New technologies are opening little by little, and are replacing to a certain extent the way we do things. One of them is VoIP which is changing to some extent the way we make voice calls. Cybercriminals are aware of it, and have exploited unpatched VoIP vulnerabilities to profit from it. Today in this article we are going to explain how they are doing it, and safety recommendations to avoid it.
In a campaign that has targeted more than 1,200 companies, they have used exploits to remotely gain access to VoIP accounts. These cybercriminals, to get money from their work, are selling access to the highest bidder.

The purpose of using unpatched VoIP vulnerabilities
In case you don’t know, VoIP or voice over Internet protocol is a set of resources that make it possible for the voice signal to travel through the Internet using the IP protocol. The voice signal is sent digitally using data packets, instead of analogically through the circuits used by conventional telephony. The point is, by exploiting unpatched VoIP vulnerabilities, these cybercriminals are looking for the best way to exploit these security breaches.
The most common main purposes are usually:
- Dialing attackers-owned premium rate numbers.
- Sell phone numbers and calling plans that others can use for free.
But there is still more, that access they get to VoIP systems, can provide cybercriminals to spy on our private calls and even take more intrusive actions.
Check Point’s report regarding VoIP
In a report by Check Point’s cybersecurity specialists, it was revealed that a hacking group has compromised the VoIP networks of nearly 1,200 organizations in more than 20 countries. In this sense, the United Kingdom, with more than half of the victims, has been the most affected country. The government, the military, the insurance and finance sectors, as well as manufacturers are estimated to have been targeted.
A systematic pattern of exploitation of SIP servers from different manufacturers was also found. Hacking SIP servers to gain their control is their main goal . One of the most interesting ways is to exploit these servers by using them to make outgoing phone calls that they can use to generate profits. As making calls is a legitimate and common function, it is difficult to detect when a server has been exploited.
To achieve this goal, attackers use unpatched VoIP vulnerabilities. In this case, it is a critical vulnerability, CVE-2019-19006, which affects the Sangoma and Asterisk VoIP telephone systems. Thanks to it, it allows a cybercriminal to gain access remotely without the need for any type of authentication. This is the flow of the Inj3ct0r attack that they use:
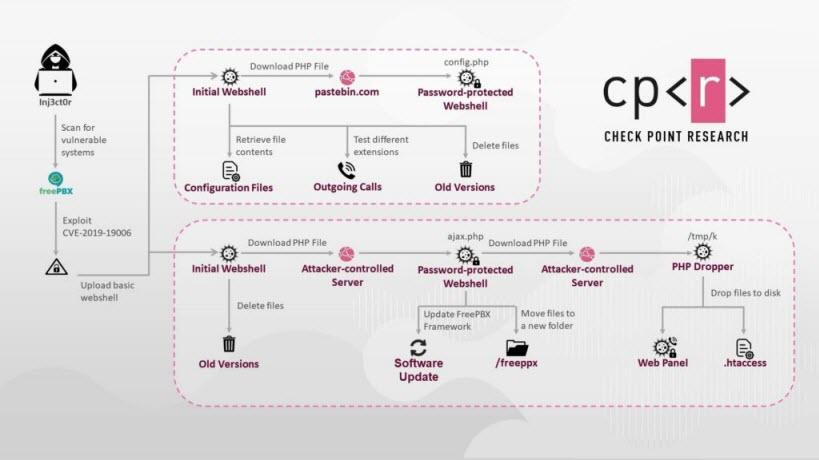
The patch that solves it has been available for a long time, what happens is that many organizations remain without applying it.
How can we detect it and what can we do?
This is a significant danger since we are facing a vulnerability that has an authentication failure, and, in addition, the exploit is publicly available so that anyone can use it. Once exploited, cybercriminals have administrator access to the VoIP system so they can control its functions. It should also be noted that this will not be detected, unless an IT team specifically searches for it.
One of the most common means for hacked systems to be exploited is to make outgoing calls. The problem is that, because companies make so many phone calls from their employees, it is difficult to detect if a server is being exploited. Therefore, we must advise companies to change the default user names and passwords on the devices. Also, if possible, it would be wise to analyze call billing on a regular basis for potentially suspicious calls.
Finally, we must avoid unpatched VoIP vulnerabilities, it is the most important thing to ensure our security. With a system with the latest patches we are less vulnerable.