USB memory sticks and external hard drives are one of the fastest and most convenient ways to always carry our data with us. We do not need the Internet, nor do we need to log in to any cloud, nor do we run the risk of leaving the session started and that others can have access to all our data. In addition, today USB memories are very cheap and have a large capacity, so they are ideal to always carry in your pocket. At first glance, everything looks like advantages. However, this type of device has a serious drawback, and that is that if we connect the disk or USB to a PC with a virus , we can bring a copy of the malware to our PC without knowing it.
Most of the viruses, Trojans and other malware samples that circulate on the network have functions that, when a new device is connected to the PC , are automatically copied to it. With this, the virus ensures that, when we connect the device to any other computer, it automatically infects it, even if this PC has never been connected to the Internet.

Surely we all have an antivirus on our computer today. Although it is Windows Defender , Microsoft‘s antivirus that is installed by default in Windows 10. These programs are always in charge of analyzing all the memories and devices that we connect to the PC and eliminate any threats that may be found. However, if for some reason we have the antivirus disabled, or we simply do not have it installed, we may be putting the security of the computer at risk without knowing it.
Protect a USB from viruses without the need for an antivirus
There are several ways to protect a USB stick or hard drive from viruses to prevent malware from copying itself to it. Many of them are based on programs, which either change permissions to prevent unauthorized writes, or simply create a corrupt and protected autorun so that, even if the virus is copied to the drive, it cannot infect other PCs. But all this we can do much better without resorting to additional software using the administrative options that Windows offers us.
The first thing we are going to do is format the USB stick in NTFS format . If we use another file system, such as FAT32 or exFAT, we will not be able to use this function. So if we don’t have the drive on this system yet, we need to format it in order to continue. To do this, we simply connect it to the PC, click the right mouse button on the unit, and choose to format.
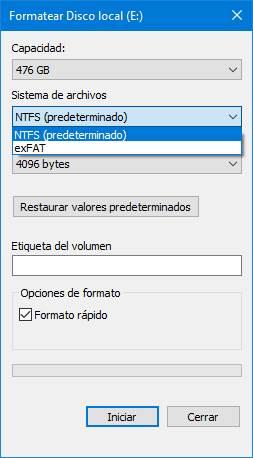
We make sure it is marked in NTFS format and we start formatting the drive. It is important to remember that this process will erase all the data that has been saved in the memory, so if we have important data we must save it on the PC first.
If the drive is already in NTFS, there is no need to format it again.
Next, we open “This computer” again, right-click on the storage unit that we want to protect and open the Properties window. In it, we are going to select the “Security” tab , as we can see below.
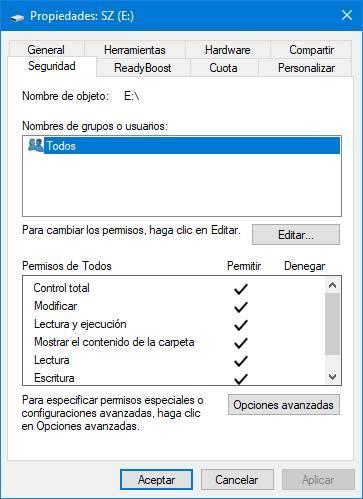
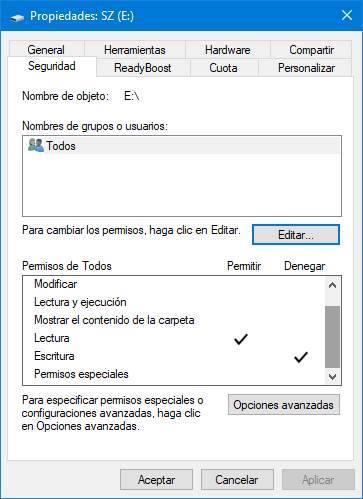
From here we will be able to modify all the general permissions of the unit, since it is one of the characteristics of the NTFS file system. So if the drive is on FAT32 or exFAT, we won’t see this tab. As we can see, being an external drive, it is designed so that any user has full permission on it. And this is what we want to avoid.
