Currently, most users have a huge concern for personal security. There are many news that can be read in different media about cyber attacks, or attempts by hackers to access personal information. The Mac is a computer that can be susceptible to this type of attack, and hackers will want to access your information or even infect it so that it suffers some problem. In this article we are going to talk about the security and privacy you have on a Mac and the tips to avoid future problems.

Risks your Mac will face when you use it
A Mac can be used in two ways: offline or connected to the Internet network. The first of the methods makes it impossible for you to browse the Internet in search of information or download files. Above all, the fact of not being able to access the information that you may have stored in the internet clouds stands out. But not having your computer connected to the internet is the way to significantly reduce all risks . You will not download any suspicious file nor will you visit content that is compromising. In this way, if you want to practically reduce the risks, you should not connect them to internet networks, be it Wi-Fi or a cable connection with Ethernet.

The risks, as we say, begin precisely when you access the network. It is a fact that currently this is practically mandatory for many people. It allows you to make queries through the different search engines, and also access the documents you have on the network. In addition, it also offers the possibility of working with different third-party applications. But the risks in this case can be summarized in the following points:
- Download infected files of any malware or virus in general that can infect the Mac.
- Access to web pages that are not reliable to be able to work.
- Possibility of interacting with people who are not who they say they are. This is something above all a danger focused on the smallest of the house.
- Leakage of data by the Mac to a third party without your authorization.
Does Apple sell your personal data?
Beyond device security, privacy is also really important. Keep in mind that you are entering a lot of personal data on this device on a daily basis. The first thing that comes to mind is the information you enter into Safari, such as your name, address, or even bank details . Likewise, you also have access to your internet history that identifies your personal tastes. What you like to eat, where you would like to travel or what your search intentions are. This is really valuable information for many people who are dedicated to digital marketing. To this we must add the information you have in the Apple cloud on which you trust all your trust to be able to have your files safe.

There are many technology companies that make use of all this data. But not to help users, but to be able to get an economic return. In the case of Apple, all this data is safe. It is known to all that the company does not have a business base with the privacy and search data of users. What has been repeated on numerous occasions is that the Cupertino company bases its business on the sale of hardware and software itself.
This may seem unimportant, but it is vital to take it into account when evaluating Apple on privacy issues. If you use a Mac, your data will be fully protected in this regard. You should not be afraid of data migration to third-party servers. This also applies to third-party apps found in the Mac App Store. These policies and very strict reviews are applied in order to achieve the full security of the users.
Basic tips for staying safe
Obviously, the normal thing for any user is to have the computer connected to the network. This means that, as we have mentioned before, the Mac assumes many more risks, especially if you are going to surf the net for many hours and download different files.
Keep the operating system up to date
At first, updates may be thought to be negative for the overall user experience. But the truth is that during the day to day of the users and also the developers , different performance or security problems can be detected . Currently, there are many work teams whose main mission is to track down these security holes in the software. These periodically will send a report to Apple with all the problems that are detected.
The mission of Apple engineers in this case is to analyze security bugs. Some of these are about not being made public until they are completely fixed. And it is that the solution arrives precisely through an update of macOS . This makes it really important to have the latest version available from Apple installed. It is a reality that most of these security problems are not shown in the update notes, precisely to prevent them from being exploited until they are fully resolved.
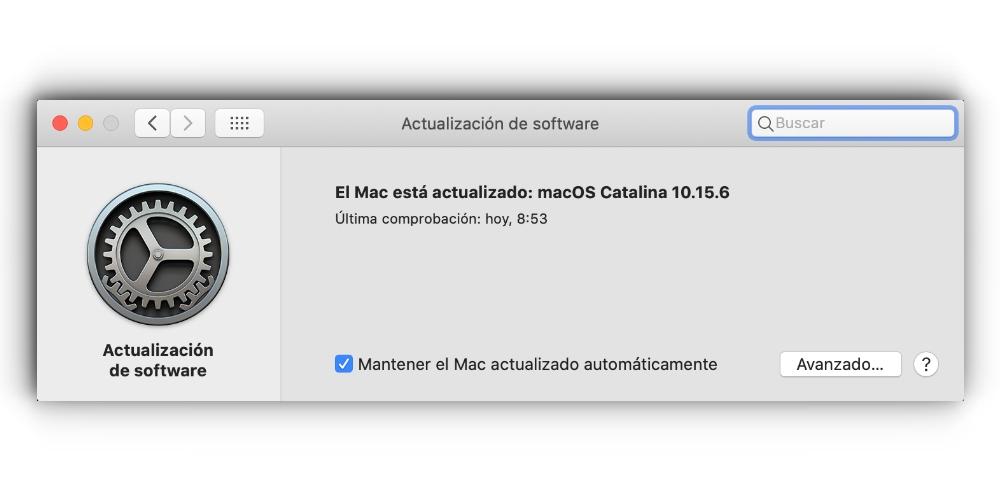
The way to know if there are new updates is to perform a periodic search through the corresponding panel in the System Preferences. But you will also be able to receive information from specialized media. The really important thing is that you don’t let these updates go by, and don’t make your software completely outdated.
Do not connect unknown accessories
But although we have focused on the internet connection, there are other risks that can occur even if you are working offline. Accessories are a great danger for any Mac computer. Accessories can include many different products, such as external storage units, whether it’s a simple flash drive or a hard drive that you’re going to connect. In the event that you do not know its origin, it is important not to connect it directly to the system. This is because they can automatically load malicious software on your computer with a simple connection. From this moment there will be no going back.

