When we have dozens of computers on a network, it is necessary to organize the data correctly and also the credentials of the different users. In order to create a hierarchical structure, it is very important to have a system such as LDAP, which will allow us to store, manage and protect the information of all the equipment properly, and will also be in charge of managing all the users and assets. Today in this article we are going to explain everything about LDAP and how to install and configure it on a Linux system.
What is LDAP and what is it for?
LDAP (Lightweight Directory Access Protocol) or also known as “Lightweight Directory Access Protocol” is a TCP/IP application layer protocol that allows access to an ordered and distributed directory service, to search for any information in an environment network. Before we continue explaining what LDAP is for, we need to know what a “directory” is. A directory is a set of objects with attributes that are organized logically and hierarchically, that is, it is in the form of a tree and perfectly ordered depending on what we want, whether alphabetically, by users, addresses, etc.
Generally, an LDAP server is responsible for storing authentication information, that is, the username and password, to later give access to another protocol or system service. In addition to storing the username and password, it can also store other information such as the user’s contact details, location of local network resources, digital certificates of the users themselves, and much more. LDAP is an access protocol that allows us to access the resources of the local network, without the need to create the different users in the operating system, and it is also much more versatile. For example, LDAP allows authentication and authorization tasks for users of different software such as Docker, OpenVPN, file servers such as those used by QNAP, Synology or ASUSTOR among others, and many more uses.
LDAP can be used both by a user who is asked for some access credentials, as well as by applications to know if they have access to certain system information or not. Generally, an LDAP server is located on a private network, that is, local area networks, to authenticate the different applications and users, but it could also work on public networks without any problem.
The two most popular active directory services that are supported by LDAP are “Windows Active Directory”, or also known as “Windows Active Directory”, as well as OpenLDAP. Therefore, the LDAP protocol is compatible with both technologies so that users can access all files and applications from anywhere, they just need to authenticate and they will have access to their computer.
Currently the version of LDAP is LDAPv3, therefore, when we install and use this protocol, in the vast majority of cases we will be using the LDAPv3 protocol to authenticate the different clients.
How an LDAP server works
LDAP is a protocol that has a client-server architecture, therefore, we are going to have several clients that will connect to one or several LDAP servers. Generally, a single LDAP server is used where tens or hundreds of clients will connect to it to access the different resources of the local network. The server is where all the data related to the directory will be stored, it will also be in charge of user authentication, checking that there is only one user connected simultaneously or several from different devices, and other tasks that we will explain below.
The operation of LDAP is quite simple, since the communication is like any other communication between a client and a server, just as it happens in Windows with Active Directory. Below, you can see the three most important steps of communication:
- The client connects to the LDAP server (the process is called Directory System Agent) over TCP/IP port 389 to start the LDAP session.
- A connection is established between the client and the server.
- Data is exchanged between the server and the client.
There are two basic actions that a client can do when connecting, but first we must differentiate between authentication and authorization. Authentication is the mechanism by which we identify ourselves with a system, for example, by means of a username and password. Authorization is the mechanism by which we are or are not allowed to do something in the system. On an LDAP server we can do this:
- Read information : to read the information the client must be authenticated, then it will try to read and obtain information from the directory, before carrying out this step the server will check if that specific user has the authorization to read information.
- Modify information : to modify information the process is the same, but the server will check if we have modification permissions on the server.
LDAP also allows us to exchange information between several servers, if we authenticate ourselves on a server and it does not have the necessary information, we can make this query to another server that we have on the same local network, to check if we actually have this information or not. It is something similar to what happens with the DNS servers, which ask each other going up the tree until they reach the root servers.
Types of operation
On a server there are different operations that we can perform as clients, below, you can see all that we can do:
- Add: add a new entry. If the entry already exists, the server will notify us.
- Modify: modify an entry. The protocol allows three different modifications, add new value, replace value or remove value.
- Delete: delete an entry.
- Search: Search or get directory entries.
- Compare: See if a named input has a particular attribute.
- Abandon: abort a previous request
- Bind: authenticate to the server
- Start TLS – Establish secure communication using TLS in the LDAPv3 protocol.
- Unbind: close the connection.
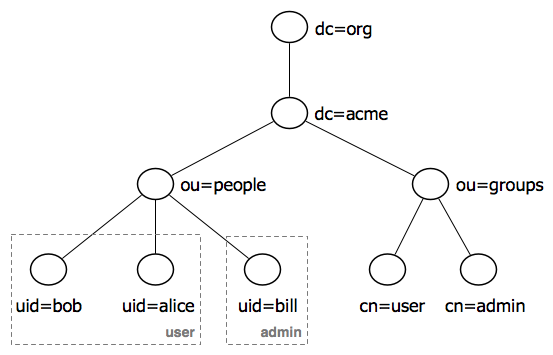
Components and structure
In order for this protocol to perform its task, there is both a directory structure and components. The most important components are:
- Directories: is a tree of directory entries.
- Inputs: Consists of a set of attributes. Entries describe the user by listing all of their attributes. Each entry has a unique identifier with its DN (Distinguished Name)
- Attributes: Attributes have a name and one or more values, they are defined in the schemas.
A basic structure of LDAP could be the following:
dn: cn=Redes Zone,dc=example,dc=com
cn: Redes Zone
givenName: Redes
sn: Zone
telephoneNumber: +34 666 111 111
telephoneNumber: +34 666 222 222
mail: redeszone@example.com
manager: cn=this article2,dc=example,dc=com
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
objectClass: top
- dn (Distinguished Name): This is the name of the entry, but it is not an attribute or part of the entry itself.
