One of the services that is already available for mobile phones for a long time is NFC . Its most popular application is the field of mobile payments. Many businesses around the world have NFC reader dataphones, both for contactless debit / credit cards, or for mobile payments with NFC. As easy as swiping the card or mobile phone through the reader, and voila! Payment made. However, as well as practically everything in the technological field, it has certain risks and it is important that we know them in order to protect our data.
Before we begin, let’s learn a little more about this technology. The abbreviations NFC correspond to Near-Field Communication . Virtually every smartphone, to date, is compatible. As we have mentioned at the beginning, it is better known because of the payments that can be made through services such as Google Pay or Apple Pay . Although it is also possible to connect devices wirelessly such as headphones, and easily link them via Bluetooth.

How NFC Technology Works
In the event that you need to share files with another person, NFC is the way to interconnect devices via Wi-Fi, since Wi-Fi technology is much faster than NFC. NFC technology is used, in this case, to configure both devices so that they “see” each other. As we see, it works similarly to Bluetooth , however, NFC works based on a distance of a few centimeters, so it is necessary that the devices involved in a file transfer or a payment, are quite close.
Unfortunately, this technology, which is relatively popular in the mobile world, has certain vulnerabilities. NFC was conceived as a utility to get more out of mobiles to make payments, for example. Another aspect that we must consider is that it is a wireless technology, so the risk of cyber attack events is higher compared to a technology that is based on a cable.
The fatal flaw of this technology is that there is no authentication when establishing the connection between compatible devices. They only need to be in the same range (visible) for the connection to be established, and the information can be read or interact. The worst part is that a data transfer or any NFC-enabled activity can be done without one of the parties realizing it. However, on mobile devices, to use NFC it is necessary to unlock the terminal, otherwise, we cannot pay with our mobile, for example, nor “associate” with other devices, it will always notify us that there is an incoming connection and that to continue it is necessary to unlock the terminal.
How to take advantage of this technology more safely
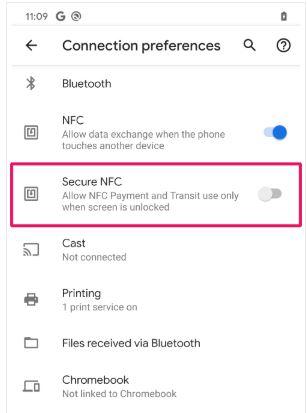
The years have turned in favor of the NFC in the sense that significant progress has been made to make its daily use safer. The latest version of Android, Android 10 , allows compatible smartphones to enable the use of Secure NFC . This consists in that the chip will only be activated in the event that the smartphone screen is unlocked. Only your device will be visible with others that have it active, in the event that you are going to make a payment or a data transfer to later exchange files via Wi-Fi or Bluetooth.
What you should do is go to Settings> Connection Preferences> Enable the third option Secure NFC in addition to the second one that is the activation of the NFC in question
When making payments, it is essential that you use NFC applications with strong security measures. Apple Pay is one of them and is characterized by the “tokenization” of transactions to ensure privacy and security. What does it consist of? In a token, which is like an identity card for each transaction. The operating scheme is complex, however, it is possible to summarize its operation in a few steps:
- Your credit card details are encrypted and go to Apple’s servers.
- The servers decrypt it and re-encrypt it to pass the information to the payment processor.
- The processor decrypts it and generates a unique account number for the transaction.
- This number goes to Apple’s servers and, always being encrypted, it is stored in a secure space in the memory of your iPhone or MacBook.
The unique account number to which we refer is as a mask for the real data of the different cards that we can have stored in Apple Pay. Which means that Apple’s servers do not have direct access to your payment details, making transactions very secure.
We had also mentioned Google Pay as an application for NFC payments. Also, it is one of the safest we can find. In addition, it uses “tokenization” in a similar way to Apple’s, just as Samsung Pay does with its virtual card numbers.
However, one of the differences is the implementation of a system called Host Card Emulation . It implies that the unique encrypted account number is stored on a cloud server, instead of using the memory of your smartphone. That the data is stored in the cloud, allows Android to use more resources to protect the data through strong encryption algorithms, among other security measures.
Protect your device from NFC attacks
There is no way to prevent different communication technologies from suffering from vulnerabilities. Fortunately, the advances that occur year after year favor technologies such as NFC to be able to use them with ease and confidence. However, it never hurts to take additional measures, especially if you use your NFC smartphone frequently. There are two approaches to protect you from attacks that are carried out using this technology. The first is a more drastic measure: do not use NFC at all, you must disconnect the NFC from your smartphone and that’s it, if you do not use it, it is best to have it disabled.
However, if you are used to making payments using this technology, there are a number of measures that you can apply to make your NFC experience safer and avoid a headache:
- Enable the option on your mobile to use the NFC only with the screen unlocked, this will minimize any possible attack that occurs while we have the smartphone in our pocket.
- In times of day when you don’t need it, you can disable NFC. That is, only activate it when necessary and in places of trust. As examples, we can mention the restaurants, bars and shops that you usually visit. Normally in Android we have a shortcut to activate or deactivate it, along with the icon of Bluetooth, Wi-Fi etc.
Another thing you should do frequently, and not only in the face of possible NFC hacks, is to scan your mobile for malware or any other type of virus that compromises the integrity of your mobile. We know it, it is almost impossible to be 100% protected from cybercriminals. However, adopting a good security awareness, it is possible to have a day to day with our personal data duly protected and at our disposal whenever we need it.