pfSense is the most widely used firewall-oriented operating system at a professional level, both in the home environment with advanced users, and in small and medium-sized companies to segment their network correctly and have hundreds of services available. pfSense is based on the popular FreeBSD operating system, therefore, we will have the guarantee that it is a stable, robust operating system, and, above all, very secure. Unlike other firewalls, pfSense has a really complete and very intuitive graphical interface, since we will have a short explanation of each parameter to configure. Today in this article we are going to explain everything about pfSense, and how to install it on any computer with two network cards (one for WAN and one for LAN).
pfSense is an operating system that consumes very few resources, however, depending on the use, the users who are going to transfer data, and the services that we install, we will need to have more or less CPU power and also RAM memory size. This operating system can be installed on practically any current computer, but logically, the performance that we will obtain will depend on the hardware, and the same happens with the configuration that we have made to the firewall itself. The most critical thing for pfSense is to recognize Ethernet network cards, the most recommended to avoid problems are Intel, but there are many other manufacturers that are also compatible, but first it would be advisable to read in the official pfSense forums.

Main features
The main objective of the pfSense operating system is to provide security for home and business environments, this equipment acts as a firewall, but we can also use it as the main router, since we have hundreds of advanced configuration options. Thanks to the possibility of installing additional software, we can have a powerful IDS / IPS (Intrusion Detection and Prevention System) such as Snort or Suricata. To use pfSense it is mandatory to have two network cards, one for the Internet WAN and the other for the LAN, although if we have more cards (or a card with several ports) much better, because we can have additional physical interfaces to configure a DMZ, an additional network and much more.
Another point in favor of pfSense are the continuous updates that we have, both of the base operating system, as well as all the packages that we can install additionally. In a firewall / router that is exposed to the Internet, having updates is very important to avoid security vulnerabilities that could be found.
Firewall and IDS / IPS
pfSense uses a rule-based SPI (Stateful Packet Inspection) firewall, as usual. We can filter packets quickly in a very advanced way, depending on the hardware, we can achieve bandwidths greater than 10Gbps. Thanks to the graphical user interface, we can create “aliases” to create groups of IPs and ports, to later apply it to the rules, and in this way, not have hundreds of rules in the firewall, it is very important to know what we are filtering and keep the rules properly updated. Of course, pfSense has advanced records of whether a rule has been executed, and everything that is happening in the operating system.
pfSense not only has a powerful firewall to mitigate and / or block DoS and DDoS attacks, but it also has an advanced IDS / IPS such as Snort and Suricata, which we can install easily and quickly through the available packages. for its installation, and in both we will have a graphical user interface to configure the different interfaces where they must act, as well as all the rules we have to detect possible attacks. We can also detect information leaks and even suspicious activity on the network that we can block. Of course, we also have the possibility to see the status of the operating system in real time, and even install additional software to view advanced graphical reports and know everything that happens in the system.
VPN
Virtual private networks (VPNs) are usually placed on the firewall itself, so as not to have problems with NAT and filtering from other firewalls. Having a VPN server or VPN client will allow us to interconnect remote locations through the Internet safely, and also connect different devices to the local network in remote access VPN mode. pfSense incorporates different types of VPN to perfectly adapt to the needs of users:
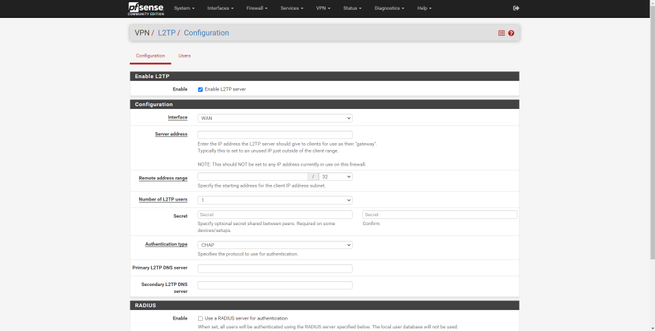
- L2TP / IPsec
- IPsec IKEv1 and IKEv2, with different types of authentication such as Mutual-PSK, Mutual-RSA and even Xauth.
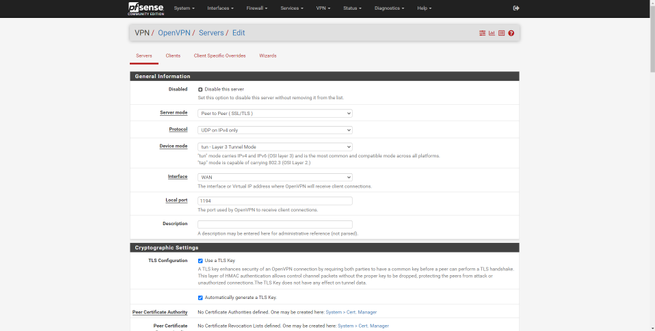
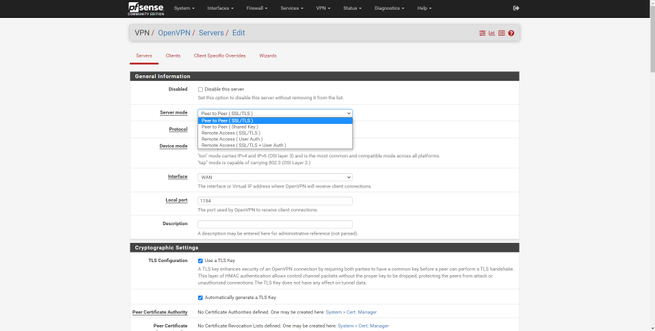
- OpenVPN with authentication by digital certificates, user credentials and more.
- WireGuard
The highlight of pfSense 2.5.0 is the incorporation of the popular WireGuard VPN, both to connect users remotely, and to make Site-to-Site tunnels quickly and easily, thanks to this new protocol that has been integrated into the kernel and it will give us great performance.
Other features
pfSense incorporates a huge number of services, the same or more than routers and other professional firewalls. For example, some of the main additional features are the possibility of configuring a DNS server with DNS Resolver, ideal for the firewall itself to resolve all requests, we also have a complete DHCP server with dozens of advanced options, an NTP server to serve the time to different devices, WoL, QoS to prioritize different equipment, Traffic Shaper, compatibility with VLANs, possibility of configuring different VLANs in one or several interfaces, possibility of configuring QinQ, Bridge and LAGG with different advanced options, we can also use the Dynamic DNS server and much more. We must not forget that, being a very advanced operating system, we can see a complete record of everything that is happening, and we will even have notifications by email or Telegram to be aware of everything that happens.
One of the most important features is the possibility of installing additional packages to have even more functionalities, thanks to this additional software, we will be able to expand the functionalities of this professional firewall. Some of the most popular extensions are:
- arpwatch to notify us by email or Telegram which new devices have connected
- bandwidthd to view graphs of bandwidth utilization
- freeradius3 to mount a RADIUS authentication server, ideal for configuring WiFi APs and having WPA2 / WPA3-Enterprise
- iperf to measure bandwidth to and from pfSense
- nmap to perform port scanning
- pfBlocker-ng to block all advertisements, and also malicious domains and IP addresses
- Snort and Suricata: the two IDS / IPS par excellence, they do not come by default but can be installed
- Haproxy for balancer
- Squid to mount a proxy server.
- nut to monitor UPS systems
- Zabbix agent for easy integration into a monitoring system
- Zeek (former Bro IDS)
pfSense works on x86 architecture, being compatible with recent 64-bit CPUs, in addition, it can be installed on almost any cloud platform such as Amazon Cloud, Azure and more, in addition, we must bear in mind that today we can buy equipment from the manufacturer Netgate that already come with pfSense pre-installed, with equipment oriented to professional field.
Download and install pfSense
The download and use of pfSense CE is completely free, just go to the official website and go directly to the “Download” tab.
Once we have clicked on «Download», we will see a section where we will choose the architecture to choose, we select AMD64.
