 TCP and UDP are two fundamental protocols for communications over the Internet, since these two protocols are located in the transport layer of the TCP / IP model , and it is the first layer where origin and destination communicate directly, since the layers Lower (network layer and middle access layer) do not perform this function. Today we will explain the main characteristics of the TCP protocol and the UDP protocol , when each one is used, differences and main uses.
TCP and UDP are two fundamental protocols for communications over the Internet, since these two protocols are located in the transport layer of the TCP / IP model , and it is the first layer where origin and destination communicate directly, since the layers Lower (network layer and middle access layer) do not perform this function. Today we will explain the main characteristics of the TCP protocol and the UDP protocol , when each one is used, differences and main uses.
TCP protocol: what is it and how does it work?
The TCP (Transmission Control Protocol) protocol is one of the fundamental protocols on the Internet, it allows applications to communicate with guarantees regardless of the lower layers of the TCP / IP model. This means that the routers (network layer in the TCP / IP model) only have to send the segments (unit of measure in TCP), without worrying whether or not that data will arrive correctly. TCP supports multiple application layer protocols , such as HTTP (web), HTTPS (secure web), POP3 (incoming mail) and SMTP (outgoing mail) as well as their secure versions using TLS. TCP is also used in such important protocols as FTP, FTPES and SFTP to transfer files from a source to a destination, and even the SSH protocol to manage computers locally and remotely securely uses the TCP protocol.
Main features
Because TCP serves a large number of application layer protocols, it is essential that the data (segments) reach the recipient correctly , without errors, and, in order. If in the transmission of the segments, they get corrupted or lost, automatically the TCP protocol starts retransmission , without intervention of the application layer. In this way, it is guaranteed that the data reaches the recipient without errors, since this protocol is responsible for solving any type of problem.
The MSS (Maximum Segment Size) is the maximum size in bytes that TCP can receive in a single segment, it is similar to the MTU, but the MSS is at the transport layer level. In order to get the best performance, the MSS must be small enough to avoid IP fragmentation. The MSS is normally advertised on each side of the communication channel, through the TCP header itself. Normally the size of the MSS is the MTU (1500 bytes normally) minus the TCP header (which has a variable length of at least 20 bytes) minus the IP header (which has a variable length of at least 20 bytes). MSS = MTU (1,500 bytes) – 20 bytes TCP header – 20 bytes IP header
TCP has a complex error control mechanism , a sliding window technique is used so that all segments arrive correctly. This feature uses different methods to detect possible errors that occur:
- Checksum
- Numbering of all segments to properly control
- Selective ACK confirmations, although it also allows you to “accumulate” segments so that with a single ACK you can confirm several.
- Timers: if a lot of time passes, TCP automatically retransmits the segment that has been “lost.”
- Duplicate segments are discarded: in case a duplicate segment arrives (because one has taken longer than normal and has been resubmitted) it deletes it.
Of course, if TCP detects an error, it will start retransmission automatically without the application layer having to do anything at all.
Another very important characteristic of the information that travels from an origin to a destination, is that the data arrive in order , that is, in the same order they were issued, since the IP protocol is a best-effort protocol, it does everything It may be so that the packages arrive in order and correct, but it is not reliable since it does not guarantee anything. TCP has a sliding window on the sender and the receiver, so that, if we receive a segment that is not in order, it will automatically “wait” until the missing segment arrives, or else, will request a retransmission only of the segment missing. With each segment received by the receiver, an ACK will be sent indicating to the sender that everything is arriving correctly, however, in real life TCP implementations allow an ACK to be sent to confirm the reception of several segments simultaneously, with the objective of not saturating the network with so many confirmations.
The TCP protocol allows flow control , that is, it is able to mitigate the possible saturation of the network or the remote host. In the event that a device is transmitting at a speed of 500Mbps, and the destination device can only receive information at 100Mbps, the TCP protocol is dynamically adapted. In this way, the TCP protocol will always try to maximize the available bandwidth between source and destination. The operation of this sliding window is complex, but it basically works in that the receiver has an available TCP window with a number of bytes that can be stored in a buffer, the sender can send data until this quantity is filled. In order for the sender to send more data, it is necessary for the receiver to send an ACK indicating that everything is correct and that it proceeds to “upload” it to the application layer.
TCP also has congestion control , this allows us not to lose packets on the Internet because there is congestion on the routers. If the router is not able to process or forward packets at the rate it receives them, the router itself will discard them and it will be lost, since its buffer will be filled. We should not confuse flow control (which we have explained above) with congestion control. The congestion window (is complementary to the reception window) is what is used to manage congestion control in TCP. In a non-congestion situation, the congestion advantage is the same as the reception window, if congestion occurs, the size of the congestion advantage is reduced, and if it disappears, it increases. The maximum number of bytes that the sender can send is the minimum of both window sizes (if the congestion window is 1500 bytes, and the reception window is 2000 bytes, then 1500 bytes are sent, the smallest).
