N shortcut) . Then, you will indicate the name, the folder where the machine will be stored, the type (Linux) and the version (Other Linux 64-bit) . Click on Next .
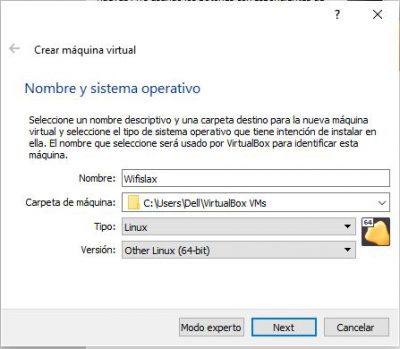
Select the amount of RAM memory. If you will use it for essential tests, 1 GB is enough and this will help the real operating system not run out of RAM, although if you have 8GB of RAM on your computer, we recommend that you select 2GB for the virtual machine.
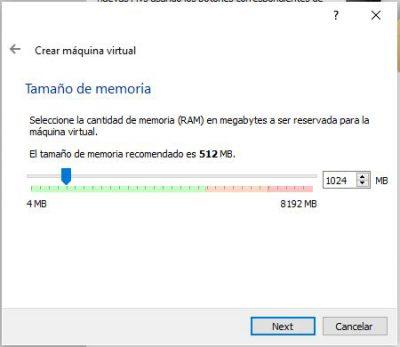
For the hard drive, if this is your first time, select the Create a virtual hard drive now option. If you already have a virtual hard drive file, you can add it. Click Create.
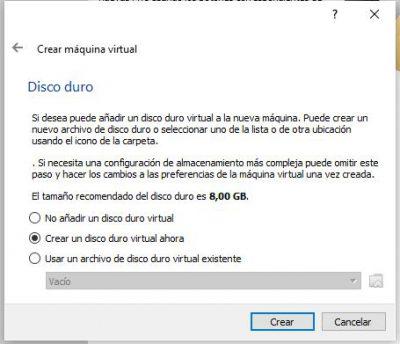
We can select the first option: VDI (VirtualBox Disk Image) . Click on Next.
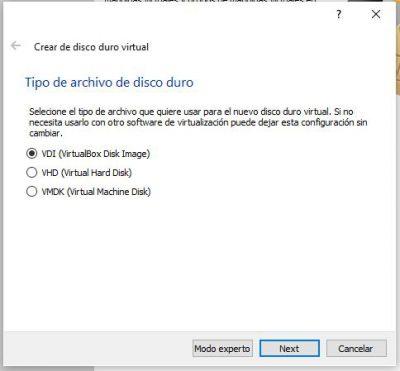
In this case, the fixed size virtual hard disk option will be enough to start using Wifislax.
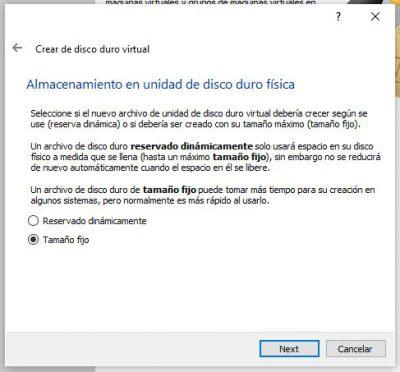
You can modify the folder where the virtual hard disk will be located. However, leaving it in its default location will be no problem. On the other hand, select the size of the hard disk, with 10 GB it will be enough for a use of the essentials.
We click Create and wait a few minutes until the virtual hard drive is created.
Once the installation is complete, you will see a screen like this. In which you can have all the information related to your newly created virtual machine.
