Hackers surprise us every time when it comes to looking for new techniques to infect our mobiles and get our money, data or whatever interests them. The new way to do this, and it’s more dangerous than you can imagine, is to spread malware via PNG images.
In principle they have reached other countries, especially in Southeast Asia, the Middle East and South Africa, which have been discovered, but they could go much further and this time their objective is to attack with malware to steal information . Now you are going to have to be more careful with the images you download, although in this case all caution is not enough.

How do they manage to infect you with these images?
Workok hackers are spreading malware via PNG images using the steganography method, which in case you didn’t know, involves hiding a message inside or on top of something that isn’t secret. With it, malware can be camouflaged, as is the case, in such everyday elements and in which it is easy to be deceived, such as in photos.
Malware hiding in a PNG file could steal data from your device without your knowledge, according to reports from Avast and ESET researchers who have confirmed that Worok hackers are doing it. High-profile victims are most at risk, though that doesn’t mean anyone is safe.
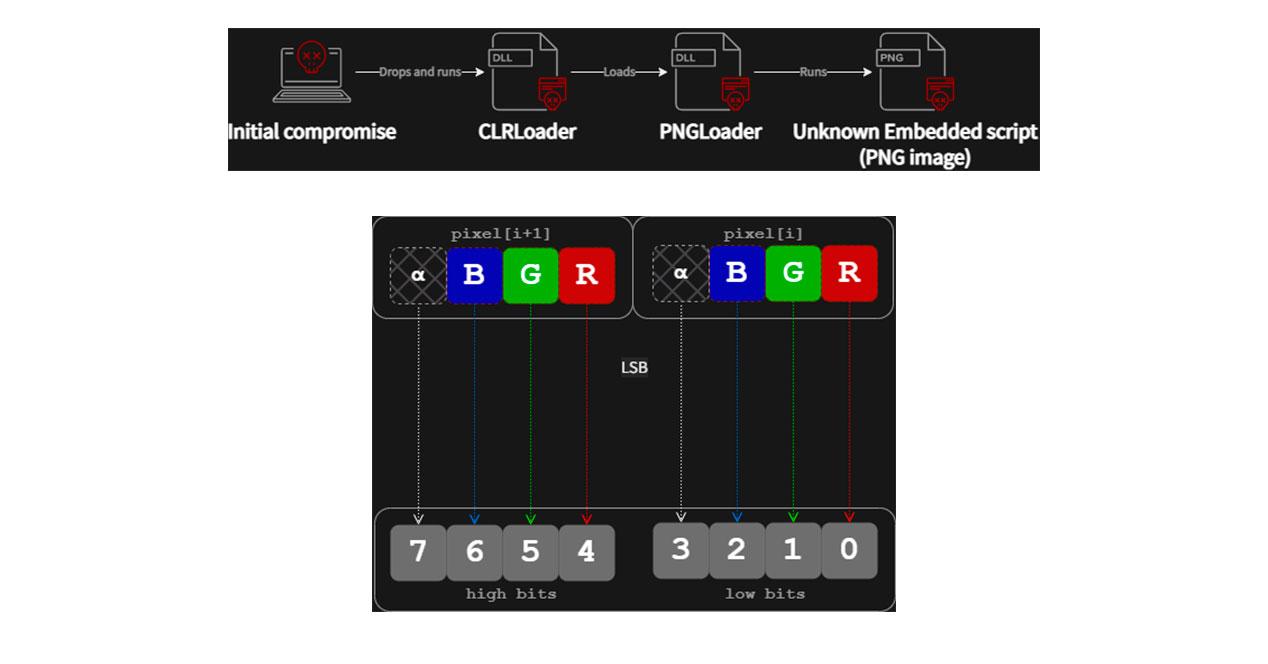
The malware hides in PNG files, probably using DLL sideloading to run the CLRLoader malware loader in memory, although the method they are using to breach networks is not known. CLRLoader should load a second stage DLL which is PNGLoader. This extracts bytes embedded in PNG files to assemble executables.