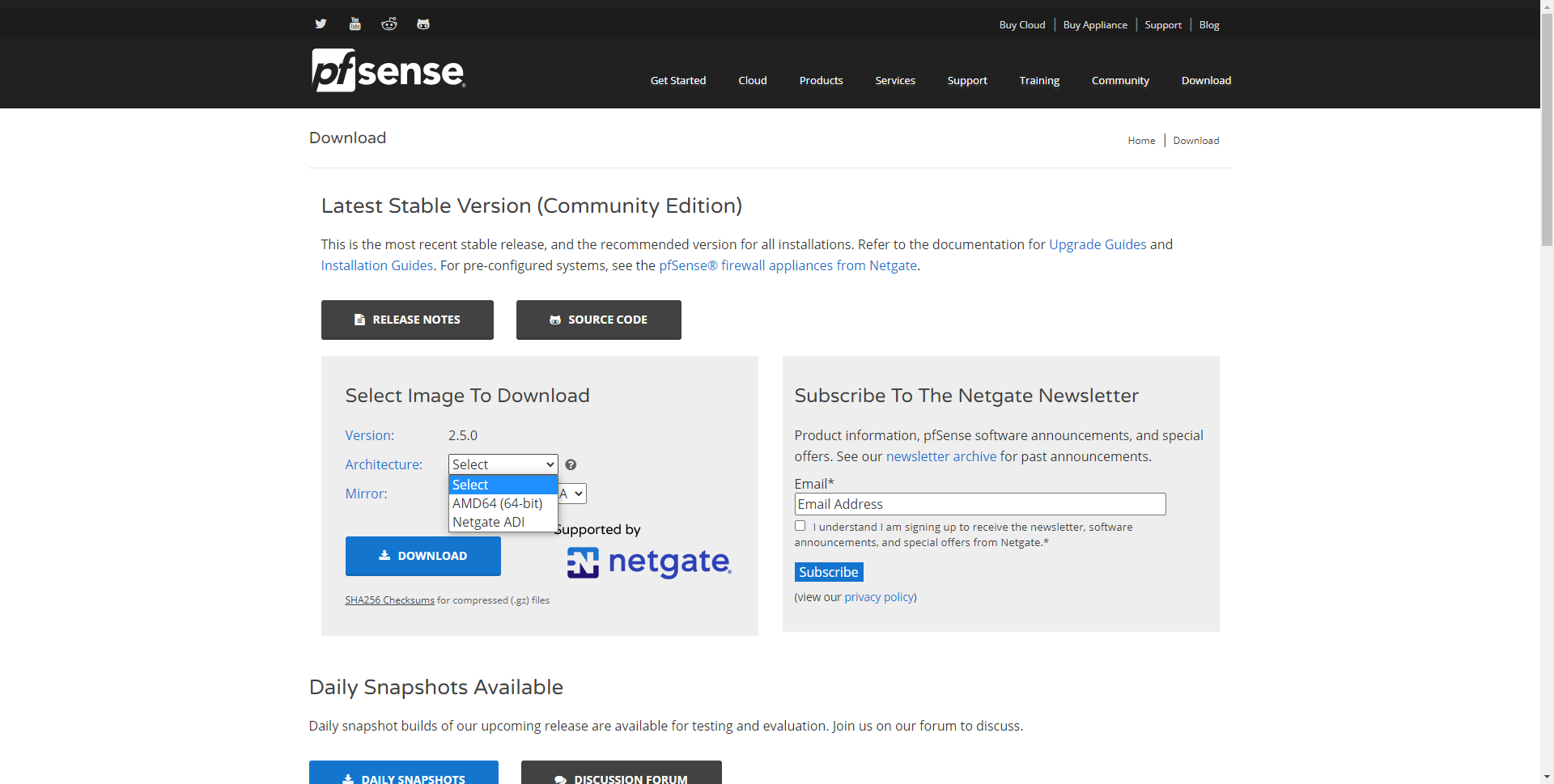
We also have to select the type of image, if we want an ISO image to copy to a DVD or pendrive, or directly a USB image, we have selected the ISO DVD image. Next, we must choose the server from where to download, it is recommended that it always be the closest physically to your current location.
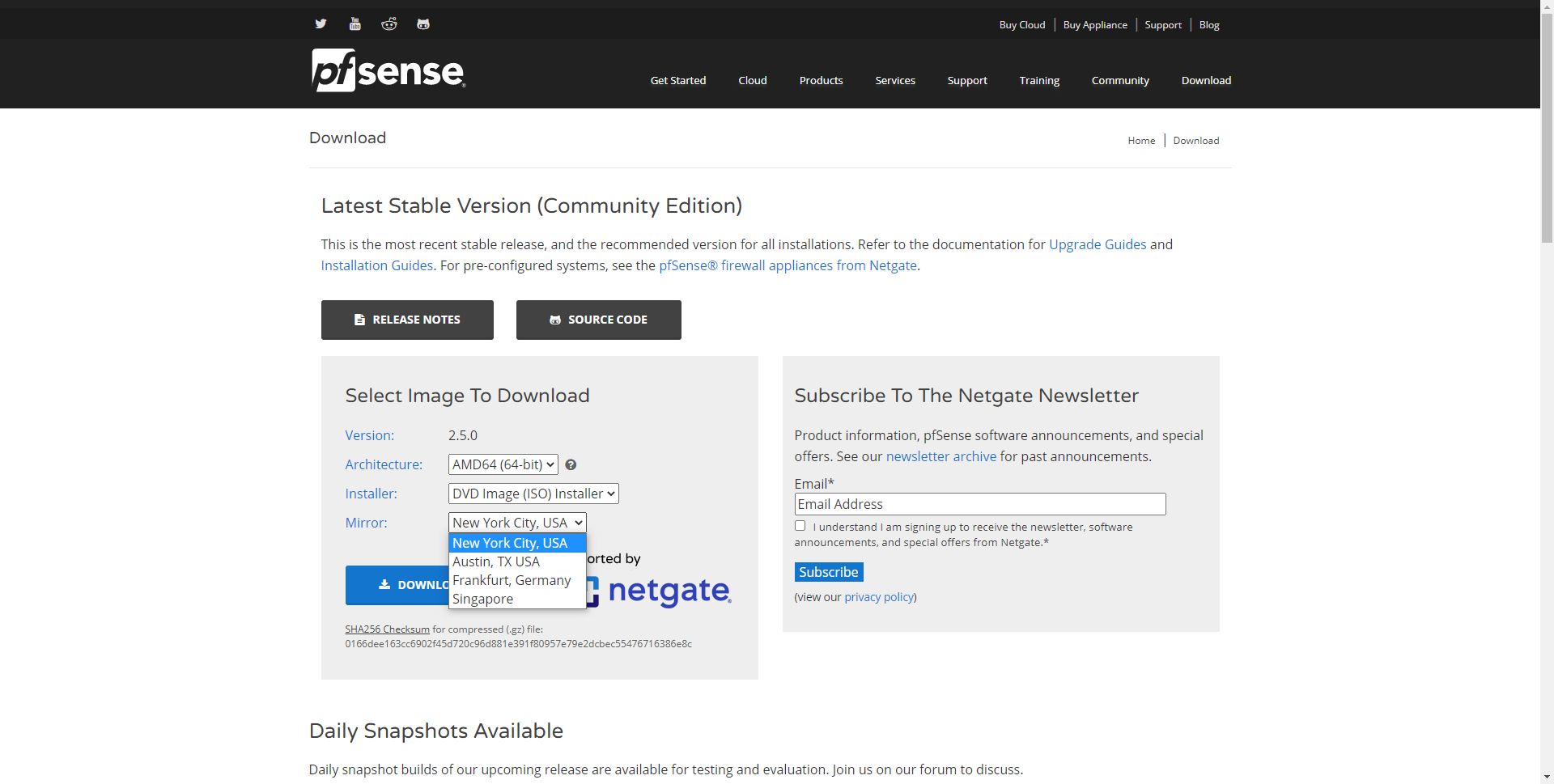
Once we have downloaded the image, we must unzip it since it comes in iso.gz format, and we must extract the ISO image directly.
Once we have downloaded it, we can burn it to a CD, copy it to a bootable USB with Rufus etc. In our case, we are going to install pfSense in a virtual machine with VMware, so that you can see how to install it in a virtual way and test it in a controlled test environment, to later move it to production. In the tutorial you are going to see how to create two network cards, one in bridge mode to connect to the real local network, and another in host-only mode to be able to access via the web from our computer, without depending on the local network.
Virtual Machine Configuration in VMware
In our case we are going to use VMware Workstation 15.5 PRO, but any version would be used to install this firewall-oriented operating system. The first thing we have to do when opening VMware is to click on «Create a New Virtual Machine», as you can see in the following screen:
In the VM configuration wizard we will have to choose «Typical» creation, load the ISO image of pfSense, it will automatically recognize that the internally recognized operating system is FreeBSD 10 (although it really is the latest version), we continue with the wizard until we choose the one VM path, we leave the disk reserved for the virtual machine at 20GB, and finally, we will see a summary of all the hardware that this virtual machine that we are going to create will have.
Before finishing, we must click on ” Customize Hardware ” to increase the RAM to 4GB, increase the number of CPU Cores, and add an additional network card, and configure the network cards correctly.