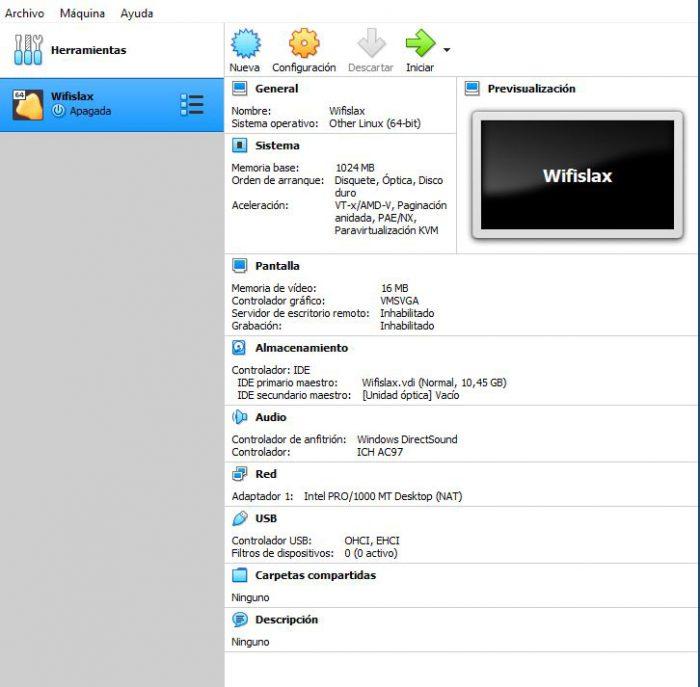
Wireless Network Card and Master Primary IDE Settings
A very important fact to keep in mind is that, if your computer has an integrated Wi-Fi network card, this card will not be recognized by WiFislax as such, but as a wired network interface. It won’t do any good if you disconnect from the network and try to connect to the virtual machine.
What you should do is have an external wireless network card. The most practical and fastest option to do so is with a Wi-Fi adapter via USB . Currently, we can find multiple very cheap options that are Plug-and-Play , you connect it and you can now use it without problems.
Before launching the virtual machine, you are going to configure your external wireless card as the main network adapter. In this way, you will make the virtualized system recognize it. Once it has recognized it, it will stop working on your base operating system and will start operating within your virtual machine.
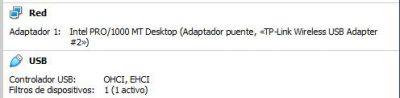
On the other hand, you must pre-load the ISO image in the secondary IDE so that when the virtual machine starts, it manages to locate Wifislax and start as the operating system.
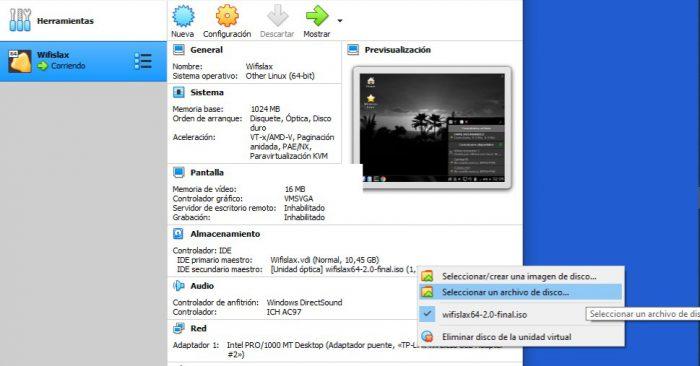
Launching the virtual machine
It is time to start it. For that, we must click on the green arrow button that says Start . In principle, it will show you some options and you can simply press Enter to select the first option. Then, you will wait a few minutes until the system finishes starting.
If within Wifislax you notice that it detected a wireless interface, but it is still operating within your base operating system, you should disconnect the USB from the wireless card and reconnect it after a few seconds. There, you should start listing the available networks and be able to connect normally.
