DDoS attacks are one of the threats that could compromise our servers and cause them to malfunction. They can affect web pages and leave without service. It is, therefore, one of the methods hackers use to put users at risk. In this article we are going to talk about BoNeSi , a tool for Linux that allows us to carry out a simulated attack of this type. One more way to learn how to act and be protected.
DDoS attacks
We can say that DDoS attacks target computer systems or networks in order to prevent them from giving a normal response. For example, a network could consume bandwidth and cause it not to respond to user requests.
Let’s put a DDoS attack against a web page. This attack will make multiple requests to saturate the server . Should a visitor try to log in, they might find that it doesn’t work.
It is a problem that over the years has been increasing. Even hackers can use it to blackmail companies and organizations. After all, leaving a company that is dedicated to online sales, for example, a whole day without service can mean a significant financial loss.
This means that we must be protected at all times. We must prevent the entry of malware that could compromise our systems, correct possible vulnerabilities, improve network security … Everything can help us to prevent attacks such as DDoS and many other varieties that put our computers at risk.
BoNeSi, a tool to make simulated attacks
BoNeSi is a tool that helps us better understand how a DDoS attack works. It basically allows us to simulate one. We can use it in our network, to point to a specific IP address. We can install it in a virtual machine with Linux and act against a computer equipment that we have.
Keep in mind that, as we mentioned, it is a tool for Linux. Therefore, we are going to have to have some distribution. We can use it on a computer if we have a distro installed, or we can also test it in a virtual machine in Windows.
The first thing we have to do is download BoNeSi from GitHub. There we will find the source code of this tool, as well as the information necessary to start it. We will see data about its installation, operation or the objectives of having it installed.
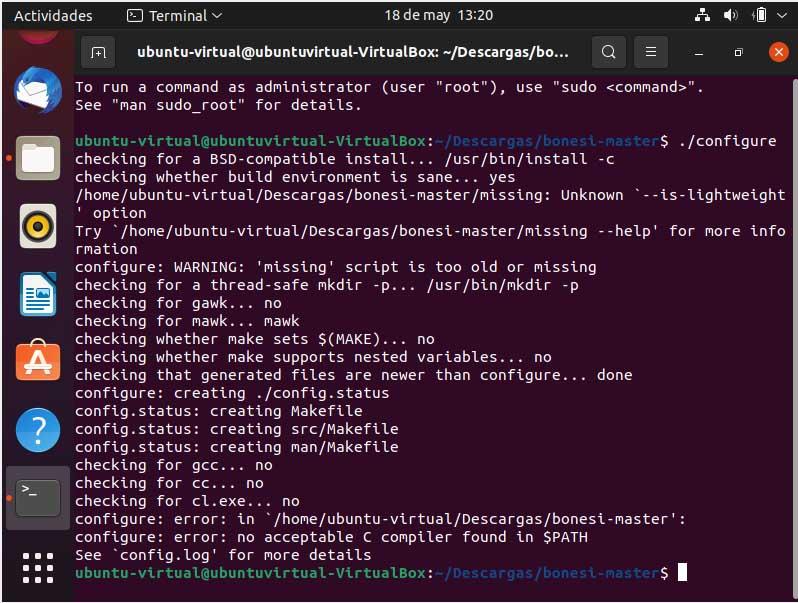
Once we have downloaded it, the next thing to do is install it. We must open a Terminal in Linux and execute the following commands:
./configure
make
make install
When we have installed it, we simply have to run it from the Terminal. It will show us a window with the different options of this tool.
The most basic thing, to carry out an attack against a specific IP would be as follows: bonesi IP: port. For example bonesi 192.168.1.10:80. From that moment on, the tool will start sending packages constantly. It will start to carry out a DDoS attack towards the address we have set.
Why is BoNeSi useful
What use is this to us? Safety is a very important factor and we must always take care of all kinds of details. For this we can also make use of tools that help us avoid problems , to also put our devices to the test. So we can see how they respond to possible failures and attacks.
BoNeSi, therefore, can help us to check if our equipment is effective against a DDoS attack . We can see to what extent security fulfills its mission and we can face a hypothetical real attack that could leave our computers and servers without providing service.
However, we must bear in mind that we are facing an attack from a single device and our property. Especially if we make use of a virtual machine, which has much less resources, we will not notice practically anything. The team will continue to function normally and the consequences are minimal. In a real DDoS attack the results are much more remarkable. We are talking about hundreds of computers that are part of a botnet, pointing against a specific server.
How to protect our team from DDoS attacks
We have seen how BoNeSi works, a tool for Linux that allows us to test our devices with simulated DDoS attacks . We have also talked about why this type of program is interesting. Now we are going to give some tips to protect ourselves from attacks of this type that we may suffer in real life. A series of recommendations to implement and improve security at all times.
Keep equipment safe
Something fundamental to protect our security at all times is to have the equipment properly insured. A good antivirus, for example, can prevent the entry of malware and attacks that can compromise our devices at any time.
But you don’t just have to have an antivirus, especially when we want to protect ourselves from DDoS attacks. It is essential to have a good firewall that can intercept malicious connections against our servers and computer equipment. We have at our disposal a wide range of options in this regard. Whatever type of operating system or device we use, we must have good protection.
Upgrade systems
Of course, an important point is to have the equipment properly updated . It is essential to correct any vulnerabilities that may exist. Hackers can take advantage of computer flaws to launch their attacks.
This means that we must update the systems at all times. We must always have the latest updates and security patches that appear for our servers or computer equipment.
Check network connections
Another issue to keep in mind is to constantly check network connections . It must be observed that there are no strange devices trying to access or within our network. We must carry out regular reviews and make sure that there are no possible intruders who put our security at risk.
In short, these are some recommendations that we can put into practice to avoid DDoS attacks. A series of tips that can help improve security and prevent potential intruders from putting our systems at risk.