- cn (Common Name): is the relative distinguished name.
- dc (Domain Component): is the Distinguished Name of the parent entry.
The rest of the lines are the attributes of the input, like the givenName, sn, telephoneNumber, mail, and the different objectClass we have. A server always hosts a subtree starting with a specific entry.
To perform searches we have to put a URL to obtain information, the syntax that we must use is the following:
ldap://host:puerto/DN?attributes?scope?filter?extensions
Many of these components are optional, for example, we could simply call the DN so that it returns all the information related to this entry.
Differences between Microsoft Active Directory and LDAP
Microsoft Active Directory uses the LDAP protocol internally to carry out all communications from the clients to the server or servers, therefore, it ensures that clients can authenticate themselves and access any stored data, in addition, we must take into account that this protocol It is multiplatform, not only do we have it on Windows operating systems but it is also compatible with Linux, Unix and macOS, all through the protocol. To give you an idea, the following directory services use this protocol for their communication:
- Microsoft Active Directory
- Apache
- Red Hat Directory Service
- OpenLDAP
And many other services use it as well, most notably the latest, OpenLDAP, which is an open source implementation of the protocol and can be installed on any system, since the source code to compile it is available. However, in most Linux distributions we have it available in their repositories.
Installation and basic configuration
Installation and commissioning on Linux-based operating systems is very easy, and we also have the possibility to activate the server on a QNAP NAS. Next, we are going to explain how to perform the installation and basic configuration in Debian, and also in QNAP.
Debian
If we have a Linux-based operating system like Debian, we will be able to install ldap through the official repositories of the distribution. To do this, we can put the following command in the terminal, logically we need superuser permissions.
sudo apt install slapd ldap-utils
Once we run it, it will ask us what administrator password to put on the server, once we have put it in, it will finish installing the software and we can start working with it.
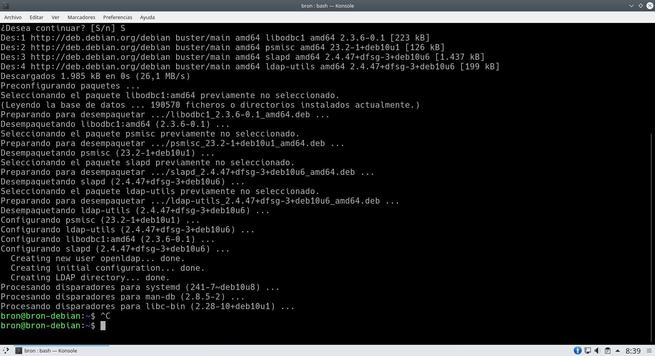
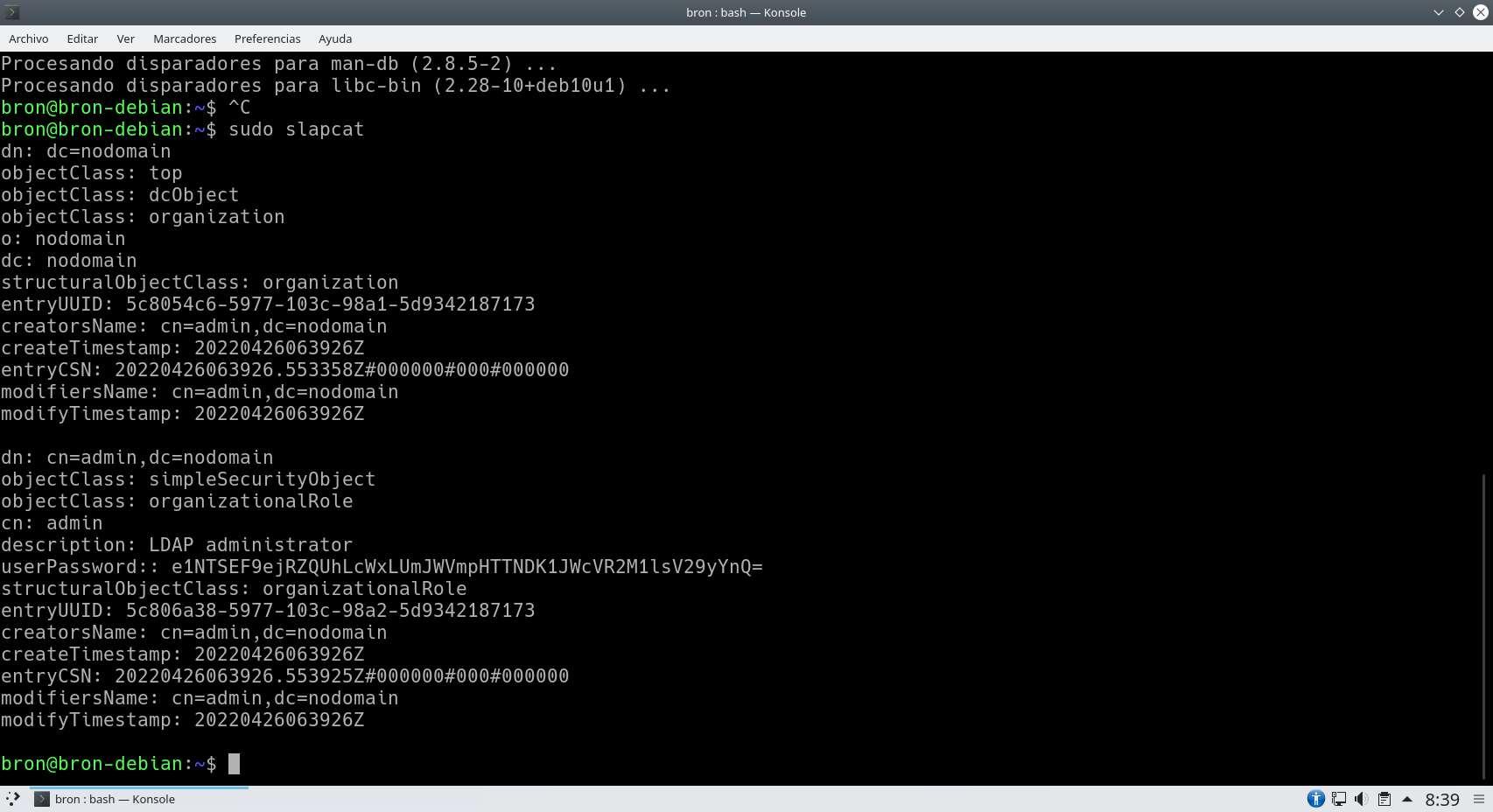
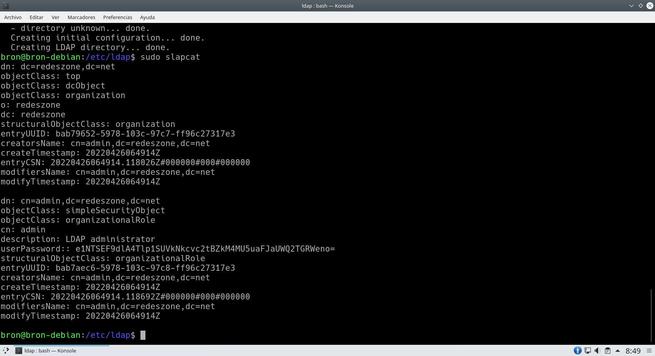
To verify that it has been installed correctly, we put the following order and it will show us all the data of the server at present.
sudo slapcat
The following screenshot should show what we get right after the installation:
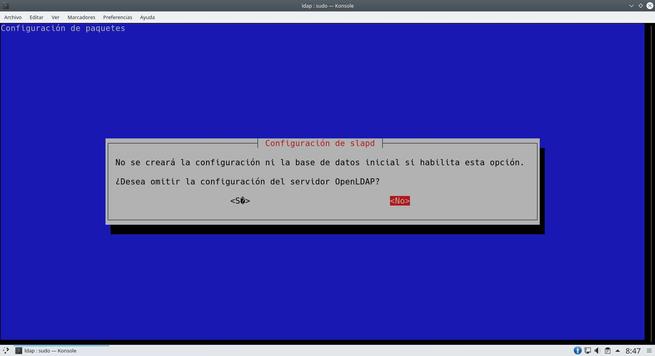
Now we have to reconfigure slapd in order to put our own domain, we execute the following command to start the configuration wizard.
sudo dpkg-reconfigure slapd
The wizard will ask us many aspects of the server, we can leave everything as we show you in the following screenshots. The most important thing is to put the DN properly.
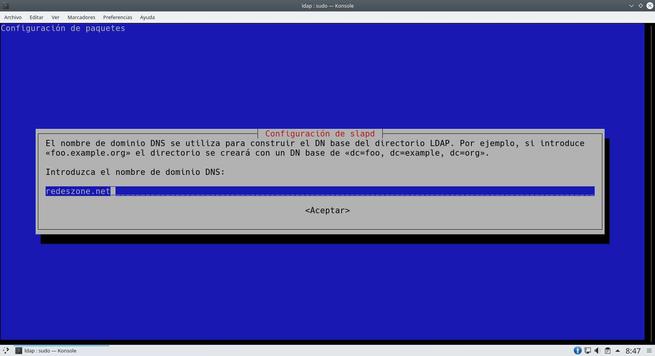
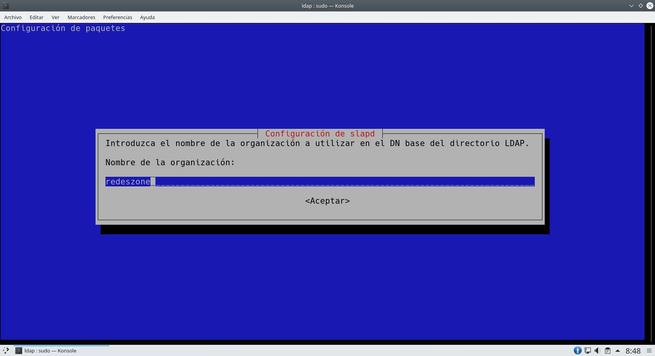
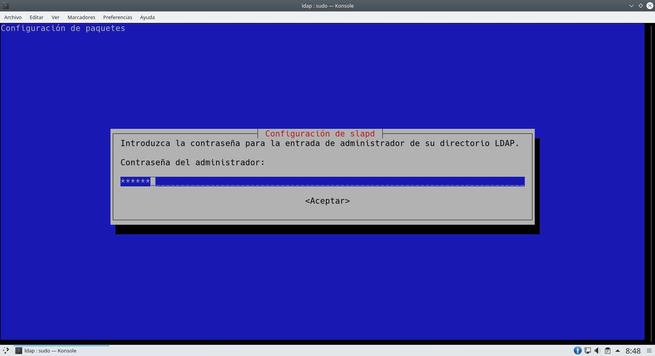
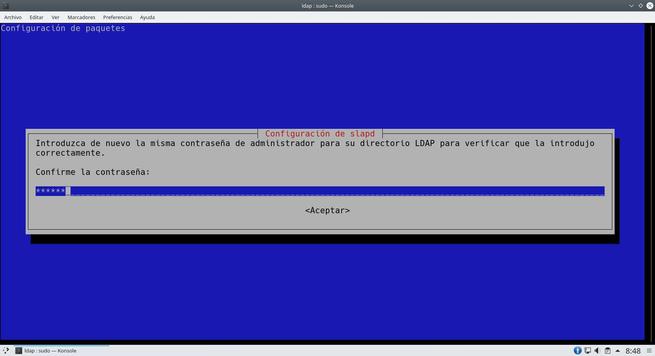
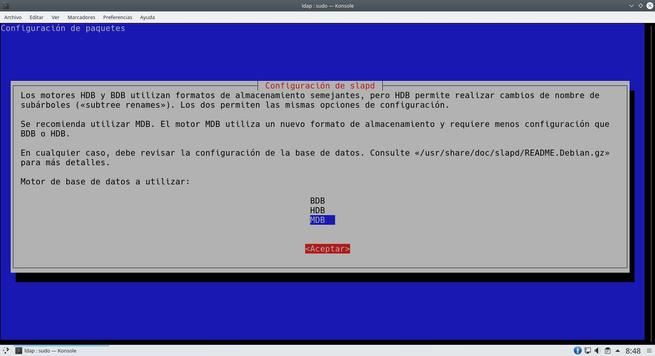
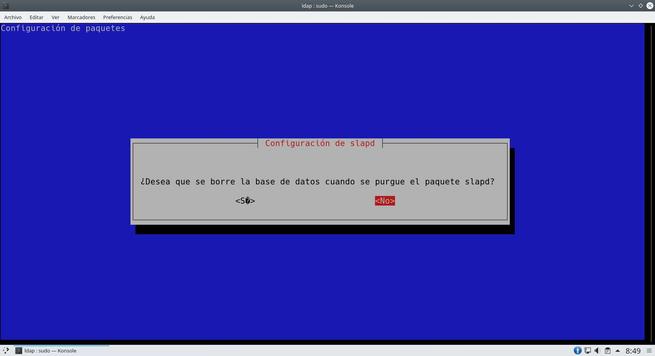
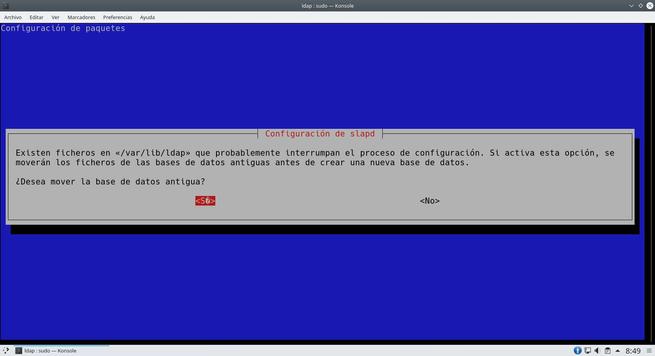
Once we have done everything, we will have the server ready to add the different users.
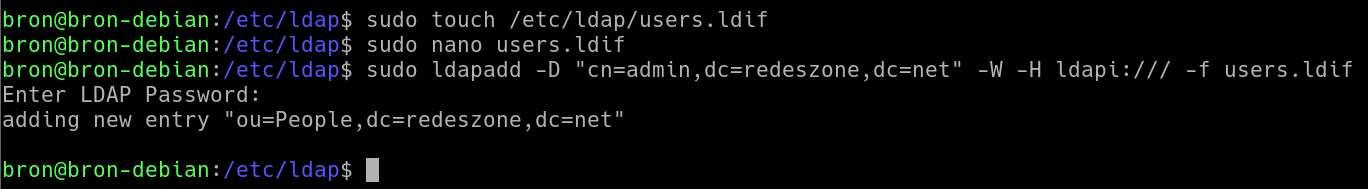
The first thing we must do is create a list of all users, for this we create a file in /etc/ldap with the name “users.ldif”.
sudo touch /etc/ldap/users.ldif
With any text editor we proceed to edit this file with the following content:
dn: ou=People,dc=redeszone,dc=net
objectClass: organizationalUnit
ou: People
Once we have done it, we have to introduce it to the server in the following way:
sudo ldapadd -D "cn=admin,dc=redeszone,dc=net" -W -H ldapi:/// -f users.ldif
It will ask us for the password and we will proceed to enter it. It should not give us any type of error.