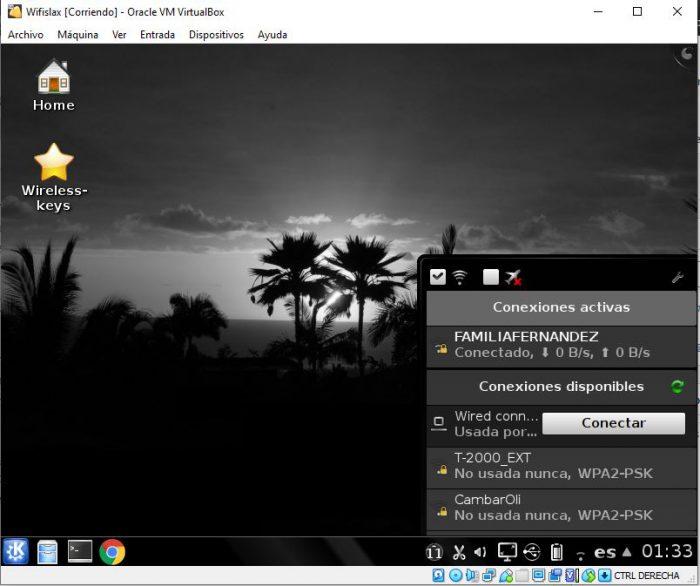
Start WiFiSlax in Windows 10 using VMware Workstation
This is another highly practical alternative to launching this ha-cking-oriented operating system for wireless networks. VMWare can be downloaded through this link and in principle, you can try its Pro version for free for 30 days. Just like VirtualBox, installation doesn’t take too many steps.
A window like this will appear:
You will click Create a New Virtual Machine. To facilitate installation we choose the Typical option. It is the simplest and will help us launch the machine more quickly. We click Next .
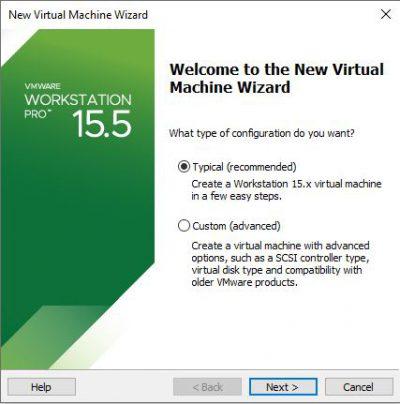
Choose the last option I will install the operating system later . This will allow the virtual machine to be created blank and you will add the ISO image later. However, and if you prefer, you can choose the second option and attach the ISO image beforehand. Click on Next .
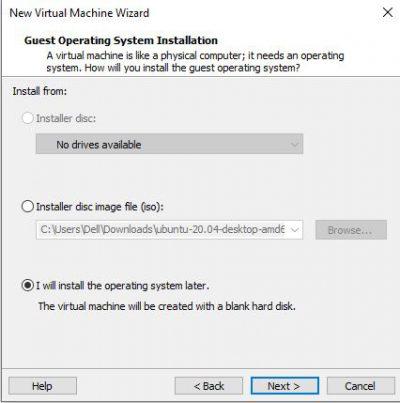
You choose the Linux option and the Other Linux 5.x or later kernel 64-bit version .
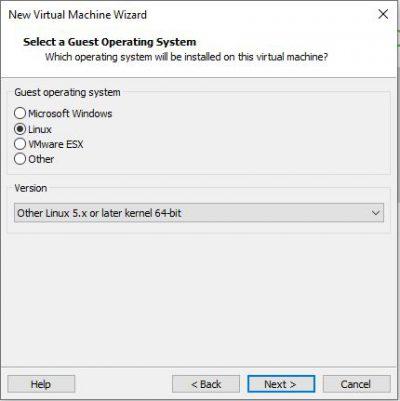
We choose and write the name that we will give to this virtual machine. We indicate the location of it. Although by default, the location indicated by the creation wizard is fine and it is not necessary to change it. Click on Next .
Now you must indicate the capacity of the hard disk. In this case, with 10 GB it is more than enough. Then, you must indicate whether said virtual hard disk should be stored as a single file or that it should be divided into multiple parts. We will mark the first option that is the most practical. Click on Next .
