PrintNightmare is the latest Windows glitch that is giving users headaches. This vulnerability is found in the Microsoft printer driver and can allow an attacker to remotely execute code on the PC and gain SYSTEM privileges within the computer. In addition, there are already several public exploits circulating on the network, so it is a failure that is being exploited on a massive scale, a failure that must be protected as soon as possible. Although Microsoft makes it difficult for us.
Just yesterday, Microsoft released an emergency update, after the deadline, to mitigate this vulnerability in all its operating systems, even some, such as 7 or some of the first versions of Windows 10, which are no longer supported. This patch blocked the most serious, the RCE bug that allowed code to be remotely executed on affected computers. Unfortunately, the new patch that Microsoft has released is of no use, and it is not even a few hours until they have shown how easy it is to avoid it.

Patch against PrintNightmare is ineffective
As usual, especially when it comes to such a serious security flaw and with so many exploits circulating as has happened with this one, as soon as Microsoft made the new patch public, they began to check if, indeed, the vulnerability was solved. And, unsurprisingly, it has not.
With a few simple changes to the exploits, it is possible to continue exploiting this security flaw without any problem. Hackers are still able to remotely execute code and gain privileges even on computers and servers that have installed this new patch out of time.
At the moment, Microsoft has not made official statements about the uselessness of its new update. But security experts are clear about it: if you want to protect yourself from these security flaws, you have to take the necessary measures yourself.
Secure computers and check mitigation
There are several ways to mitigate these problems. One of the easiest and fastest is to use the PowerShell console, as an administrator, and run the following commands:
- Stop-Service -Name Spooler -Force
- Set-Service -Name Spooler -StartupType Disabled
We can also do it from group policies. In “Computer Configuration> Administrative Templates> Printers” we will double click on ” Allow the print job manager to accept client connections ” and we will mark this directive as ” Disabled “.
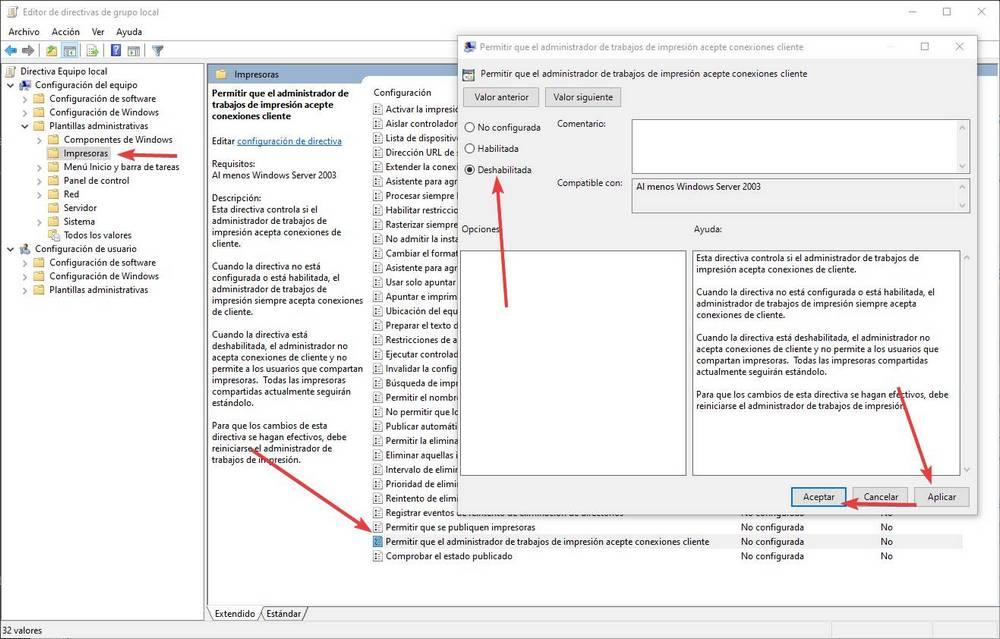
We must also ensure that the following registry entries, within HKEY_LOCAL_MACHINE> SOFTWARE> Policies> Microsoft> Windows NT> Printers> PointAndPrint, have a value of zero:
- NoWarningNoElevationOnInstall
- NoWarningNoElevationOnUpdate
We remind you that 0Patch has an unofficial patch that does block these computer attacks. However, if we have installed the Microsoft patch (which is useless), it modifies the «localspl.dll» library , so the 0Patch patch stops working. Great care.
Now we can only wait until next week, Patch Tuesday, to see if Microsoft releases a second update with which to try to mitigate these PrintNightmare vulnerabilities. And if this second update really does any good.