Currently there are a large number of hashing algorithms to check the integrity of the different files that we download over the Internet, transfer to other users, and we can even check if a certain file has been modified or not. Thanks to free tools such as QuickHash, we will be able to generate the hash of different files using different hashing algorithms such as SHA-3 and even SHA2-512. Today in this article we are going to explain what a hash is, which ones are the most used, and how we can obtain the SHA3 hash of a file in Windows.
What is a hash and what can we use it for?
A simple explanation of what a hash is, is that it is a unique fingerprint of the digital data, if the data of a particular file changes, the hash will change completely. Thanks to hashes, we can check if a file has been modified, and we can even check the integrity of the files when sending them over the Internet or downloading them from different servers. Currently we have many hashing algorithms, some of them are already considered insecure because collisions have been discovered (when generating the hash of two different files, the same hash is obtained) such as MD5 or SHA1, however, today we have algorithms safe hashes like SHA2-256, SHA2-512 and even the latest SHA3 that we already have available.

A very important aspect of hashes is that as soon as a certain data in the file is altered, the alphanumeric code we have as output in the hash, is completely altered. Imagine for a moment that you have to download the firmware of a router from a server that is on another continent. If, for example, that file was corrupted in the download, and the update started, it could render that device unusable. Some manufacturers provide the hash of their files to verify that we have made a correct download.
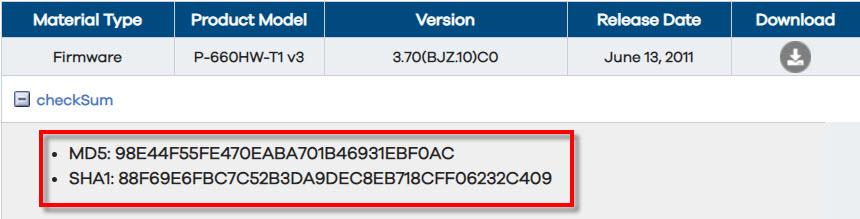
In this case, with a tool that could generate a hash that supports the MD5 or SHA-1 algorithm, we could contrast it with the one that the manufacturer is offering us. If it matches, we will have verified its integrity, and we can proceed with the installation of the firmware without any fear. Otherwise, we will know that it is wrong and we should not install it. An example of a program that we can use is QuickHash, which we will talk about later.
One thing to keep in mind is that with the hash of a certain file you cannot recover the original file. Also a good security practice is to store the password hashes in the databases, so that nobody can get the information in plain text. In order to store passwords, there are hashing algorithms specifically designed for this, such as scrypt or bcrypt.
QuickHash: generate SHA3 or SHA2-512 hashes easily
QuickHash is an open source data hashing tool for Linux, Windows and Apple Mac OS operating systems, it has a very friendly and easy-to-use graphical user interface. This tool currently supports the following hash algorithms: MD5, SHA1, SHA-3 (256 bits), SHA2-256, SHA2-512, xxHash, Blake2B (256 bits) and Blake3, therefore, it is a really complete tool. As if all this were not enough, we must indicate that it is completely free, and its development is sustained thanks to the donations of the people who use it.

Download, start up and main screen
To download the QuickHash tool we have to click on the following link to download QuickHash for free . As we discussed earlier, we can use the version for Windows, Linux and MacOS. In my case I am going to use the latest version available for Windows, the specific version is 3.2.0. Once downloaded we will find a file in ZIP format, which we will proceed to unzip into a folder.
A very positive aspect of this tool is that it does not require installation, therefore, in that folder that we have just unzipped, all we have to do is double click on the Quickhash-GUI file, in the file explorer you will see how application type. We also have a user guide for the tool itself.
The first time you start it, a screen like this will appear:

Above in the red box we have the main options of the program which are:
- Text : to hash fragments of text, such as paragraphs in a file.
- File – to select and then hash an individual file.
- FileS : to hash multiple files that are in a directory.
- Copy – Used to copy and paste, but with the added data integrity of hashing. It is designed to allow a user to copy files from one place to another, but have the copying process verified and backed by hash values.
- Compare Two Files : Compare the hashes of two different files found in two different locations.
- Compare Two Folders : it is used to compare the contents of the file of one folder with another to see if all the files inside match according to the hash (the file names are not compared).
- Disk : to check the hash of physical disks and logical volumes.