Finally, if we want to perform a search we will be able to do it in the following way:
sudo ldapsearch -x -b "dc=redeszone,dc=net" ou
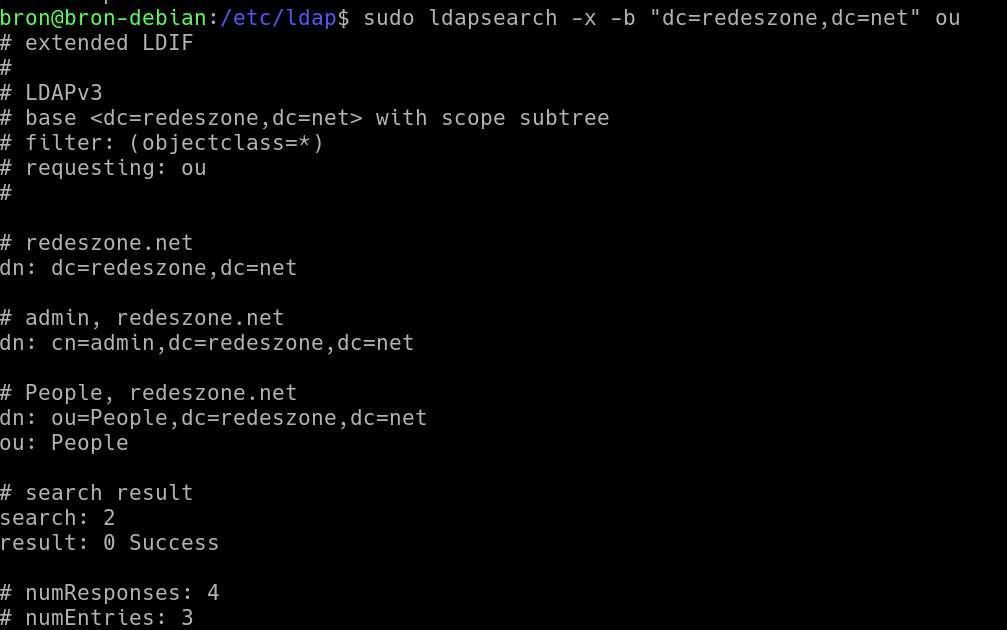
The basic configuration of the server is already done, now we have to add the different entries with the information that we want.
QNAP NAS server
If you use a QNAP NAS server, we have an LDAP server installed by default. To do this, we go to the “Control Panel / Applications / LDAP Server” section. In this menu we proceed to put the domain name and the administrator password, once we have indicated it, we proceed to click on “Apply”.
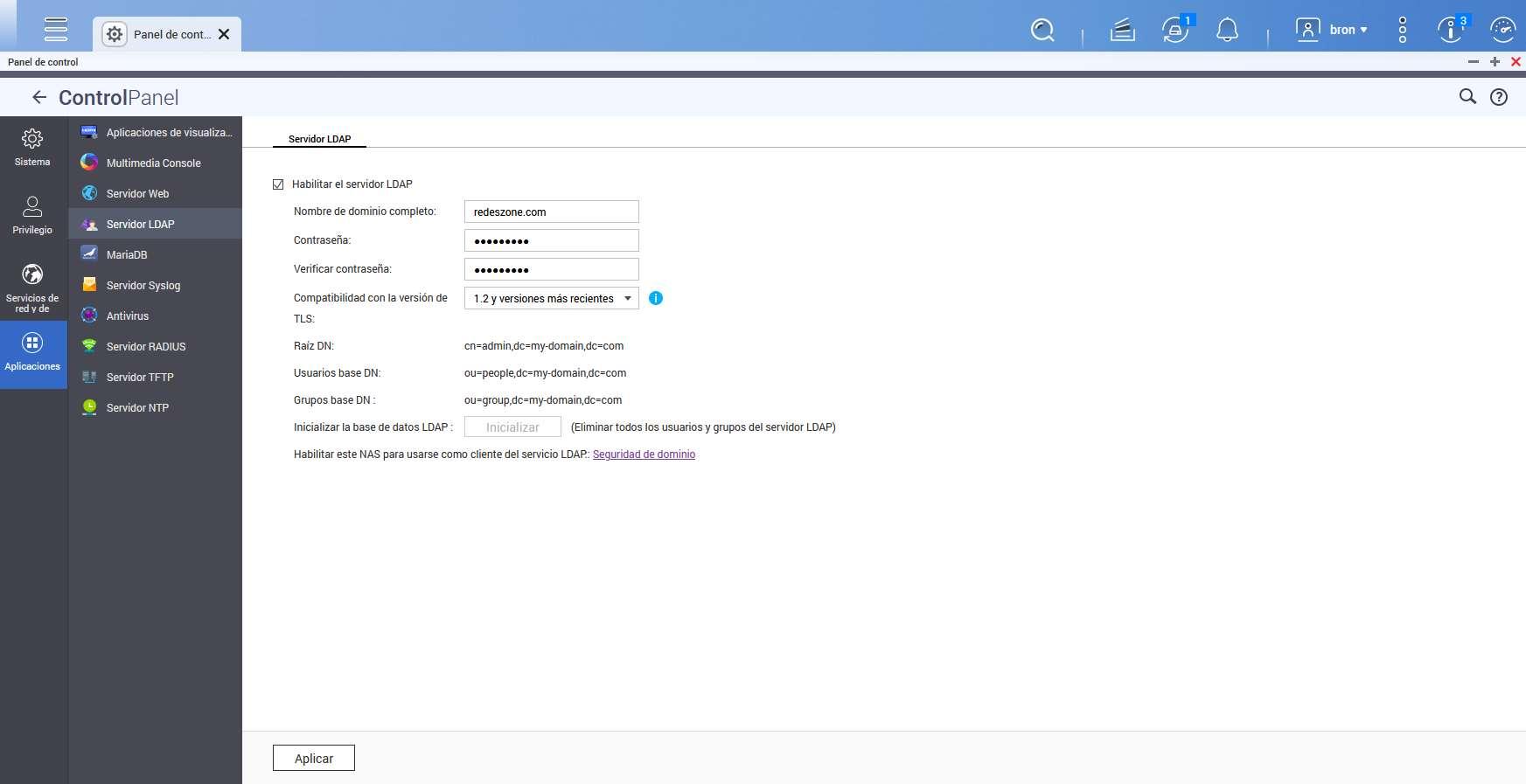
Once we have applied the changes, we will have the server up and running. Now new tabs called “Users”, “Group” and also “Backup and Restore” will appear.