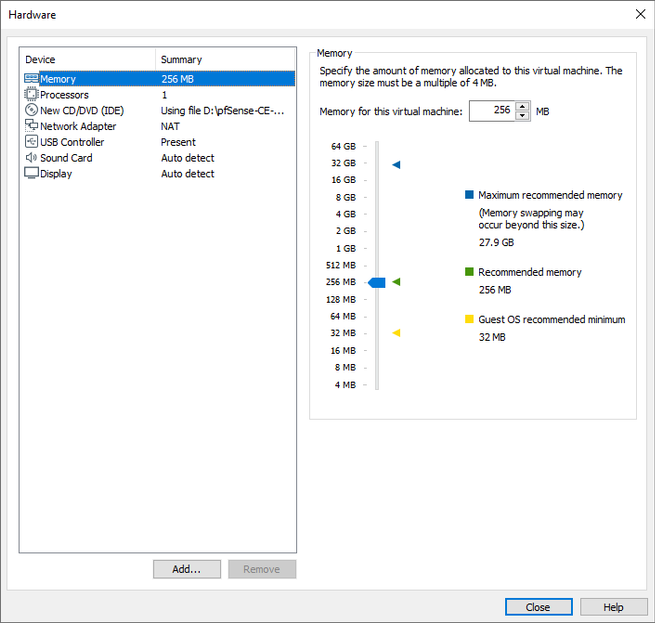
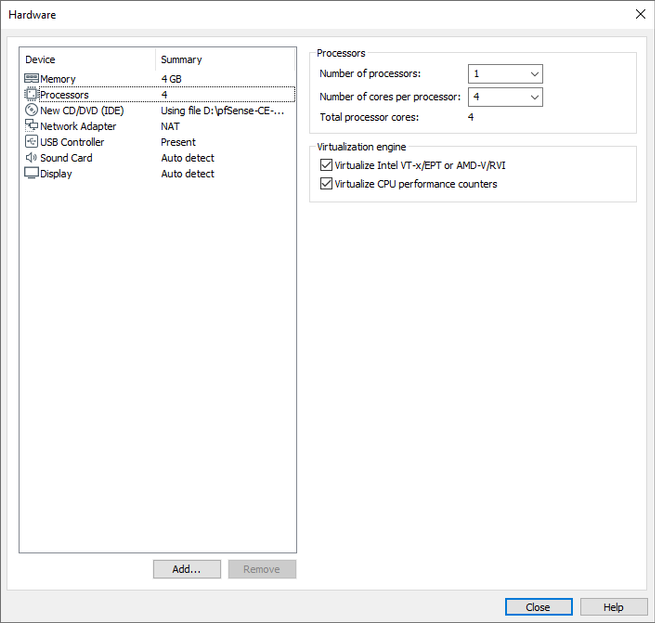
Regardless of the number of CPUs and cores (we recommend 1 CPU and 4 Cores), and RAM (we recommend a minimum of 4GB), we have to add a second network card, because we will have the Internet WAN and the LAN. We click on “Add” and click on “Network Adapter” to add it. We could also add additional cards to have more configuration options at the firewall level, but starting with a WAN and LAN is fine.
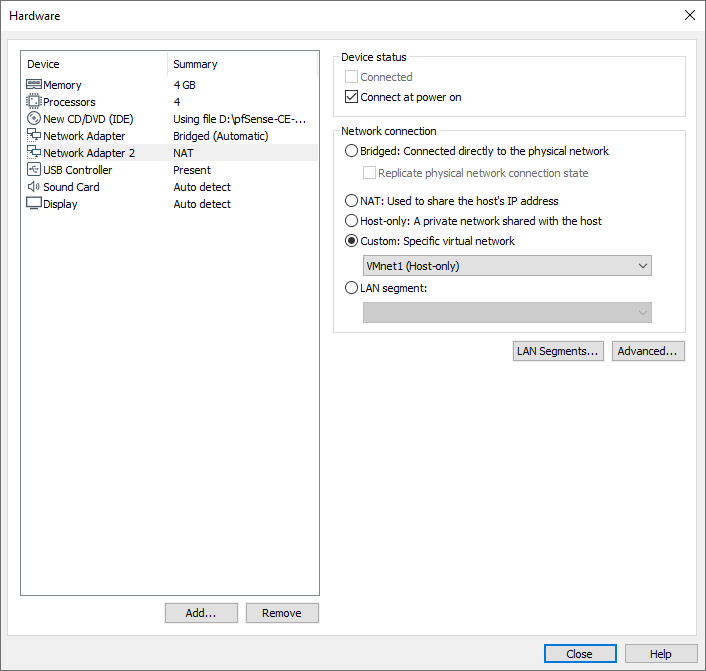
Once we have the two added, we will have to configure them as follows:
- Adapter 1: bridge (automatic)
- Adapter 2: custom VMnet1 (Host-only)
Next, you can see how this configuration would look.
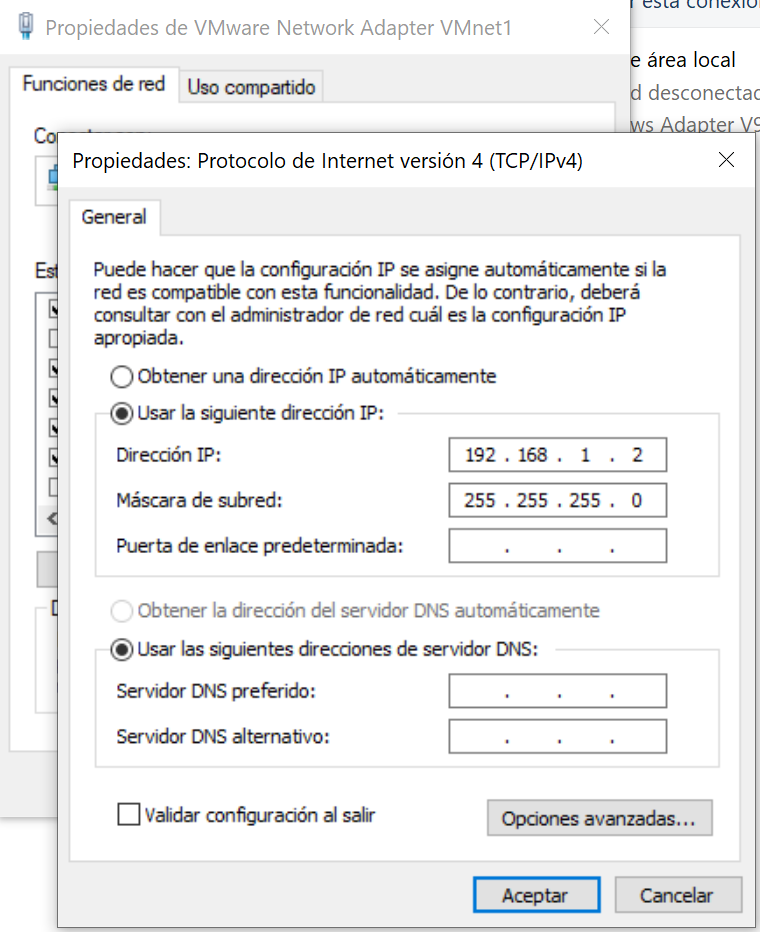
In order to access the operating system administration via the web, it is necessary to configure the VMnet1 adapter. To do this, we go to ” Control Panel / Network and Sharing Center / Change adapter settings ” and change the IP address to the adapter VMware Network Adapter VMnet1, putting the IP 192.168.1.2/24 as you can see below. Once done, click on accept and accept to exit the configuration menu.
Once we have everything configured at the virtual machine level, we can run the virtual machine to begin the installation.
Install pfSense on VMware
When we start the virtual machine, we can see a menu with several boot options, we should not touch anything and wait for the seconds to pass. Later it will load, and we will be able to see the different options that the ISO image gives us for the installation of pfSense.
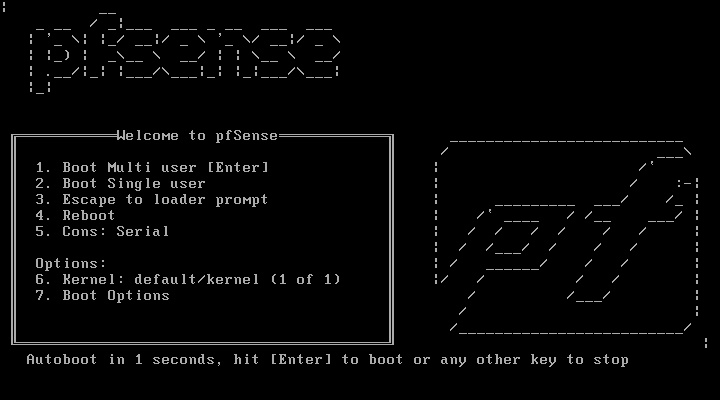
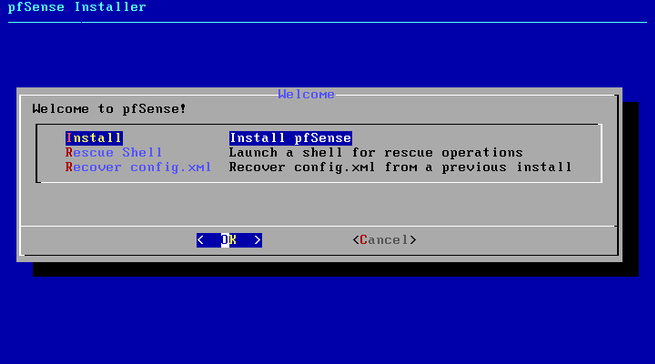
Once you start the installation of this operating system, you accept the copyright that it shows us. In the following menu we can install, recover the operating system in case of catastrophic failure, and also recover the configuration file config.xml from a previous installation. We will click on «Install» to install the operating system from scratch. In the next menu we will have to configure the keyboard, choosing our language and keyboard layout.
