Today most websites use the secure HTTPS protocol for communications between clients and the web server, thanks to this protocol that uses TLS and the cryptographic algorithms incorporated in the latter, communications are encrypted point-to-point, in addition, also The authenticity of the connection and even the integrity of the data are checked, so that cybercriminals cannot modify the packets on the fly. However, there is an attack on the HTTPS protocol called SSL Stripping , this attack consists of “lifting” the TLS encryption of the communication so that a cybercriminal can see all communications in plaintext using HTTP. Do you want to know everything about the SSL Stripping attack and how you can protect yourself to prevent a cybercriminal from compromising your communications?

How does the HTTPS protocol work?
The HTTPS (Hypertext Transfer Protocol Secure) protocol is the secure version of the popular HTTP (Hypertext Transfer Protocol) protocol. This protocol is in the application layer and is based on HTTP, but the security of the TLS protocol (at the transport layer level) is added in order to provide point-to-point security in all connections, from clients to the web server. The TLS protocol is one of the most used to provide communication security, in addition, it is not only used in HTTPS connections but also in other protocols such as FTPES (the version of FTP, but with the security layer using TLS) and even virtual private network protocols like OpenVPN. The TLS protocol (and therefore also the HTTPS protocol at the application layer level) makes use of different cryptographic algorithms that provide us with the following characteristics:
- Confidentiality : Confidentiality in cryptography means that all data is encrypted end-to-end, and that only the source and destination will be able to “read” that data. If a cybercriminal places himself in the middle of the communication (Man in the Middle attack) he will be able to capture the information without problems, but he will never be able to read it if he does not have the private decryption key.
- Authenticity : this characteristic of cryptography guarantees us that the data is authentic from the origin, and that there has not been an impersonation by a third party.
- Integrity : this feature guarantees that all data from origin to destination has not been modified, in case it had been modified due to a malicious third party, that information could be detected and discarded.

Currently the HTTPS protocol for the HTTP / 2 version makes use of the TLS protocol in its version TLSv1.2 and also TLSv1.3, these two protocols are currently considered safe, and no vulnerabilities have been discovered that make them dangerous to use. The TLSv1.3 version is much faster than the previous version, in addition, it only supports secure cipher suites, and does not allow the configuration of less secure cipher suites like TLSv1.2.
Regarding the ports, while the HTTP protocol uses the TCP protocol in the transport layer and port 80, the HTTPS protocol uses the TCP port 443. In recent months the QUIC protocol has been standardized for web connections, a protocol for HTTPS when HTTP / 2 and / or HTTP / 3 is used and that uses the UDP protocol to make point-to-point connections, this QUIC protocol already incorporates secure cryptography with the latest secure cryptographic algorithms such as Chacha20-Poly1305 or AES -GCM.
Once we know how HTTPS works and what protocols we have underneath in the different TCP / IP layers, we are going to see what the SSL Stripping attack consists of to decrypt all HTTPS communications.
What is the SSL Stripping attack?
When we carry out an ARP Spooping attack and we put a sniffer to capture all the traffic, what we do is capacity all the network traffic generated by a certain computer (the victim). In the event that you use non-secure protocols such as HTTP or FTP, we can easily see all your communications, authentication credentials and even session cookies. For this reason it is so dangerous to connect to public WiFi networks or unreliable networks, because any cybercriminal can carry out this Man in the Middle attack and capture all the information.
If we use a secure protocol such as HTTPS, the attacker will be able to capture all the information without problems, however, he will not be able to read any of its content, that is, he will not be able to see authentication credentials, session cookies or absolutely nothing, because all traffic is encrypted end-to-end (from clients to the web server). Thanks to the TLS protocol and cryptographic algorithms such as AES, our information will be confidential, that is, it will be encrypted end-to-end.
SSL Strippping attacks consist of setting up an HTTP / HTTPS proxy in order to “lift” this encrypted HTTPS protocol, and the victim makes use of the HTTP protocol to be able to capture all the information and see the data inside . The process that would have to be carried out in order to violate an HTTPS connection would be the following:
- Carry out an ARP Spoofing attack on the victim , to forward all the network traffic to us before passing it to the router, in this way, we will capture all the information that this victim sends and receives.
- We put the sniffer to work , for example, WireShark is a very good option, it is one of the most complete and easy-to-use software, and it is completely free.
