 It is not necessary to have PCs, laptops or equipment with high performance. The TCP SYN attack can work even on computers still compatible with very slow Internet connections. This is a threat that lurks both the domestic and also in the professional field of small, medium and even large companies. TCP SYN attacks is one of the most used DoS attacks to block a server, although there are ways to mitigate it effectively.
It is not necessary to have PCs, laptops or equipment with high performance. The TCP SYN attack can work even on computers still compatible with very slow Internet connections. This is a threat that lurks both the domestic and also in the professional field of small, medium and even large companies. TCP SYN attacks is one of the most used DoS attacks to block a server, although there are ways to mitigate it effectively.
DoS attacks are known to be devastating with servers, especially those that provide web services. By generating junk traffic, the possibility of real traffic from making legitimate requests is denied. On the other hand, DDoS attacks are the ones that have made the most history for more than 20 years. One of the essential tasks of everyone who is involved in computer security and who wants to prevent attacks is knowing in detail how they work. Thus, the action plans to be developed and implemented are much more effective.
How TCP SYN attacks affect servers
The main target of this type of attack is the hosts that run TCP processes. Thus, the vulnerability of the three-way handshake TCP process explodes. This process is designed in such a way that two computers can negotiate the TCP socket connection parameters, before data transmission as SSH and HTTP requests. TCP three-way handshake scheme:
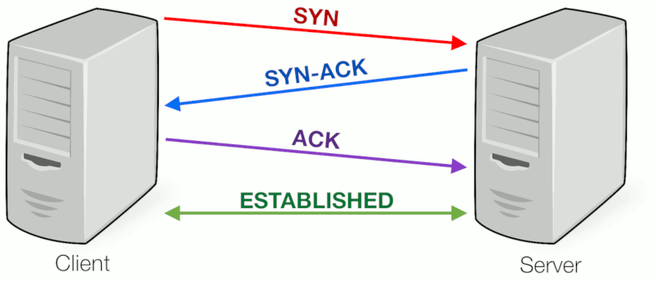
- Host A sends a TCP SYN chronize packet to Host B.
- Host B successfully receives the SYN from Host A.
- Host B sends a SYN chronize- ACK nowledgement to Host A.
- Host A receives the SYN-ACK from Host B.
- Host A sends an ACK nowledge to Host B.
- Host B receives the ACK from Host A.
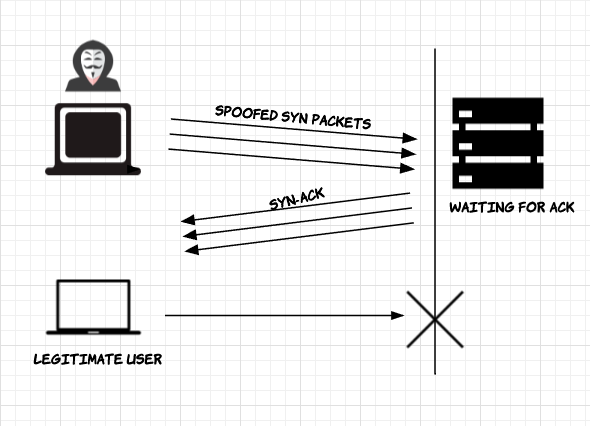
Considering the diagram above and assuming that Host A (Client) and Host B (Server), the attacker pretends to be Host A. Then, he begins sending an excessive number of TCP SYN requests under random IP addresses to Host B .
Host B takes for granted that the requests received are legitimate, so it responds with a SYN-ACK. However, he does not receive the final ACK. As a consequence, the connection request is never specified. Meanwhile, you must continue sending SYN-ACKs to the other requests even without receiving a response. Thus, Host B is no longer available for truly legitimate connection requests.
We suggest here several ways to mitigate these types of attacks:
- SYN Cookies: A cryptographic hashing process is performed, using an Initial Sequence Number and the initial SYN-ACK that is generated. That number originates from the source IP address, destination IP, port numbers and a secret number. The NSI is useful when the server receives the ACK from the client, validates by checking the incremental matches of that number. Finally, memory is needed to establish the TCP connection.
- Increase of Backlog Queue: Each operating system has a BQ limit to store unfinished TCP connection requests. Once that limit is reached, those connections are terminated. To mitigate the SYN attack, the Backlog memory can be increased so that legitimate connections can also be created.
- Limit the time of connections without fully establishing: operating systems allow you to configure the kernel to reduce the time for which a TCP connection is saved, after this type, if it has not been fully established, the connection is finally closed.
- Firewall Filter: The limit of the source (source threshold) can be changed by configuring the firewall to allow connections ends just before the new limit established origin.
As you can see, although the TCP SYN attack is very popular, there are effective ways to mitigate the effect of this technique.