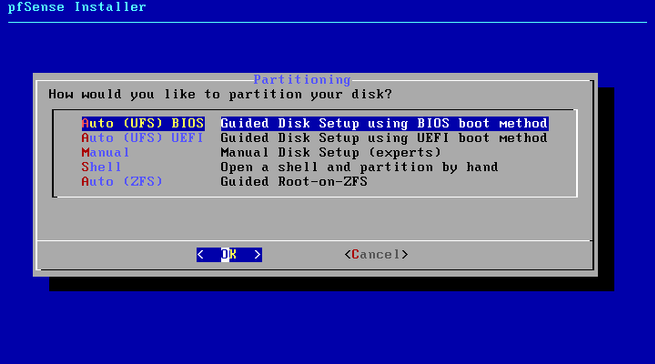
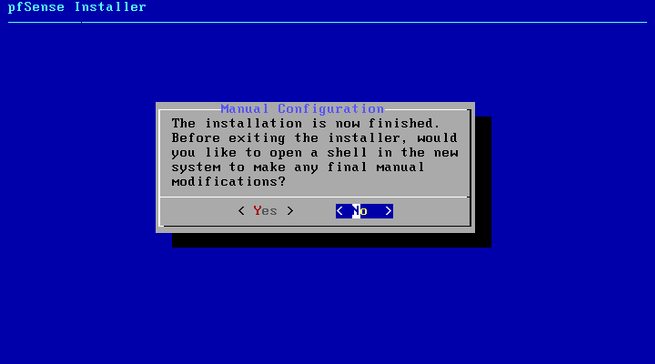
Then it will ask us how we want to install the operating system, if with UFS for BIOS or UEFI, manually for experts, open the console to do everything manually, or use ZFS as the file system. In our case, we have chosen the first of all, Auto (UFS) BIOS and we proceed with the installation. The installation will take about a minute, although it will depend on the hardware you have, when it finishes it will ask us if we want to launch a console to make specific configurations, we click on “No” and later it will ask us if we want to restart the operating system, and we accept.
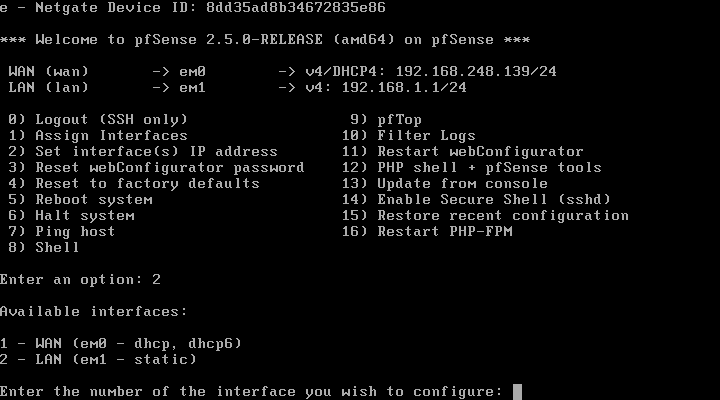
As soon as pfSense is started again, we can see that an IP has been correctly assigned to the Internet WAN and another to the LAN.
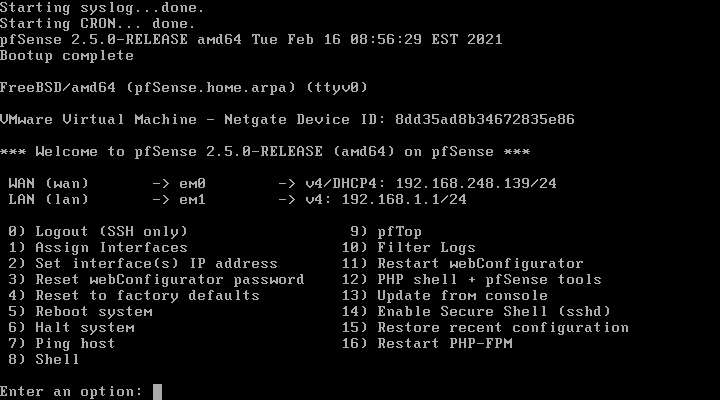
In the administration menu by console we can perform the following actions:
- Log out to SSH
- Assign physical interfaces to the WAN or LAN, it also allows you to configure VLANs for the Internet connection and even for the LAN.
- Configure the IP address of the different interfaces previously configured
- Reset the administrator password to enter via the web
- Restore pfSense to factory settings
- Restart the operating system
- Shut down the operating system
- Ping a host
- Launch a console for advanced command-based administration tasks
- Launch pfTop to see all current connections
- View the filtering operating system logs
- Restart the web server
- Launch console with pfSense utilities for quick settings
- Update from console
- Enable SSH in the operating system
- Restore a recent configuration
- Restart PHP-FPM in case we have problems accessing the operating system via the web.
If you want to configure the physical interfaces through the console, before logging in via the web, we can easily do it and even assign the corresponding VLANs:
Of course, we must carry out the configuration from scratch, assigning the corresponding interface to the WAN and the LAN:
Finally, we can configure the interfaces at the IP level, both on the WAN and on the LAN. However, this configuration is very basic, you can see all the available options via the web.
At that time, we will be able to access the pfSense configuration via the web, through https://192.168.1.1 with the username “admin” and password “pfsense”.
PfSense Configuration Wizard
To be able to access the pfSense operating system via the web, we have to enter the URL https://192.168.1.1 with username “admin” and password “pfsense”, the port is 443 by default for HTTPS, it is not necessary to use a specific port.
Once we have accepted the self-signed SSL / TLS certificate from pfSense, we will see the login menu, as you can see here:
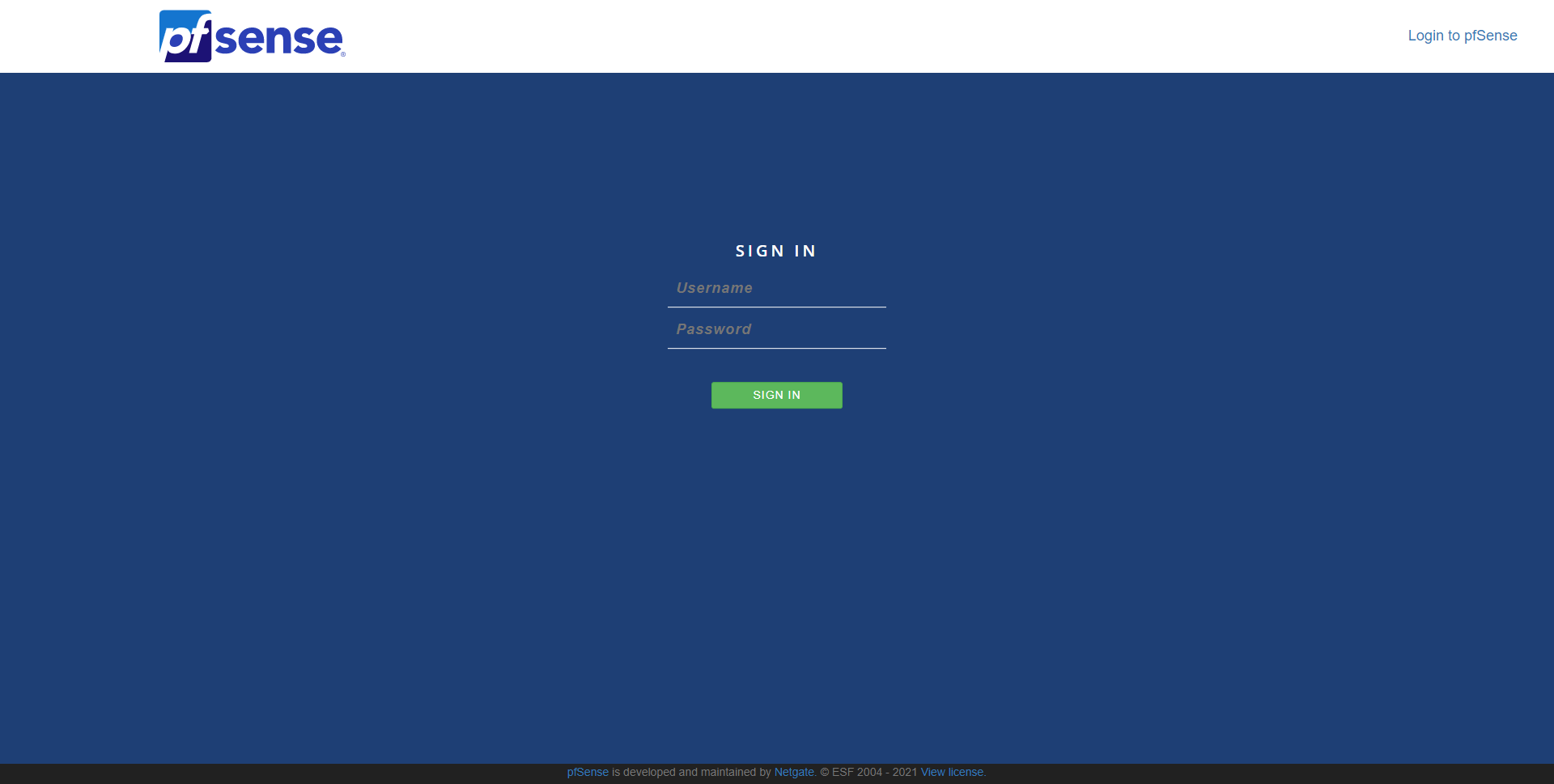
pfSense will provide us with a step-by-step installation wizard to carry out the main network configurations. We have the option of not doing it, but it is advisable to follow it if it is the first time we use it.
The first thing we will see in this wizard is the welcome, then it will indicate that we can buy a Netgate support subscription to help us make different configurations, we must remember that years ago Netgate was made with pfSense to continue developing it, both for their own teams as well as for the community. With version 2.5.0 we will have a division between both projects, each time they will bifurcate more (pfSense CE vs pfSense Plus).