- Check if we are capturing all the victim’s traffic, in this way, we will make sure that the ARP Spoofing and the sniffer is working correctly. In this case, surely we can only see DNS, ICMP and other traffic in clear text, but not HTTPS traffic because it is encrypted end-to-end.
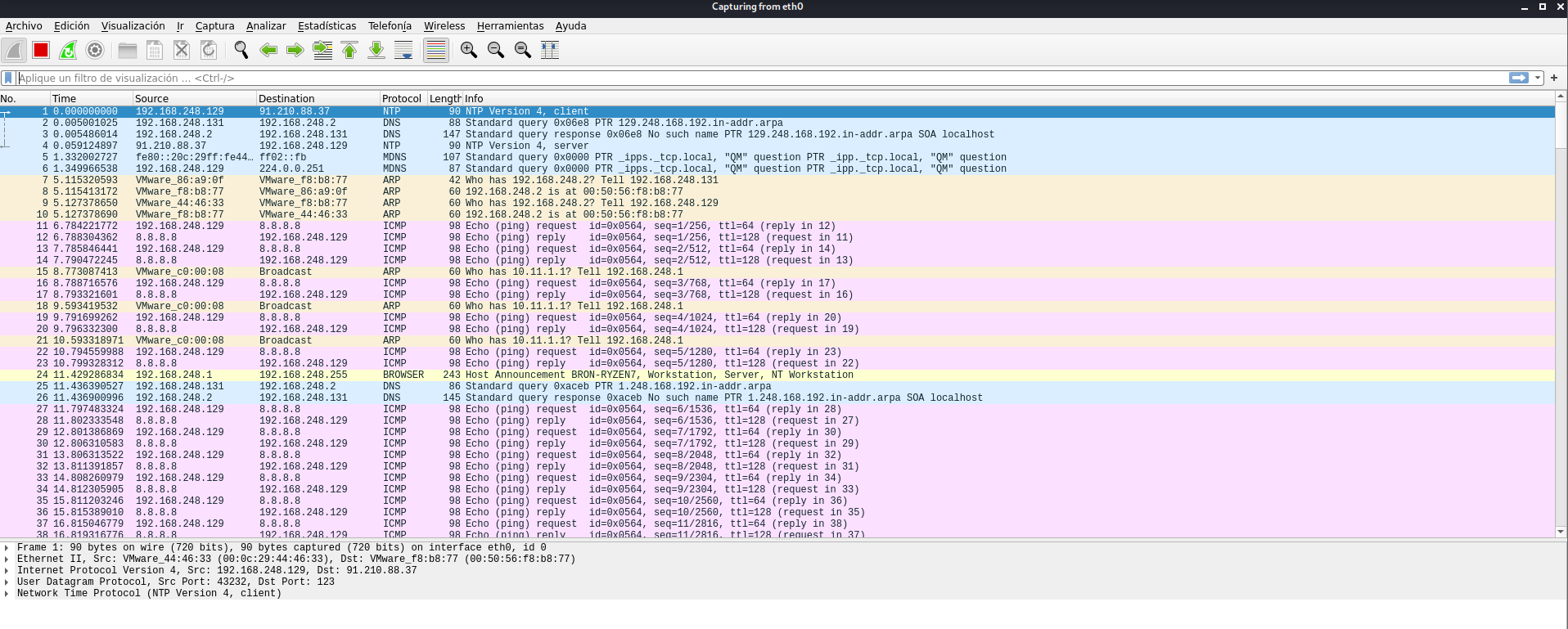
Once we have carried out these three steps, what we have to do is configure an HTTP / HTTPS proxy using free tools, for example, Bettercap is the best tool that we can use to carry out this type of attack. Once we have configured this HTTP / HTTPS proxy, what will happen will be the following:
- The victim will try to connect to the webs through the HTTPS protocol, however, the HTTP / HTTPS proxy that we have configured will tell the victim that the connection must be HTTP, subsequently, our HTTP / HTTPS Proxy could forward the information to the web real (Google, PayPal, Amazon etc.) via HTTPS. In this way, the attacker will have all the data in clear text coming and going from the victim and from the real web server, continuously transforming between HTTP and HTTPS and vice versa.
- The network sniffer that we had previously activated will capture all HTTP traffic and show us in clear text the user credentials, session cookies and everything the victim is doing.
