As the person responsible for the administration of your company’s network, you have done everything possible to ensure that operations continue as normal. But in these times, from the home of each of the workers. However, have you thought about protecting yourself from devastating attacks like ransomware? Lack of focus regarding protection measures can cost a certain sector of the organization, or the organization as a whole, dearly. At the end of the day, those who are most affected are the users.
Many organizations have been forced to migrate a good part of their workforce to their homes, and even in certain companies, to all their workers. What is often not taken into account is that, although the collaborators are outside the organization, they are exposed to cyber attacks, in fact, cyber attacks are more dangerous in these cases because we do not have the protection measures of the company in question.

Essential measures of protection against ransomware
Unfortunately, almost all good cybersecurity practices applied to the workplace are not usually applied in the home. Because it is customary to think that homes “are safer.” That’s a lie. There is nothing more insecure than the home network. You are absolutely exposed to any type of cyber attack if you do not take the necessary measures on your computer. For example, the installation, configuration and maintenance of antivirus / antimalware solutions.
On the other hand, we also have to avoid taking advantage of connectivity from our homes to use services that are not related to work through corporate emails. At some point, it could be an oversight: you will receive an email with a suspicious attachment or a link urging you to take a certain action.
A few seconds later, you already have the warning on the screen informing you that your files have been encrypted. Although even if you are not working, at leisure you could be a victim of ransomware.
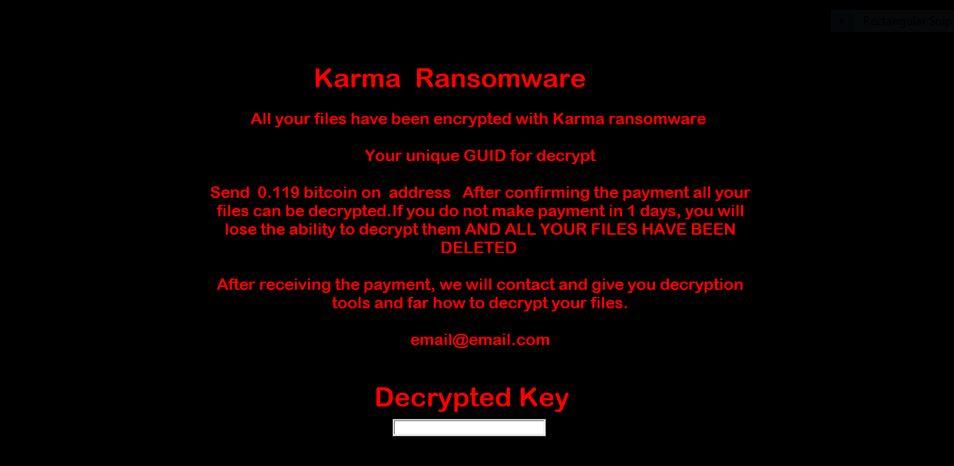
Ransomware example
Remember that ransomware attacks are characterized by ransom . In Spanish, this term means “rescue“. Which means that if we make the ransom payment, we would be doing it for the rescue of our files. However, this is one of the least recommended practices.
You are more likely to become a victim of ransomware after paying for it, as opposed to not having done so. It is like the cybercriminal counts on you so that whenever he attacks you, you pay him. It is like the cybercriminal is the sales executive and you are his client.
Port and protocol blocking
As network administrators, you can perform a number of Group Policy settings. This, in order to disable all network connections to any server or computer, according to the policies. What does it consist of? Common ports and protocols should be blocked which in fact should be blocked between computers.
Also, block all common ports and protocols that should be blocked when there is communication between computers and non-domain controllers, as well as non-file servers. Some of the ports – at the Windows Firewall level – that are recommended to be blocked are:
- Server Message Block
- TCP Protocol – Port 445
- TCP Protocol – Port 135
- TCP Protocol – Port 139
- Remote Desktop Protocol (TCP / 3389)
- Windows Remote Management / Remote PowerShell
- TCP Protocol – Port 80
- TCP Protocol – Port 5985
- TCP Protocol – Port 5986
- Windows Management Instrumentation
- Port number range assigned through DCOM
Remember that these actions are performed at the firewall level. On the other hand, in the event that you take the step of blocking any type of incoming connection, that is, any port number and protocol; there will definitely be no traffic. It is important to consider that this measure is appropriate only in a critical scenario. The latter may be if the organization is a victim of ransomware.
Beyond technical actions or measures that we can take to protect our computers, the most important thing is to educate ourselves. Connectivity is part of our daily life, let’s take the opportunity to access this and hundreds of other guides that will tell you everything you need to know to protect yourself from ransomware. So, too, how to keep day-to-day connected much more securely.