This is something that can also happen with a simple peripheral that you are going to add to your computer. Therefore, the general rule is that you avoid connecting any device to the ports that your computer has. You should only do it if you fully know its origin, or if you yourself have bought it from a trusted establishment. Likewise, in storage units it is always interesting to carry out a first format in order to avoid major problems.
Avoid connecting to public networks
In the event that you have a MacBook laptop, you are probably always looking for the internet to be able to work when you leave home. There are many establishments that have Wi-Fi networks that are completely open to customers. It can be tempting to go online when you don’t have to pay anything for the internet and start browsing and downloading files. This is something that is not recommended at all. It is necessary to have as a general rule that the tasks that you do with the internet connection at home cannot be done on public networks . The difference lies in security. Private networks have security measures that ensure that only you are connected. But in public networks you will share the internet with many other unknown people.
This means that if you run into any hackers on these public networks, your data may be completely at risk . The main thing to keep in mind is the information that is sent over the network with sensitive data such as bank passwords, addresses and also financial data such as payment card data. All this information is really compromised and anyone will want to have access to it at any time.

That is why we are always going to recommend that you do not connect to these types of networks that are open, even if you are really tempted. You have to know how to navigate with the greatest security so as not to run any kind of risk when doing something as simple as making a search or paying online.
Be careful where you write down your passwords
One of the recommendations when talking about internet security is specifically the fact of changing the passwords that are used in different logins. This means that Twitter and Facebook passwords should not be shared for security . This is basically due to the fact that if a hacker obtains your Facebook password, they will be able to access the rest of the services in the event that they are the same login data. That is why sometimes you have to make it much more difficult and complicate it a bit. This also adds to the need to use alphanumeric keys with special characters that are much more complicated to extract.

But the problem in the case of having really complex passwords is that you will not be able to remember them. That is why you will be tempted to have them written down in a simple Mac notepad and have it stored locally. This is a serious beginner’s mistake when it comes to cybersecurity. Any hacker who breaks into your Mac’s internal storage is going to have access to literally your entire digital life.
The recommended thing if you are within the Apple ecosystem is to opt for the keychain that is integrated into the system . It allows to have a complete integration with the Safari browser. In addition, it will be protected by password or your own fingerprint. But what you should not do is have all this fundamental data written down on a simple piece of paper or in a document that is stored locally. And if you’re not convinced by Apple’s default option, you can opt for third-party applications found in the App Store.
Keep the Mac webcam covered if you don’t use it
This is a really important aspect, since the webcam that is integrated into Macs or that you use externally is a window into your privacy. There are many malware that can be used to infect your computer and gain access to your microphone or camera . In an effort to improve privacy and security, macOS adds a small visual indicator to the operating system interface. This materializes in orange or green dots to know what is being used and specifically the application that is doing it.