- Base64Data – Allows the user to hash a Base64 encoded file and generate a hash of its decoded counterpart, without the user having to create the decoded version. Also, it supports decoding of Base64 encoded data, just for convenience.
In purple are the algorithms that we can use to obtain our hashes, to highlight the algorithms of SHA2-512, SHA-3 and also BLAKE3.
Sections Text, File, Compare Two Files of QuickHash
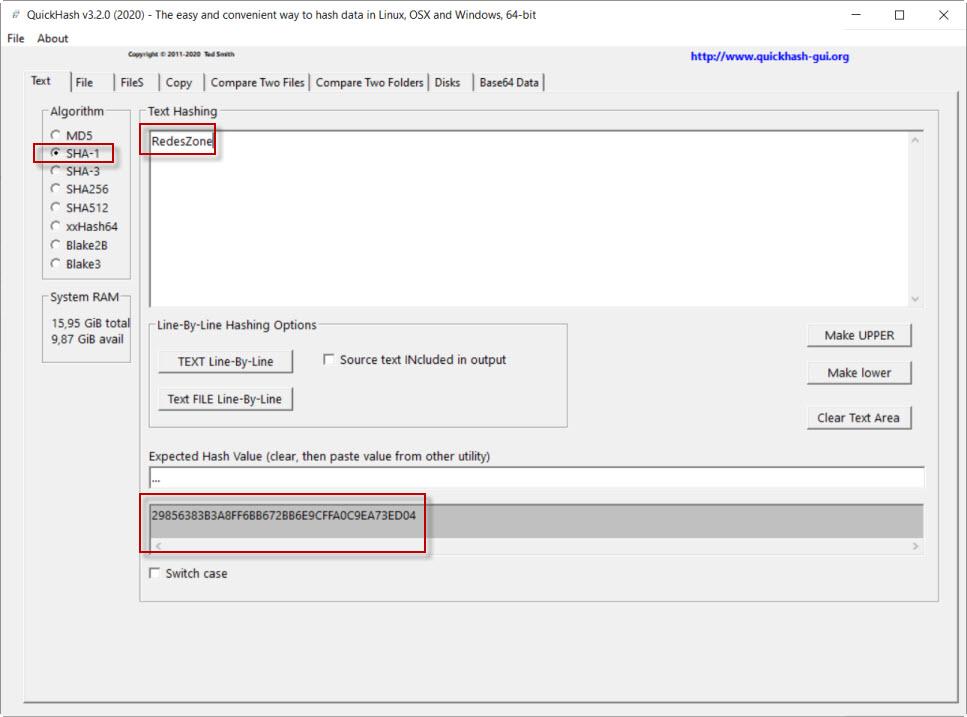
Let’s start with the Text section. For example, imagine that we need to hash the text this article with the SHA-1 algorithm. This would be done like this, starting by selecting the SHA-1 algorithm, then we write the text and finally we will get the hash below.
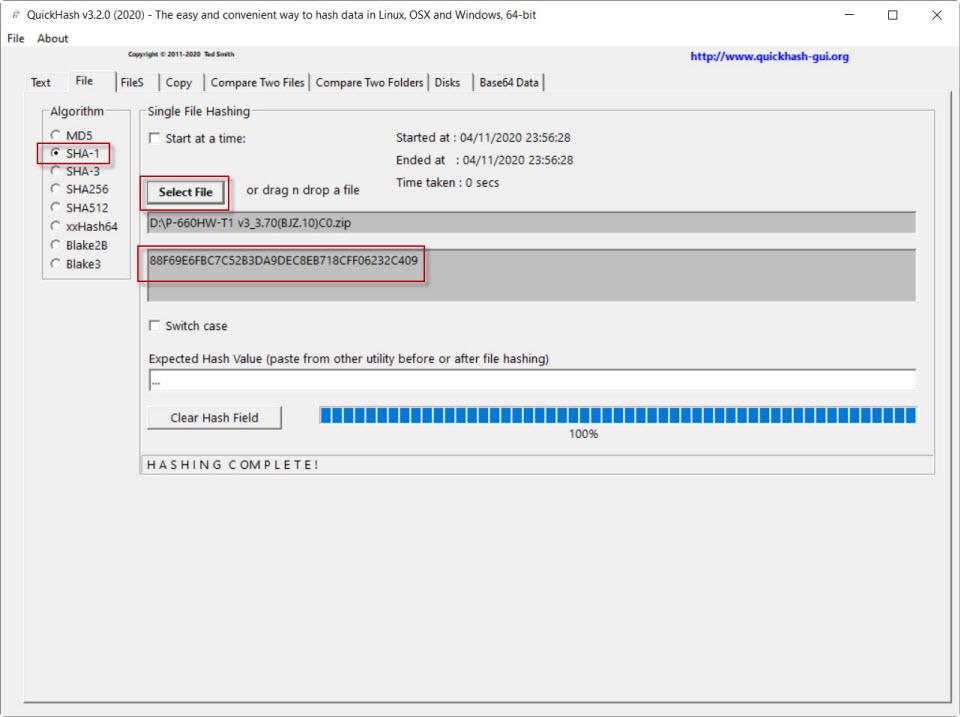
At the beginning of the tutorial we talked about the file of a router that we wanted to check if it was in good condition after downloading it, and if it had not been corrupted. The manufacturer gave the possibility of verifying that this file was ok using the SHA-1 algorithm. Thus it offered the following value for verification: 88F69E6FBC7C52B3DA9DEC8EB718CFF06232C409.
