We must always keep in mind the importance of having security tools to protect our equipment and systems. We have a wide range of possibilities, both free and paid. But there are also many attacks that in one way or another could affect us and put the proper functioning of our equipment at risk. One of them, one of the methods used by hackers, is what is known as a DDoS attack . In this article we are going to show some tools that help us create attacks of this simulated type to see how they work and see to what extent our servers are trained to deal with.
Why DDoS Attacks Are So Important
Among all the attacks that we may suffer, the denial of services or DDoS attack has the mission that our servers, our teams, cannot respond to the requests they receive. This could make a web page or any server that is vital to a business or organization unavailable.

DDoS attacks produce significant financial losses. Hence, sometimes the organizations themselves are forced to pay a financial ransom to end these attacks as soon as possible. Let’s think about a website to sell products and that it needs users to be able to access the catalog and make purchases. If that website is down for a day, users will go to the competition, our company would lose face and directly lose sales.
Therefore, protecting ourselves against these types of threats is very important. But sometimes the best protection is knowledge. The fact of knowing how an attack acts or seeing if our teams are protected and trained to face. Sometimes we are going to need to use certain programs that help us to have a better knowledge about it.
It does not matter what type of device or operating system we use, since we must always keep in mind the importance of security. Luckily we can count on many programs that can help us. Many tools that allow you to maximize security to prevent the entry of intruders.
Programs to simulate DDoS attacks
We are going to see some of the most important programs that we can use to carry out DDoS attacks . A selection that we can take into account and analyze the capacity of our servers. All of them are free and available for home users and organizations to use to learn more about the operation and protection of this type of threat.
LOIC
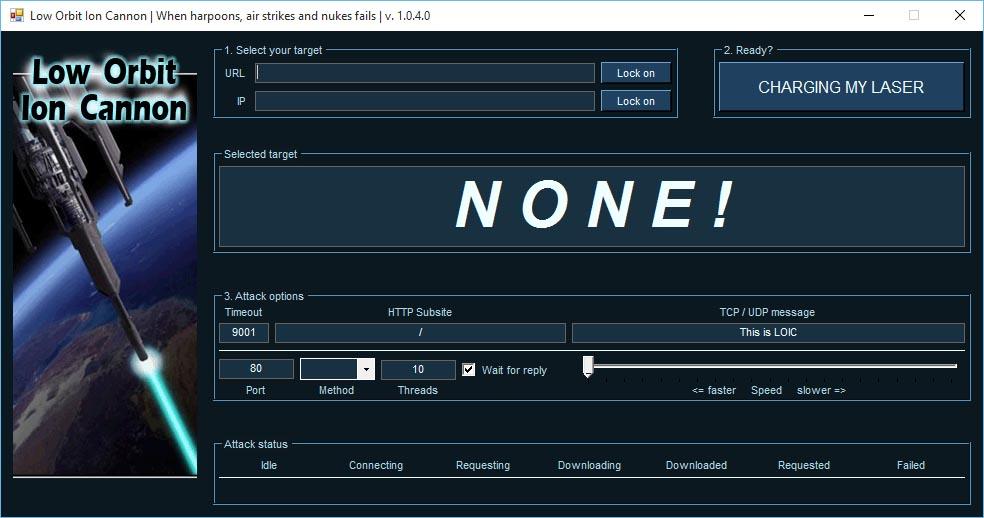
One of the tools we have to simulate a DDoS attack and learn about how our system can protect itself is LOIC. It stands for Low Orbit Ion Cannon. Basically what this program, which is free software and available for Windows and Linux, does is send a large number of TCP, UDP and HTTPS requests. It tests the target network to see how well it can withstand these types of attacks.
The objective of the developers of this tool is that it serves for educational use. They want users to learn more about how to defend against DDoS attacks, see if the defense of the equipment is adequate and improve certain parameters.
We can access the LOIC source code and download it to run on Linux or Windows.
HULK
Another program that we can use for the same purpose, to test our computers and simulate a DDoS attack, is HULK. It is ideal for our web servers and to see to what extent they could withstand such a threat that could render all visitors who try to access our site down.
HULK stands for HTTP Unbearable Load King . This tool is written in Python and allows generating a large number of unique requests to affect the load on a server. We can also download it from GitHub , where we will see the information regarding the code.
Tor’s hammer
Tor’s Hammer also allows us to simulate DDoS attacks. Allows you to test servers and applications . Its name is not a coincidence, and it is that it allows it to be used through the Tor network so that it is totally anonymous.
The goal of this program is to saturate the TCP stack with multiple requests. Send incomplete requests, slowly, to keep the connection active as long as possible. It thus seeks to cause a denial of service when the server can no longer maintain active connections.
We are facing a tool written in Python and that we can download from GitHub.
BoNeSi
In this case we are facing a program that works for Linux. It is open source and totally free that we can run on the command line. It allows to point to an IP address and we can also use it in a virtual machine.
As in the previous cases, with BoNeSi we can put our servers to the test. We can see to what extent they are capable of dealing with a DDoS attack that could compromise their proper functioning. One more way to achieve a significant improvement in security and have a greater knowledge.
In GitHub we find all the information about this program and the code to download it.

DDOSIM Layer 7
This program allows you to simulate a DDoS attack with multiple random IP addresses. This allows you to create a large number of TCP requests to point to a target server. It works in a similar way to BoNeSi and we can also use it in Linux. We can download the source code from GitHub and get all the necessary documentation there.
The objective of DDOSIM Layer 7 is none other than to show us the real capacity that our server has to be able to withstand possible denial of service attacks that they may receive. One more way to preserve the good functioning and to avoid possible problems that are exploited by cybercriminals to destroy our connections.
In short, these are some of the tools that we can use to test our servers. We have shown an interesting selection of programs to simulate DDoS attacks. This way we can see to what extent we would withstand this type of attack and help us take measures to achieve greater defensive capacity in order to protect our equipment and that everything works properly at all times.