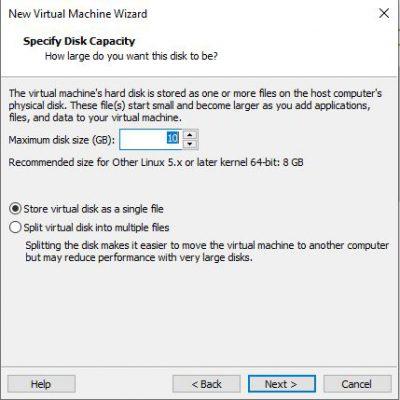
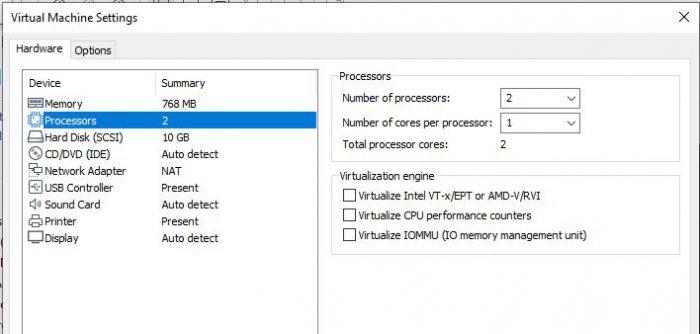
With this we are almost done. Now we must verify that in the Hardware section there are at least two processors. This will help us to make the machine run much more smoothly, you can also choose a processor and two cores. As for the RAM, it is recommended 1GB as a minimum, although if your computer supports it, it is best to have 2GB of RAM.
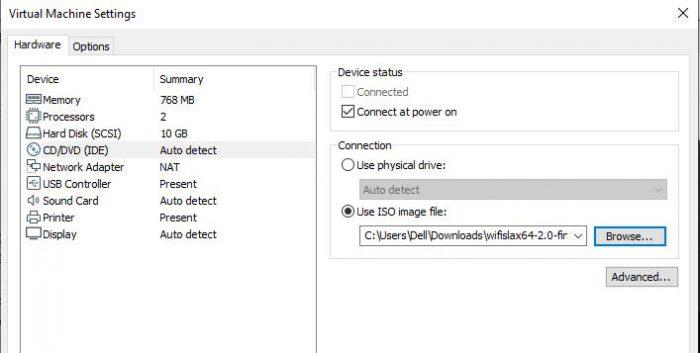
On the other hand, in the CD / DVD (IDE) section we must indicate the Wifislax ISO image. This is essential for our machine to work.
Ready! On the side of the VMWare window you will see your created machine. Select it, click the button with the green icon and it will start running.
What programs are available in WiFiSlax?
We can see that we have multiple programs installed to carry out all the activities corresponding to the audit of Wi-Fi networks. We see several dictionary generators, forensic computing tools, the Aircrack-ng suite, wireless network crackers with WPA encryption and also with the WPS protocol.
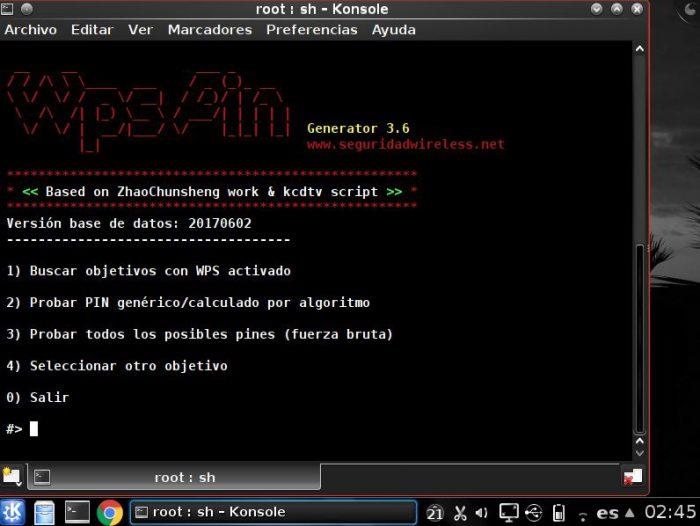
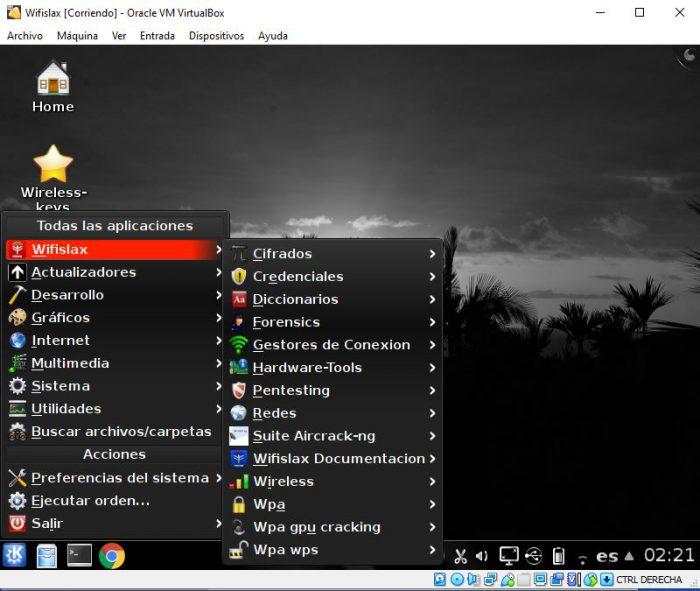 WPS Pin is a program that runs through the console that will help us ha-ck wireless networks that have WPS activated. If we hit the WPS pin of our target network, we would already have connectivity to it, in addition, it would return the WPA / WPA2 key of the router, since with WPS you can directly remove the WPA2-PSK key without any more problems. The program menu is quite practical and easy to understand.