To check it, we go to the File section . In Select File we select the firmware file, we put the SHA-1 algorithm and then we can verify that the hash is identical. That means the file is fine, and we can flash the firmware with complete peace of mind.
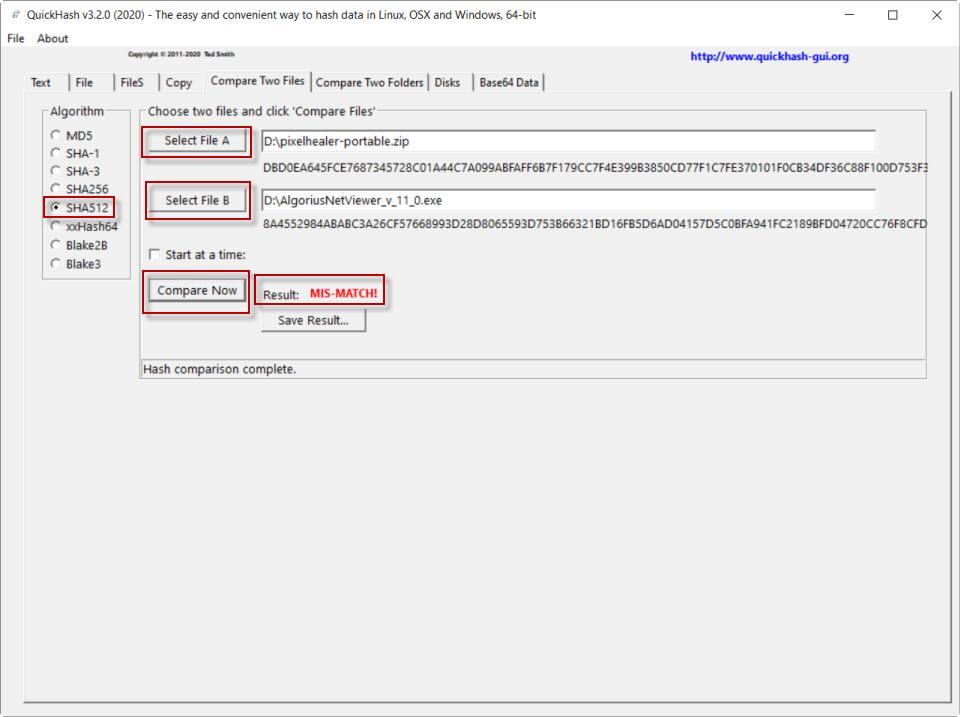
Now we are going to compare two files using the SHA2-512 algorithm. To do this, we turn to Compare Two Files . First we are going to give an example with two different files. We start by selecting the algorithm and then the two files. We would put the first file in Select File A and the second file to make the comparison in Select File B. Next, we give Compare Now and MIS-MATCH will appear in red indicating that they are different.