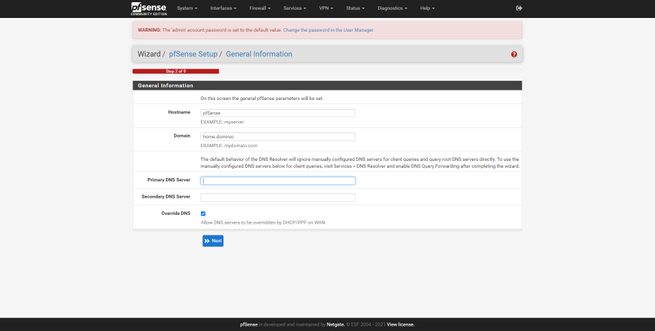
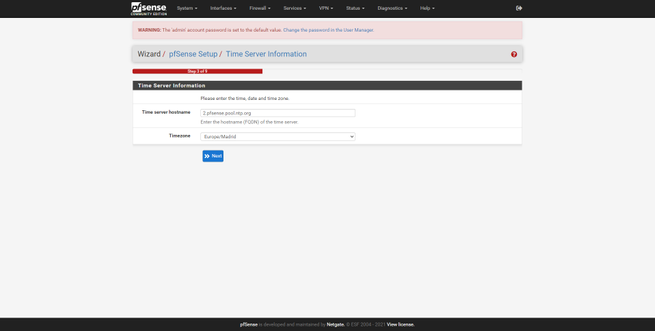
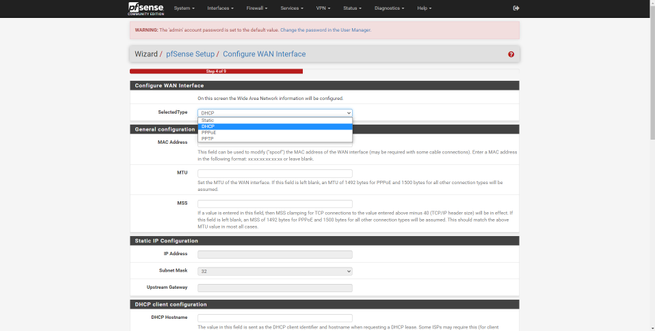
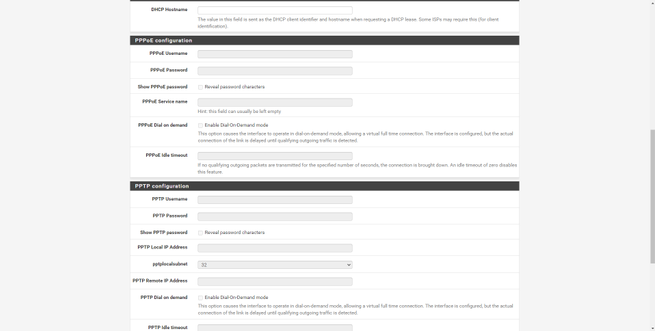
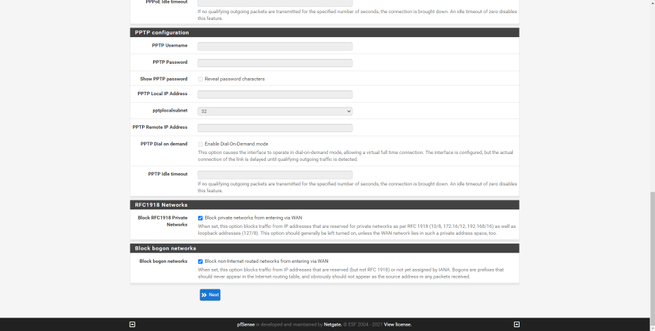
Next, we can see and configure the name of the host, domain, and DNS servers if we want to put others that are not those of our operator. We can also configure the NTP server to synchronize the time, and even the time zone. This pfSense wizard will help us to configure the Internet WAN interface, we have four possible configurations: Static, DHCP, PPPoE and PPTP, in addition, it supports VLAN ID for operators that need it. In this menu we can clone the MAC, configure the MTU and MSS, make specific configurations depending on the type of connection, and we can even incorporate automatic rules to the firewall to avoid attacks on the networks.
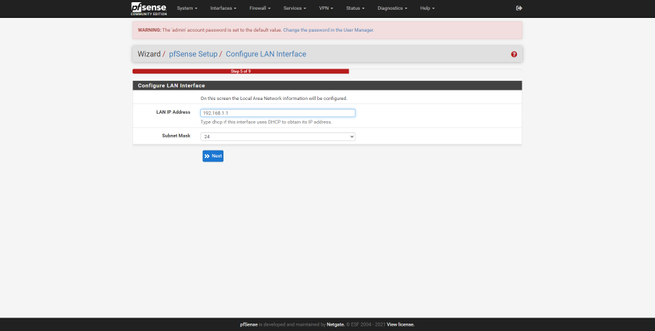
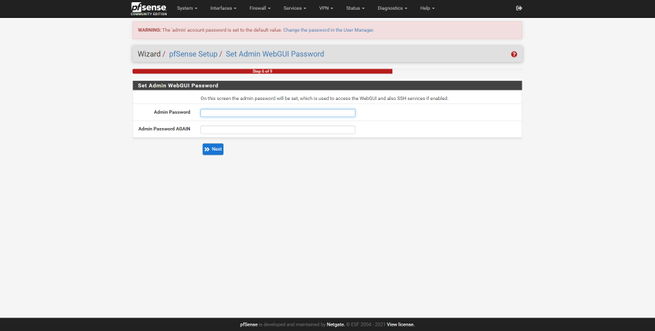
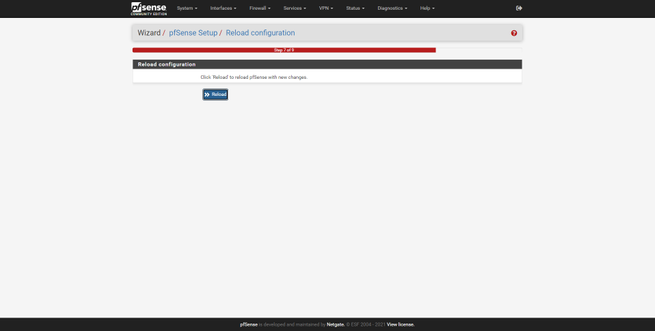
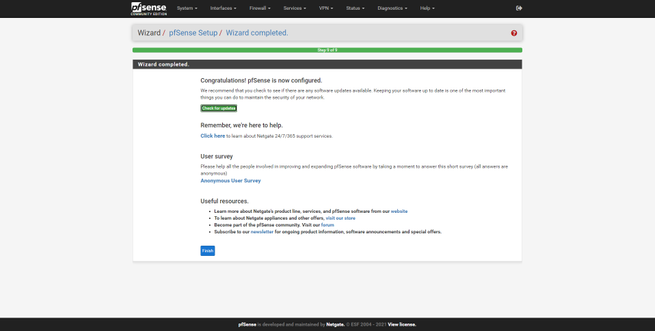
We can also configure the LAN interface, by default we use 192.168.1.1 but we can choose the one we want, in addition, we can also configure the subnet mask. Another very important option is to change the default password, pfSense will invite us to change it to be protected. Once changed, click on “Reload” to continue with the configuration wizard and finish it, it will give us congratulations and we can begin to configure this complete firewall in an advanced way.
Once we have seen the web configuration wizard in detail, we are going to fully enter all its configuration options.