In order to avoid congestion, and that we can squeeze the maximum available bandwidth between origin and destination, there are a total of three phases. The slow start phase (slow start) is responsible for growing exponentially (so it can not really be considered slow start) the congestion window, then the congestion avoidance phase that is responsible for growing the congestion window linearly, and, finally, the constant phase where the reception window is the same as the congestion window.
TCP currently has different algorithms to efficiently manage congestion, the first were TCP Tahoe and Reno, although we also have others such as TCP Vegas, but, over the years, with the new TCP / IP data networks, they have other algorithms appeared that are more efficient. For example, we have TCP BRR that allows us to send information as quickly as possible, since it is much more efficient than the original TCP protocol (we will have greater speed). We also have TCP Cubic which is the congestion control used by the Linux and Unix operating systems.
Finally, another interesting feature of TCP is that it allows us to multiplex data , so that we can receive information from different hosts simultaneously. It also allows Full-Duplex, as we can send and receive data simultaneously through the same communication channel.
Establishment of the connection between client and server, and disconnection in TCP
The main characteristic of the TCP protocol is that it is a connection-oriented protocol , in order to establish a connection between client and server, it is absolutely necessary to establish a previous connection with said server.
This previous connection is called 3-way handshake , and it basically consists of the client (the one who initiates the connection) sending a SYN message to the server (the one receiving the connection). Subsequently, the server will send a SYN-ACK type message, indicating that it can start sending information, finally, the client sends an ACK indicating that it has received it correctly, and all the information between client and server is already being sent. bidirectional way. A very important detail of TCP is that, it generates sequence numbers on each side, helping that false connections between them cannot be established, although if the attacker is “in the middle”, then an ARM-type MitM attack could be made Spoofing or similar, but not over the Internet.
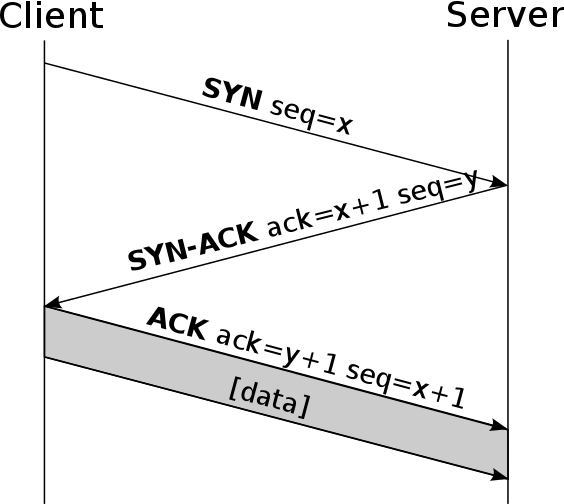
One of the vulnerabilities of TCP lies in the sending of a large number of TCP SYN segments, with the aim of “saturating” connections to the receiver. Some possible solutions to mitigate this denial of service attack are:
- Limit the number of connections, either global or IP connections.
- Accept only connections to trusted IP addresses.
- Delay the allocation of resources using “cookies”, or also called SYN Cookies.
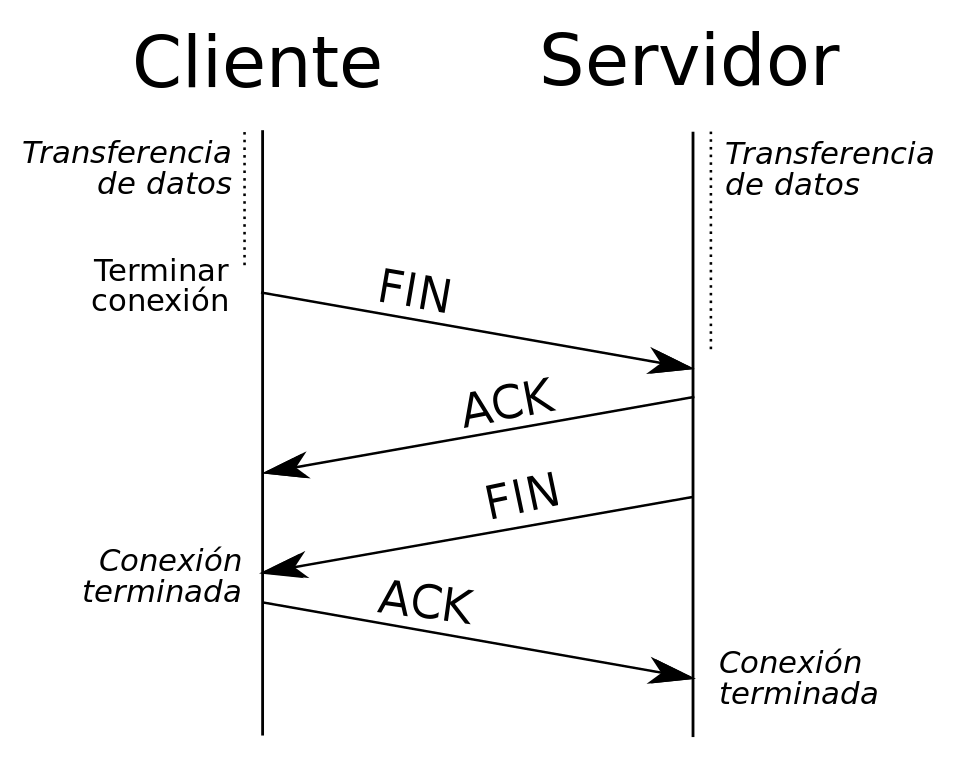
To terminate the connection , the one who wants to terminate the connection sends a FIN message, and the host that receives it will send an ACK message along with another FIN message, so that the team that initiated the connection termination sends it one last ACK and the open socket will close. An important detail is that we can have a “half-open” connection, if one host terminates the connection and the other does not, the side that has terminated the connection will not be able to send more data, but the one that has not closed it can continue sending information .