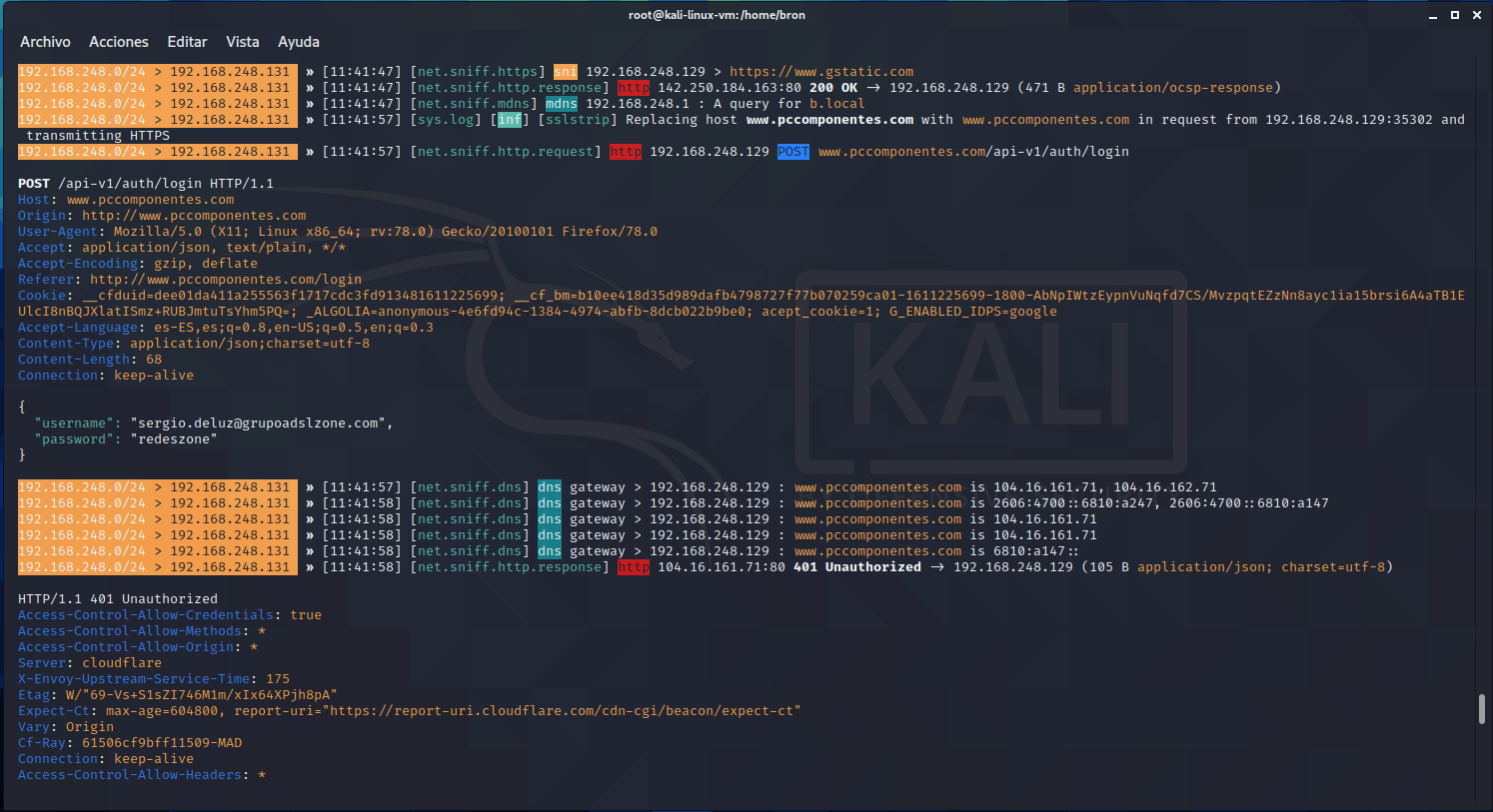
As you can see, the possibility of carrying out an SSL Stripping attack is available to everyone making use of free tools such as Bettercap for Linux, in fact, in this article you have a complete tutorial for you to do security audits and check if a certain target could use it against us, or if we are protected against this type of attack.
How can I protect myself from this attack?