On the contrary, if we take two identical files and repeat the process following the same steps and giving Compare Now, we obtain this result:
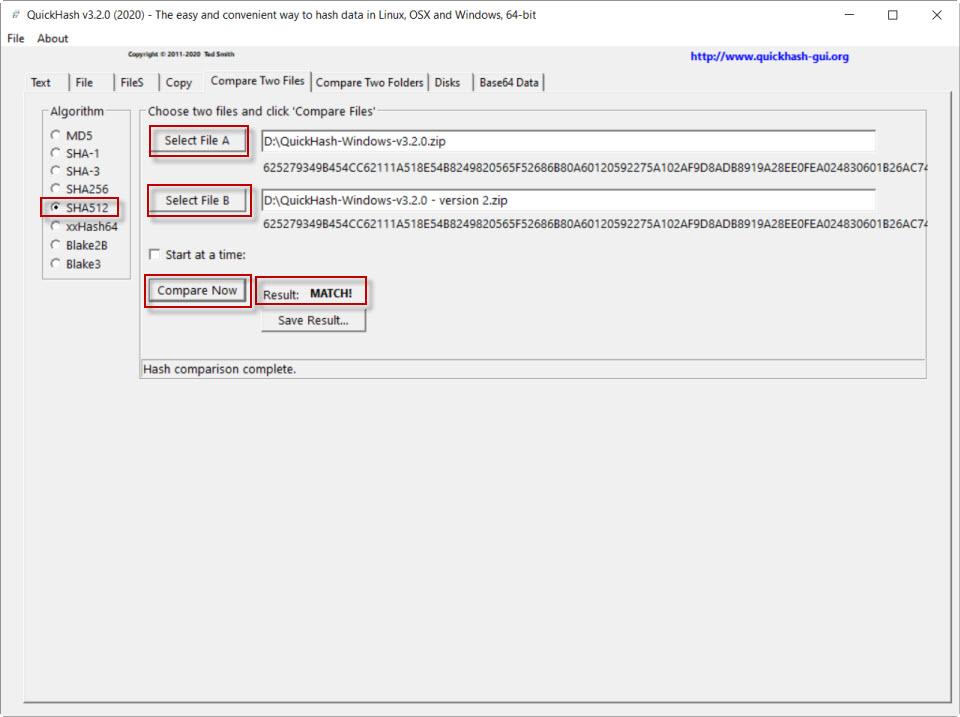
Here it says MATCH! , which means they match.
FileS, Copy and Compare Two Folders sections of QuickHash
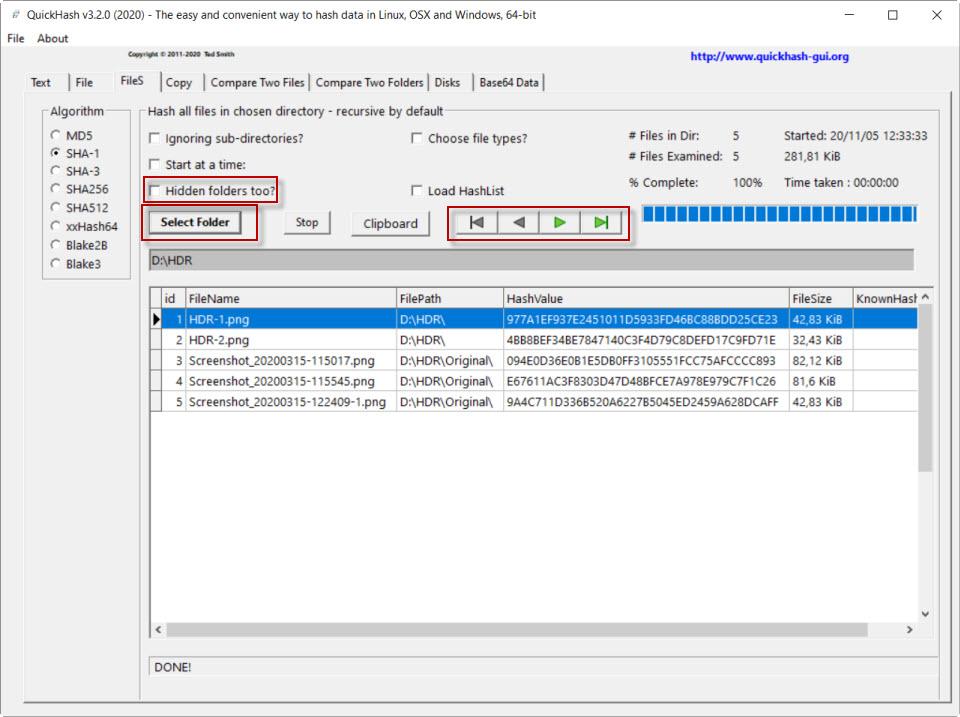
The next section you are going to use is FileS , which is used to see the hash of the files in a directory. In Select Folder we select the folder. As you can see, it detects the files that are in the subdirectories. You also have the option to search for hidden directories with the Hidden folders too? In addition, you have a media player style bar to move between files.