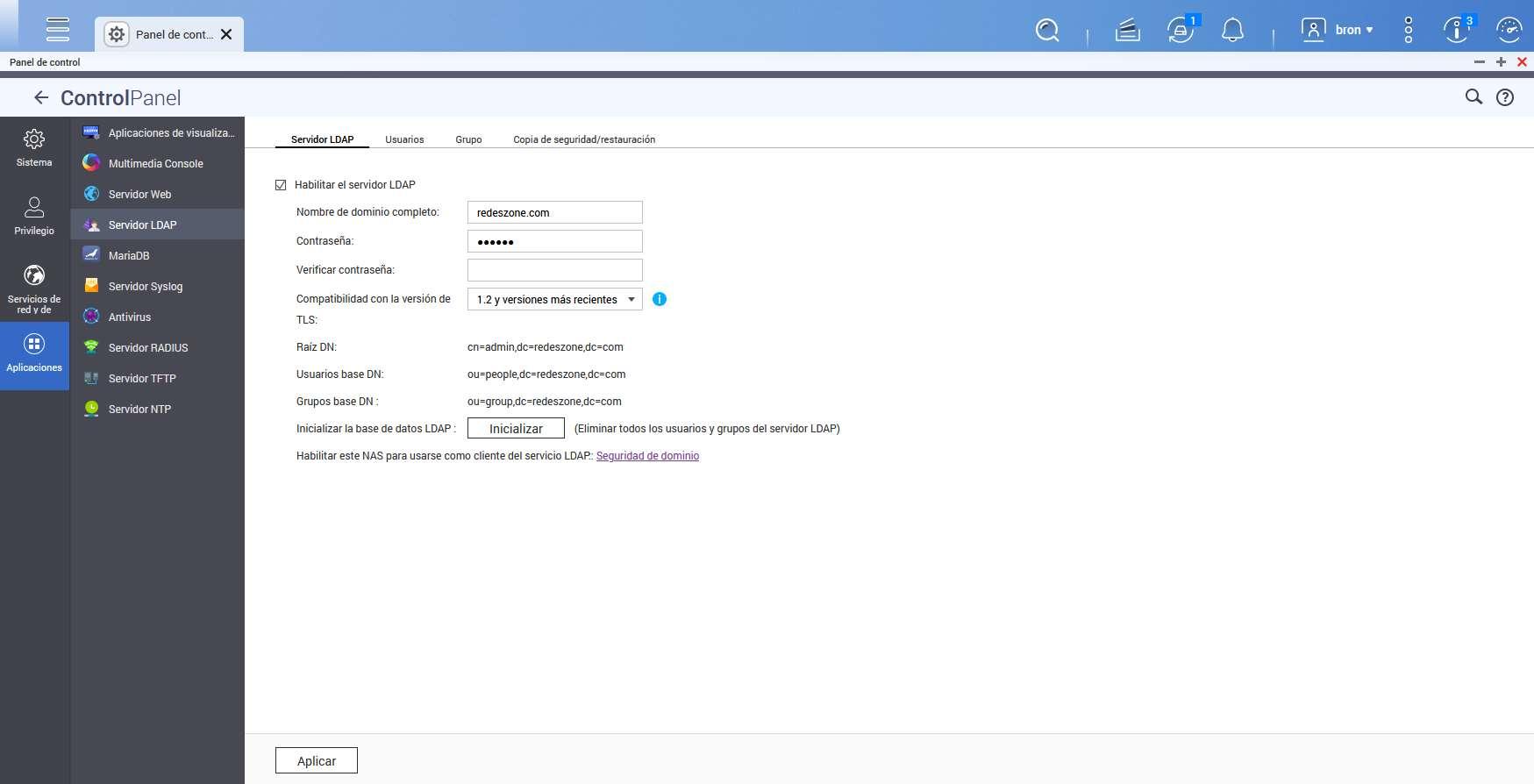
In the users section is where we will be able to register the different users with a small configuration wizard. We simply have to follow this simple wizard to add all the users we want.