WPS Pin is a program that runs through the console that will help us ha-ck wireless networks that have WPS activated. If we hit the WPS pin of our target network, we would already have connectivity to it, in addition, it would return the WPA / WPA2 key of the router, since with WPS you can directly remove the WPA2-PSK key without any more problems. The program menu is quite practical and easy to understand.
Basically, it has two methods to gain access to WPS networks. The first is to use algorithms to generate various PIN combinations . If the wireless network has WPS and the PIN has not been modified at any time, you can access that network.
On the other hand, ha-cking can be done using brute force . It will test all possible PIN combinations. Keep in mind that brute force attacks and attacks that have multiple PIN combinations (in WPS at most we will have about 11,000 combinations) will require a long time, and sometimes, resources of the virtual machine in a continuous way.
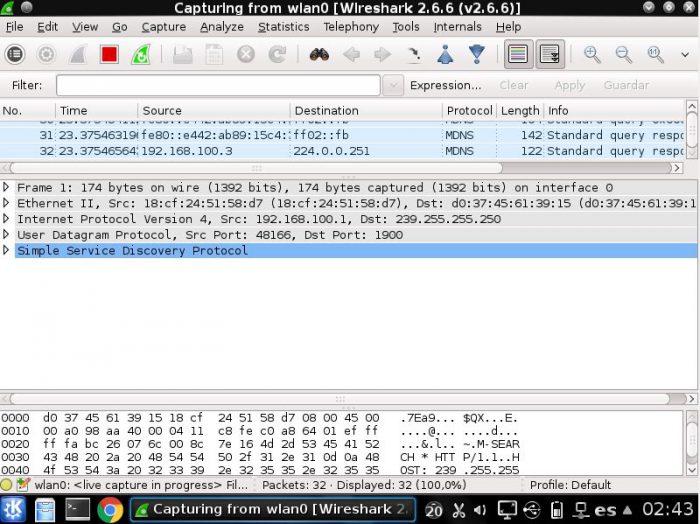
A popular tool that is present in this and several computer security suites is Wireshark . You will be able to capture all the data regarding the traffic generated by the wireless network interface that we have associated. You can take advantage of this tool in the same way that it can be done in other operating systems. Of course, if you have a wired network interface, Bluetooth and other connecting peripherals, you can capture traffic without major inconveniences.
You can customize your capture according to the protocols of which you want to know more information. Furthermore, it is a program that can be used in conjunction with others. So there will be no problem in using Wireshark along with other tools.
