A VPN network, as we know it, occurs thanks to the creation of a tunnel through which all network traffic flows. One of the main benefits is that whoever browses said VPN will generate point-to-point encrypted traffic, from the VPN client to the VPN server, therefore, your information will be protected within this VPN tunnel. Information outside the VPN tunnel prevents information from being read by other people. However, is it really necessary for any type of traffic to go through the VPN? Not always. For this reason, we will talk about one of the alternatives that could optimize its effectiveness: the divided tunnel , or also known as split tunneling.
It is good to remember that a VPN has multiple applications. Some of them are: access to Internet resources that are restricted by region, private browsing and why not, to be more secure when going to the Internet. But, a VPN has an important detail. The connection quality (speed and latency) tends to decrease, mainly due to the encryption algorithms that are implemented. Consequently, the user perceives a slower access than when he is outside a VPN. And this is part of the nature of virtual private networks, especially the VPN clients that we can install on users’ computers. By default, such clients have complete control of all traffic.

What is the divided tunnel?
It is a feature of virtual private networks (VPNs) that allows you to configure the specific type of traffic that you want to flow through the tunnel. A classic example is that all traffic that comes directly from an organization’s internal network passes through the VPN, but not Internet traffic in general that is under the control of the ISP. Also, it is possible to adjust the VPN needs according to the type of application or resource that is being used. For example, those that handle very sensitive information, that go through the VPN, the rest, that go to the Internet normally.
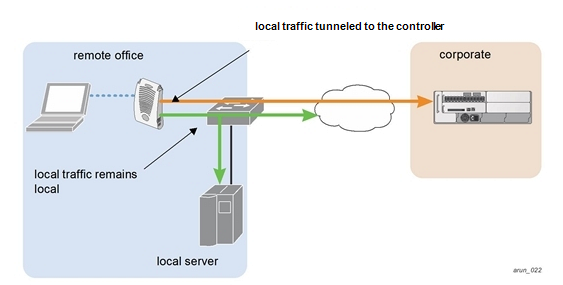
Another way to take advantage of the split tunnel is to have the services linked to the VPN used to block certain traffic. A recurring example is not allowing access to a certain website, and blocking is done using its IP address. Also, there are other services that allow users to disable their VPN connectivity to access certain applications or resources.
It is possible to do that, by means of this VPN feature, the creation of what is called “interesting traffic” is achieved. The latter has to do with all kinds of traffic that we want to monitor and / or protect. Why would one need to make these distinctions? It may be for security reasons or simply to optimize your available network resources.
Divided Tunnel Types
- Reverse Divided Tunnel: performs a process of reversing the tunnel’s own standard, allowing all generated traffic to pass through the default VPN tunnel. Users can use this method to choose what kind of traffic is outside this tunnel.
- IP-based routing : Remember that routing allows data packets to travel directly to the destination, of course, according to the IP address of that destination. However, it is possible to use routing-based policies to implement a kind of split tunnel. These policies apply changes to the routing table, all based on considerations such as the size of the data packet.
Is it really safer?
So far, we have explained that the divided tunnel has benefits, especially when it comes to facilitating the management of the network traffic that we administer. It is clear that in the long term there is nothing worse than looking at Internet traffic through a VPN tunnel. The latter not only generates inconveniences at the level of network administration, but also at the user level that repeatedly perceives problems in connecting, such as slowness when accessing certain resources.
However, so far there is no evidence that VPN management through split tunnel is the safest. Above all, if we talk about a scenario that consists of company workers who must start doing their activities from home. Let’s add the fact that they have to use their own computers. In this case, what happens if the person’s computer is infected by malware or any other type of virus? In the event that you are going to connect remotely via VPN, even if you have a divided tunnel, there is a risk that this infected computer will “infect” the network. What happens next, we already know.
What to do when opting for this VPN variant
The first thing to consider is what security-focused features each VPN service offers. To keep in mind, there are VPNs based on software and those that are included in firewalls. Above all, if you opt for firewall-based VPN, ask the provider what are the options available regarding VPN traffic control.
On the other hand, there are solutions that limit access to the VPN taking into account considerations such as: the version of the computer’s operating system, the version of the antivirus and its virus databases, in addition to other aspects that can be defined by whoever requires it. of the VPN solution.
In this article we always promote the use of free and open source software, especially when you have limitations in terms of resources, but also, all the knowledge necessary to implement solutions like PacketFence . It is a platform that is aimed at reviewing devices prior to connecting them to the VPN. This is extremely useful when working for an organization that allows employees to use their own devices. Remember that this practice is known as BYOD (Bring your own device) .