This type of attack is widely used by cybercriminals to obtain all the traffic of their victims, especially in public networks, whether they are wired networks or public WiFi networks, for this reason, it is discouraged to connect to these types of networks that we do not manage. However, if someone is able to hack into our WiFi network, we would be in exactly the same scenario: we are on the same local network as the cybercriminal, they could make us an ARP Spoofing attack and also an SSL Stripping attack. For this reason it is so important to keep a list of wired or WiFi devices connected to our local network, and check from time to time that there are no intruders, in addition, we must also make sure that no one can enter our WiFi network, putting a WPA2 encryption -AES and disabling WPS (Wi-Fi Protected Setup).
This SSL Stripping attack cannot prevent them from doing it to us if we are on the same local network as the attacker, but what we can do is prevent it from being effective, that is, from being able to “lift” the HTTPS connection, so that confidentiality would continue to be maintained and we will be able to navigate safely. Currently there are several methods that we can use to protect ourselves against these attacks, some depend on the web administrator, and others depend exclusively on us.
That the web has HSTS enabled
HSTS or also known as HTTP Strict Transport Security, is a policy that is in web servers that forces us to use HTTPS in our web browser to communicate with the server. Previously we have explained that the HTTP / HTTPS proxy server can communicate via HTTPS without problems with the web server, however, if a website has HSTS activated, a cookie will be saved in the browser indicating that that browser can never use the HTTP protocol to communicate with the web server, in this way, we will have point-to-point security, even if someone intrudes by putting an HTTP / HTTPS proxy to “lift” the HTTPS of our communication with the web.
Today many web servers of different web pages are correctly configured with this security policy, in order to protect their users. These cookies that are stored in the clients’ web browsers expire, however, what is done is to put that the duration is the maximum (one year), in order to protect the clients as long as possible.
The negative part of HSTS is that, if it is the first time that we access a website and they do an SSL Stripping, this feature will not be able to protect us. The protection is from the second visit because the cookie will have already been downloaded, unless we have a list of preloaded websites in our web browser, as happens with the “big ones” like Google and other services. We ourselves could set up a list of sites for HSTS preloading that is provided by Google as part of the Chromium project.
In the Apache web server we would have to incorporate the following directive:
- Header always set Strict-Transport-Security «max-age = 31536000; includeSubDomains »
In the Nginx web server we would have to incorporate the following directive:
- add_header Strict-Transport-Security «max-age = 31536000; includeSubDomains »
We could also indicate to these directives the “preload” at the end, to indicate that it is preloaded in the web browser and to be able to enter the web without problems.
To check if a certain website has HSTS enabled, you can always access the Qualys SSL Labs official website where you can analyze all the websites you want. Before concluding, we must indicate that this HSTS protection can also be circumvented, based on DNS Spoofing to forward the victim to another domain under our control that is the same as the original, with the aim of “deceiving” him, Bettercap also includes this feature.
Use a VPN
Another method to avoid this type of attack on HTTPS connections is to use a VPN service. A virtual private network or VPN is responsible for encrypting all point-to-point communications within a tunnel, therefore, an attacker who makes us an ARP Spoofing attack and puts a sniffer, would only see all the encrypted traffic, he could not see any additional protocol, because DNS resolutions also go inside the VPN tunnel. It is possible that the cybercriminal tries to “throw” this VPN tunnel, in fact, he could achieve it by injecting packets and making the VPN service stop working for security, however, we must remember that VPNs have a feature called Kill-Switch. The Kill-switch functionality allows you to completely block Internet traffic in the event that the VPN tunnel falls or has some kind of problem, in this way, we will have the assurance that our data is not filtered nor can they make us any other type of attacks. It is always better to stay without an Internet connection than to have information stolen.

Currently there are several VPN protocols such as WireGuard, OpenVPN or IPSec IKEv2, all of them are safe and we can use them to prevent someone from intercepting communications and lifting the encryption of the HTTPS protocol. For this reason, if you are going to connect to wired networks or public or unsecured WiFi networks, it is highly recommended that you always use this type of VPN. We can configure VPN servers ourselves in our home local network, if we have a NAS server it will have VPN applications, and even some home routers such as ASUS, AVM FRITZ! Box and even D-Link or NETGEAR have this type of servers to connect us to the Internet safely, because they redirect traffic.
In the event that you do not have the possibility or knowledge of installing and configuring a VPN server in your home, our recommendation is that you use VPN services such as WARP from Cloudflare, which is completely free and works really well, you can get high speeds download and upload and very low latency. Other alternatives that you can use are paid VPN services, because they have applications for all operating systems, multiple servers spread all over the world and important functionalities such as the Kill-switch among many others.