PfSense Management Options
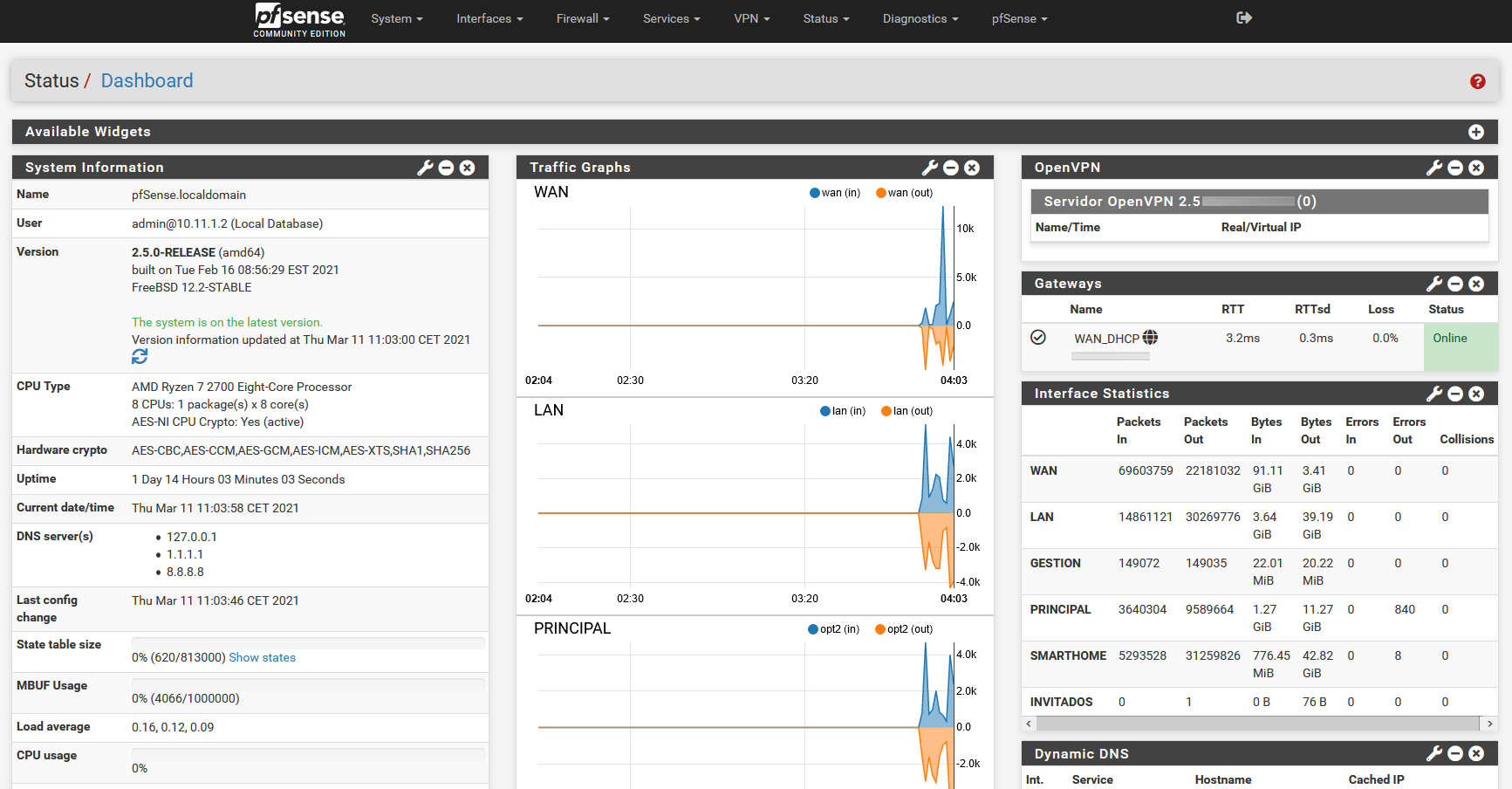
In the main menu of pfSense we can see the system information, the name of the pfSense, the user who has logged in, system, hardware used and even the exact version of pfSense and what version we have of the base operating system (FreeBSD), we can also view uptime, current time, DNS servers and the status of storage, CPU and RAM. Of course, on the right side we will see the status of the network interfaces that we have configured.
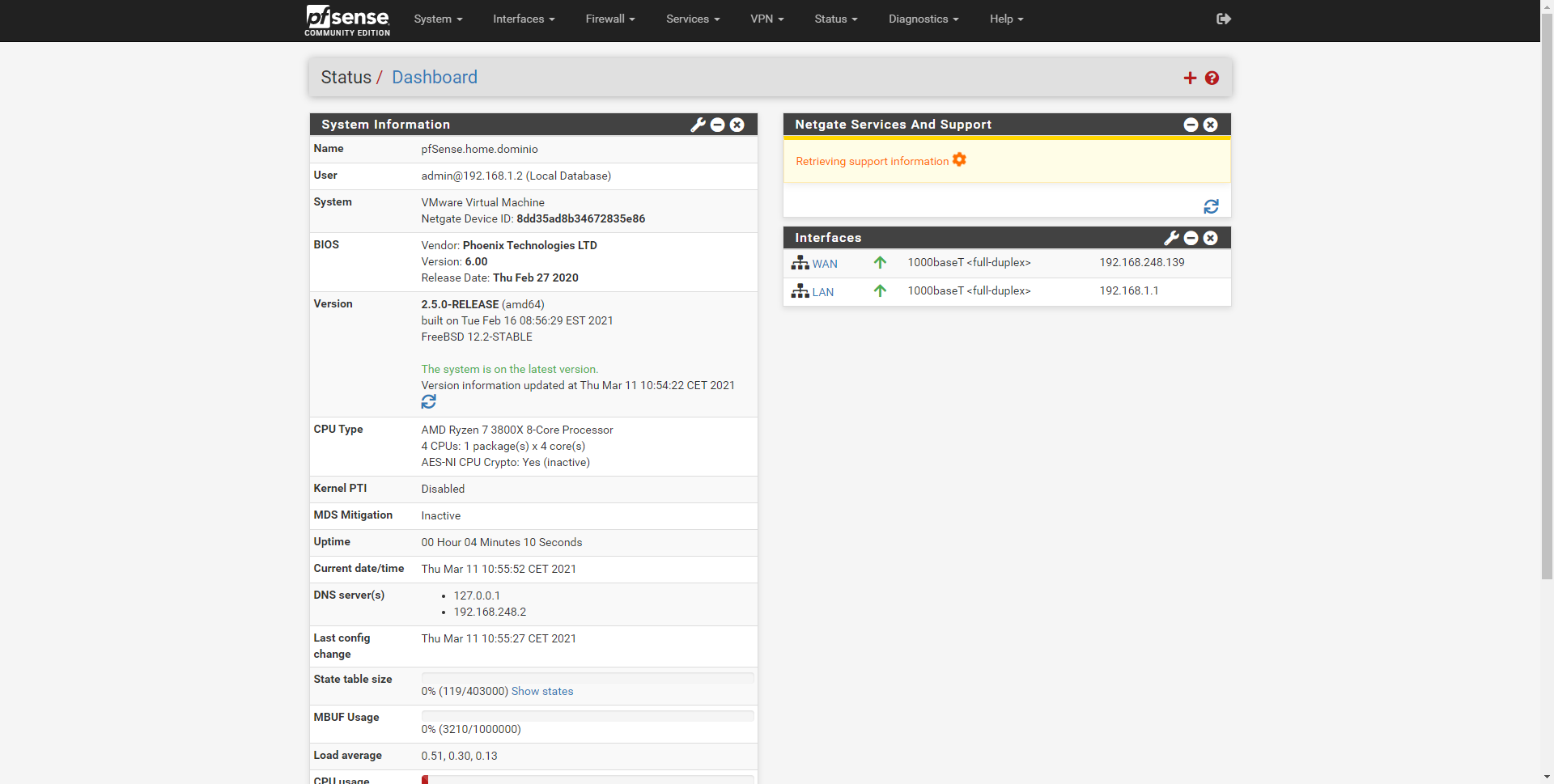
This main menu is very configurable, to have all the status of pfSense at a glance, we can add widgets such as the real status of the network interfaces, OpenVPN and IPsec, firewall logs and many others. This menu is highly customizable to adapt to the needs of the network and see everything at once.
Once we have seen the main menu, we are going to see the pfSense operating system part by part, without going into much detail in all the configurations because we have hundreds of possibilities.
System
The “System” section is where we can configure pfSense’s own web server, activate the HTTPS and SSH protocol, configure access security and login protection in detail. We can also configure global parameters of the firewall and NAT, we can also configure global parameters at the network level, both IPv6 and network interfaces, an important detail is that we can activate or deactivate “offloading” to accelerate performance if the hardware supports it. Other configuration options are to configure proxy, load balancing, and power saving features. Finally, we can configure base operating system parameters at a low level, and configure notifications by email and Telegram (a novelty in the latest pfSense 2.5 version).
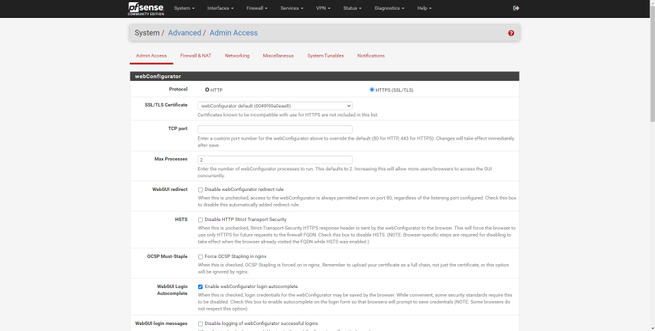
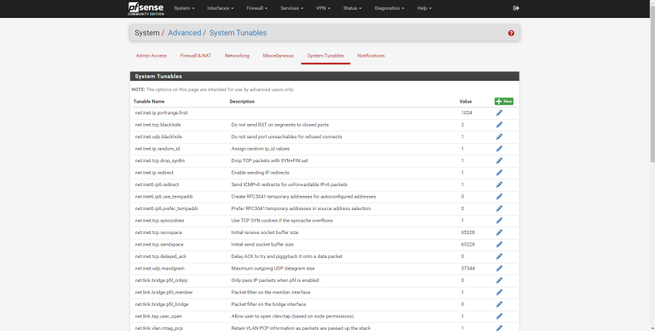
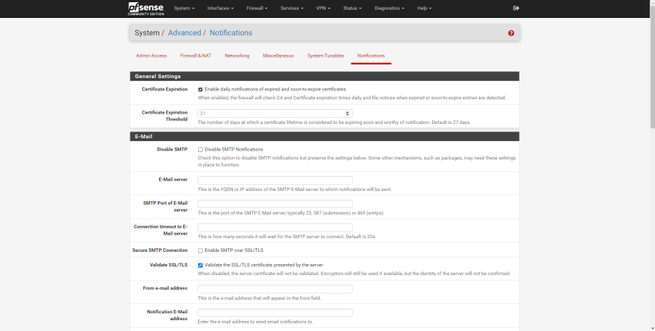
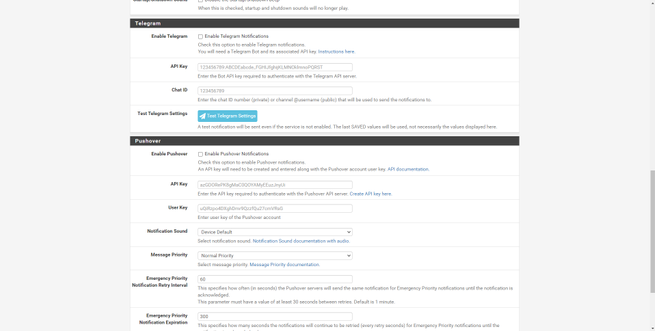
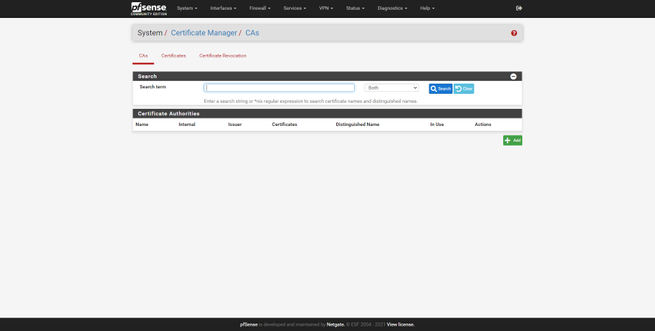
In this section of «System» we will also have a digital certificate manager, we can create a CA and server and client certificates easily and quickly, with the aim of later using it on VPN servers such as IPsec or OpenVPN, as well as on the server RADIUS Freeradius that we can install as an option. This certificate manager will allow us to create certificates based on RSA and also on EC with different algorithms.