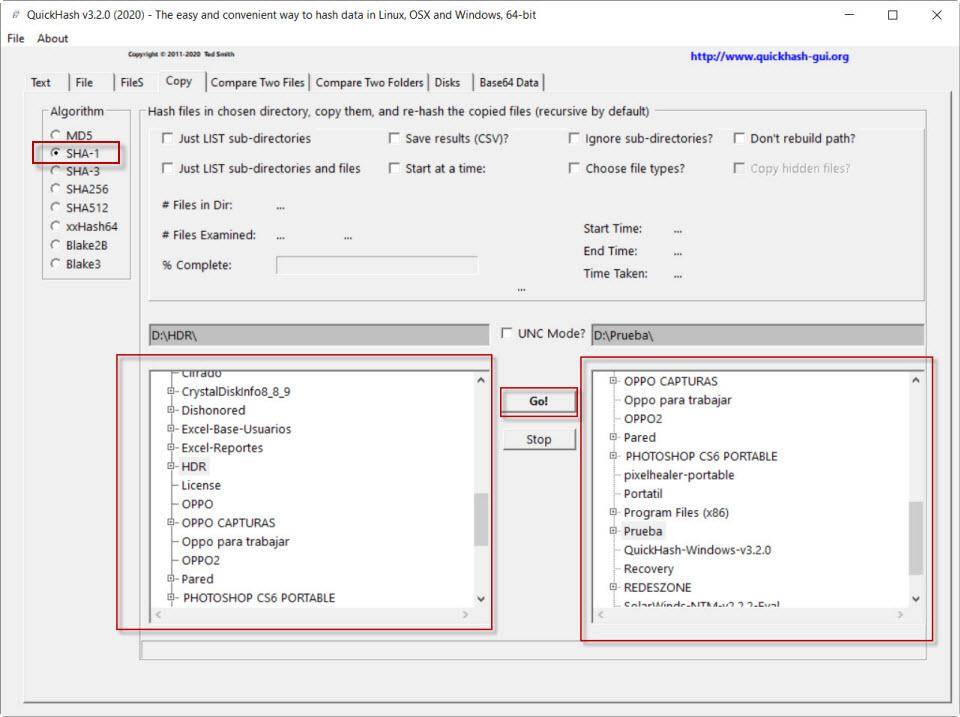
Now it is the turn of the Copy section, which is used to copy files and to verify that it has been done correctly by checking its hash. We will start as usual, choosing an algorithm. Then, on the left side, we choose the source folder that we want to copy. On the right we choose the destination, in this case I created an empty folder called Test. Once done, click on Go! to start the process.
Then we get a screen like this. Here we see the path of both, both origin and destination with their corresponding hashes. In this case, it can be seen that they coincide and that 5 files have been copied.
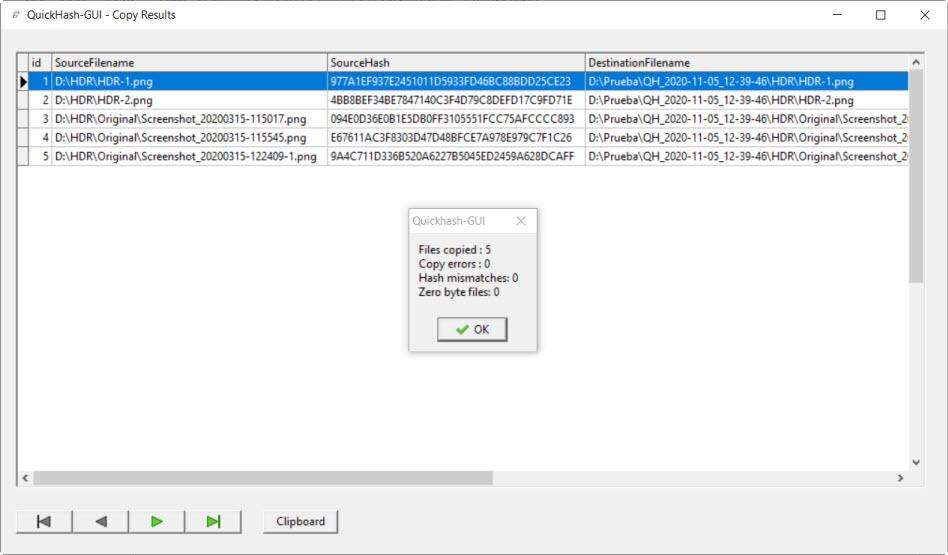
If we leave here, we see how it indicates a summary of the work done and that the copying process has finished.