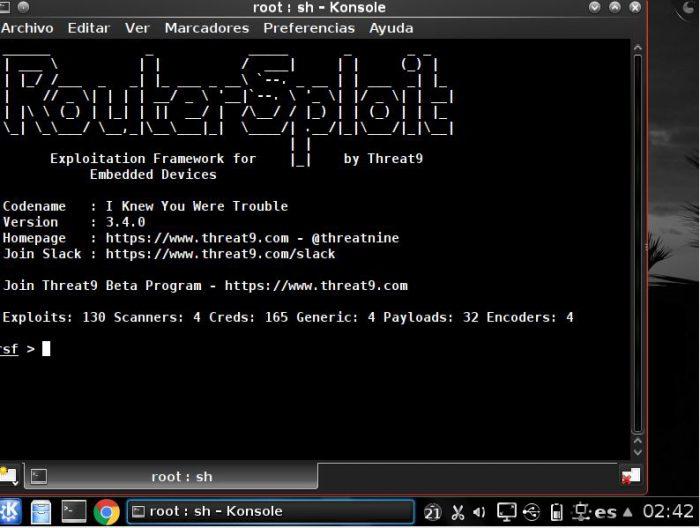
The RouterSploit tool that we have already presented in this article, is also found in WiFiSlax. RouterSploit is one of the most complete that will help us find vulnerabilities and attack routers. In addition, it is possible to do the same in conjunction with other networked devices.
The goal is to find those devices that have administrator credentials that are by default. Let’s remember that it is one of the main reasons why millions of routers are vulnerable. Just changing the administrator credentials to a truly secure password will make a difference. Today, tomorrow or maybe they will never attack your router. However, this should not be a valid excuse for not protecting our networked devices.
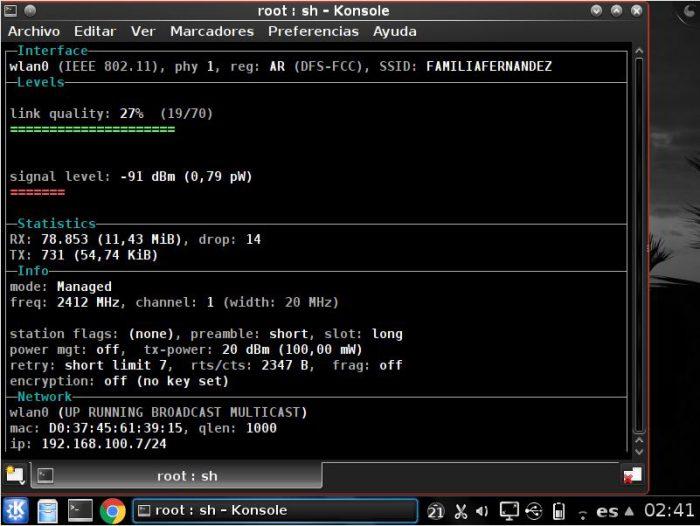
Another utility that we can find is one that will help us to know the signal level and the quality of our Wi-Fi network. It is updated in real time.
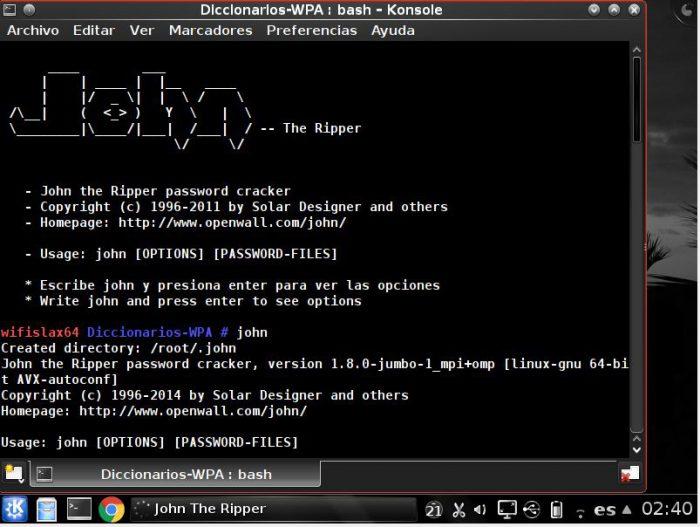
 John The Ripper is another tool that will help us crack passwords. It is one of the most popular and one of its most popular applications is in the professional environment. An IT or Computer Security manager can check with this tool how weak are the passwords used by all collaborators. From the information obtained, you will be able to make people aware of the importance of using strong passwords and also of storing them in a truly secure way. This is even more important if a good part or almost all of the workforce is working from home.