Perform an SSH Tunneling
Another way to protect yourself against SSL Stripping attacks is to perform an SSH tunnel with redirection of traffic. This technique consists of connecting to a remote SSH server that is trusted, and setting up a SOCKS proxy to later configure it in the web browser. In this way, we will be redirecting web browser traffic through the SSH server where we have connected. To do so, we must follow the following steps:
- Configure an SSH server in a secure way, changing ports, good authentication and a good cipher suite.
- Activate TCP forwarding on the SSH server, otherwise, even if we connect, we will not be able to forward Internet traffic.
- Configure this SSH server in programs such as PuTTY and enable forwarding or forwarding, in a specific SOCKS5 proxy.
- Configure this local proxy that we have just created in the web browser, so that all traffic flows through the SSH server to the Internet.
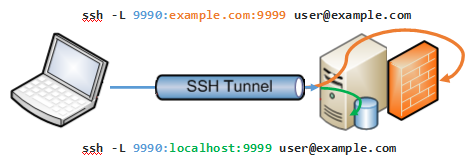
This method is exactly the same as that of the VPN server, using a “server” to connect to it securely, and then going to the Internet via HTTPS without anyone being able to lift this encryption.
Conclusions
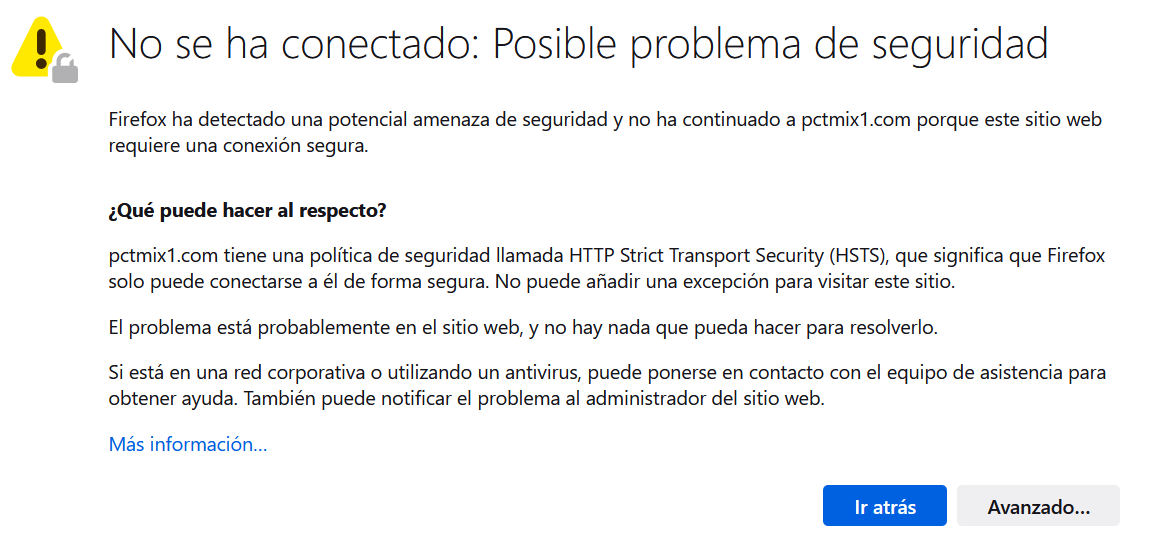
Although HTTPS connections are secure, in certain circumstances an attacker could “lift” that security to obtain user credentials and also session cookies, rendering HTTPS connections less secure. However, this type of attack can only be carried out in certain circumstances, such as the attacker and the victim being on the same local network, whether wired or wireless, and the websites visited by the user do not have the HSTS protocol enabled. It is very important to know in which websites we have the HSTS protocol available, to be calm when we navigate through that website, because if someone is carrying out an attack on us, the website will automatically tell us that a secure connection has not been established, and that the connection will not be made, protecting us from exchanging more data.
If we connect to the Internet in public networks through a VPN or doing an SSH Tunneling, we can be calm because they will not be able to intercept communications and violate them, for this reason the use of these techniques is so important when we are outside of our trusted networks . It does not matter if the VPN or SSH server is in our home, on a VPS server hired by us, and even if we use paid VPN services like the ones we all know, the important thing is to protect ourselves against an attacker who is on our local network and Avoid this type of SSL Stripping attack.