TCP header
TCP adds at least 20 bytes of header in each segment, since we have an “optional” field. In this TCP header we will find the source port and destination port of the connection (socket), we will also find the sequence number, ACK number, and the different TCP FLAGS such as SYN, ACK, RST, FIN, URG and others. In this header we also have a very important part for the operation of the sliding window, and we will have a 16-bit field that indicates the size of the reception window that we have explained before.
The ports (Source Port and Destination Port) are essential for the proper functioning of TCP. TCP uses these port numbers to identify a socket, that is, an application that emits data or receives data. TCP ports range from 0 to 65535, but we have three different types of ports:
- Known ports : from 0 to 1023. These ports are reserved by IANA for certain applications, such as HTTP server, FTP, SSH, and many other well-known ports.
- Registered ports : 1024 to 49151. These ports are reserved for specific applications, such as database management systems, BitTorrent, and many other applications.
- Private ports : from 49152 to 65535. These ports are not reserved by any application, and you can use them freely without affecting any other protocol.
UDP protocol: what is it and how does it work?
The UDP protocol (User Datagram Protocol) is one of the fundamental protocols on the Internet, it allows applications to communicate with guarantees regardless of the lower layers of the TCP / IP model. This means that routers (network layer in the TCP / IP model) only have to send the datagrams (unit of measurement in UDP). UDP supports multiple application layer protocols, such as the popular DNS and even the DHCP protocol to obtain (and provide) IP addressing automatically.
Main features
The UDP protocol allows the sending of datagrams without the need to establish a connection, it is only necessary to have a socket open at the destination to accept the datagrams of the source. UDP is a non-connection-oriented protocol, that is, it does not happen as in TCP where there is a phase of connection establishment, here they are directly sent without prior establishment “warning”.
This protocol does not provide any type of flow control , if one device is faster than another and sends information, it is very possible that information will be lost because it will collapse at the slowest, and we will have to proceed to the information forwarding. An important detail is that the datagram forwarding management is performed by the transport layer, since UDP is very simple and does not have control mechanisms for datagram forwarding because it has been lost.
UDP also does not provide any type of control of congestion , if there is congestion in the network, packets could be lost, and, of course, it will not be in charge of resending them as it happens with TCP. Therefore, UDP does not have congestion control, flow control or error control, it could be said that UDP is an unreliable protocol. In addition, it does not provide order in the datagrams sent, nor information if a datagram has arrived correctly, since there is no confirmation of delivery or receipt. Any type of guarantees for the transmission of information must be implemented in higher layers.
This protocol is mainly used in DHCP and DNS where speed is more important than reliability. UDP is widely used in tasks of controlling audio and video transmissions over a network. UDP only adds application multiplexing and checksum addition to the header and payload.
UDP header
UDP adds 8 byte header in each datagram. In this UDP header we will find the source port and destination port of the connection (socket), the length of the datagram and the checksum of said datagram to verify that it has no errors neither the header nor the datagram data. The ports (Source Port and Destination Port) are essential for the proper functioning of UDP. UDP uses these port numbers to identify a socket, that is, an application that emits data or receives data.
TCP vs UDP in the different VPN protocols such as OpenVPN
OpenVPN is a protocol to create virtual private networks that allow us to ensure point-to-point communication, since all tunnel traffic is encrypted and authenticated. In RedesZone you have a complete tutorial on how to configure an OpenVPN server and connect to it easily.

OpenVPN allows us to use both the TCP and UDP protocol for the data tunnel, as you have seen, TCP and UDP are very different, and it is always advisable to use TCP since it has flow control, congestion control, error control and many other features that make a connection reliable. If you are going to use OpenVPN, by default UDP is used, this is because, if there is any problem, the application layer protocols such as HTTP (which uses TCP below) will be responsible for performing retransmissions if were necessary, so the connection would be reliable (flow control, congestion, errors etc) even if the point-to-point encrypted tunnel uses UDP.
A very important aspect is that an OpenVPN server with UDP, will be able to accept more incoming connections simultaneously if you use UDP than if you use TCP, in addition, we will also have a greater bandwidth since an additional “load” is not added, because because UDP is much “lighter”.
As you have seen, both TCP and UDP are two fundamental Internet protocols, and each of them handles different protocols of the application layer.