DNS services are essential for browsing the web. However, it is one of the most vulnerable to attack. This guide will detail you regarding the most dangerous DNS attacks and some actions that will allow the network infrastructure to be protected.

One of the reasons why DNS services have a certain susceptibility to attacks is the UDP transport layer protocol. Let’s remember that it is a conectionless transmission protocol . The latter means that it is not connection oriented, the UDP protocol does not care that the data reaches its destination completely, it will also continue to transmit everything that is queued. Let’s say that the data packets are on their own, they may reach their destination successfully or they may suffer from some inconvenience in the middle. Let’s look at the following scheme for a better understanding:
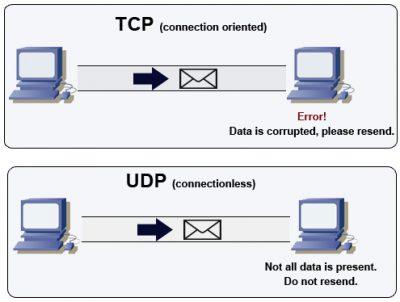
- The first half of the image shows us how another popular protocol works which is connection oriented: TCP . It does not accept corrupted or integrity data packages. Yes or yes they must be sent again so that it reaches its destination 100%.
- The other half refers to UDP . As we mentioned, it is not connection oriented. The destination will receive the data packets regardless of whether they are in trouble or not.
Think of streaming services. They, at certain times, stop and then resume the transmission. Either the image comes out somewhat pixelated or you hear the famous “robotic voice” of the speaker. Even though all of that can happen, the transmission doesn’t stop on its own. Of course, there are exceptions such as no Internet connectivity or that the person runs out of battery or power.
We recommend reading our tutorial on TCP vs UDP, characteristics and uses of the two transport layer protocols.
The most powerful DNS attacks
Botnet-based DNS attacks
Keep in mind that with a small botnet, there are multiple possibilities for attacks. Not to mention if you have more than one and in turn, each of them has thousands of zombie computers. Basically, the attack based on these networks of connected and infected computers consists of running DDoS.
A single botnet would be large enough to render a regular DNS server useless. Simply, each zombie must be “programmed” to send multiple access requests to a web resource recognized by that DNS server. Then, said server will be saturated by so many requests, it cannot answer them and therefore, it stops operating.
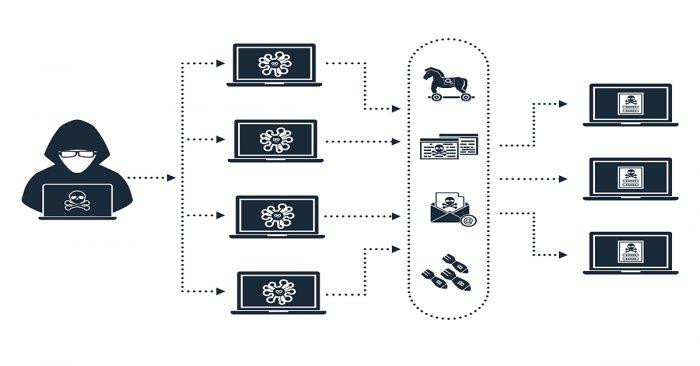
In this article, we have an extremely interesting list of threat maps and cyber attacks . In that article you can see some of them illustrate the behavior of botnets when executing an attack. Botnet-based attacks can be prevented by applying a few actions that, in the long term, will prevent one or more eventualities:
- Check if your networked devices have vulnerabilities.
- Do you have IoT devices in your network? Review the security settings as soon as possible.
- Are there DNS attack threats? IDS / IPS security solutions are essential to identify them and act accordingly.
DNS Flood attacks
The purpose of this attack is to get the capacity of the DNS server to the limit. To the point where you can no longer receive any requests. Let’s see a small scheme below:
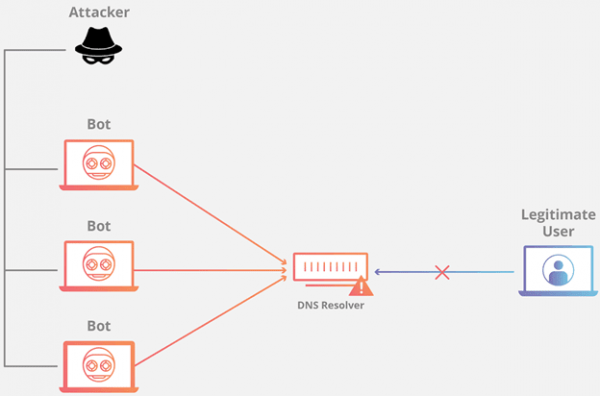
A cybercriminal can infect one or more computers on a network by creating a network of zombies. As you can see, this is one of the attacks that can be executed through a botnet. All infected computers start sending multiple DNS requests to match domain names and IP addresses.
It reaches an instance where there are so many requests and it stops being operational. Consequently, any legitimate user who makes a DNS request and goes through the affected server, simply cannot obtain the expected result: accessing a web resource. This is one of the circumstances by which a user would not have access to one or more pages on the Internet.
As a web server administrator, a good protective shield could be the implementation of Content Delivery Network or CDN solutions. They not only take care of speeding up the loading of web pages but also protect them from potential threats. Some of them can be DNS requests from bots, botnet zombies or any user who has intentions of executing DNS Flood attacks, for example.