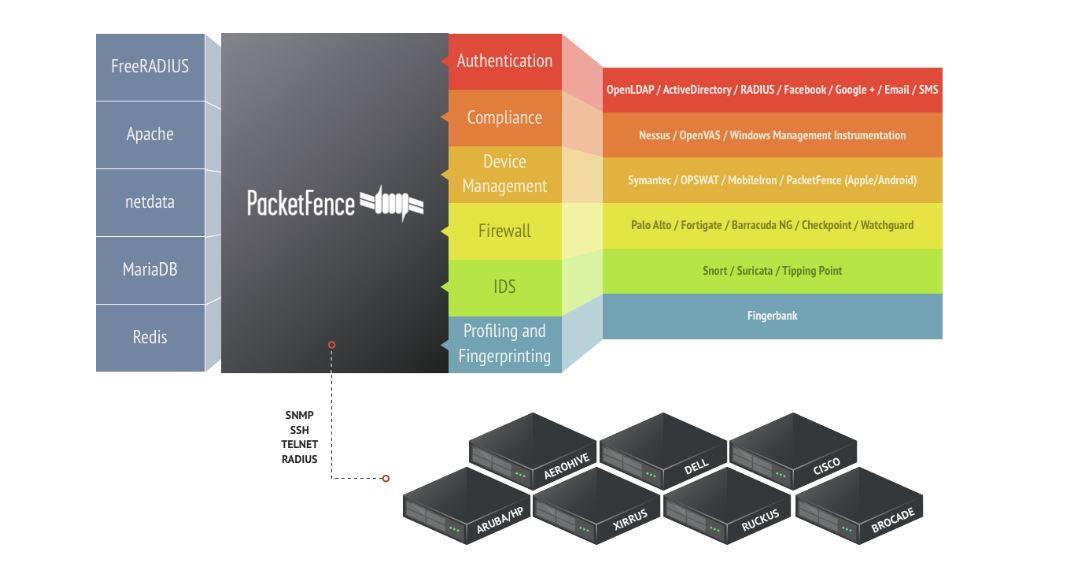
PacketFence is presented as a Network Access Control (NAC) solution. It has various features such as the availability of a captive portal for the users involved to register and authenticate. Also, it has centralized management of both wired and wireless connections. Something worth noting is the fact that you can integrate IDS / IPS solutions like Snort, which is mentioned in our IDS / IPS solutions guide. Even if you have vulnerability scanners like Nessus, PacketFence is fully compatible. Consequently, you can create a complete network security suite without requiring high financial investments. Above, we see an outline of all the possibilities that this solution has to control our networks in any aspect, from authentication to user profiling .
If you want to try it, you can access its official website where you can find two download options:
- Source Code : If you have experience coding, you will feel quite comfortable with this option. You will also find packages for some Linux distributions.
- ZEN (Zero Effort NAC) : in Spanish we can say that it is an effortless version of NAC. In other words, the download consists of a file already pre-configured to implement Packet Fance as soon as possible. In turn, it has two variants:
- Virtual Appliance
- Live PacketFence System (a portable version that can fit on any storage device like a USB one).
If I only have one mobile, can I use the VPN split tunnel?
Of course yes, if you configure the VPN client with protocols such as IPsec, OpenVPN or Wireguard, you can have a divided tunnel without any problem. Furthermore, commercial VPN applications like PureVPN , NordVPN or Surfshark also support this configuration option.
These commercial services allow you to perform split tunneling easily and quickly, in most of them, you will see a screen where you will see a power button which serves to connect and disconnect from the VPN with a single touch. You should bear in mind that its Smart Location feature chooses the country that offers the best quality of connectivity. According to the region where the test has been done. However, you can choose between several countries including Asia, Europe, Africa and the entire continent of America.
In the advanced configuration options of the different applications you can activate split tunneling, and choose from several options. For example, in the case of Express VPN we have the following:
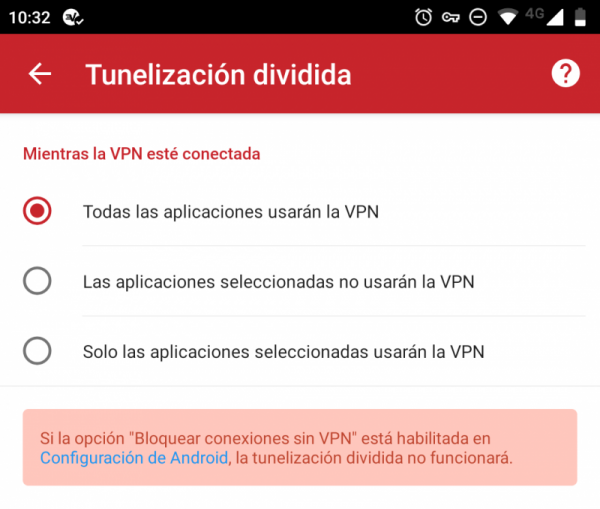
The first is the default VPN functionality, which will affect all the traffic you generate on the Internet. The second and third are the options corresponding to the divided tunnel and the reverse divided tunnel, respectively. Generally, it is easier to determine which applications will not use the VPN , so you waste less time with these settings.