In the “General Setup” section we can change the name of the computer, the domain, the DNS servers to configure so that the clients can use them later, the location (time zone and NTP server), and we can also configure the appearance of pfSense by having of different subjects. This last part is interesting to modify the graphical user interface with a dark pfSense or directly other themes that we like more. We can also configure HA to have high availability and even install a large amount of additional software, since we will have in the “Package Manager” section a large number of plugins to extend the functionalities of pfSense.
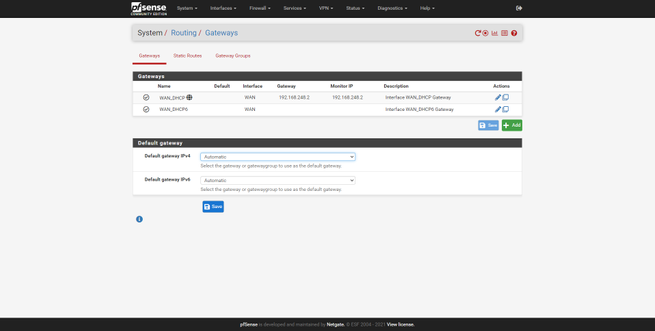
In the “Routing” section we can see the different gateways registered, the possibility of configuring static routes to reach other networks, and even create a group of gateways.
pfSense allows updating through the operating system itself, as soon as it detects that there is a new version, we can update it through the graphical user interface, without having to download the ISO image and perform the update manually.
Being a very complete operating system, we can create different users and groups with different permissions. For example, we can create a list of local users to authenticate via SSH in the system, or to make use of a specific VPN. We can also configure an authentication server with RADIUS or LDAP, to make use of those users that we have.
Once we have seen the “System” section, we are going to go to “Interfaces” to see everything we can do.
Interfaces
In the “Interfaces” section we can see the assignment of the WAN and LAN with the different physical interfaces, from here we can easily configure the different physical and logical interfaces, since we can configure VLANs and later assign it to a virtual interface. Other configuration options that we can do are create groups of interfaces, configure WiFi, QinQ, PPPs, GIFs, Bridges or bridges, and we can even create a LAGG with different algorithms (LACP, Failover, LoadBalance and Roundrobin).
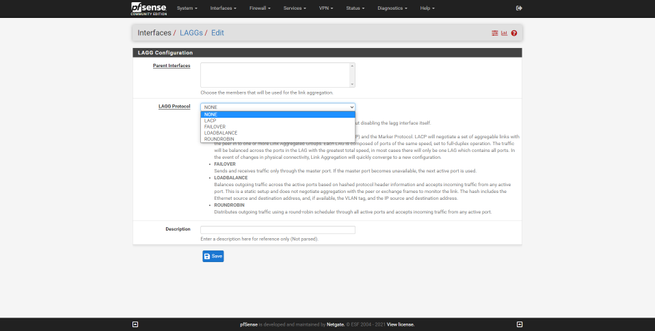
Let’s imagine that our operator makes use of VLAN ID 6 to provide us with Internet, as it is the current configuration of the WAN will not work. We must create a VLAN ID 6, and later apply it to the Internet WAN. If in the professional local network we have different VLANs and we want to intercommunicate between them, we can also do it with pfSense, registering the different VLAN IDs and later creating virtual interfaces that “hang” on the LAN.
If we go into the WAN or LAN configuration, we can see the configuration that has been made in the installation wizard that we saw previously. In the WAN menu we will have different types of configuration for the connection, the same happens with IPv6, and we can even put the MAC address that we want. We can also configure the MTU and MSS, in addition to configuring advanced parameters of the DHCP client.
Regarding the LAN, the normal thing is to have the configuration in “Static IPv4” and later activate the DHCP server, of course, here we must also configure the gateway for the clients that connect, which is the IP address itself.
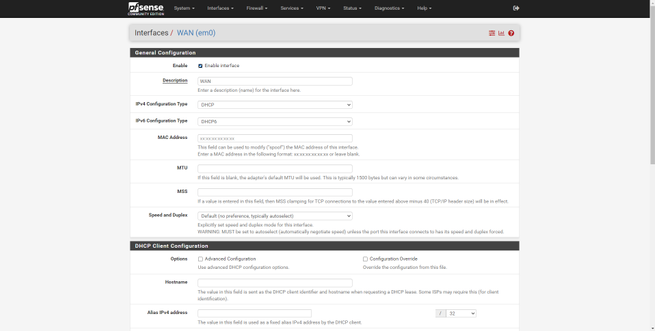
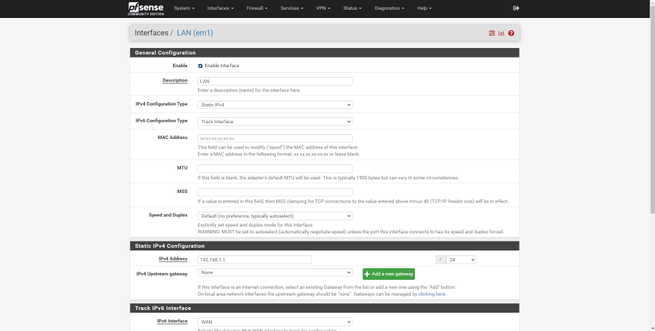
Once we have seen all the configuration options for “Interfaces”, we will briefly see the firewall options.
Firewall
In the “Firewall” section is where we have to configure all the firewall rules. In the “Aliases” section we can create an alias to apply a rule to a set of IP addresses, ports and also URLs. This is ideal to have the rules very well organized in the firewall, it is very important to have a certain order to have the best possible performance (the most used rules at the top, and the least used at the bottom), in addition, the More specific rules should be at the top and more general rules at the bottom for proper operation.
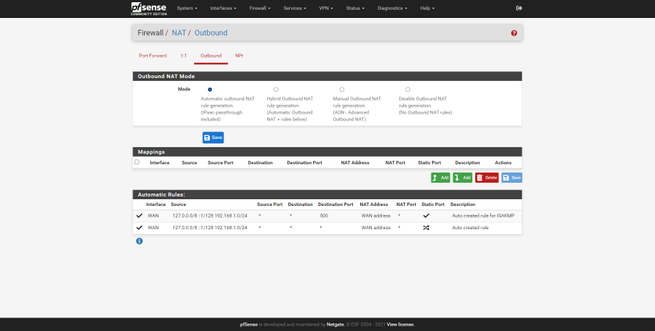
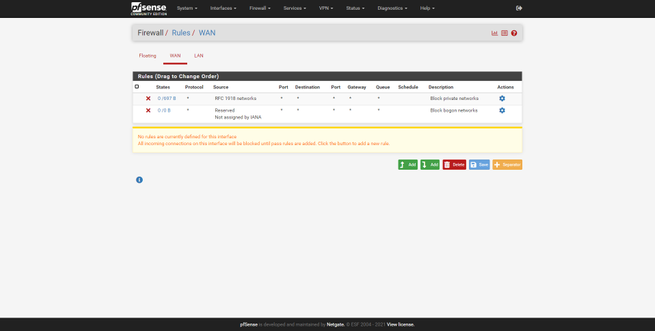
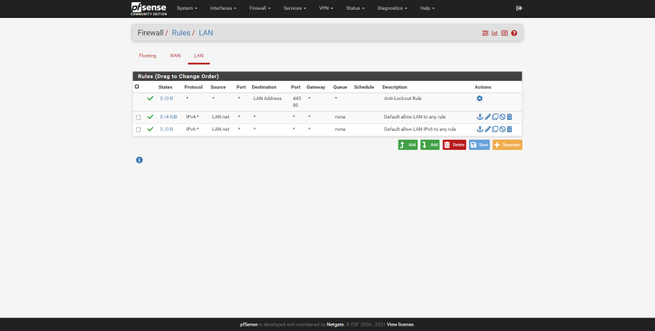
We will have the possibility to configure the NAT rules in Port Forward, we can also configure the 1: 1 NAT, the Outbound NAT rules and even the NPt for IPv6. The “Rules” section is where we will create the different allow or deny rules in the different network interfaces that we have in pfSense. We will create these rules through the graphical user interface, and we can define dozens of advanced parameters and using different protocols, we can drag to move the rules from one position to another, and even add separators to help us identify a set of rules.