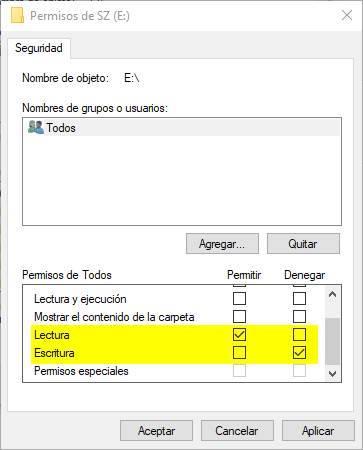
We select the user “All” , and click on the “Edit” button to modify the permissions . A new window will appear from which we will be able to adjust the permissions of our PC as we want. What we must do is deactivate all the options that come to us, and leave only the following:
- Allow -> Read
- Deny -> Write
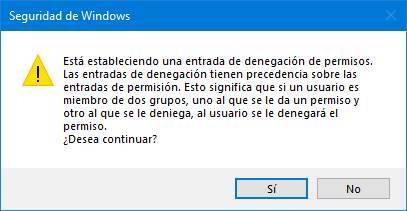
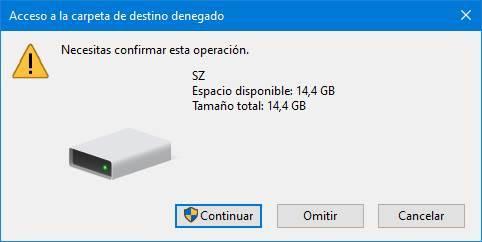
We apply the changes and we will see a notice that tells us that, by giving a deny permission, if a user belongs to two groups, the more restrictive permission will be applied. We accept it and let Windows perform the necessary tasks. If an error appears, we can ignore it.
Ready. We have already blocked the write permissions to our USB memory, allowing only reading. In this way, if we introduce it into a computer, and a virus tries to copy itself to it, we can see how it will not be able to do so.
Of course, we must bear in mind that this method is a double-edged sword. We will prevent viruses from being copied to the USB memory, but we will be left without the possibility of copying files to it from other computers. We can always change the permissions back if we need to copy files to memory. But we must always do it from a clean and reliable PC.
If we need to copy files to USB we can resort to the following intermediate “trick”.
Create a “clean” folder to save files
With the above method, our USB will be totally blocked. The files we have will remain in memory, but cannot be erased. And we won’t be able to create new files and new folders either. Of course, no malware can copy itself to memory without permission, or create an autorun.
We have a “read only” memory. But, using a trick, we will be able to use it. What interests us to protect the USB or hard drive from viruses is to block the root. But we can create a folder inside memory, and change the permissions , to save the data we want in it.
To do this, before blocking the write permissions on the USB, we will have to create a new folder, and give it the name we want. Next, we block the USB write permissions as indicated in the previous step. But, before disconnecting it, we open the properties of the folder that we just created, and in the “Security” tab , we will edit the permissions.
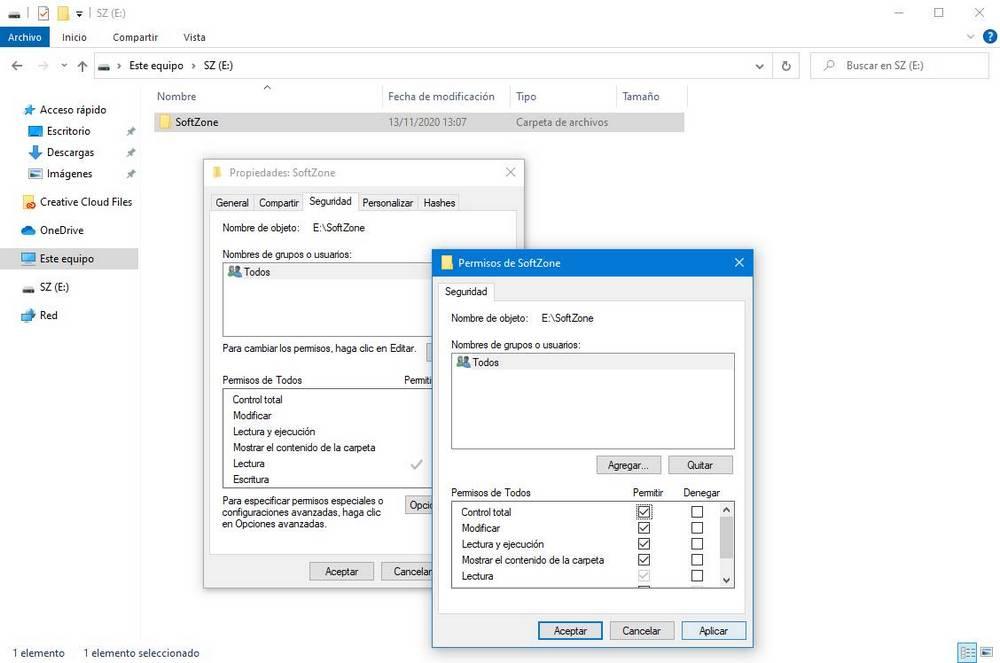
We will mark the option of “Allow” the “Full control” of the folder . This will allow us to both open and copy and delete files within this folder, while the root, and the rest of the directories that we do not modify, will be blocked.
Malware is not typically copied to personal folders, instead creating its own hidden folders and generating the autorun to run automatically when the drive is connected. With these configurations we will prevent it from doing this and, in addition, we will have the unit fully functional.