That is why in general you are going to have to get used to covering the camera if you are not going to use it . In this way, even if the computer becomes infected, you will not be able to access the images of your private life. You should only uncover the webcam when you are going to use it to make a videoconference. You can use a simple adhesive paper, but you can also opt for a protector that allows you to cover the camera and that is found online.
The most specific measures to avoid risks
Until now we have been able to see different measures that are general to protect your security and privacy. But there are many other measures to take into account that delves into security and privacy. It should also be noted that there are also measures to be able to have a response to these failures.
Always use two-factor authentication
In order to preserve the security of Internet service logins, it is important to always have two-factor authentication active. This is defined as an additional layer of security for Apple ID and other services. This has been designed and implemented by numerous companies in order to ensure that you are the only person who can access your account, even if someone else has known your password. In this way, if a hacker has accessed your personal keychain, you will be able to guarantee that no one will access your personal information by requiring additional authentication.
The operation is really simple. It is activated automatically when you log in for the first time on a website. In this way , when sending the username and password, a verification code will also be requested. This will be sent to the devices that you have configured as trusted. This will be done mainly through a simple text message or also by email. Naturally, only you will have access to these trusted devices, so the security measure is perfect in these cases.
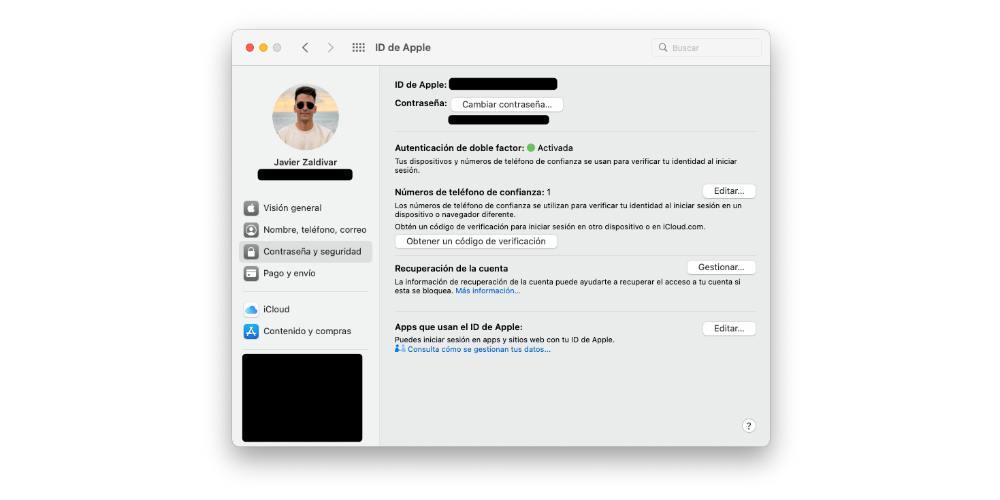
In the case of wanting to activate it in your Apple ID on the Mac, you will simply have to follow the following steps:
- Go to System Preferences.
- Click Apple ID.
- Next to Two-factor authentication , tap Turn on.
- Perform any additional steps that will be requested. Make sure you have your phone number set up.
Block the installation of unverified apps
Applications are the soul of any computer in order to provide the best possible tools in order to improve user productivity. But there are two ways to get them: in the App Store or search for the .dmg file online. Keep in mind that the recommendation that should be made in these situations is precisely to use the Mac App Store. This is mainly due to the fact that all the apps that are in this service have the approval of Apple. Developers must pass many checks when it comes to quality, security, and privacy. This means that any installation you make from the Mac App Store has all the guarantees from Apple.
But in the Mac App Store there are not all the applications that exist. Developers, in order not to pass these filters or opt for Apple’s payment systems, upload the installation file to their own web page . But you always have to be careful. On many occasions, the problem can arise that there are some web pages that host infected installation files, masked with the name of some paid application that many users cannot afford.
As a security measure, macOS by default blocks any suspicious files when it tries to run. This is something that can be known thanks to the developer’s signature. If the installer has the data of the person who created it, and is trustworthy, there will be no problem. But this changes when it is not. Before authorizing it manually, it is important to remember never to run files that are unknown or downloaded from unreliable websites. This is because any infected executable can bring serious consequences to your Mac.
Perform Mac hard drive file encryption
A lot of important information is stored on storage drives, both hard drives and SSD drives. From documents that can become confidential to compromising images. That is why Apple has a system integrated into macOS that allows all disks to be encrypted. This is something that has been implemented for many years, but lately it is more fashionable. It is aimed at encrypting the files of those people who need some confidentiality in their storage. In this way, it should be noted that it is not intended for a general public , but if you want to prioritize your security you can always choose to activate it.
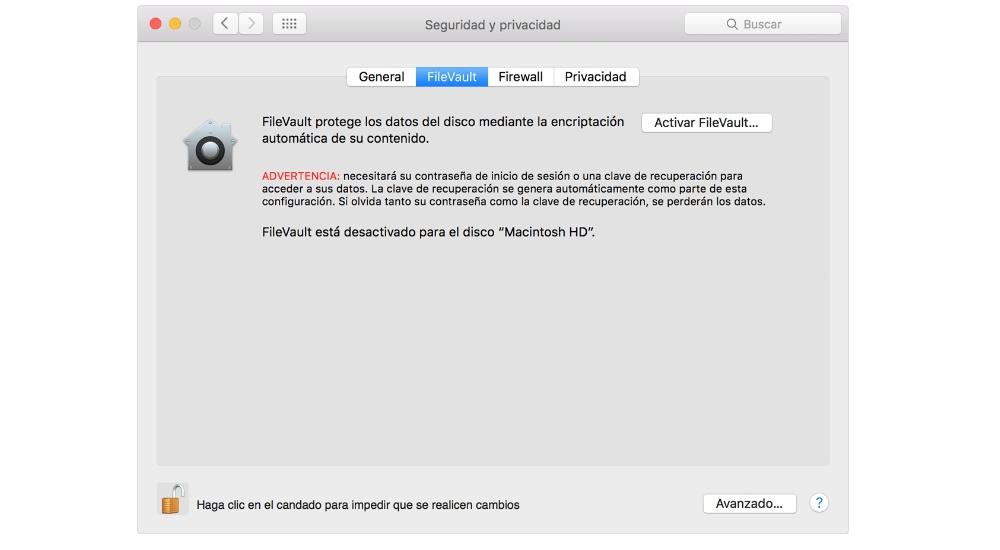
Disk encryption is done seamlessly so that no one can gain access to the disk even if they have it physically. This is important when your Mac is stolen and they want to extract the information from the storage drive by connecting it externally. But with this system all files will be locked. In order to perform the complete activation, you will simply have to perform the following steps:
- Access System Preferences.
- Click on Security and privacy.
- Click on the FileVault tab.
- Click on the FileVault tab, reading through all the security tips on offer.
Keep in mind that this is not an immediate process. You will have to wait quite some time until the encryption of all the information is completed. This is something that can vary depending on the amount of data you have stored on these drives.
Always make a backup
On many occasions you always have to be really careful. There are some malware that aim to lock down your computer completely and ask for a ransom to get your files back. This is something that may not worry you too much in the event that you have a backup of all this information on an external storage unit . This is mainly due to the fact that you will be able to restore the system without any problem and recover all the information by connecting the storage unit and restoring the files. Likewise, it should also be noted that the copy can be made online in the cloud, such as iCloud Drive.
We particularly recommend always making use of Time Machine to be able to make the backup. This is mainly because it works really well to have a temporary location of all the files. In the end, it should be a routine to make a backup of all this data when your workday ends and you are going to turn off the device. Obviously we recommend connecting the physical unit only when the backup is going to be made and not being permanently connected in order to avoid massive data deletion.