Poisoning cache
This attack is one of the most effective ways for users to be victims of phishing attacks . Well, the users, knowing that they are entering a legitimate website, are actually accessing one that has the task of collecting all your data. Especially access credentials and bank details.
Suppose you want to enter your bank’s website and, without paying too much attention, you see that you have effectively accessed the official page. Apparently everything looks the same and there is nothing to worry about. However, you enter your access data and at a certain moment, you realize that something is wrong.
But what is caching in DNS ? It is a process in which a DNS server resolves . Its function is to store the responses of DNS requests for a certain time. This is to respond to all DNS requests much more quickly, without going through the entire domain name resolution process.
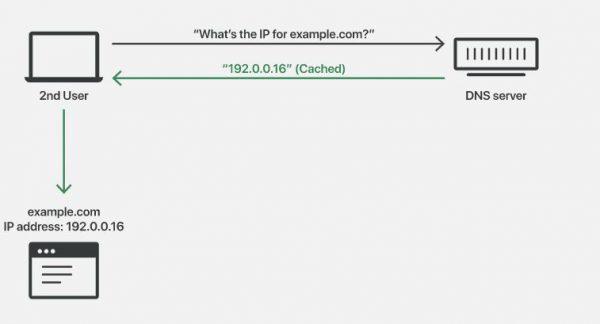
Unfortunately, a cybercriminal can gain control of the DNS by resolving and altering the responses to all the stored DNS requests. For example, if the site www.example.com was originally associated with IP 192.0.0.16, the cybercriminal can alter this response by associating the domain with a malicious IP: 192.0.0.17. Let’s see below an outline that illustrates what we have mentioned:
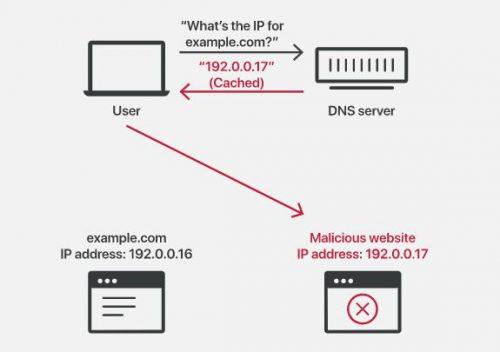
Inadvertently, the user accesses a malicious site despite having entered a legitimate domain. As a web services administrator, you should implement the following:
- Restrict recursive queries (requests).
- Store DNS records only associated with domain names.
- Limit DNS request responses to information truly associated with the domain.
DrDoS (Reflexive Distributed Denial of Service Attack)
This is other evidence that DDoS attacks can reach large scales. The servers that act as reflectors in this variant of DDoS could belong to different networks. The advantage to the attacker is that it becomes very difficult to trace back the attack scheme.
Consequently, multiple networks can participate in a DrDoS attack . If I have three reflector servers that belong to three different networks, the cybercriminal could take control of those three networks so that all the connected devices participate in the attack.
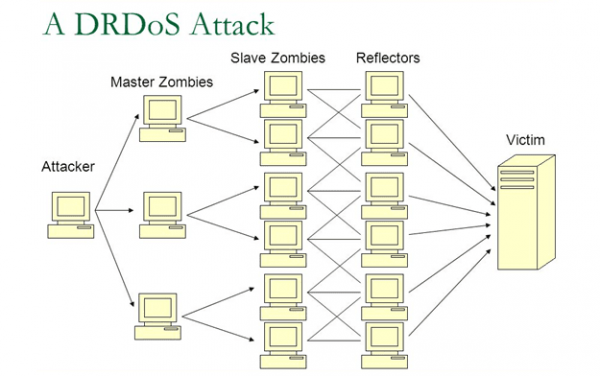
Let’s move this to the DNS context. If there are multiple devices connected from several networks and in turn, all these networks have reflective servers, the latter will not be affected by the large number of DNS requests that pass through them. Precisely, this feature of reflectors makes them directly redirect that large number of requests to the victim DNS server.
The affected server will receive so many illegitimate requests, along with legitimate ones. As its capacity has reached its limit, it will begin to discard packages including those that correspond to legitimate requests. Therefore, stop responding.
What to do to prevent an attack on such a large scale? All the preventive measures suggested so far apply. However, if the network infrastructure you manage is large, it is worth considering the following:
- Multiple servers must be located in more than one data center.
- Data centers must belong to different network segments.
- Ensure that data centers have multiple routes.
- Have little or almost no amount of security holes.
Impact of DNS attacks
DNS attacks do great harm to the various organizations that are victims of them. The sums of money that are the result of losses easily reach millions of dollars. Most worryingly, DNS attacks tend to be increasingly sophisticated and specific in relation to modus operandi .
Insider threats are the order of the day. Organizations, while appearing to be less susceptible to DNS attacks, must protect their infrastructure from insiders using Threat Intelligence tools that are fortunately broad in offering. On the other hand, the security tools for managing web services also have many options.
DNS attacks, although they have been carried out for many years, do not stop growing in terms of the number of events that occur each year. Although your organization is likely never to be the victim of any of the aforementioned attacks, protecting network infrastructure is not an option.