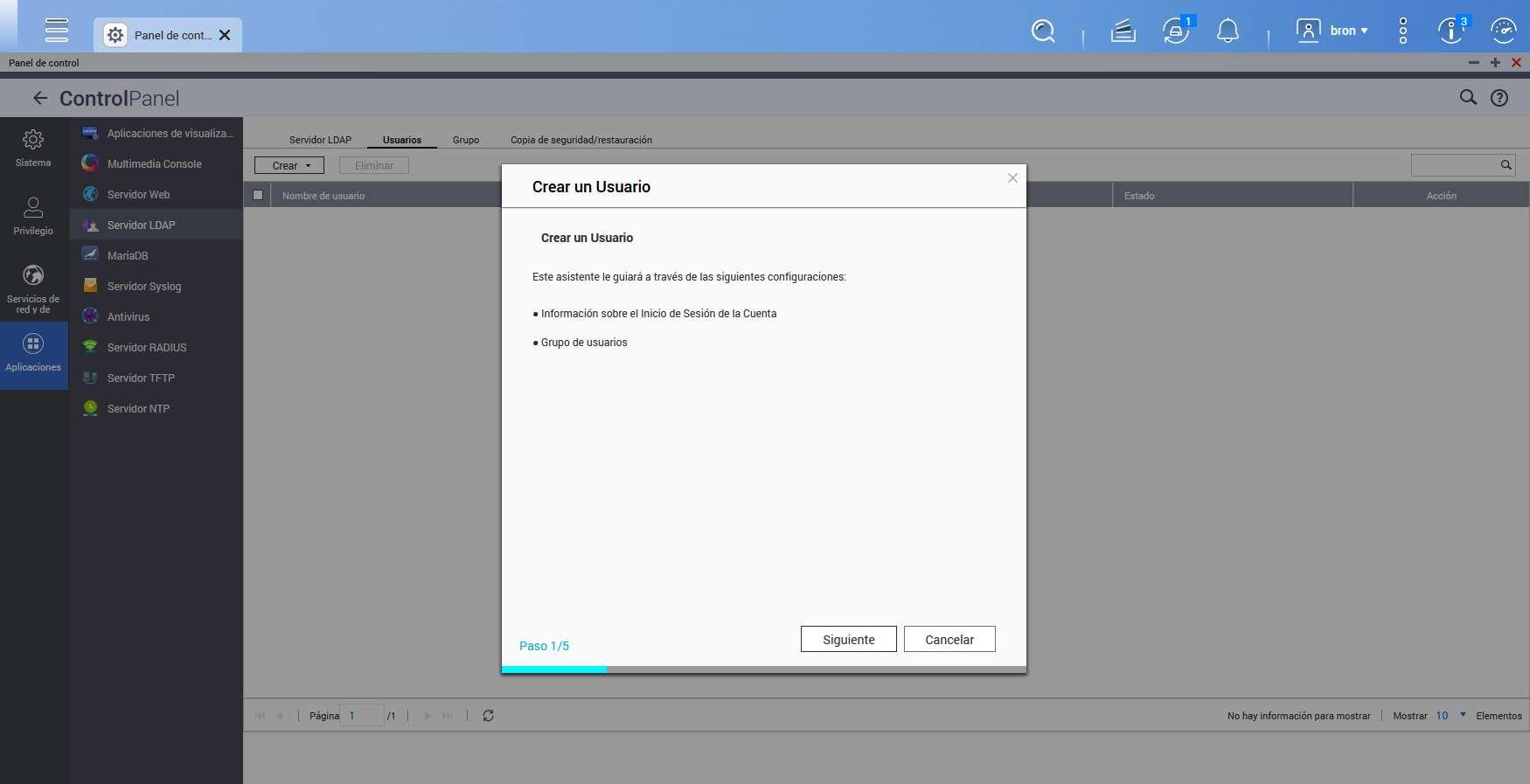
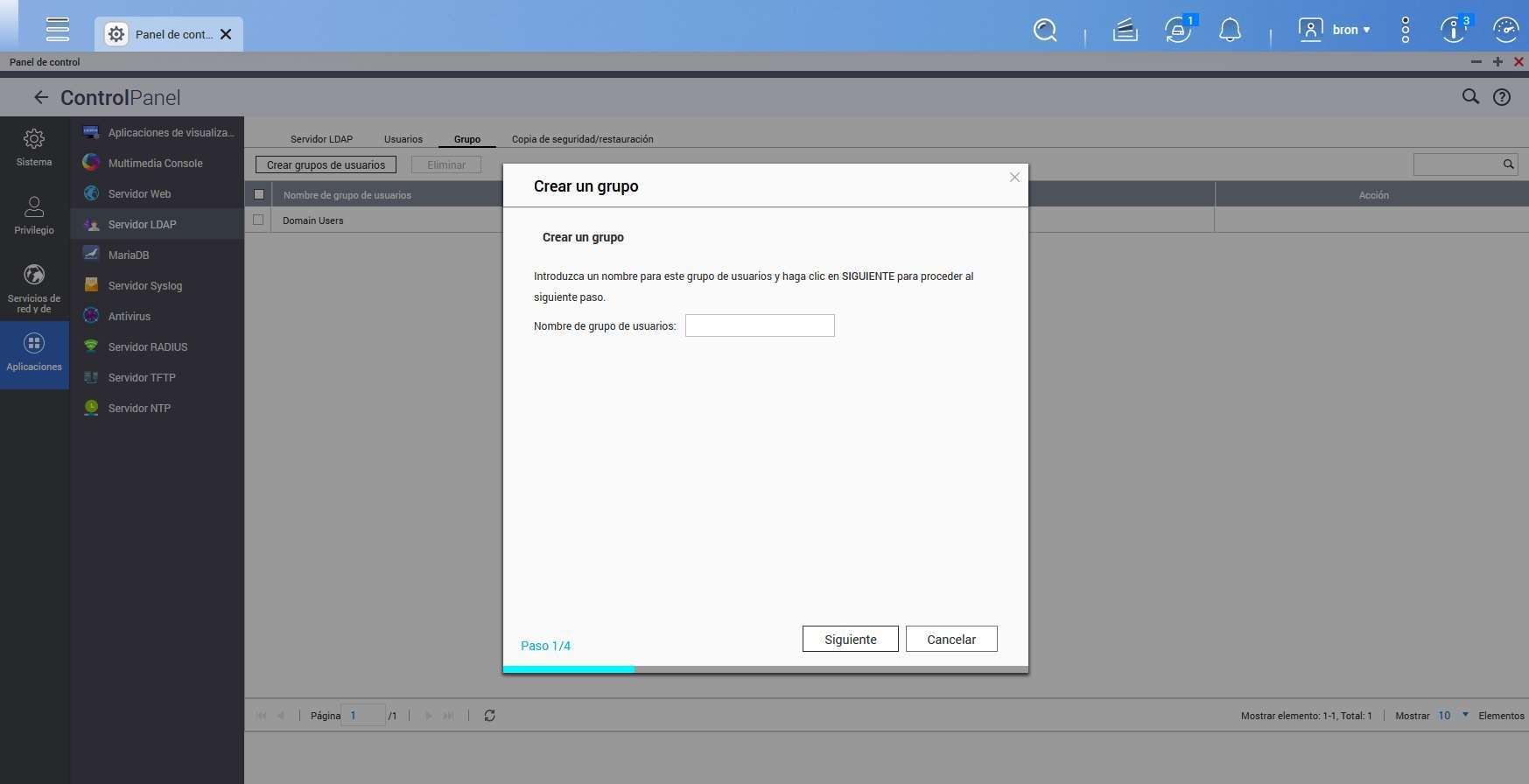
We also have the possibility to add a new group of users, we will also have a wizard to help us with the process.