Make use of a VPN network
There are many tools that aim to have a connection that is hidden. This is precisely what is achieved with VPN networks that camouflage the connection to your computer. This is ideal to use especially when you have a connection that is not completely secure . All the data you send and receive will be completely safe so that it can reach its destination. This is something that also adds to the fact of being able to camouflage your virtual location. In other words, VPNs will always indicate that you are in another region than the original one. Ideal when you travel to some kind of country where there is some kind of internet censorship.
But as was the case previously, you have to know how to choose VPN applications. This mainly translates into the fact that you have to flee from those options that are free. This is mainly due to the fact that they do not generally have optimal characteristics that are really important. But in the case of paid VPNs, you will have access to a large collection of really interesting features to meet your needs. This also always guarantees that your data is not being commercialized, since its source of income is another.

Browsers that are safe on Mac
To be able to search the internet, it is important to have a good browser to access the network and the main search engines. These are the main gateway for viruses and malicious files. That is why you should never opt for any browser, and you must choose it correctly. Natively macOS comes with Safari installed. This provides a series of features that are ideal to prevent the tracking of your information. This makes it ideal for this type of browser to be used by default both for security and for the performance it provides.
Some very specific features need to be prioritized when making this choice. The main thing is to look for those options that have tracker blockers . This is ideal, since personal information cannot be collected from all the searches you carry out. In this way, companies will not have to negotiate with this type of data. This also adds to the need for browsers to have a database of websites that are malicious. This way you will block any user’s access to these completely malicious web pages.
Will you need to have an antivirus installed?
This is one of the big questions that you are going to be able to ask yourself in the day-to-day use of your Mac. Numerous software are available online that aim to prevent the Mac from ending up being infected. These programs have the mission of analyzing all the activity you carry out on the Internet, such as the web pages you visit and also the files you are going to download. Your files will be constantly checked for malware so that it can be quarantined or removed completely. Likewise, exhaustive analyzes of all the files that are contained on the hard disk can also be carried out in order to track down any problem that may exist.

But on many occasions antiviruses can generate more problems than solutions. Keep in mind that these software will have access to all your personal information. In the case of options that exist totally free, you should be wary. This is mainly due to the fact that the developers must obtain some type of economic revenue and will dedicate themselves to selling personal data. That is why if you opt for one of these protection programs, we recommend you always choose those options that require a payment to work . These assure you that they will only have the mission of protecting you and not doing business with your data.
In particular, we recommend you not to install any antivirus. Natively, macOS has a firewall that prevents the entry of most network threats. But in the end, keep in mind that the best antivirus is common sense . You should always avoid accessing those websites that are unreliable and above all, do not download anything from which you do not have data about its security.