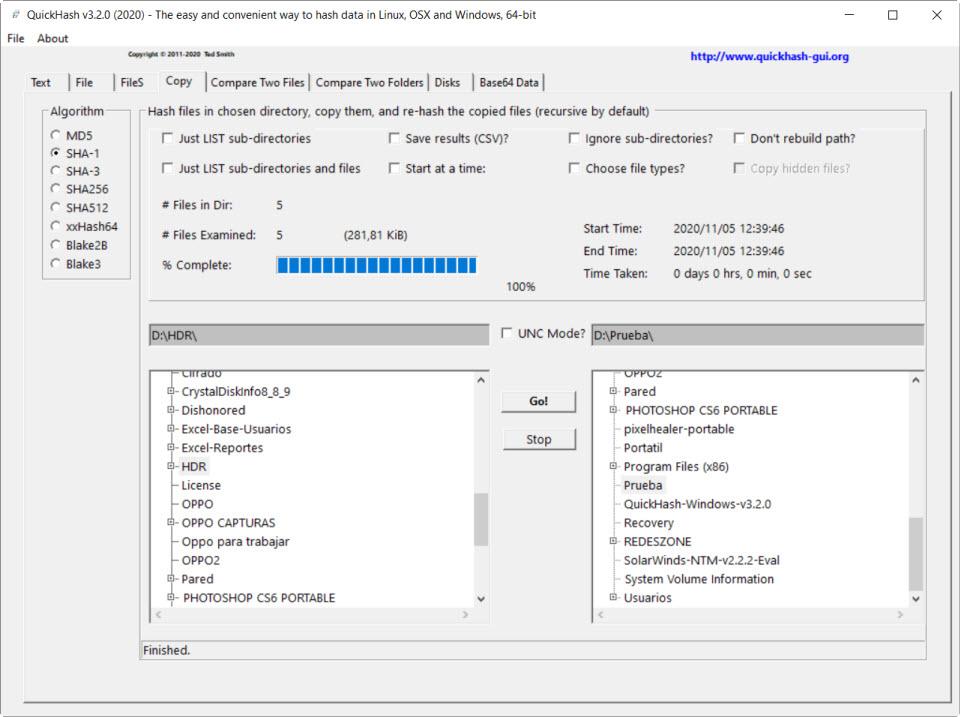
The next section that we are going to see is Compare Two Folders, which is used to compare the hashes of the files in two directories. To do this, we select the algorithm, in Select Folder A we put one folder and in Select Folder B the other. Next, click on Compare Now .