The second payload would be abusing the DropBox cloud hosting service to do communication with the C2 and other actions. The DropBoxControl malware can receive data and commands or upload files from your device via an actor-controlled DropBox account.
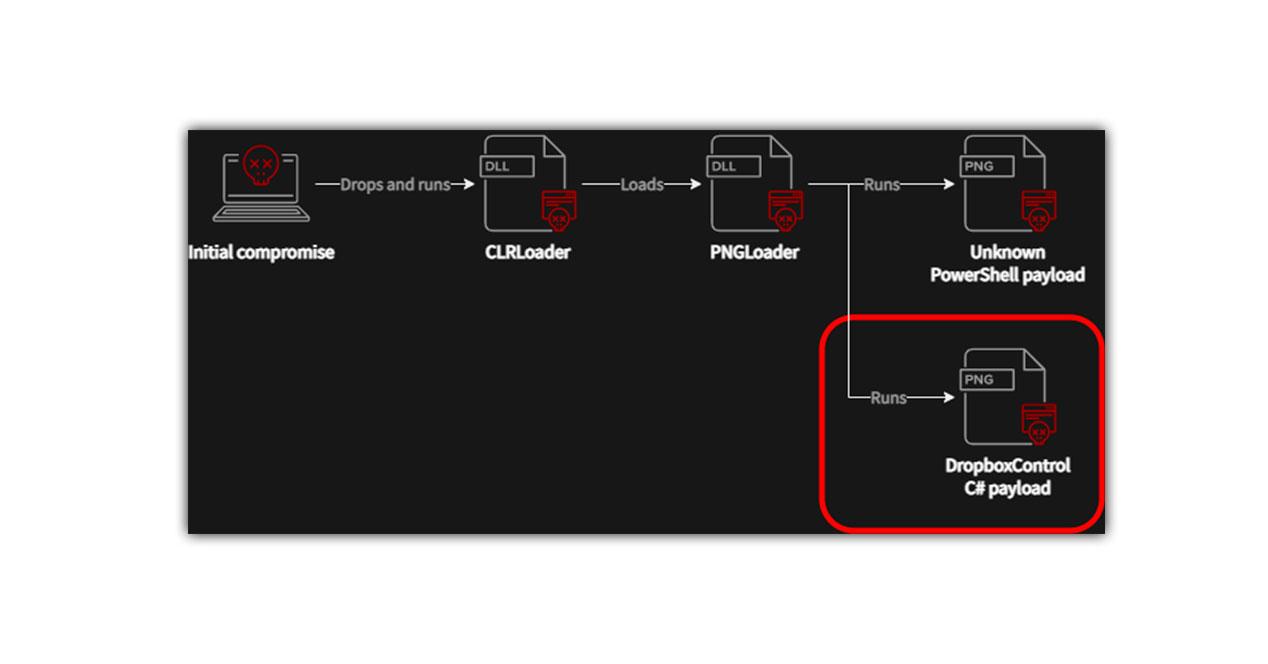
Because these commands are stored in encrypted files in the actor’s DropBox repository, they can be accessed periodically by malware. If you are attacked, you will not know anything or receive a warning of any kind.
In image viewers everything is apparently normal , in fact, images can be opened without problems, although what really happens is that they are stealing data from your device such as those in documents and files of your interest and you would not even know it. Even if you had been infected.
What can you do to avoid getting infected?
At the moment, the DropBoxControl malware initially has a low scope , although this may only be the beginning of what awaits us in the near future. Cybercriminals are constantly working to find new ways to reach their victims and take every opportunity to do so.
The best thing you can do is be careful with the files you download from the Internet, especially from unknown sources or messages that are sent to you without your request, and have a good antivirus that you constantly update. Update your mobile and the installed programs and if you see something suspicious, make the appropriate checks.