By default, in pfSense we have an “deny all” at the bottom implicitly, therefore, to have traffic you will need at least one allow rule.
Other interesting features are the possibility of creating «Floating rules» in different interfaces in an easy way, to have the repetitive rules well ordered, and even temporary rules that are active at a certain time, and the possibility of configuring «Virtual IPs» to use. the pfBlocker-ng, for example. Finally, we will also have here the “Traffic Shaper” per interface, per queue, we can configure bandwidth limiters and even run a configuration wizard.
Services
The “Services” section is where we will have available all the services that come by default in pfSense, and even the services that we have installed additionally through the package manager. In this section we can find a tool to make backups automatically, configure the captive portal of pfSense, configure the DHCP and DHCPv6 server for the LAN.
One of the most notable services is the DNS resolver, which is the DNS server of pfSense itself, and which we can configure with DNS over TLS and have very specific rules for clients, we can make advanced configurations, such as defining different DNS servers for the different rules.
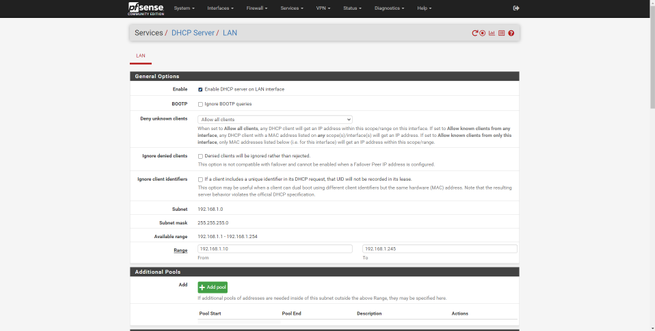
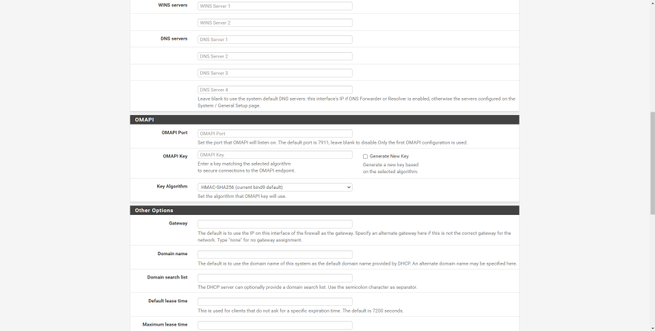
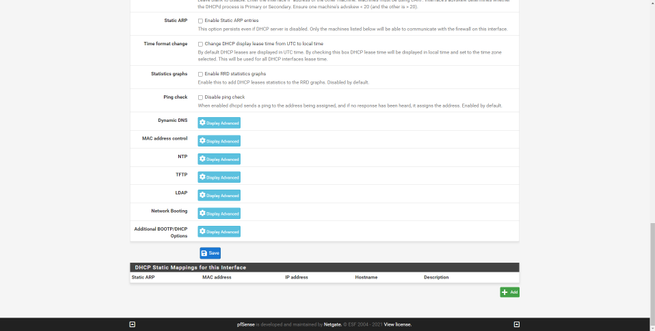
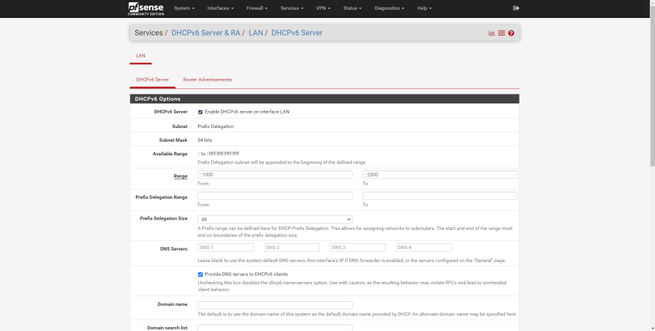
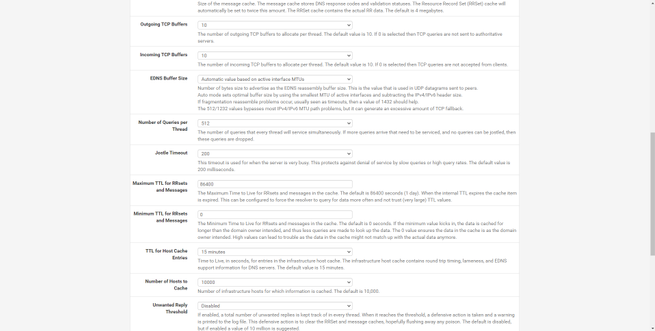
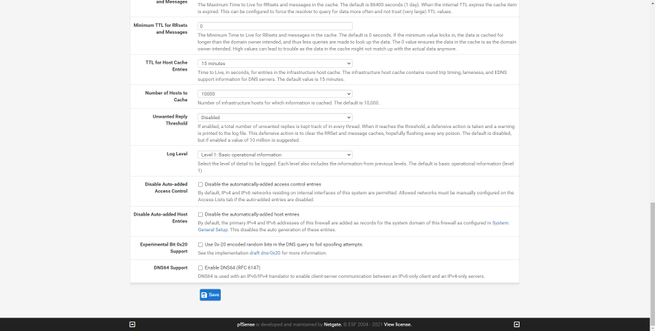
Other services available in this section are the dynamic DNS service, the IGMP Proxy, the NTP server to provide the time to the different computers, the PPPoE server, the SNMP protocol to monitor this firewall remotely and even the UPnP / NAT-PMP protocol. to open ports automatically and dynamically, the Wake-on-LAN (WoL) to wake up computers on the local network.
Once we have seen several services incorporated in pfSense, we are going to go directly to the VPN section.
VPN
This firewall-oriented operating system supports most of the VPN protocols that currently exist, we have L2TP / IPsec, IPsec, OpenVPN and also WireGuard. Taking into account that it is aimed at professional use, we have all the available configuration options and existing types of authentication. We can create remote access type VPNs and also Site-to-Site.
Depending on the needs of the users and the company, it will be advisable to configure and build the tunnel with one type of protocol or another, the novelty of pfSense 2.5.0 onwards is the incorporation of WireGuard natively, although in previous versions also it was supported by doing a “manual” installation. Thanks to the addition of WireGuard and the latest versions of OpenVPN, we will have all the latest improvements in security and performance.
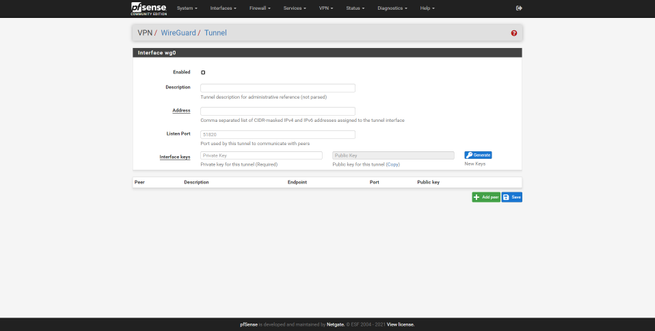
What we like the most about pfSense is that we can configure a VPN from scratch without having to edit complicated configuration text files, everything can be done through the graphical user interface.
Status
The “Status” section is where we can see the global status of the firewall, see the logs of different areas of the operating system, see the status of the interfaces, the status of traffic, CPU and RAM usage and the status of all the services that we have in use in the operating system. Something that we like a lot about pfSense is that very rarely we will have to enter via SSH or through the console to see logs, everything is found in the graphical user interface itself via the web.
In this menu we can see the status of the captive portal, CARP, main dashboard, status of DHCP and DHCPv6, status of DNS resolver, gateway, interfaces, Ipsec and OpenVPN VPN tunnels, monitoring of different interfaces, services, and even view a real-time graph of traffic, among other options. Depending on the additional software you install, these options for displaying the status of different services may increase.
Diagnostics
In the «Diagnostics» section we can see the ARP table, authentication, backup and restore, do a DNS Lookup, edit files manually, restore the operating system to factory settings, shut down and restart the system, see the NDP table, run the traffic grabber to detect problems, run pfInfo and pfTop to view current connections, ping and tracert, view SMART status, perform a port test, and much more.
As you have seen, pfSense is an operating system that we can use as a firewall and main router, both at a domestic level when we have extensive knowledge, as well as at a professional level in small and medium-sized companies. Thanks to the great stability we have in the operating system, and to the large amount of additional software that we can install, this system becomes one of the best to use as a firewall / router.