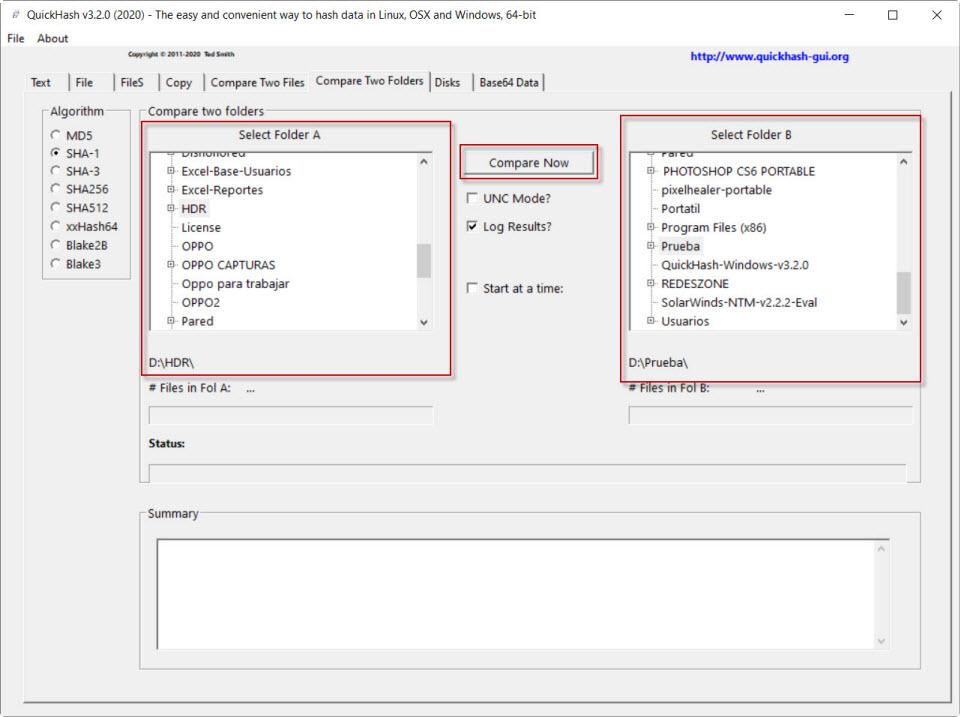
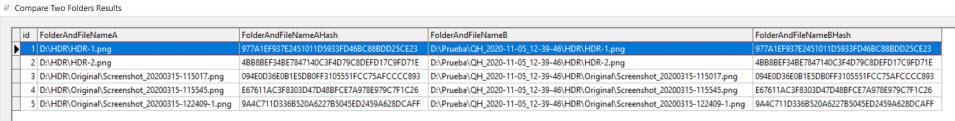
Here we see the routes of both with their corresponding hashes and it can be seen that they coincide.
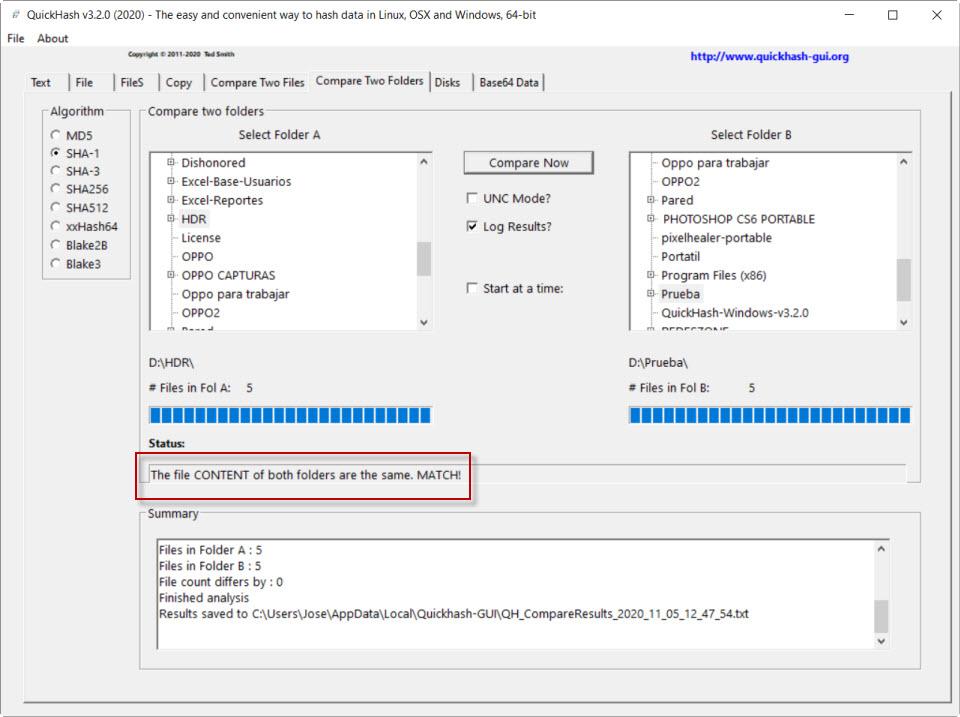
If we return to the screen where we started at the bottom in the red box, it tells us in English that the two directories coincide.
Finally, as you can see, Quickhash becomes a useful tool with which we can work with hashes in many ways.