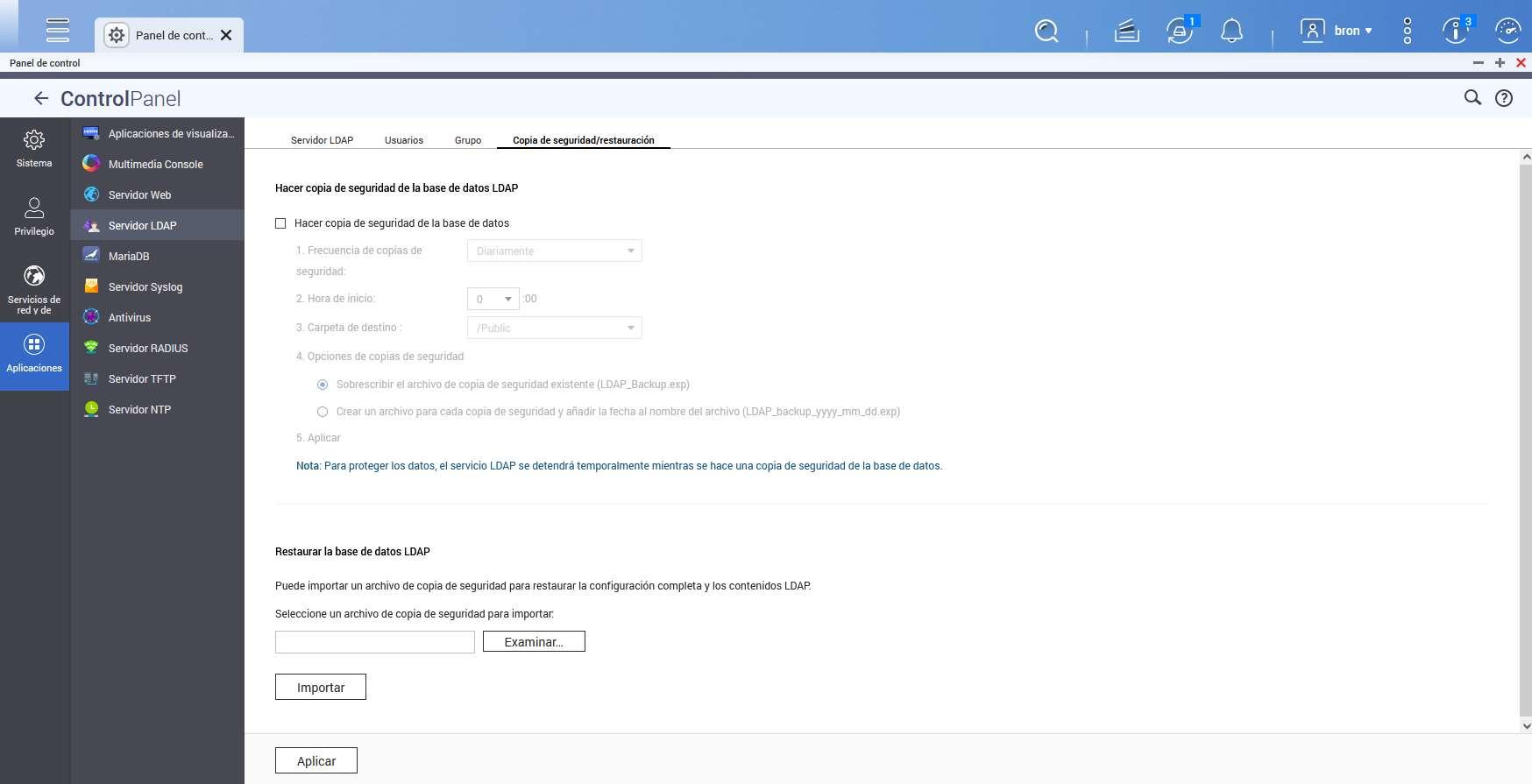
Finally, in the backup and restore section, we will be able to make a backup of the entire server database, and even restore it from a previous copy, ideal for not losing all the information contained on our server.
As you can see, the implementation of this LDAP server in a QNAP is very simple, we do not have to execute any command through the console, everything is done through the graphical user interface.
Conclusions
The LDAP protocol is widely used in professional environments to authenticate the different users, and where we are going to be able to store the ordered and hierarchical information. This protocol is not only used by software such as OpenLDAP, but also by other directory systems such as Windows or RedHat, among many others that we have explained to you. Although its operation may seem complicated at first, once we install the server and start registering users and groups, you will perfectly understand everything related to this important protocol.
This protocol is one of the most important to authenticate users within a company, in addition, it is also often used together with RADIUS servers, and depending on our needs, we can choose this protocol instead of RADIUS and even both coexist in the same local network for different uses that we can give it.