John The Ripper is another tool that will help us crack passwords. It is one of the most popular and one of its most popular applications is in the professional environment. An IT or Computer Security manager can check with this tool how weak are the passwords used by all collaborators. From the information obtained, you will be able to make people aware of the importance of using strong passwords and also of storing them in a truly secure way. This is even more important if a good part or almost all of the workforce is working from home.
At the time of starting to crack passwords, it is not necessary to indicate the encryption algorithm. John The Ripper detects it automatically. This is one of the most powerful solutions (with Hashcat’s permission), so even those most robust algorithms could be defeated. It does not hurt, remember that this is another possibility that the resources of the virtual machine are used to a great extent, especially if the encryption algorithms are complex. And there is something better, if you have encrypted passwords with more than one algorithm, they could also be cracked. Without a doubt, we are facing an extremely powerful solution.
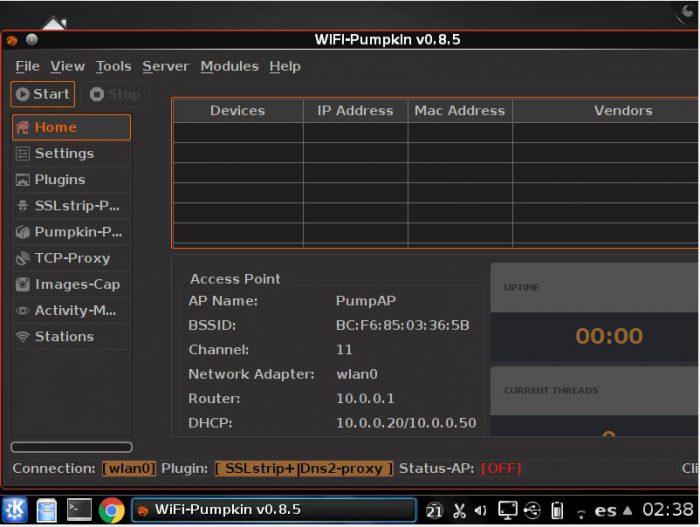
 WiFiPumpkin is a framework that will allow us to create rogue access points. That is, malicious access points with the ability to execute man-in-the-middle attacks . This framework was developed in the Python language and is constantly updated. By default, the version included in Wifislax is 0.8.5. However, it is possible to go to version 3. We recommend doing it since your official repository is the one corresponding to version 3. The one corresponding to previous versions is already “deprecated”.
WiFiPumpkin is a framework that will allow us to create rogue access points. That is, malicious access points with the ability to execute man-in-the-middle attacks . This framework was developed in the Python language and is constantly updated. By default, the version included in Wifislax is 0.8.5. However, it is possible to go to version 3. We recommend doing it since your official repository is the one corresponding to version 3. The one corresponding to previous versions is already “deprecated”.
Apart from attacks by malicious access points and man-in-the-middle, the following is possible:
- Modules for deauthentication attacks.
- Templates for extra-captiveflask (creation of malicious captive portals).
- DNS server rogue (malicious).
- Attacks using malicious captive portals.
- Web traffic: all web traffic logs will be intercepted, inspected, modified and reproduced.
- WiFi network scanning.
- DNS services monitoring.
- Collection of credentials.
- Transparent Proxy Servers and much more.
Although only some programs require it, it is necessary to follow the steps indicated above to ensure that we have wireless connectivity and not through the network cable. In this way, we will be able to execute the infinity of tests that we can carry out with Wifislax. We suggest making the most of it, especially if you are in a professional environment. Virtually at no cost and without too many requirements or prior knowledge, you can carry out a complete audit and even the first steps of pentesting WiFi networks.
We must not forget: any il-legal purpose for which solutions of this type are used will be subject to the legal conditions of each country. Always do it in an environment that you know, that is yours or that is under your administration.